2016-11-08 - JRAT INFECTION FROM EMAIL LINK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 22016-11-08-jRAT-infection-traffic.pcap.zip 254.1 kB (254,109 bytes)
- 2016-11-08-jRAT-infection-traffic.pcap (270,266 bytes)
- 2016-11-08-files-from-jRAT-infection.zip 1.7 MB (1,719,340 bytes)
- 2016-11-08-malspam.eml (33,476 bytes)
- Query Reference Slip .zip (472,416 bytes)
- Windows6052555107978301025.dll (46,592 bytes)
- nSlrfMRSMfa.jAtqpg (247,119 bytes)
- pkKDftHgUY.NvMEa (968,665 bytes)
NOTES:
- Documenting a malicious email I received with a link to a jRAT backdoor.
- Some might call this Adwind, but that's an older name. I understand it's currently called jRAT.
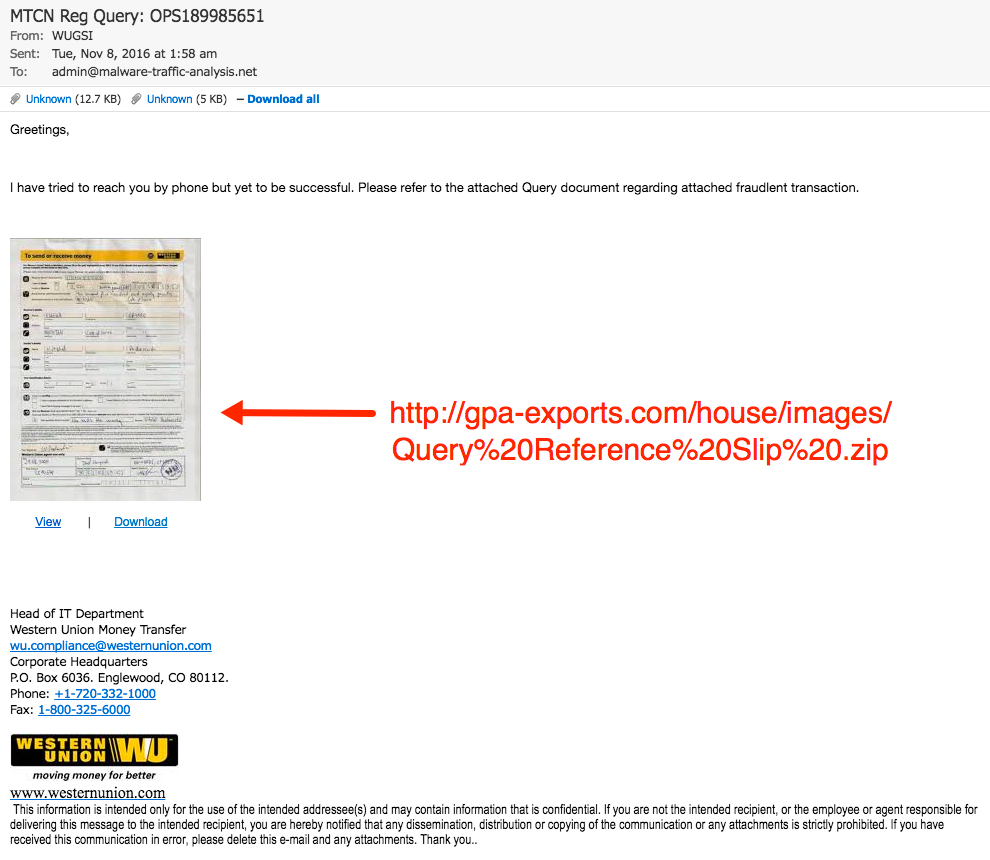
Shown above: Screenshot of the email.
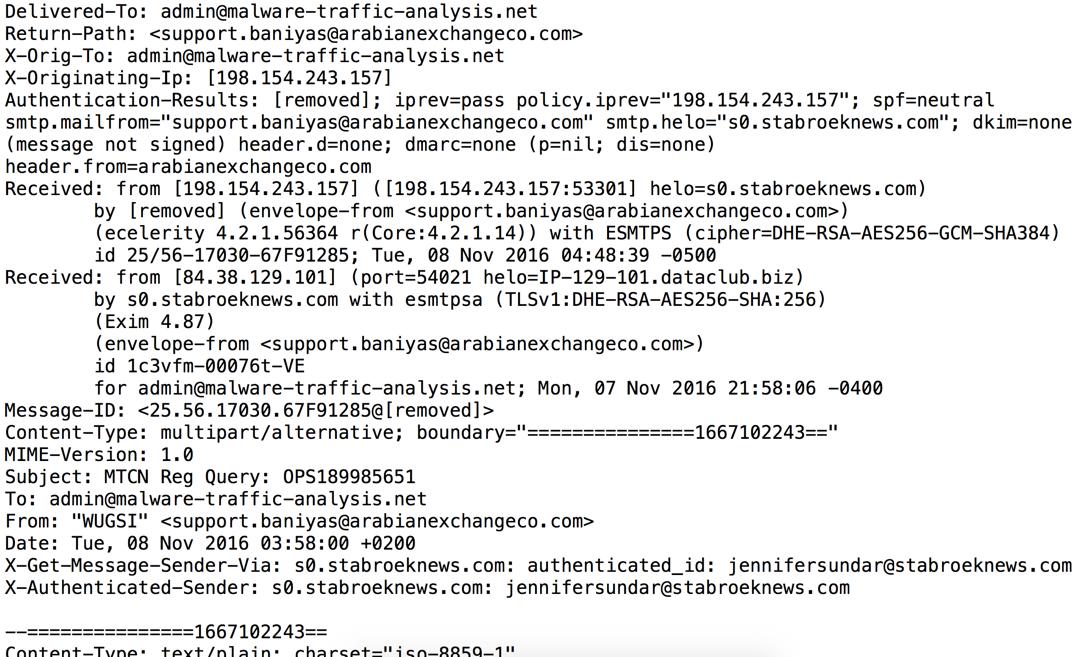
Shown above: Screenshot of some of the message headers.
INFORMATION FROM THE HEADER LINES:
- 198.154.243.157 - s0.stabroeknews[.]com - sending mail server
- Subject: MTCN Reg Query: OPS189985651
- From: "WUGSI" <support.baniyas@arabianexchangeco[.]com> (This is a spoofed sending address)
- Date: Tue, 08 Nov 2016 01:58:00 UTC
MESSAGE TEXT:
Greetings,
I have tried to reach you by phone but yet to be successful. Please refer to the attached Query document regarding attached fraudlent transaction.
View | Download
Head of IT Department
Western Union Money Transfer
wu.compliance@westernunion[.]com
Corporate Headquarters
P.O. Box 6036. Englewood, CO 80112.
Phone: +1-720-332-1000
Fax: 1-800-325-6000
www.westernunion[.]com
This information is intended only for the use of the intended addressee(s) and may contain information that is confidential. If you are not the intended recipient, or the employee or agent responsible for delivering this message to the intended recipient, you are hereby notified that any dissemination, distribution or copying of the communication or any attachments is strictly prohibited. If you have received this communication in error, please delete this e-mail and any attachments. Thank you.
DOWNLOADED MALWARE
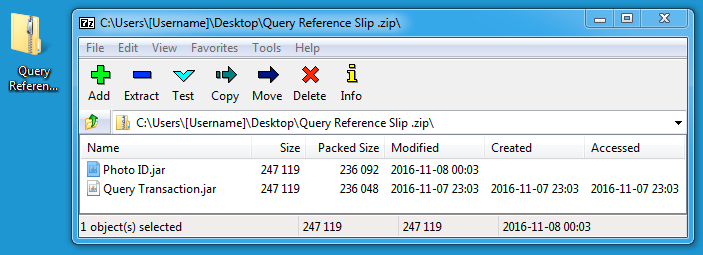
Shown above: The zip archive downloaded from the link in the email.
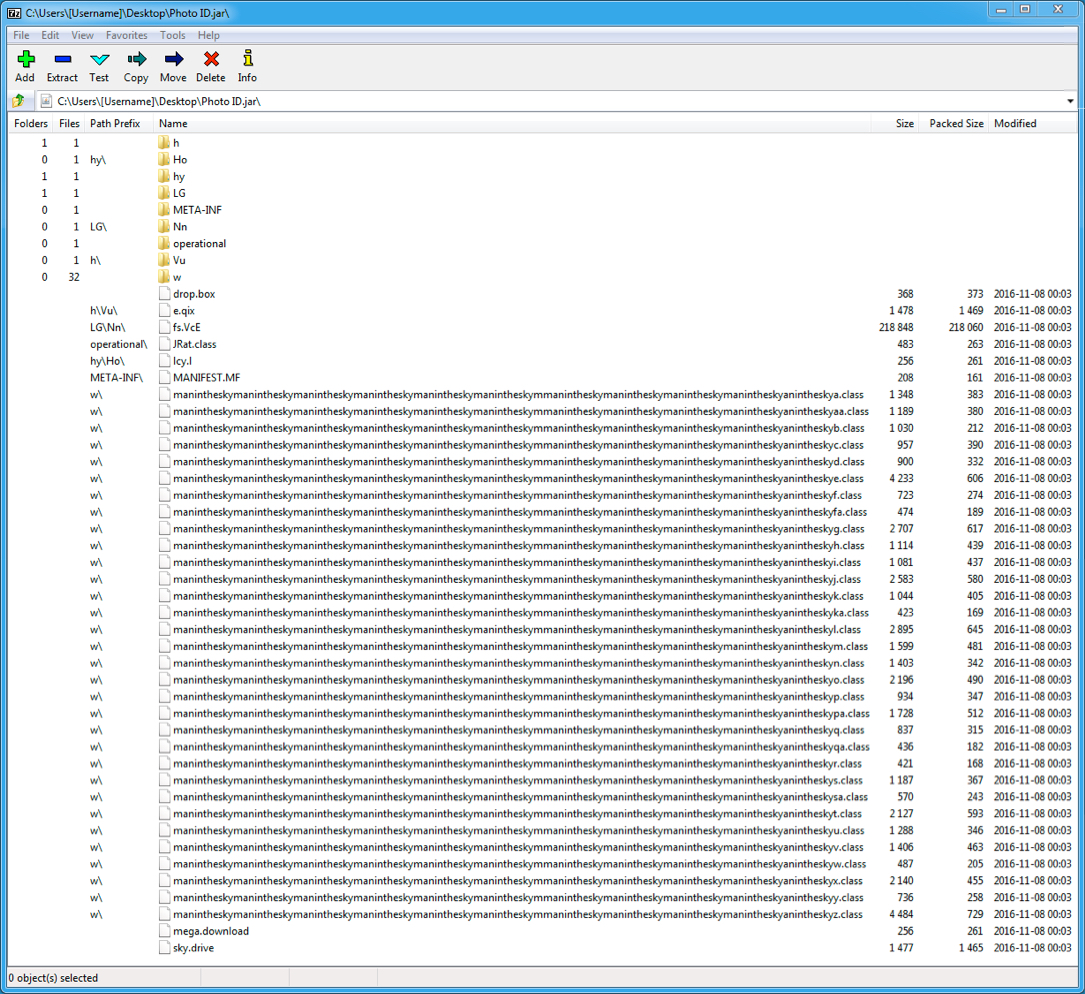
Shown above: Screenshot of one of the extracted .jar files (both are the same, with different names).
TRAFFIC
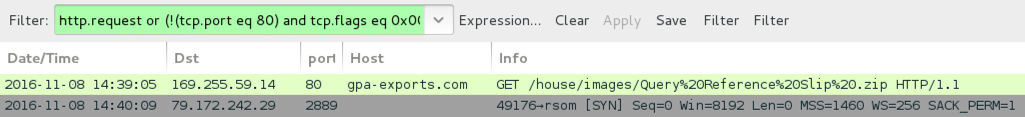
Shown above: Traffic from the pcap filtered in Wireshark.
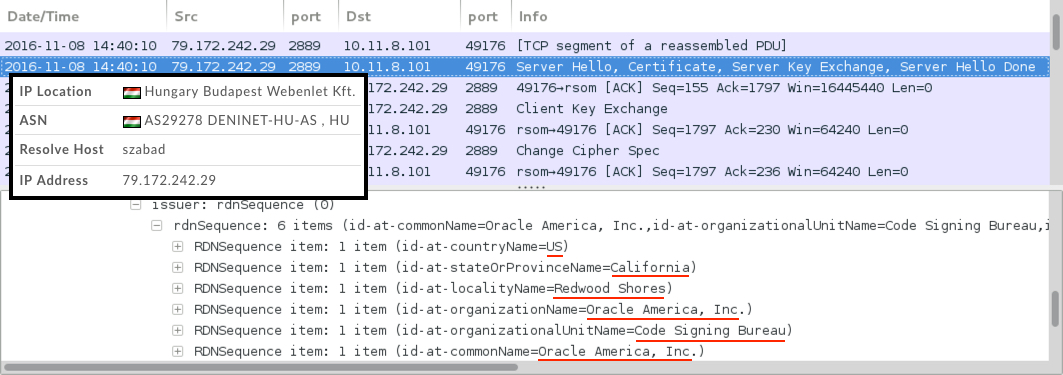
Shown above: A closer look at the certificate data from the HTTPS/SSL/TLS traffic on port 2889.
ASSOCIATED DOMAINS:
- 169.255.59[.]14 port 80 - gpa-exports[.]com - GET /house/images/Query%20Reference%20Slip%20.zip (download link from the email)
- 79.172.242[.]29 port 2889 - HTTPS/SSL/TLS post-infection traffic with self-signed certificate
FILE HASHES
DOWNLOADED ZIP ARCHIVE:
- SHA256: 665aadbfc60eae637df17a2c757468f24da1e65f98ad6ca6af67cdc146f7c19e
File name: Query Reference Slip .zip
File type: Zip archive (contains "Photo ID.jar" and "Query Transaction.jar")
THE EXTRACTED .JAR FILE(S):
- SHA256: eef94145397eade71a046ca8f42a8dec2475fcf54551e9a19dd4e59772a31710
File name: Photo ID.jar
File name: Query Transaction.jar
File name: C:\Users\[Username]\SXnTkXdhvAJ\nSlrfMRSMfa.jAtqpg
File type: Java/zip archive (.jar/.zip)
OTHER ARTIFACTS FROM THE INFECTED WINDOWS HOST:
- SHA256: 8fe4877c9b38ae637fdd1f025e31fa7a9dd33a4d350425bf7f44ac71c4e81b99
File name: C:\Users\[Username]\SXnTkXdhvAJ\JWUuwnDkC\pkKDftHgUY.NvMEa
File type: Java/zip archive (.jar/.zip)
- SHA256: a6be5be2d16a24430c795faa7ab7cc7826ed24d6d4bc74ad33da5c2ed0c793d0
File name: C:\Users\[Username]\AppData\Local\Temp\Windows6052555107978301025.dll
File type: DLL file
LIST OF ARTIFACTS ON THE INFECTED HOST:
- C:\Users\[Username]\SXnTkXdhvAJ\JWUuwnDkC\pkKDftHgUY.NvMEa
- C:\Users\[Username]\SXnTkXdhvAJ\ID.txt
- C:\Users\[Username]\SXnTkXdhvAJ\nSlrfMRSMfa.jAtqpg
- C:\Users\[Username]\AppData\Local\Temp\Windows6052555107978301025.dll
REGISTRY KEY UPDATED FOR PERSISTENCE:
- Registry Key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Value Name: SrgKtbhxDWu
- Value Type: REG_EXPAND_SZ
- Value Data: "C:\Users\[username]\AppData\Roaming\Oracle\bin\javaw.exe" -jar "C:\Users\[username]\SXnTkXdhvAJ\nSlrfMRSMfa.jAtqpg"
IMAGES
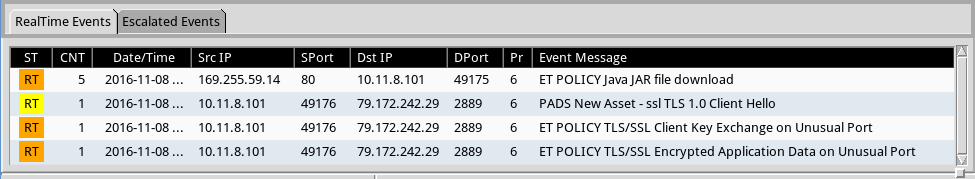
Shown above: Hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion.
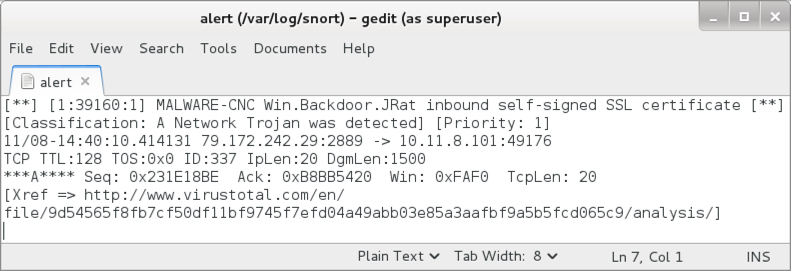
Shown above: Hits from Snort 2.9.8.3 using the Snort subscription ruleset.
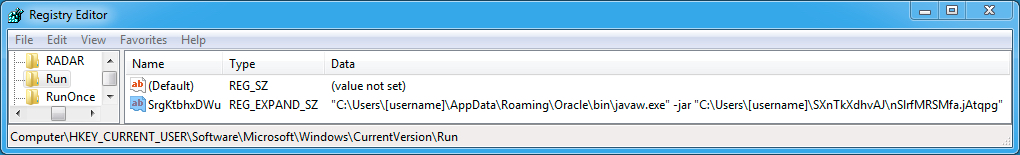
Shown above: Registry entry for persistence on an infected Windows host.
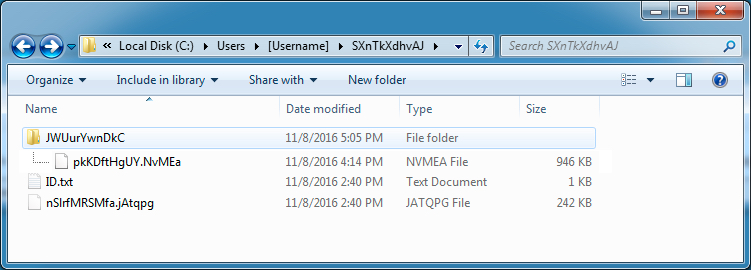
Shown above: Some fo the artifacts from an infected Windows host.
Click here to return to the main page.
