2016-11-16 - RIG EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-16-Rig-EK-data-dump-all-7-pcaps.zip 16.5 MB (16,467,765 bytes)
- 2016-11-16-1st-run-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (587,033 bytes)
- 2016-11-16-2nd-run-EITest-Rig-E-sends-Terdot.A-or-Zloader.pcap (6,926,217 bytes)
- 2016-11-16-3rd-run-EITest-Rig-E-sends-Quant-Loader.pcap (8,987,574 bytes)
- 2016-11-16-4th-run-EITest-Rig-standard-sends-CryptFile2-ransomware.pcap (170,733 bytes)
- 2016-11-16-6th-run-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (581,120 bytes)
- 2016-11-16-7th-run-EITest-Rig-E-sends-Cerber-ransomware.pcap (559,793 bytes)
- 2016-11-16-8th-run-EITest-Rig-E-sends-Qadars.pcap (771,317 bytes)
- 2016-11-16-Rig-EK-data-dump-malware-and-artifacts.zip 1.75 MB (1,750,907 bytes)
- 2016-11-16-1st-run-Rig-V-flash-exploit.swf (50,816 bytes)
- 2016-11-16-1st-run-Rig-V-landing-page.txt (5,209 bytes)
- 2016-11-16-1st-run-Rig-V-payload-Cerber-ransomware.exe (255,192 bytes)
- 2016-11-16-1st-run-page-from-joellipman_com-with-injected-pseudoDarkleech-script.txt (68,382 bytes)
- 2016-11-16-2nd-run-Rig-E-flash-exploit.swf (52,582 bytes)
- 2016-11-16-2nd-run-Rig-E-landing-page.txt (32,82 bytes)
- 2016-11-16-2nd-run-page-from-cavallinomotorsport_com-with-injected-EITest-script.txt (18,612 bytes)
- 2016-11-16-3rd-run-Rig-E-flash-exploit.swf (52,582 bytes)
- 2016-11-16-3rd-run-Rig-E-landing-page.txt (3,281 bytes)
- 2016-11-16-3rd-run-Rig-E-payload-Quant-Loader.exe (156,672 bytes)
- 2016-11-16-3rd-run-follow-up-malware.exe (434,176 bytes)
- 2016-11-16-3rd-run-page-from-cavallinomotorsport_com-with-injected-EITest-script.txt (18,597 bytes)
- 2016-11-16-4th-run-Rig-standard-flash-exploit.swf (48,722 bytes)
- 2016-11-16-4th-run-Rig-standard-landing-page.txt (3,140 bytes)
- 2016-11-16-4th-run-Rig-standard-payload-CryptFile2-ransomware.exe (80,896 bytes)
- 2016-11-16-6th-run-Rig-V-flash-exploit.swf (50,816 bytes)
- 2016-11-16-6th-run-Rig-V-landing-page.txt (5,179 bytes)
- 2016-11-16-6th-run-Rig-V-payload-Cerber-ransomware.exe (237,902 bytes)
- 2016-11-16-6th-run-page-from-wordtemplates_org-with-injected-pseudoDarkleech-script.txt (54,199 bytes)
- 2016-11-16-7th-run-Rig-E-flash-exploit.swf (52,582 bytes)
- 2016-11-16-7th-run-Rig-E-landing-page.txt (3,278 bytes)
- 2016-11-16-7th-run-Rig-E-payload-Cerber-ransomware.exe (266,430 bytes)
- 2016-11-16-7th-run-page-from-cavallinomotorsport_com-with-injected-EITest-script.txt (18,603 bytes)
- 2016-11-16-8th-run-Rig-E-flash-exploit.swf (52,582 bytes)
- 2016-11-16-8th-run-Rig-E-landing-page.txt (3,283 bytes)
- 2016-11-16-8th-run-Rig-E-payload-Qadars.exe (343,552 bytes)
- 2016-11-16-8th-run-page-from-cavallinomotorsport_com-with-injected-EITest-script.txt (18,613 bytes)
NOTES:
- I'm currently tracking 3 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns and RC4 encryption for the payload. Used by the Afraidgate, EITest, and pseudoDarkleech campaigns.
- Rig-E: a variant with old URL patterns, but uses with RC4 encryption for the payload. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
- Rig standard: a standard version (like Rig-E) but uses new URL patterns introduced by Rig-V. The EITest campaign uses Rig standard to send CryptFile2 ransomware.
- Thanks to the person who emailed me about the compromised site wordtemplates[.]org. It had injected psuedoDarkleech campaign that I used for the 6th run.
- I made a mistake getting the malware payload from the infected host during the 2nd run (and I couldn't extract the binary from the pcap), so it's not included in the malware archive.
- During the 5th run, I saw Sundown EK from the EITest campaign, so that's in a separate blog post (link).
TRAFFIC
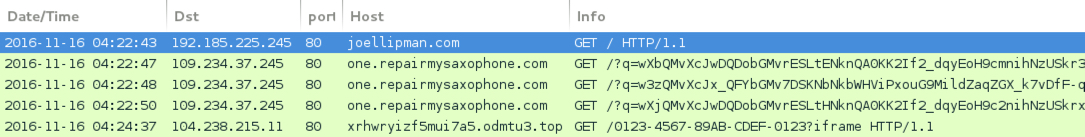
Shown above: Traffic from the 1st run in Wireshark.
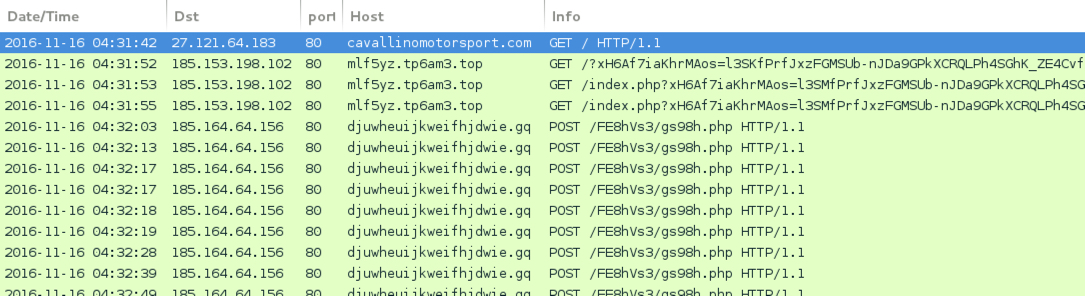
Shown above: Traffic from the 2nd run in Wireshark.
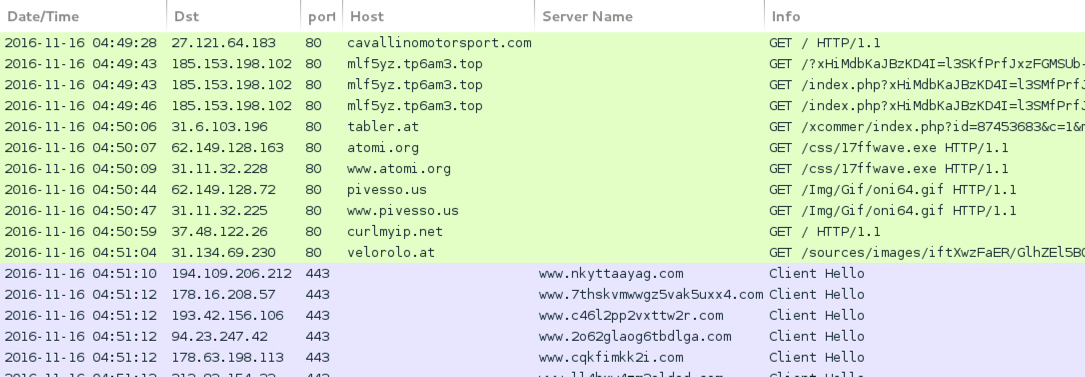
Shown above: Traffic from the 3rd run in Wireshark.
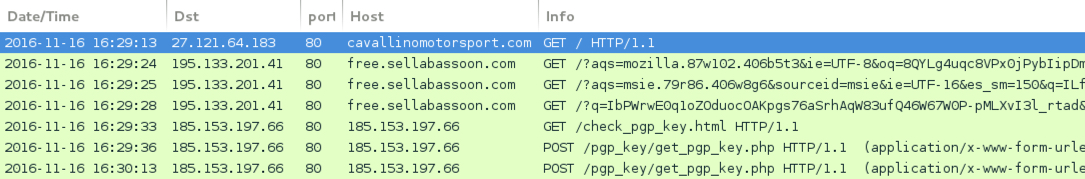
Shown above: Traffic from the 4th run in Wireshark.
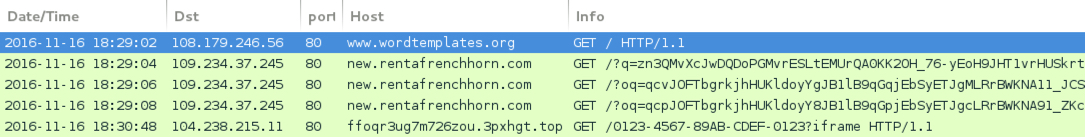
Shown above: Traffic from the 6th run in Wireshark.
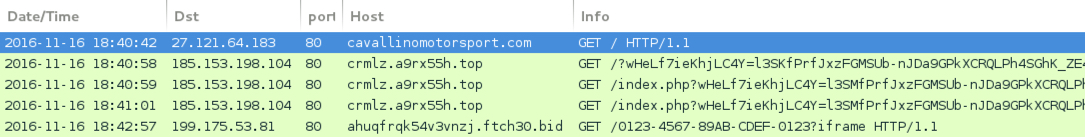
Shown above: Traffic from the 7th run in Wireshark.
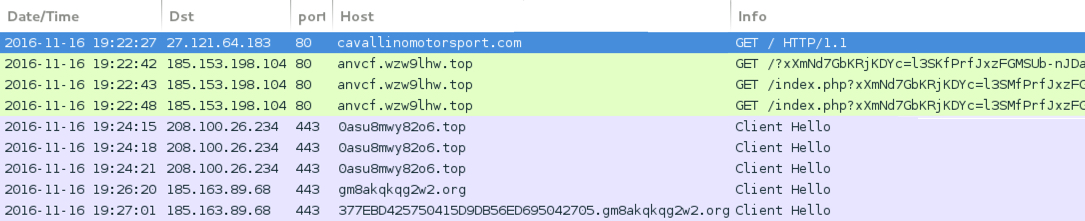
Shown above: Traffic from the 8th run in Wireshark.
ASSOCIATED DOMAINS:
- 109.234.37[.]245 - new.rentafrenchhorn[.]com - Rig-V (6th run)
- 109.234.37[.]245 - one.repairmysaxophone[.]com - Rig-V (1st run)
- 185.153.198[.]102 - mlf5yz.tp6am3[.]top - Rig-E (2nd & 3d runs)
- 185.153.198[.]104 - anvcf.wzw9lhw[.]top - Rig-E (8th run)
- 185.153.198[.]104 - crmlz.a9rx55h[.]top - Rig-E (7th run)
- 195.133.201[.]41 - free.sellabassoon[.]com - Rig standard (4th run)
- NOTE: You'll need to review the pcaps for compromised webwsites, post-infection traffic and other details.
FILE HASHES
FLASH EXPLOITS:
- 1613acd34bfb85121bef0cd7a5cc572967912f9f674eefd7175f42ad2099e3d1 - 2016-11-16-2nd-run-Rig-E-flash-exploit.swf
- 1613acd34bfb85121bef0cd7a5cc572967912f9f674eefd7175f42ad2099e3d1 - 2016-11-16-3rd-run-Rig-E-flash-exploit.swf
- 1613acd34bfb85121bef0cd7a5cc572967912f9f674eefd7175f42ad2099e3d1 - 2016-11-16-7th-run-Rig-E-flash-exploit.swf
- 1613acd34bfb85121bef0cd7a5cc572967912f9f674eefd7175f42ad2099e3d1 - 2016-11-16-8th-run-Rig-E-flash-exploit.swf
- f33cf0ec177338f7d583b47ac4e127e44d1fa7322111db523bb4ecd6c393374f - 2016-11-16-4th-run-Rig-standard-flash-exploit.swf
- aa7abfeea6ff997809bd495ee636cb44cc8e8a0ec3264b7eb87924bbde762485 - 2016-11-16-1st-run-Rig-V-flash-exploit.swf
- aa7abfeea6ff997809bd495ee636cb44cc8e8a0ec3264b7eb87924bbde762485 - 2016-11-16-6th-run-Rig-V-flash-exploit.swf
PAYLOADS (READ: SHA256 HASH - FILE NAME):
- 6e9b7a01702334ec9cb4c3d1e81e34cf156b30b8a8db2eb54ea43aea9c2b07ff - 2016-11-16-1st-run-Rig-V-payload-Cerber-ransomware.exe
- 8cf20a0953c701b826b4c949ccc7d99d2214db3f3051d0512433bf0ed1057c4d - 2016-11-16-3rd-run-Rig-E-payload-Quant-Loader.exe
- 88f12cf66117c119a0d7bea104df7549dcc2c10a23ae79883d43bed333266646 - 2016-11-16-3rd-run-follow-up-malware.exe
- 4b447266bd7a130c5b27c9ec4bd68a9ebf731a4ce0300702f41b37da1d6384ef - 2016-11-16-4th-run-Rig-standard-payload-CryptFile2-ransomware.exe
- 97a5181dd9951669cb934b5437f4cc9a3cc49facec3f73a3aeaec084f14722e7 - 2016-11-16-6th-run-Rig-V-payload-Cerber-ransomware.exe
- 994ad16fc0699d26bc07fd2463a3238db90d23978b044bfb9f51d1ea955c6073 - 2016-11-16-7th-run-Rig-E-payload-Cerber-ransomware.exe
- 5ff5e7b025ae7f67d1b20cb1d9e821bcd77d07378a55022c9d52ce1f2432bfd6 - 2016-11-16-8th-run-Rig-E-payload-Qadars.exe
Click here to return to the main page.
