2016-11-21 - "AESIR" VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-21-Locky-ransomware-data.zip 1.6 MB (1,624,829 bytes)
- 2016-11-21-Locky-ransomware-tracker.csv (7,045 bytes)
- 2016-11-21-Locky-ransomware-infection-traffic.pcap (338,107 bytes)
- files-from-infected-hosts / 2016-11-21-Locky-ransomware-DLL-sample.dll (286,720 bytes)
- files-from-infected-hosts / 2016-11-21-Locky-ransomware-Decryptor-style.css (3,602 bytes)
- files-from-infected-hosts / 2016-11-21-Locky-ransomware-Decryptor.htm (6,569 bytes)
- files-from-infected-hosts / 2016-11-21-Locky-ransomware-decryption-instructions-INSTRUCTION.html (8,257 bytes)
- files-from-infected-hosts / 2016-11-21-Locky-ransomware-decryption-instructions-INSTRUCTION.jpg (804,526 bytes)
- attachments / ORDER-050-8378457-6432583.zip (7,613 bytes)
- attachments / ORDER-164-1897058-5410357.zip (7,638 bytes)
- attachments / ORDER-210-2356200-4106706.zip (7,631 bytes)
- attachments / ORDER-269-4312087-7600497.zip (7,602 bytes)
- attachments / ORDER-291-2608445-1000757.zip (7,623 bytes)
- attachments / ORDER-478-9353190-9763851.zip (7,635 bytes)
- attachments / ORDER-614-0205103-8611455.zip (7,607 bytes)
- attachments / ORDER-660-0384203-6833726.zip (7,622 bytes)
- attachments / ORDER-661-0378261-3171277.zip (7,633 bytes)
- attachments / ORDER-860-8499201-7275519.zip (7,637 bytes)
- attachments / pm09BA8F5.zip (7,623 bytes)
- attachments / pm589EC21.zip (7,615 bytes)
- attachments / pm648504.zip (7,603 bytes)
- attachments / pm6D72C.zip (7,623 bytes)
- attachments / pm85CD0.zip (7,667 bytes)
- attachments / pmAA0.zip (7,658 bytes)
- attachments / pmCA3F.zip (7,624 bytes)
- attachments / pmED847.zip (7,598 bytes)
- attachments / pmFB2.zip (7,603 bytes)
- attachments / pmFEB84D74.zip (7,617 bytes)
- emails / 2016-11-21-0904-UTC.eml (12,063 bytes)
- emails / 2016-11-21-0905-UTC.eml (12,052 bytes)
- emails / 2016-11-21-0906-UTC.eml (12,070 bytes)
- emails / 2016-11-21-0907-UTC.eml (12,043 bytes)
- emails / 2016-11-21-0912-UTC.eml (12,043 bytes)
- emails / 2016-11-21-0917-UTC.eml (12,118 bytes)
- emails / 2016-11-21-0922-UTC.eml (12,052 bytes)
- emails / 2016-11-21-0925-UTC.eml (12,037 bytes)
- emails / 2016-11-21-0929-UTC.eml (12,124 bytes)
- emails / 2016-11-21-0931-UTC.eml (12,047 bytes)
- emails / 2016-11-21-0935-UTC.eml (11,810 bytes)
- emails / 2016-11-21-0937-UTC.eml (11,771 bytes)
- emails / 2016-11-21-0938-UTC.eml (11,798 bytes)
- emails / 2016-11-21-0942-UTC.eml (11,793 bytes)
- emails / 2016-11-21-0955-UTC.eml (11,775 bytes)
- emails / 2016-11-21-1012-UTC.eml (11,773 bytes)
- emails / 2016-11-21-1018-UTC.eml (11,788 bytes)
- emails / 2016-11-21-1020-UTC.eml (11,773 bytes)
- emails / 2016-11-21-1032-UTC.eml (11,753 bytes)
- emails / 2016-11-21-1035-UTC.eml (11,736 bytes)
- extracted-files / BYDICK290731.js (25,445 bytes)
- extracted-files / DYXULJ871830.js (25,118 bytes)
- extracted-files / FBBNL821441.js (25,448 bytes)
- extracted-files / FPORUT712221.js (25,738 bytes)
- extracted-files / HDXWS173226.js (25,448 bytes)
- extracted-files / JVCKEE503541.js (25,095 bytes)
- extracted-files / JXWOS353240.js (26,653 bytes)
- extracted-files / NNVVB261314.js (25,400 bytes)
- extracted-files / NTTVY562239.js (25,469 bytes)
- extracted-files / OBMFOR383123.js (25,148 bytes)
- extracted-files / OSLELN972414.js (26,401 bytes)
- extracted-files / PSBLD450107.js (25,437 bytes)
- extracted-files / UXKZF552145.js (25,144 bytes)
- extracted-files / WXVAQF951210.js (25,459 bytes)
- extracted-files / XHSEU550740.js (26,384 bytes)
- extracted-files / XXWHA143018.js (25,708 bytes)
- extracted-files / YHIOE303045.js (26,652 bytes)
- extracted-files / YKULQ123727.js (26,657 bytes)
NOTES:
- Today, I noticed Locky ransomware using .aesir as a file extension for the files it encrypts.
- This has already been blogged about by My Online Security (link), Bleeping Computer (link), and likely several others by the time you read this.
- All attachments from the 2 waves of malspam I saw delivered the same Locky ransomware DLL file.
- The entry point for today's Locky ransomware DLL sample is kokoko in case anyone wants to run it with rundll32.exe in a controlled environment.
Shown above: Locky's authors are sticking with Norse mythology for the file extension name.
EMAILS
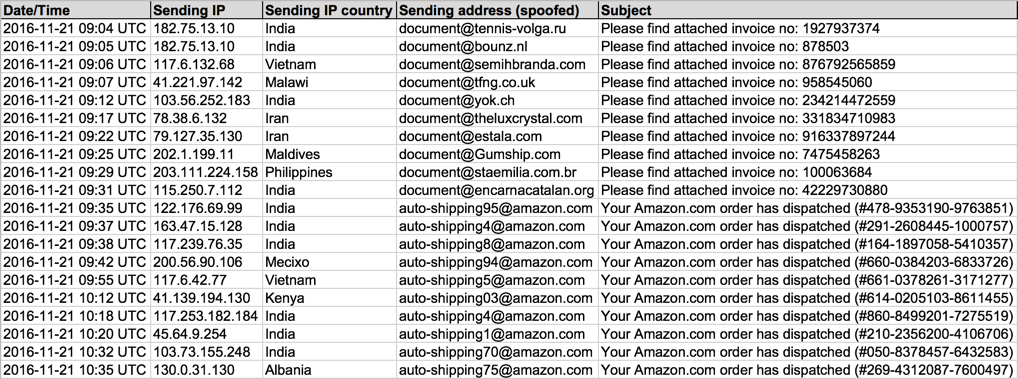
Shown above: Data from 20 emails pushing Locky ransomware (part 1 of 2).
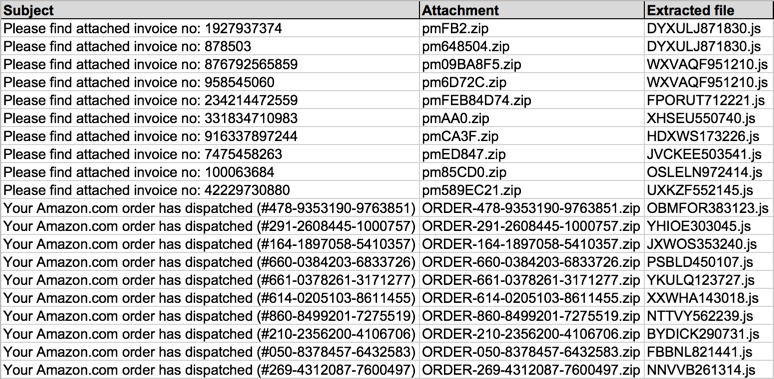
Shown above: Data from 20 emails pushing Locky ransomware (part 2 of 2).
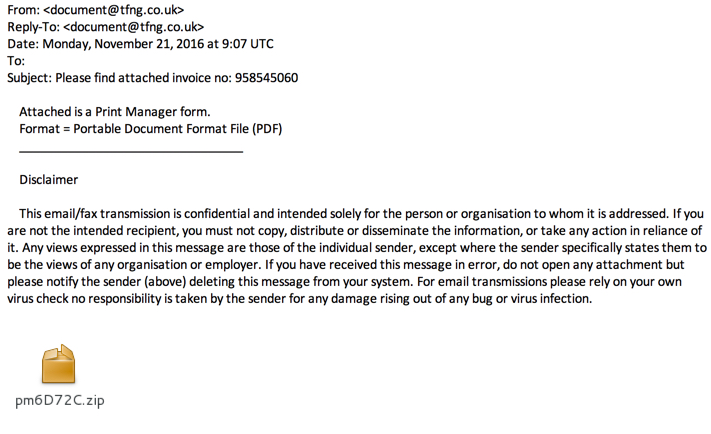
Shown above: An example from the first wave of these emails.
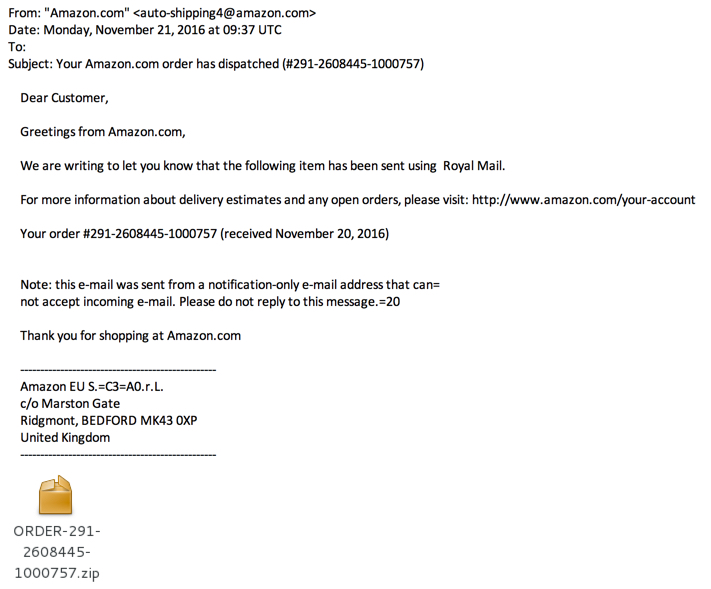
Shown above: An example from second wve of these emails.
TRAFFIC
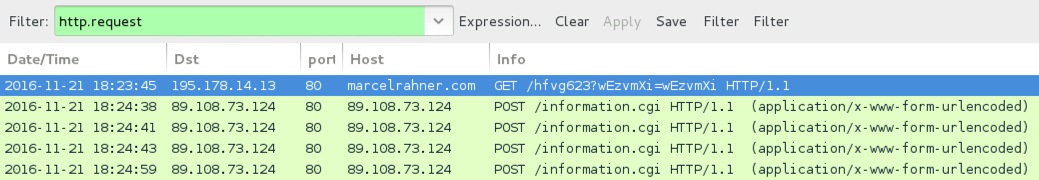
Shown above: An example of infection traffic from one of the emails.
TRAFFIC GENERATED FROM THE EXTRACTED .JS SCRIPTS:
- 195.178.14[.]13 port 80 - marcelrahner[.]com - GET /hfvg623?wEzvmXi=wEzvmXi
- 198.204.227[.]250 port 80 - hotelsheikhpalace[.]com - GET /hfvg623?hwOhxBPYb=hwOhxBPYb
- 86.57.246[.]177 port 80 - ayurvedic[.]by - GET /hfvg623?ELrHopNfUtm=ELrHopNfUtm
- 210.16.189[.]97 port 80 - job0916[.]cn - GET /hfvg623?ELrHopNfUtm=ELrHopNfUtm
- 46.45.178[.]123 port 80 - kemerhaber[.]net - GET /hfvg623?RyHWVDrWDmO=RyHWVDrWDmO
- 174.120.70[.]137 port 80 - kppngarut[.]org - GET /hfvg623?jcdzzYbMT=jcdzzYbMT
- 103.254.151[.]60 port 80 - jltl[.]net - GET /hfvg623?dqarJd=dqarJd
- 107.180.13[.]247 port 80 - joshcomeauxhair[.]com - GET /hfvg623?dqarJd=dqarJd
- 174.120.70[.]137 port 80 - kppngarut[.]org - GET /hfvg623?fQGKpcfi=fQGKpcfi
- 174.136.29[.]130 port 80 - librosinculpa[.]com[.]ar - GET /hfvg623?UQvVqrcsUOb=UQvVqrcsUOb
- 5.9.80[.]136 port 80 - kirillpryadukhin[.]ru - GET /hfvg623?UQvVqrcsUOb=UQvVqrcsUOb
- 116.255.195[.]133 port 80 - kailijiazu[.]com - GET /hfvg623?UQvVqrcsUOb=UQvVqrcsUOb
- 41.77.112[.]55 port 80 - majesticimmo[.]com - GET /hfvg623?LhIbrmNl=LhIbrmNl
- 89.42.218[.]173 port 80 - icdsarch[.]com - GET /hfvg623?RowFlyu=RowFlyu
- 87.106.145[.]10 port 80 - decorvise[.]com - GET /hfvg623?vSJvUwhn=vSJvUwhn
- 141.138.151[.]121 port 80 - innovationcircle[.]com - GET /hfvg623?bURJdJt=bURJdJt
- 94.23.224[.]52 port 80 - kahane[.]fr - GET /hfvg623?pdUHseI=pdUHseI
- 103.254.151[.]60 port 80 - jltl[.]net - GET /hfvg623?aEenAXMm=aEenAXMm
- 107.180.13[.]247 port 80 - joshcomeauxhair[.]com - GET /hfvg623?aEenAXMm=aEenAXMm
- 59.188.236[.]52 port 80 - jjbook[.]net - GET /hfvg623?KxyHPvYh=KxyHPvYh
- 141.138.151[.]121 port 80 - innovationcircle[.]com - GET /hfvg623?gxFDoV=gxFDoV
- 5.9.80[.]136 port 80 - kirillpryadukhin[.]ru - GET /hfvg623?eEIJRj=eEIJRj
- 178.159.242[.]82 port 80 - kubstroy[.]by - GET /hfvg623?eEIJRj=eEIJRj
- 5.9.80[.]136 port 80 - kirillpryadukhin[.]ru - GET /hfvg623?LpxIiO=LpxIiO
- 178.159.242[.]82 port 80 - kubstroy[.]by - GET /hfvg623?LpxIiO=LpxIiO
POST-INFECTION CALLBACK FROM THE LOCKY RANSOMWARE SAMPLE:
- 89.108.73[.]124 port 80 - 89.108.73[.]124 - POST /information.cgi
- 91.211.119[.]98 port 80 - 91.211.119[.]98 - POST /information.cgi
- 69.195.129[.]70 port 80 - uuvuhqhnwnpdy[.]org - POST /information.cgi
TOR DOMAIN FROM THE DECRYPTION INSTRUCTIONS:
- mwddgguaa5rj7b54[.]onion
FILE HASHES
LOCKY RANSOMWARE DLL SAMPLE:
- SHA256 hash: ff4a021e6175e5f2c0a666270081d74991c69e651c249a6fdf82a004dd9215e5
File name: C:\Users\[username]\AppData\Local\Temp\[random characters].dll (303,104 bytes)
IMAGES
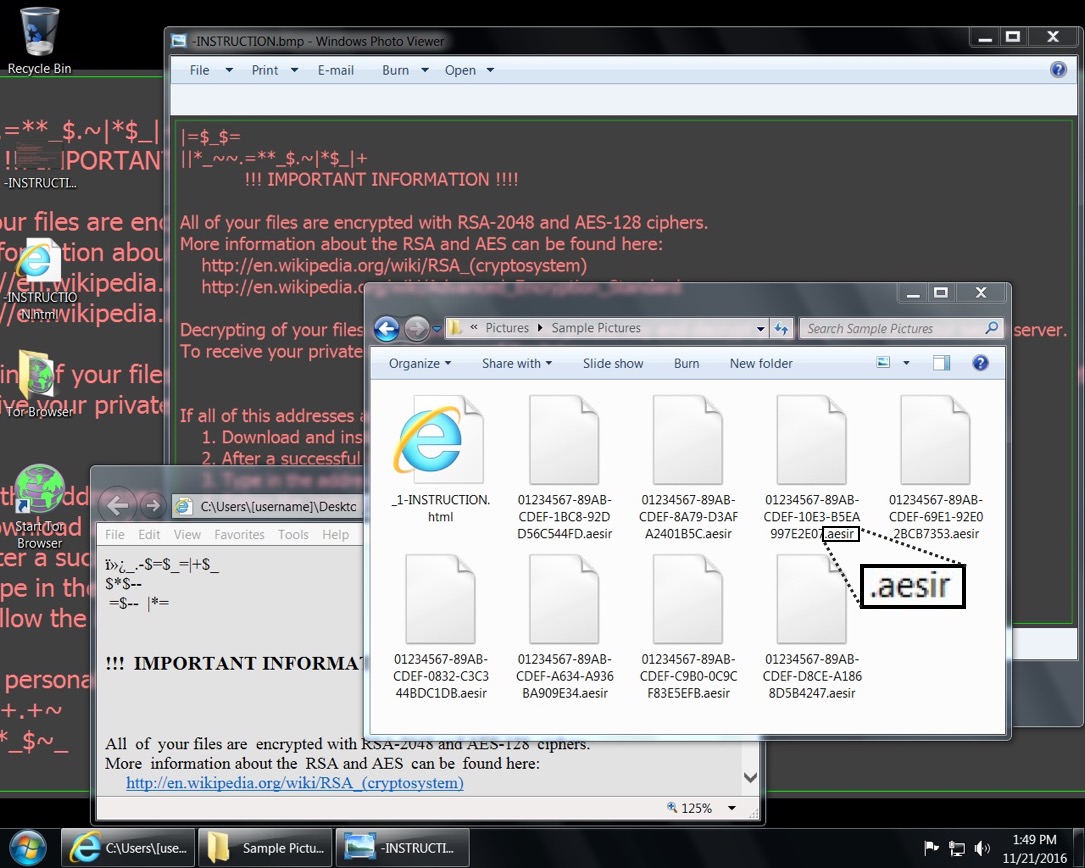
Shown above: Screen shot from an infected Windows desktop. Note the .aesir file extension.
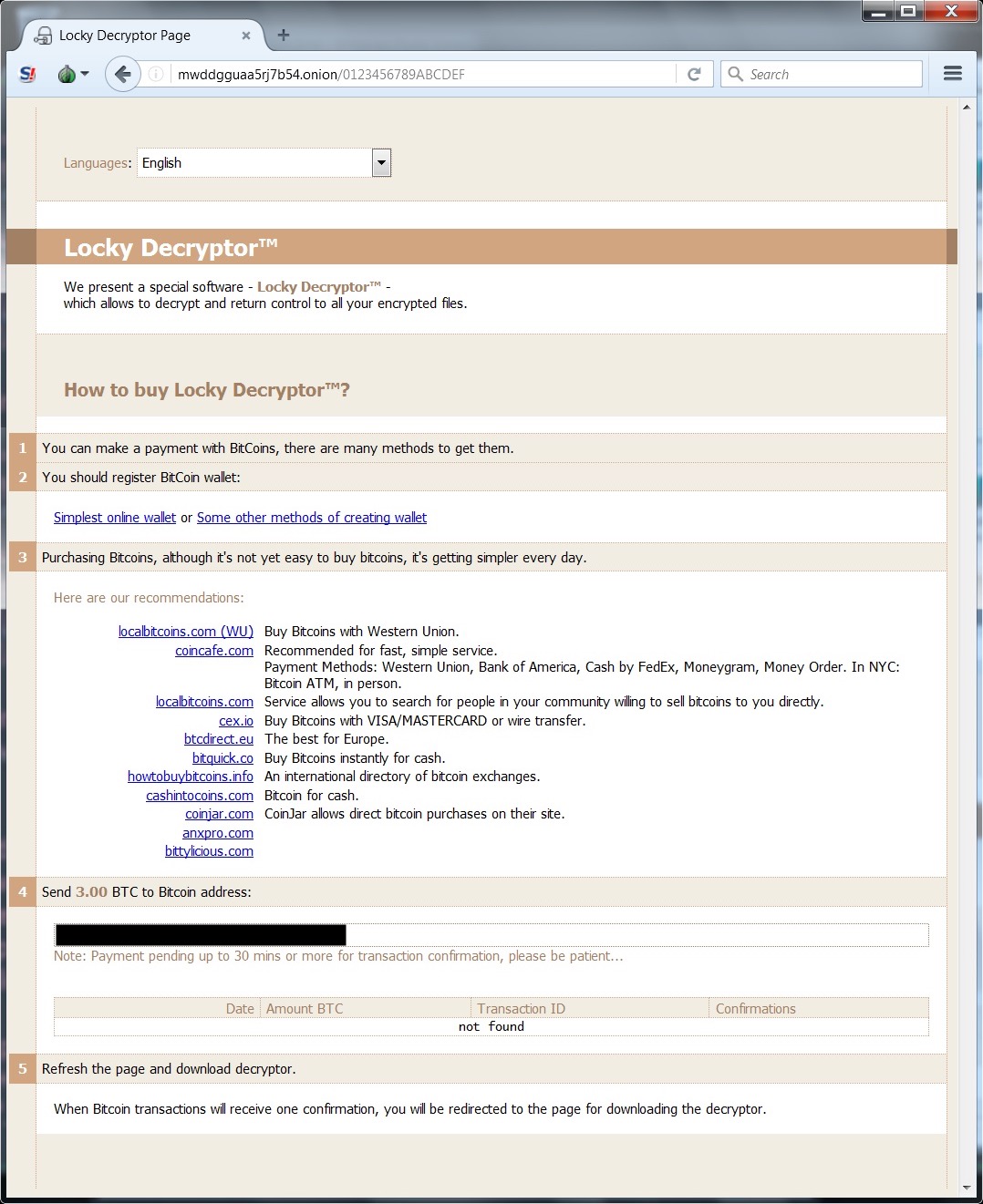
Shown above: Ransom payment was 3.0 bitcoin for the infections I generated.
Click here to return to the main page.