2016-11-21 - RIG EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-21-Rig-EK-data-dump-all-4-pcaps.zip 9.8 MB (9,760,489 bytes)
- 2016-11-21-1st-run-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (677,745 bytes)
- 2016-11-21-2nd-run-EITest-Rig-standard-sends-CryptFile2-ransomware.pcap (260,984 bytes)
- 2016-11-21-3rd-run-EITest-Rig-E-traffic.pcap (627,307 bytes)
- 2016-11-21-bonus-run-EITest-Rig-E-traffic.pcap (9,235,297 bytes)
- 2016-11-21-Rig-EK-data-dump-malware-and-artifacts.zip 1.24 MB (1,243,580 bytes)
- 2016-11-21-1st-run-Cerber-ransomware-decryption-instructions-README.hta (67,713 bytes)
- 2016-11-21-1st-run-Cerber-ransomware-decryption-instructions.bmp (1,920,054 bytes)
- 2016-11-21-1st-run-page-from-wordtemplates_org-with-injected-script.txt (54,472 bytes)
- 2016-11-21-1st-run-pseudoDarkleech-Rig-V-flash-exploit.swf (40,141 bytes)
- 2016-11-21-1st-run-pseudoDarkleech-Rig-V-landing-page.txt (5,181 bytes)
- 2016-11-21-1st-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware.exe (334,837 bytes)
- 2016-11-21-2nd-run-CryptFile2-ransomware-decryption-instructions.txt (3,221 bytes)
- 2016-11-21-2nd-run-EITest-Rig-standard-flash-exploit.swf (39,147 bytes)
- 2016-11-21-2nd-run-EITest-Rig-standard-landing-page.txt (20,879 bytes)
- 2016-11-21-2nd-run-EITest-Rig-standard-payload-CryptFile2-ransomware.exe (83,456 bytes)
- 2016-11-21-2nd-run-page-from-cavallinomotorsport_com-with-injected-script.txt (18,816 bytes)
- 2016-11-21-3rd-run-EITest-Rig-E-flash-exploit.swf (40,141 bytes)
- 2016-11-21-3rd-run-EITest-Rig-E-landing-page.txt (85,248 bytes)
- 2016-11-21-3rd-run-EITest-Rig-E-payload.exe (249,856 bytes)
- 2016-11-21-3rd-run-EITest-Rig-E-post-infection-scheduled-task.xml.txt (3,188 bytes)
- 2016-11-21-3rd-run-page-from-cavallinomotorsport_com-with-injected-script.txt (18,796 bytes)
- 2016-11-21-bonus-run-EITest-Rig-E-flash-exploit.swf (40,141 bytes)
- 2016-11-21-bonus-run-EITest-Rig-E-landing-page.txt (85,259 bytes)
- 2016-11-21-bonus-run-follow-up-malware-oimy6bc2h16.exe (276,544 bytes)
BACKGROUND:
- I'm currently tracking 3 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns and RC4 encryption for the payload. Used by the Afraidgate, EITest, and pseudoDarkleech campaigns.
- Rig-E: a variant with old URL patterns, but uses with RC4 encryption for the payload. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
- Rig standard: uses new URL patterns introduced by Rig-V, but old obfuscation (ASCII string to XOR the payload binary). The EITest campaign uses Rig standard to send CryptFile2 ransomware.
NOTES:
- I'm going to see how long I can keep using cavallinomotorsport[.]com and wordtemplates[.]org (and probably joellipman[.]com) to kick off Rig EK infection chains.
- I figure at some point someone will fix those compromised websites, or at least wonder why they are on so many blacklists.
- I forgot to retrieve any files from the infected Windows host in the "bonus run," but there was too much good info not to include the pcap in this blog post.
- Any artifacts from the bonus run were extracted from the pcap, except for the follow-up executable, which I downloaded using curl and the proper user-agent string.
TRAFFIC
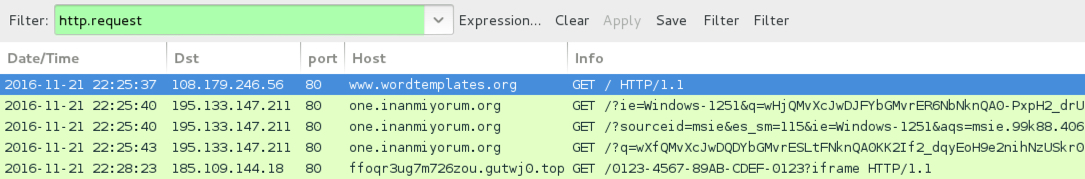
Shown above: Traffic from the 1st infection filtered in Wireshark.
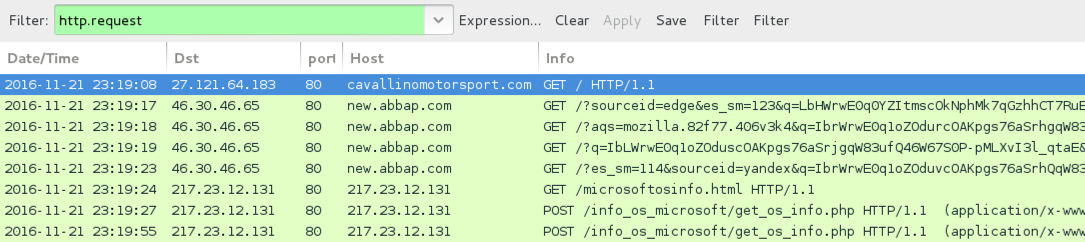
Shown above: Traffic from the 2nd infection filtered in Wireshark.

Shown above: Traffic from the 3rdd infection filtered in Wireshark.

Shown above: Traffic from the bonus infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 195.133.147[.]211 port 80 - one.inanmiyorum[.]org - Rig-V from the 1st run
- 46.30.46[.]65 port 80 - new.abbap[.]com - Rig standard from the 2nd run
- 185.153.198[.]121 port 80 - fw324.kzxi10n[.]top - Rig-E from the 3rd run
- 174.128.251[.]4 port 80 - k9x6.akkazrrvw[.]top - Rig-E from the bonus run
- 185.109.144[.]18 port 80 - ffoqr3ug7m726zou.gutwj0[.]top - Cerber ransomware post-infection traffic from the 1st run
- 65.55.50[.]0 - 65.55.50[.]31 (65.55.50[.]0/27) port 6892 - UDP traffic caused by Cerber ransomware from the 1st run
- 192.42.118[.]0 - 192.42.118[.]31 (192.42.118[.]0/27)port 6892 - UDP traffic caused by Cerber ransomware the 1st run
- 194.165.16[.]0 - 194.165.16[.]255 (194.165.16[.]0/22) port 6892 - UDP traffic caused by Cerber ransomware from the 1st run
- 217.23.12[.]131 port 80 - 217.23.12[.]131 - Cryptfile2 ransomware post-infection traffic from the 2nd run
- 81.4.108[.]169 port 80 - vitaetortorvitaesuscipit[.]us - Post-infection traffic from the bonus run
- 217.160.34[.]53 port 80 - hotel-orsoni[.]com - Post-infection traffic from the bonus run
- 62.149.140[.]138 port 80 - www.artkar[.]it - Post-infection traffic from the bonus run
- various IP addresses - various ports - various domains - Tor traffic from the bonus run
- 93.77.61[.]228 port 80 - hip1000[.]at - Post-infection traffic from the bonus run
FILE HASHES
FLASH EXPLOITS:
- b73dd34e63a001b3be1e809c889df4a075162891034404e4d344d7cfafb1bc0e - 2016-11-21-1st-run-pseudoDarkleech-Rig-V-flash-exploit.swf
- 8794626ca0160b5be2965240fdfd05d0c4818d6f72a4ddffbc7a6f48c0460094 - 2016-11-21-2nd-run-EITest-Rig-standard-flash-exploit.swf
- b73dd34e63a001b3be1e809c889df4a075162891034404e4d344d7cfafb1bc0e - 2016-11-21-3rd-run-EITest-Rig-E-flash-exploit.swf
- b73dd34e63a001b3be1e809c889df4a075162891034404e4d344d7cfafb1bc0e - 2016-11-21-bonus-run-EITest-Rig-E-flash-exploit.swf
PAYLOADS AND FOLLOW-UP MALWARE:
- 7ab41b73e13f67d5f7139e5ebb168330c65f9b8c96c9ccfdd5565aab8ec9174e - 2016-11-21-1st-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware.exe
- f2dbf29985a759e73c6a515422e218e6b0a1a844a327917428a1f9a1248f2320 - 2016-11-21-2nd-run-EITest-Rig-standard-payload-CryptFile2-ransomware.exe
- 8caa41e58eb33ab479bd06ef0d933fb36b3c6dd8b567df2bc1f508ce4df7f7df - 2016-11-21-3rd-run-EITest-Rig-E-payload.exe
- ae0f6699fc56fcc81904380a4091d8ceca02eeb5890e6bc5081aa39d69fb66d5 - 2016-11-21-bonus-run-follow-up-malware-oimy6bc2h16.exe
Click here to return to the main page.
