2016-11-23 - RIG EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
BACKGROUND:
- I'm currently tracking 3 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns and RC4 encryption for the payload. Used by the Afraidgate, EITest, and pseudoDarkleech campaigns.
- Rig-E: a variant with old URL patterns, but uses with RC4 encryption for the payload. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
- Rig standard: uses new URL patterns introduced by Rig-V, but old obfuscation (ASCII string to XOR the payload binary) The EITest campaign uses Rig standard to send CryptFile2 ransomware.
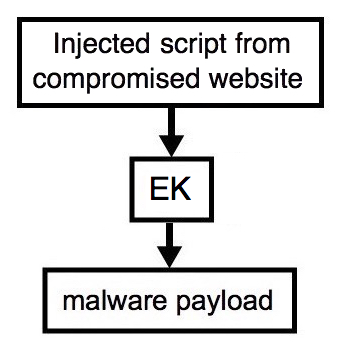
Shown above: Flowchart for today's infections.
TRAFFIC
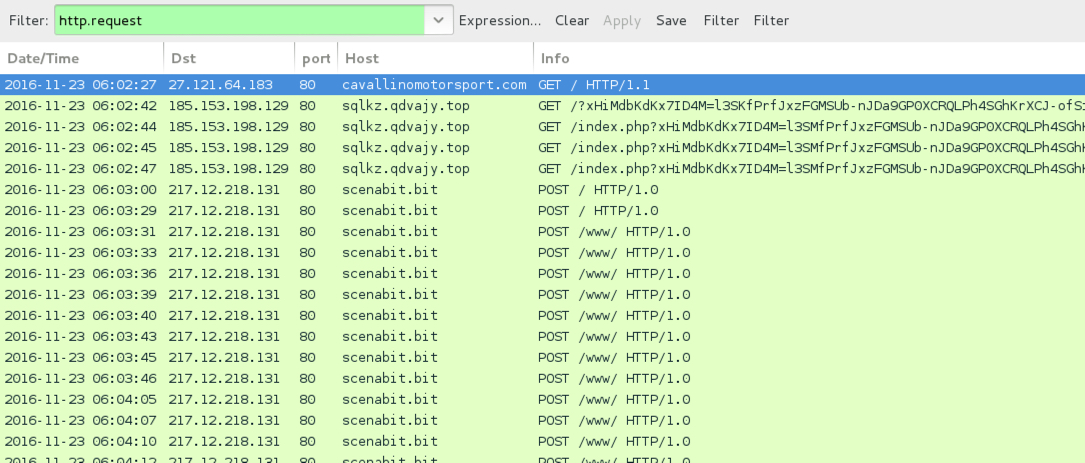
Shown above: Traffic from the 1st infection filtered in Wireshark.
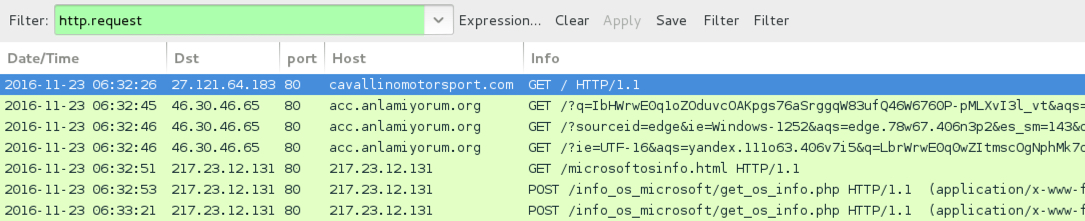
Shown above: Traffic from the 2nd infection filtered in Wireshark.
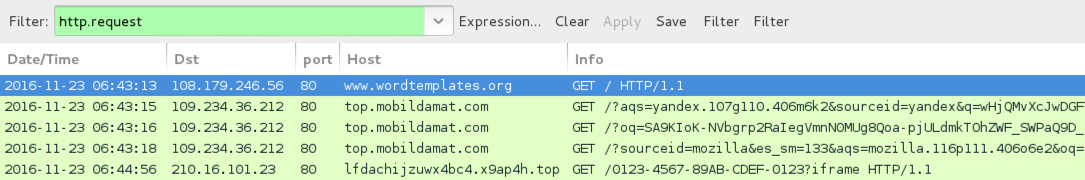
Shown above: Traffic from the 3rd infection filtered in Wireshark.
Click here to return to the main page.