2016-11-28 - MALWARE INFECTION FROM BRAZILIAN EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-28-infection-traffic-from-Brazilian-email.pcap.zip 8.8 MB (8,756,638 bytes)
- 2016-11-28-infection-traffic-from-Brazilian-email.pcap (9,466,579 bytes)
- 2016-11-28-files-from-infection-through-Brazilian-email.zip 7.4 MB (7,448,186 bytes)
- 2016-11-28-0427-UTC.eml (7,103 bytes)
- AN_COBRANCA-.js (9,903 bytes)
- rsd1-from-rsdw1.plu.DLL (5,064,192 bytes)
- rsd1-from-rsdy1.plu.DAT (3,113,985 bytes)
- rsd2-from-rsdw2.plu.DLL (6,011,904 bytes)
- rsd2-from-rsdy2.plu.DLL (3,612,160 bytes)
- rsd4-from-rsdy4.plu.DLL (571,904 bytes)
THE EMAIL
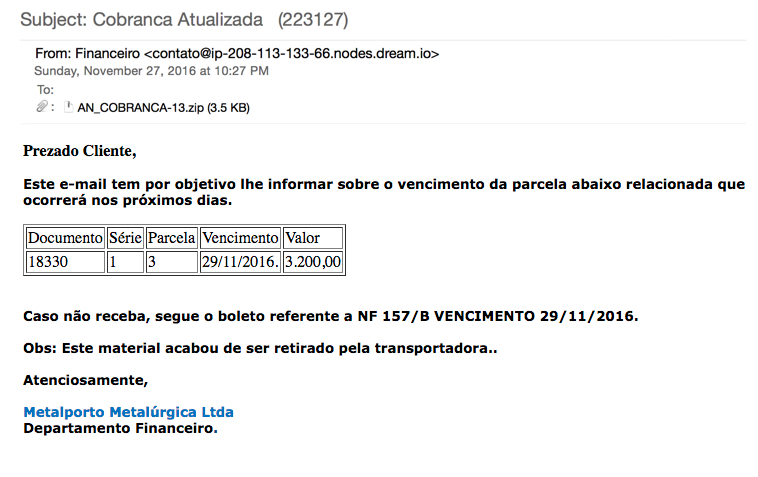
Shown above: Screenshot of the email.
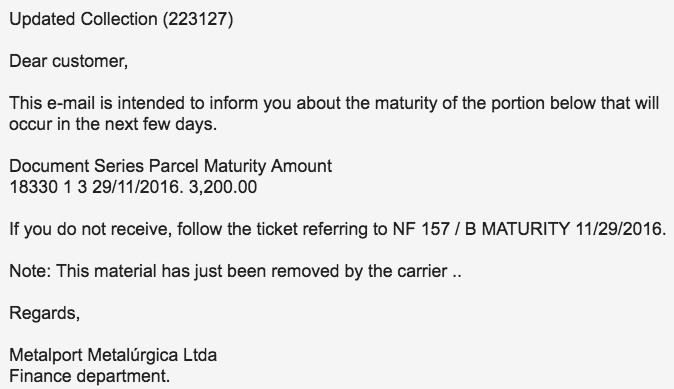
Shown above: Google translation of the email text.
EMAIL DATA:
- Received from mailserver at: ip-208-113-133-66.nodes.dream[.]io ( IP address: 208.113.133.66 )
- Subject: Cobranca Atualizada (223127)
- From: Financeiro <contato@ip-208-113-133-66.nodes.dream[.]io>
- Date/Time: Monday 2016-11-28 at 04:27:09 UTC
THE ATTACHMENT
Shown above: The attachment, a zip archive named: AN_COBRANCA-13.zip.
Shown above: The .js file extracted from the zip archive, AN_COBRANCA-.js.
ATTACHMENT AND EXTRACTED .JS FILE:
- SHA256 hash: 5f1fcb213563bd5fbf366026bee2c672dd299663756a1d1da0b75a1b6c823185
File name: AN_COBRANCA-13.zip (2,675 bytes)
- SHA256 hash: 377038f69df342fd90d31dea7b9eabf19f35b054c3e49418bd4cb5b424cfa0c9
File name: AN_COBRANCA-.js (9,903 bytes)
TRAFFIC
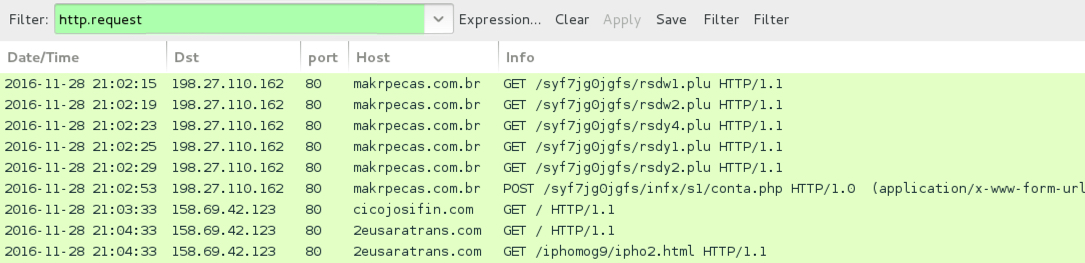
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED URLS:
- 198.27.110[.]162 port 80 - makrpecas[.]com[.]br - GET /syf7jg0jgfs/rsdw1.plu
- 198.27.110[.]162 port 80 - makrpecas[.]com[.]br - GET /syf7jg0jgfs/rsdw2.plu
- 198.27.110[.]162 port 80 - makrpecas[.]com[.]br - GET /syf7jg0jgfs/rsdy4.plu
- 198.27.110[.]162 port 80 - makrpecas[.]com[.]br - GET /syf7jg0jgfs/rsdy1.plu
- 198.27.110[.]162 port 80 - makrpecas[.]com[.]br - GET /syf7jg0jgfs/rsdy2.plu
- 198.27.110[.]162 port 80 - makrpecas[.]com[.]br - POST /syf7jg0jgfs/infx/s1/conta.php
- 158.69.42[.]123 port 80 - cicojosifin[.]com - GET /
- 158.69.42[.]123 port 80 - 2eusaratrans[.]com - GET /
- 158.69.42[.]123 port 80 - 2eusaratrans[.]com - GET /iphomog9/ipho2.html
IMAGES
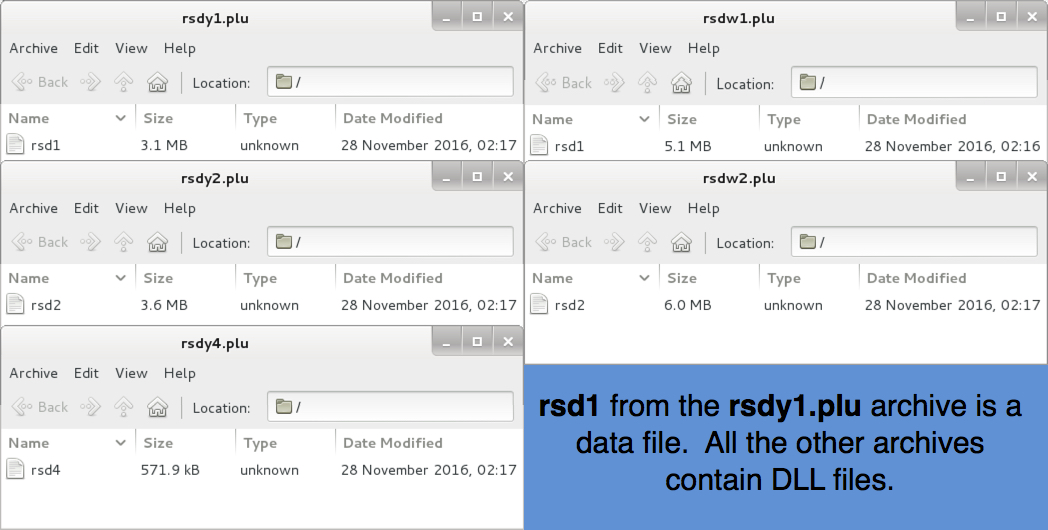
Shown above: Archives downloaded from makrpecas[.]com[.]br.
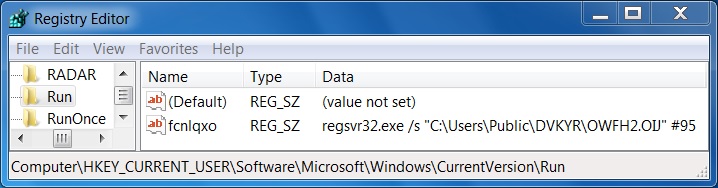
Shown above: A registry key from the infected Windows host.
FILES EXTRACTED FROM ARCHIVES DOWNLOADED BY THE INFECTED HOST:
- SHA256 hash: 533c257fb9c51153ec9da46dd5586d0e38582dfeaf408ccbcf0739a9f8cb542e
File name: rsd1-from-rsdw1.plu.DLL (5,064,192 bytes)
- SHA256 hash: a94c046fdff3de63e02e6e3d62bfb581234ab543d86ede109812097b720aa0d8
File name: rsd1-from-rsdy1.plu.DAT (3,113,985 bytes)
- SHA256 hash: 6fac323885918c96f6866fe61bccf08cbeb8ecf410c65339d6b098decdd9c59e
File name: rsd2-from-rsdw2.plu.DLL (6,011,904 bytes)
- SHA256 hash: a1889e0f973f7498972b227582991f53c644f99d5877689b56b1a86c38b1377f
File name: rsd2-from-rsdy2.plu.DLL (3,612,160 bytes)
- SHA256 hash: 3234a6bc92629b41014a169a7df9974d52da8d1f90ff830940f71d482b7e782e
File name: rsd4-from-rsdy4.plu.DLL (571,904 bytes)
website.
Click here to return to the main page.
