2016-11-29 - "ZZZZZ" VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-29-Locky-ransomware-email-tracker.csv.zip 3.2 kB (3,190 bytes)
- 2016-11-29-Locky-ransomware-infection-both-pcaps.zip 289.8 kB (289,831 bytes)
- 2016-11-29-Locky-ransomware-data.zip 3.3 MB (3,306,056 bytes)
- 2016-11-29-Locky-ransomware-email-tracker.csv (7,994 bytes)
- 2016-11-29-Locky-ransomware-infection-traffic-example-from-1st-wave.pcap (244,630 bytes)
- 2016-11-29-Locky-ransomware-infection-traffic-example-from-2nd-wave.pcap (134,876 bytes)
- files-from-infected-hosts / 2016-11-29-Locky-ransomware-Decryptor-style.css (3,422 bytes)
- files-from-infected-hosts / 2016-11-29-Locky-ransomware-Decryptor.html (6,400 bytes)
- files-from-infected-hosts / 2016-11-29-Locky-ransomware-decryption-instructions-INSTRUCTION.bmp (3,578,902 bytes)
- files-from-infected-hosts / 2016-11-29-Locky-ransomware-decryption-instructions-INSTRUCTION.html (9,221 bytes)
- files-from-infected-hosts / 2016-11-29-Locky-ransomware-luswiacs1.dll (221,184 bytes)
- attachments / COPY.29112016.0076.XLS (28,443 bytes)
- attachments / COPY.29112016.022138.XLS (28,490 bytes)
- attachments / COPY.29112016.0493.XLS (28,546 bytes)
- attachments / COPY.29112016.11089.XLS (28,490 bytes)
- attachments / COPY.29112016.132642.XLS (28,519 bytes)
- attachments / COPY.29112016.2456.XLS (28,555 bytes)
- attachments / COPY.29112016.3054.XLS (28,530 bytes)
- attachments / COPY.29112016.494446.XLS (28,534 bytes)
- attachments / COPY.29112016.5314.XLS (28,555 bytes)
- attachments / COPY.29112016.61652.XLS (28,533 bytes)
- attachments / COPY.29112016.625239.XLS (28,453 bytes)
- attachments / COPY.29112016.6596.XLS (28,554 bytes)
- attachments / COPY.29112016.6610.XLS (28,516 bytes)
- attachments / COPY.29112016.6922.XLS (28,531 bytes)
- attachments / COPY.29112016.705897.XLS (28,551 bytes)
- attachments / COPY.29112016.7141.XLS (28,558 bytes)
- attachments / COPY.29112016.7955.XLS (28,567 bytes)
- attachments / COPY.29112016.917519.XLS (28,532 bytes)
- attachments / COPY.29112016.94437.XLS (28,540 bytes)
- attachments / COPY.29112016.94603.XLS (28,496 bytes)
- attachments / INVOICE.TAM_078107_20161129_EB80D624D.xls (44,368 bytes)
- attachments / INVOICE.TAM_083482_20161129_178B52CB2.xls (44,347 bytes)
- attachments / INVOICE.TAM_135486_20161129_F54C387E0.xls (44,394 bytes)
- attachments / INVOICE.TAM_139603_20161129_FCC172411.xls (44,387 bytes)
- attachments / INVOICE.TAM_161425_20161129_F8363B5F4.xls (44,347 bytes)
- attachments / INVOICE.TAM_19014_20161129_1155219AD.xls (44,370 bytes)
- attachments / INVOICE.TAM_21078_20161129_E3DBB2719.xls (44,371 bytes)
- attachments / INVOICE.TAM_28697_20161129_1E4F735BA.xls (44,381 bytes)
- attachments / INVOICE.TAM_40234_20161129_49ED776BD.xls (44,399 bytes)
- attachments / INVOICE.TAM_42709_20161129_A805F73C0.xls (44,369 bytes)
- attachments / INVOICE.TAM_52133_20161129_B72AE506E.xls (44,348 bytes)
- attachments / INVOICE.TAM_52201_20161129_FCAE04AC3.xls (44,377 bytes)
- attachments / INVOICE.TAM_55935_20161129_055BB65DD.xls (44,394 bytes)
- attachments / INVOICE.TAM_61960_20161129_AFA46BED8.xls (44,359 bytes)
- attachments / INVOICE.TAM_83732_20161129_EFD7983DD.xls (44,363 bytes)
- attachments / INVOICE.TAM_84170_20161129_91A729B75.xls (44,340 bytes)
- attachments / INVOICE.TAM_844370_20161129_3B7365ECB.xls (44,339 bytes)
- attachments / INVOICE.TAM_875063_20161129_B2D8CF86B.xls (44,361 bytes)
- attachments / INVOICE.TAM_90207_20161129_910A929DF.xls (44,334 bytes)
- attachments / INVOICE.TAM_96492_20161129_CF7763F18.xls (44,394 bytes)
- emails / 2016-11-29-0809-UTC.eml (61,253 bytes)
- emails / 2016-11-29-0901-UTC.eml (61,222 bytes)
- emails / 2016-11-29-0929-UTC.eml (61,211 bytes)
- emails / 2016-11-29-0932-UTC.eml (61,217 bytes)
- emails / 2016-11-29-0952-UTC.eml (61,233 bytes)
- emails / 2016-11-29-0953-UTC.eml (61,293 bytes)
- emails / 2016-11-29-1000-UTC.eml (61,183 bytes)
- emails / 2016-11-29-1003-UTC.eml (61,248 bytes)
- emails / 2016-11-29-1015-UTC.eml (61,237 bytes)
- emails / 2016-11-29-1031-UTC.eml (61,238 bytes)
- emails / 2016-11-29-1117-UTC.eml (61,204 bytes)
- emails / 2016-11-29-1121-UTC.eml (61,247 bytes)
- emails / 2016-11-29-1134-UTC.eml (61,274 bytes)
- emails / 2016-11-29-1135-UTC.eml (61,272 bytes)
- emails / 2016-11-29-1137-UTC.eml (61,271 bytes)
- emails / 2016-11-29-1138-UTC.eml (61,215 bytes)
- emails / 2016-11-29-1205-UTC.eml (61,259 bytes)
- emails / 2016-11-29-1239-UTC.eml (61,193 bytes)
- emails / 2016-11-29-1256-UTC.eml (61,287 bytes)
- emails / 2016-11-29-1300-UTC.eml (61,217 bytes)
- emails / 2016-11-29-1416-UTC.eml (40,486 bytes)
- emails / 2016-11-29-1421-UTC.eml (40,547 bytes)
- emails / 2016-11-29-1434-UTC.eml (40,524 bytes)
- emails / 2016-11-29-1503-UTC.eml (40,528 bytes)
- emails / 2016-11-29-1512-UTC.eml (40,486 bytes)
- emails / 2016-11-29-1513-UTC.eml (40,496 bytes)
- emails / 2016-11-29-1543-UTC.eml (40,536 bytes)
- emails / 2016-11-29-1549-UTC.eml (40,551 bytes)
- emails / 2016-11-29-1553-UTC.eml (40,507 bytes)
- emails / 2016-11-29-1558-UTC.eml (40,419 bytes)
- emails / 2016-11-29-1559-UTC.eml (40,584 bytes)
- emails / 2016-11-29-1607-UTC.eml (40,536 bytes)
- emails / 2016-11-29-1614-UTC.eml (40,559 bytes)
- emails / 2016-11-29-1623-UTC.eml (40,501 bytes)
- emails / 2016-11-29-1625-UTC.eml (40,571 bytes)
- emails / 2016-11-29-1629-UTC.eml (40,569 bytes)
- emails / 2016-11-29-1630-UTC.eml (40,569 bytes)
- emails / 2016-11-29-1707-UTC.eml (40,557 bytes)
- emails / 2016-11-29-1721-UTC.eml (40,589 bytes)
- emails / 2016-11-29-1725-UTC.eml (40,612 bytes)
NOTES:
- As you probably already know, Locky ransomware is currently using .zzzzz as an extension for the files it encrypts.
- This started sometime last week, and several sources have reported on it (for example, this article).
- All attachments from the 2 waves of email I saw delivered the same Locky ransomware DLL file.
- The entry point for today's Locky ransomware DLL is sample exit in case anyone wants to run it with rundll32.exe in a controlled environment.
Shown above: A Google image search related to the .zzzzz file extension.
EMAILS
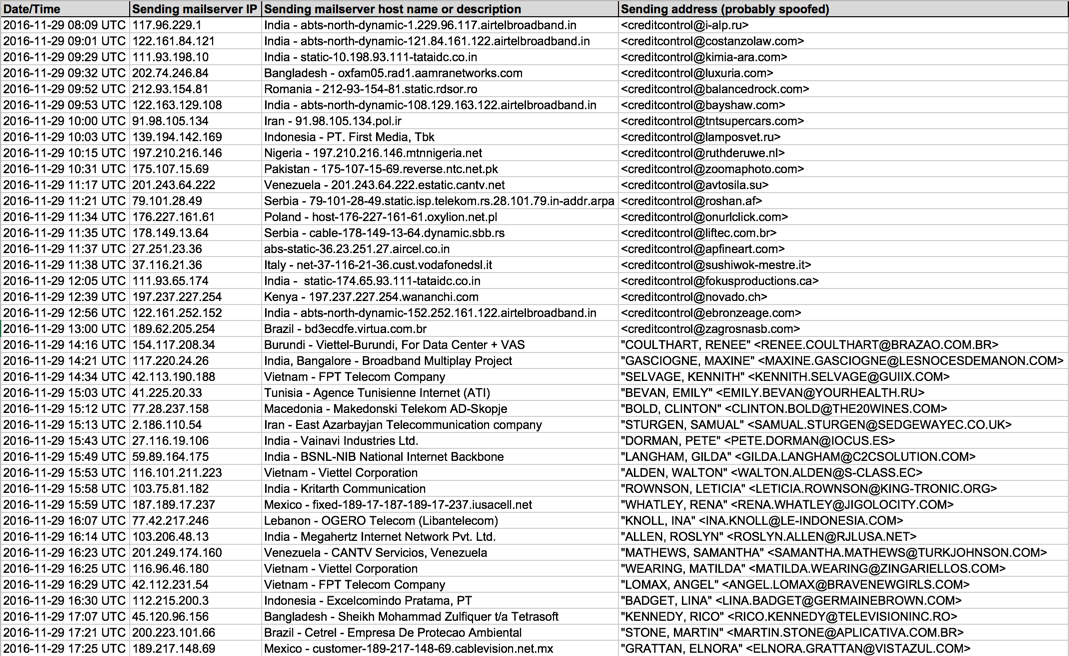
Shown above: Data from 40 emails pushing Locky ransomware examples (part 1 of 2).
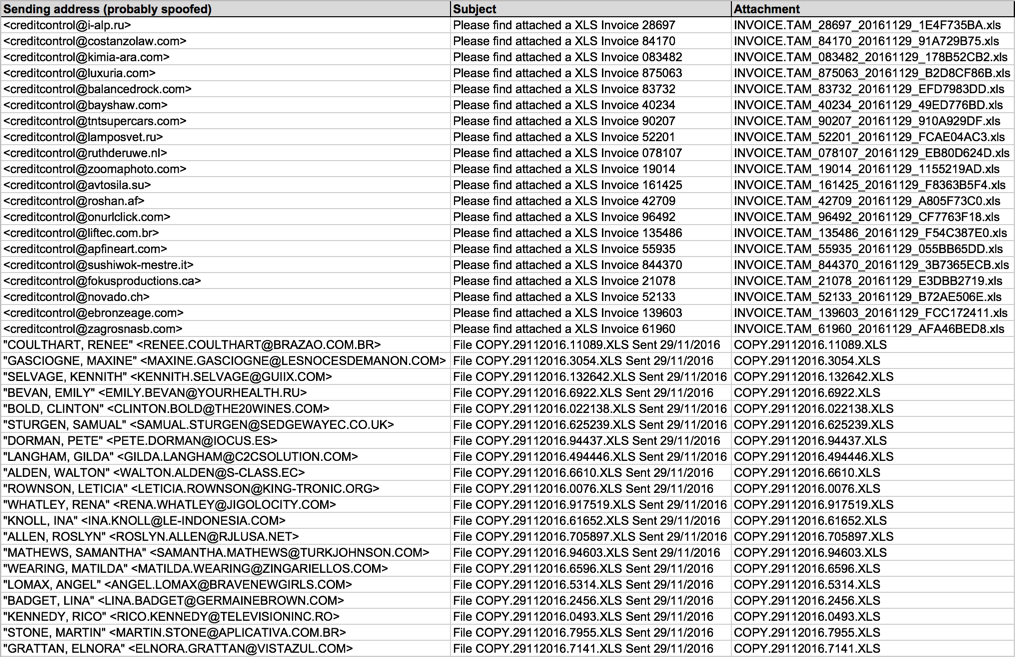
Shown above: Data from 40 emails pushing Locky ransomware (part 2 of 2).
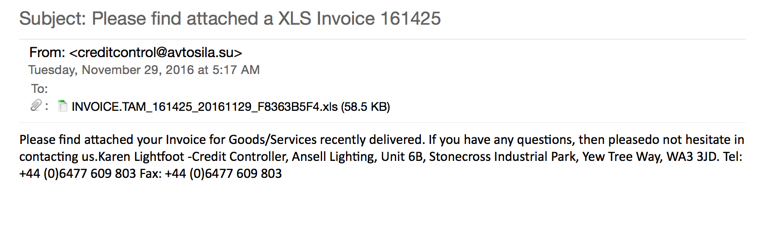
Shown above: An example from the first wave of these emails.
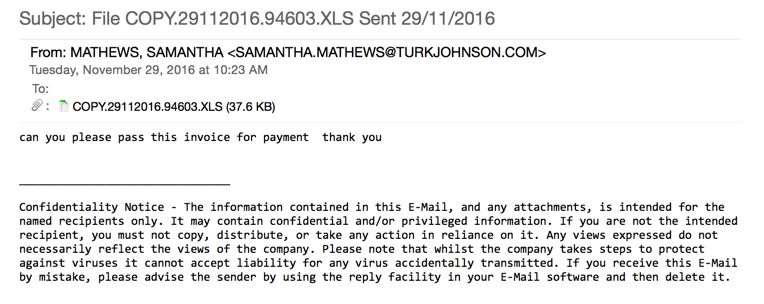
Shown above: An example from second wave of these emails.
TRAFFIC
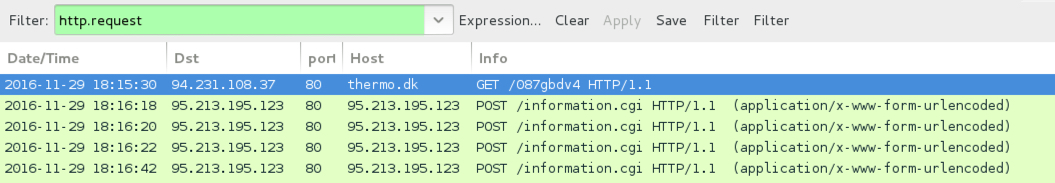
Shown above: An example of infection traffic from one of the emails in the first wave.
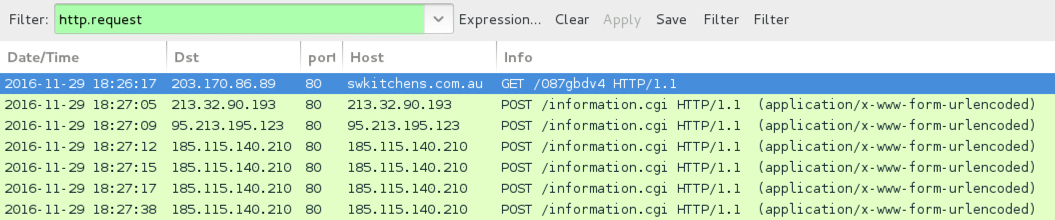
Shown above: An example of infection traffic from one of the emails in the second.
EXAMPLES OF TRAFFIC GENERATED BY THE EXCEL MARCO GRABBING THE LOCKY RANSOMWARE BINARY:
- 5.22.252[.]32 port 80 - revdev[.]nl - GET /087gbdv4
- 27.254.41[.]206 port 80 - pregnancysquare[.]com - GET /087gbdv4
- 67.198.188[.]20 port 80 - qiqi-store[.]com - GET /087gbdv4
- 87.98.189[.]74 port 80 - secotral[.]fr - GET /087gbdv4
- 91.218.213[.]181 port 80 - semeystvo[.]com[.]ua - GET /087gbdv4
- 94.73.148[.]50 port 80 - signumtte[.]net - GET /087gbdv4
- 94.231.108[.]37 port 80 - thermo[.]dk - GET /087gbdv4
- 94.231.108[.]252 port 80 - steffweb[.]dk - GET /087gbdv4
- 103.6.196[.]80 port 80 - sreekrishnatemple[.]com - GET /087gbdv4
- 103.6.196[.]118 port 80 - rhyzrin[.]com - GET /087gbdv4
- 106.185.53[.]205 port 80 - tyfastener[.]com - GET /087gbdv4
- 108.174.149[.]222 port 80 - rgbserver[.]be - GET /087gbdv4
- 146.112.61[.]108 port 80 - rechoboth[.]com - GET /087gbdv4
- 158.69.218[.]96 port 80 - sayvir[.]com - GET /087gbdv4
- 159.253.0[.]64 port 80 - radom[.]nl - GET /087gbdv4
- 173.254.231[.]136 port 80 - stocktradex[.]com - GET /087gbdv4
- 203.170.86[.]89 port 80 - swkitchens[.]com[.]au - GET /087gbdv4
POST-INFECTION CALLBACK FROM THE LOCKY RANSOMWARE SAMPLE:
- 69.195.129[.]70 port 80 - 69.195.129[.]70 - POST /information.cgi
- 95.213.195[.]123 port 80 - 95.213.195[.]123 - POST /information.cgi
- 185.115.140[.]210 port 80 - 185.115[.]140.210 - POST /information.cgi
- 213.32.90[.]193 port 80 - 213.32[.]90.193 - POST /information.cgi
TOR DOMAIN FROM THE DECRYPTION INSTRUCTIONS:
- mwddgguaa5rj7b54[.]onion
FILE HASHES
LOCKY RANSOMWARE DLL FILE:
- SHA256 hash: ff4a021e6175e5f2c0a666270081d74991c69e651c249a6fdf82a004dd9215e5
File name: C:\Users\[username]\AppData\Local\Temp\luswiacs1.dll (221,184 bytes)
EXCEL SPREADSHEETS FROM THE MALSPAM (SHA256 HASH - FILE NAME):
- 7b1a1c92e477bbfa974e2a4af5165e596abe0074d46aa44ccfc7b0a7435e324e - COPY.29112016.0076.XLS
- 024d738f04f77225e2ea3f3304eda505bb4cb1600d4d8922881646e4c37933f1 - COPY.29112016.022138.XLS
- 96c0ed6a8c2f3609153803de68e23b83f51a60313c51ecc37bc042a3dc8bdd6a - COPY.29112016.0493.XLS
- 40a3855bddbeffa459535af49cfbf8cd6167f899069ae5986816cd19fbb98aab - COPY.29112016.11089.XLS
- 19cc425a6b18669af78481c6e99c8529214281d4f6a6ce22a3e5fd8d704554b4 - COPY.29112016.132642.XLS
- 6e676f6bf324a6f11cae592384b30fdb7c04f7d9409a5930b9e3957d9ef7f7ef - COPY.29112016.2456.XLS
- 6192fc62c10a7f30dc3c01493d79bd663579b9251f31a0e31f5448a4711ec2c5 - COPY.29112016.3054.XLS
- 5af5751874883a71d25d277a32149317d44c93e04d1a68f2aa3010287e1bab73 - COPY.29112016.494446.XLS
- 6e676f6bf324a6f11cae592384b30fdb7c04f7d9409a5930b9e3957d9ef7f7ef - COPY.29112016.5314.XLS
- 6459ecc657ef33b27a3d21b2a16fea6f028db4ef717b97abf0009acbeba82e60 - COPY.29112016.61652.XLS
- 66ac28d49782cea85c19da2ca6ac393a01c305a16303fa60167d9cde7e6bd153 - COPY.29112016.625239.XLS
- 6d061bb3fedb65dc85fe04669bbdeca086c4879e28bbef0f60ed5bcabf920706 - COPY.29112016.6596.XLS
- 7aad672b7b2b4c96ff6ece75535511fad236a3620638546074222db9000b62cd - COPY.29112016.6610.XLS
- cc88a9307e9c4b4074fc0e8e02025e218a793a9eb0bb1d58a21decafc5b4fa86 - COPY.29112016.6922.XLS
- 4ec01b216af48909ec86c9e5ab26ba584e3569c471a54c2cd2467350cd85190c - COPY.29112016.705897.XLS
- 6b8d3b43178807c9937e82a9e6581e9bc1510a12d285eea06df58901f54aff90 - COPY.29112016.7141.XLS
- 122a7d05cfec7fd5b6b6cc296c53d9656c423245291b25c71e31611455eef944 - COPY.29112016.7955.XLS
- e57087b14acebde3f87da90864a923d9bfe4f4636cf1fbb0a61e4a0bb293ce2c - COPY.29112016.917519.XLS
- e27acb8509df42a58deef921a00d65325a6fe700d0d71e6dd6103e63e14bb7b1 - COPY.29112016.94437.XLS
- 759c1b65e0a9c07669871e5f368ea2c61d5f865e632609512e65f76e006ebb79 - COPY.29112016.94603.XLS
- e78e8f608e46b8bc101c723783d1b53696db594fa633034fb8d0bad402fa2294 - INVOICE.TAM_078107_20161129_EB80D624D.xls
- 0092f679b52240f2a7fe9aaaa273690dfaa6455c382fcaaf32154aa09a245886 - INVOICE.TAM_083482_20161129_178B52CB2.xls
- addda1969719c220e2d2477136ae8ea92fa3a3c9b349050855d35478d93a85bb - INVOICE.TAM_135486_20161129_F54C387E0.xls
- 70893cbb999f5f66360c0f0296d0855077ed0677af51ac2cd20bd29a3dc0c986 - INVOICE.TAM_139603_20161129_FCC172411.xls
- 364d9b50d0d28d57e65a087dd2d767ea9ca90a01f561e370086a0848b3654f76 - INVOICE.TAM_161425_20161129_F8363B5F4.xls
- 5e242004ef65b6266c110ea8b99613321c7bf6c9c7d9542735097e4626a46739 - INVOICE.TAM_19014_20161129_1155219AD.xls
- 862a7459e22e674cf5ddf741e0ae879e5caddfe399c4eb08fe6a51da17599117 - INVOICE.TAM_21078_20161129_E3DBB2719.xls
- 1a666890e564b89c1ed4e559144c604a1a3032fa0a10bc572e9938235b8016b8 - INVOICE.TAM_28697_20161129_1E4F735BA.xls
- 81dde58f511622bc21046b184404eebfc83b61c2d2da9e544cad0b421a7a230a - INVOICE.TAM_40234_20161129_49ED776BD.xls
- b2c111bcf3fd2151ca05c2d6d186b4fa6588a72650bfc6da6ec04285ee37f1b1 - INVOICE.TAM_42709_20161129_A805F73C0.xls
- 5705d03fc3010a009e5808b84a9c6014e1bfc7a63f3558823019f730198af663 - INVOICE.TAM_52133_20161129_B72AE506E.xls
- 5d9845048c717be38b878764af48a0b3123e6a0d42db74bf12f9837cbbad4bec - INVOICE.TAM_52201_20161129_FCAE04AC3.xls
- addda1969719c220e2d2477136ae8ea92fa3a3c9b349050855d35478d93a85bb - INVOICE.TAM_55935_20161129_055BB65DD.xls
- 1be32da6a61495fe026b151a4748d0b0a0f976f85c9d77bd8b06244cbf94064d - INVOICE.TAM_61960_20161129_AFA46BED8.xls
- 7db91900306cdf71fd99c2d06848a4a854be01c4bdbd770b6c4173faeadc2654 - INVOICE.TAM_83732_20161129_EFD7983DD.xls
- 45a6e63bae0988be324491eab1ff2e88f7446cf380393fc8ebb338cd12a44847 - INVOICE.TAM_84170_20161129_91A729B75.xls
- 0565d977485b97946f15b203b8a699a86e914070ac10a7347c4a7c9b88823730 - INVOICE.TAM_844370_20161129_3B7365ECB.xls
- f5f2eadc4a4d8797ba8a90be12da532390057cc0b31cc6db7bc3e4cf5ac9bc45 - INVOICE.TAM_875063_20161129_B2D8CF86B.xls
- d95b931fa618713310122a228df1b28ec17e9b17f573b82267f578d97a713ef3 - INVOICE.TAM_90207_20161129_910A929DF.xls
- addda1969719c220e2d2477136ae8ea92fa3a3c9b349050855d35478d93a85bb - INVOICE.TAM_96492_20161129_CF7763F18.xls
IMAGES
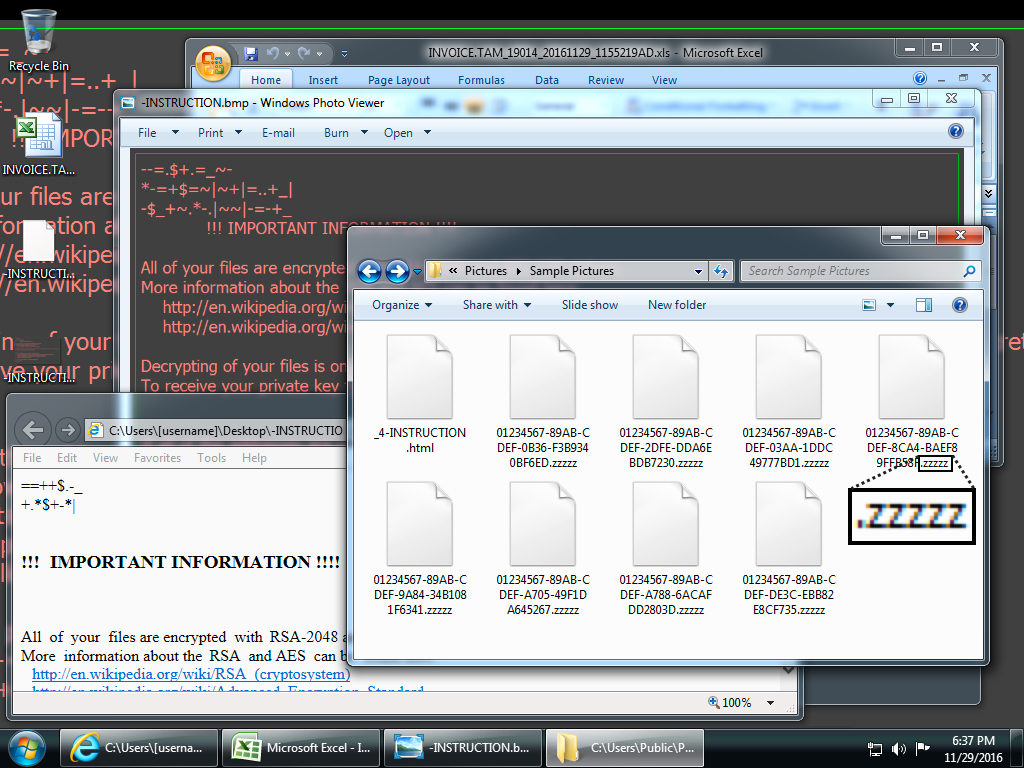
Shown above: Screen shot from an infected Windows desktop. Note the .zzzzz file extension.
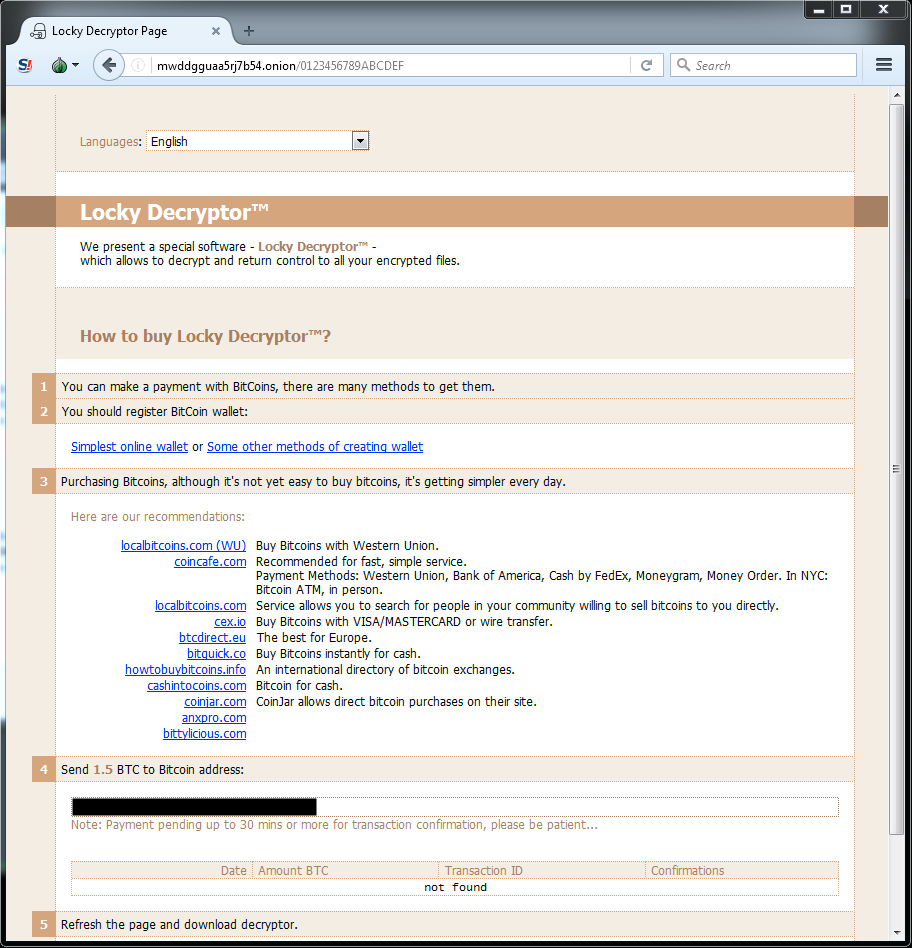
Shown above: Ransom payment was 1.5 bitcoin for the infections I generated.
Click here to return to the main page.
