2016-12-06 - RIG EK DATA DUMP
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- Sometime today, Rig-E switched from the old 40 kB Flash exploits to the same 15 kB Flash exploit as Rig-V.
- At the same time, Rig-E landing pages went from approximately 3 kB to approximately 85 kB in size.
ASSOCIATED FILES:
- 2016-12-06-Rig-EK-data-dump-5-pcaps.zip 2.5 MB (2,489,107 bytes)
- 2016-12-06-1st-run-EITest-Rig-E-sends-Chthonic.pcap (806,307 bytes)
- 2016-12-06-2nd-run-EITest-Rig-E-sends-Gootkit.pcap (201,607 bytes)
- 2016-12-06-3rd-run-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (413,749 bytes)
- 2016-12-06-4th-run-EITest-Rig-E-sends-Quant-Loader.pcap (141,193 bytes)
- 2016-12-06-5th-run-EITest-Rig-E-sends-Chthonic.pcap (1,279,665 bytes)
- ZIP archive of the malware: 2016-12-06-Rig-EK-data-dump-malware-and-artifacts.zip 1.2 MB (1,167,187 bytes)
- 2016-12-06-1st-run-EITest-Rig-E-artifact-MXj6sFosp.txt (1,137 bytes)
- 2016-12-06-1st-run-EITest-Rig-E-flash-exploit.swf (40,141 bytes)
- 2016-12-06-1st-run-EITest-Rig-E-landing-page.txt (3,416 bytes)
- 2016-12-06-1st-run-EITest-Rig-E-payload-Chthonic.exe (393,216 bytes)
- 2016-12-06-1st-run-page-from-cavallinomotorsport_com-with-injected-script.txt (18,835 bytes)
- 2016-12-06-2nd-run-EITest-Rig-E-artifact-MXj6sFosp.txt (1,137 bytes)
- 2016-12-06-2nd-run-EITest-Rig-E-flash-exploit.swf (40,141 bytes)
- 2016-12-06-2nd-run-EITest-Rig-E-landing-page.txt (3,410 bytes)
- 2016-12-06-2nd-run-EITest-Rig-E-payload-Gootkit.exe (294,912 bytes)
- 2016-12-06-2nd-run-page-from-cavallinomotorsport_com-with-injected-script.txt (18,839 bytes)
- 2016-12-06-3rd-run-page-from-joellipman.com-with-injected-script.txt (68,856 bytes)
- 2016-12-06-3rd-run-pseudoDarkleech-Rig-V-artifact-MXj6sFosp.txt (1,137 bytes)
- 2016-12-06-3rd-run-pseudoDarkleech-Rig-V-flash-exploit.swf (15,043 bytes)
- 2016-12-06-3rd-run-pseudoDarkleech-Rig-V-landing-page.txt (5,376 bytes)
- 2016-12-06-3rd-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware.exe (267,894 bytes)
- 2016-12-06-4th-run-EITest-Rig-E-flash-exploit.swf (15,043 bytes)
- 2016-12-06-4th-run-EITest-Rig-E-landing-page.txt (85,255 bytes)
- 2016-12-06-4th-run-EITest-Rig-E-payload-Quant-Loader.exe (70,393 bytes)
- 2016-12-06-4th-run-page-from-cavallinomotorsport_com-with-injected-script.txt (18,826 bytes)
- 2016-12-06-5th-run-EITest-Rig-E-flash-exploit.swf (15,043 bytes)
- 2016-12-06-5th-run-EITest-Rig-E-landing-page.txt (85,243 bytes)
- 2016-12-06-5th-run-EITest-Rig-E-payload-Chthonic.exe (393,216 bytes)
- 2016-12-06-5th-run-page-from-cavallinomotorsport_com-with-injected-script.txt (18,830 bytes)
TRAFFIC
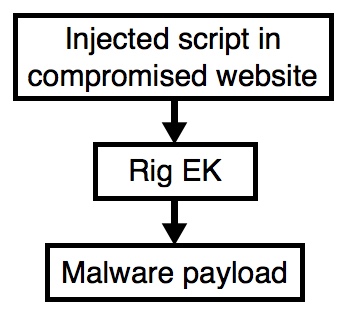
Shown above: Flow chart for today's infection traffic.
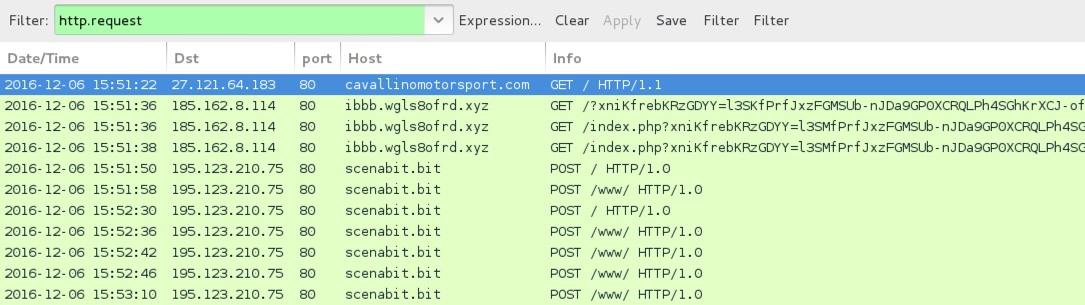
Shown above: Traffic from the 1st infection filtered in Wireshark.
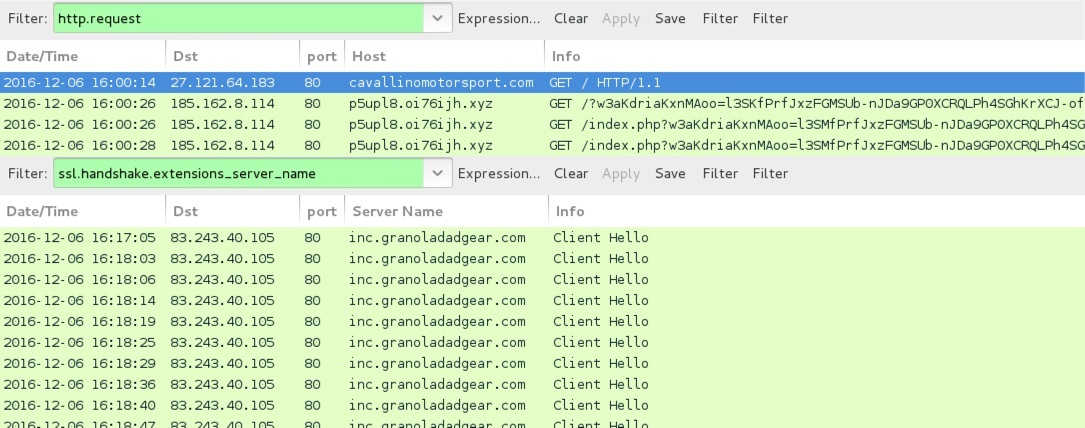
Shown above: Traffic from the 2nd infection filtered in Wireshark.
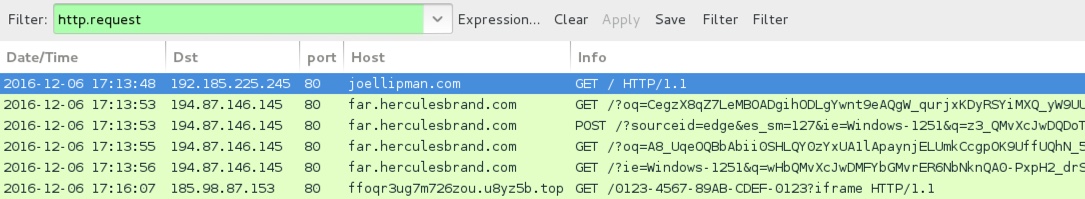
Shown above: Traffic from the 3rd infection filtered in Wireshark.
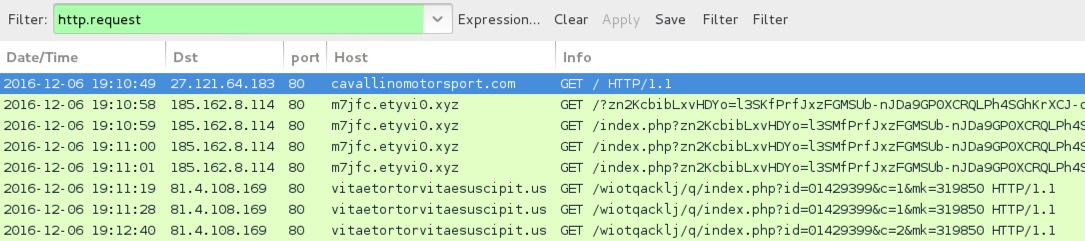
Shown above: Traffic from the 4th infection filtered in Wireshark.
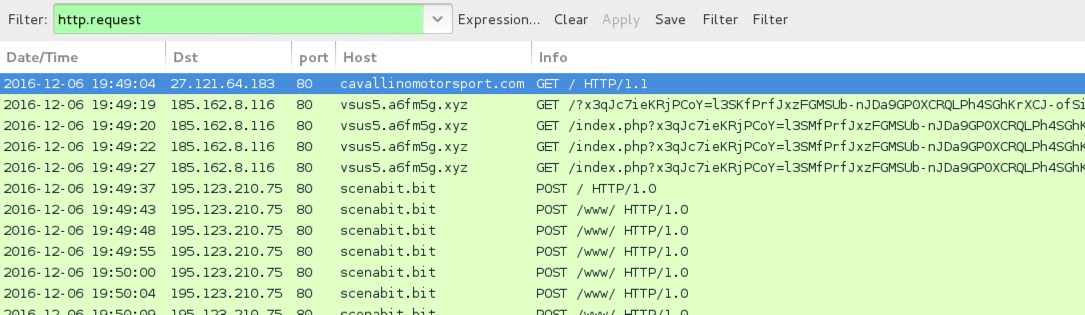
Shown above: Traffic from the 5th infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 185.162.8[.]114 port 80 - ibbb.wgls8ofrd[.]xyz - Rig-E (1st infection)
- 185.162.8[.]114 port 80 - p5upl8.oi76ijh[.]xyz - Rig-E (2nd infection)
- 194.87.146[.]145 port 80 - far.herculesbrand[.]com - Rig-V (3rd infection)
- 185.162.8[.]114 port 80 - m7jfc.etyvi0[.]xyz - Rig-E (4th infection)
- 185.162.8[.]116 port 80 - vsus5.a6fm5g[.]xyz - Rig-E (5th infection)
- 31.3.135[.]232 port 53 - DNS queries for scenabit[.]bit from the Chthonic post-infection traffic
- 195.123.210[.]75 port 80 - scenabit[.]bit - Chthonic post-infection HTTP traffic
- 83.243.40[.]105 port 80 - inc.granoladadgear[.]com - Gootkit post-infection traffic via HTTS/SSL/TLS over TCP port 80
- 15.49.2[.]0 to 15.49.2[.]31 (15.49.2[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 122.1.13[.]0 to 122.1[.]31 (122.1.13[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 194.165.16[.]0 to 194.165.17[.]255 (194.165.16[.]0/23) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 185.98.87[.]153 port 80 - ffoqr3ug7m726zou.u8yz5b[.]top - Cerber ransomware post-infection HTTP traffic
- 81.4.108[.]169 port 80 - vitaetortorvitaesuscipit[.]us - Quant Loader post-infection HTTP traffic
FILE HASHES
FLASH EXPLOITS (READ: SHA256 HASH - FILE NAME - FILE SIZE)
- b73dd34e63a001b3be1e809c889df4a075162891034404e4d344d7cfafb1bc0e - 2016-12-06-1st-run-EITest-Rig-E-flash-exploit.swf - 40,141 bytes
- b73dd34e63a001b3be1e809c889df4a075162891034404e4d344d7cfafb1bc0e - 2016-12-06-2nd-run-EITest-Rig-E-flash-exploit.swf - 40,141 bytes
- fb9eb0a848cba0eb9c706287194b76fa9b72d3843b1b94296e9003ccb5c27dfd - 2016-12-06-3rd-run-pseudoDarkleech-Rig-V-flash-exploit.swf - 15,043 bytes
- fb9eb0a848cba0eb9c706287194b76fa9b72d3843b1b94296e9003ccb5c27dfd - 2016-12-06-4th-run-EITest-Rig-E-flash-exploit.swf - 15,043 bytes
- fb9eb0a848cba0eb9c706287194b76fa9b72d3843b1b94296e9003ccb5c27dfd - 2016-12-06-5th-run-EITest-Rig-E-flash-exploit.swf - 15,043 bytes
PAYLOADS:
- 99c610031b3710cb6c58b4045239701093ae4b96ca5dfa96fd175ef6accc1f10 - 2016-12-06-1st-run-EITest-Rig-E-payload-Chthonic.exe - 393,216 bytes
- 65c4866588dd84db00f79a4707c7521cfd941ac254a0149c98b062310fc77060 - 2016-12-06-2nd-run-EITest-Rig-E-payload-Gootkit.exe - 294,912 bytes
- 1ccf8c29844dc295649c0fe170ded98fe63f380614bef467a887275be75ecd26 - 2016-12-06-3rd-run-pseudoDarkleech-Rig-V-payload-Cerber-ransomware.exe - 267,894 bytes
- 26b2cd43577993e8f2a36c9f73134393aed073ffef2548f7bc7d547c1735d4d7 - 2016-12-06-4th-run-EITest-Rig-E-payload-Quant-Loader.exe - 70,393 bytes
- 99c610031b3710cb6c58b4045239701093ae4b96ca5dfa96fd175ef6accc1f10 - 2016-12-06-5th-run-EITest-Rig-E-payload-Chthonic.exe - 393,216 bytes
Click here to return to the main page.
