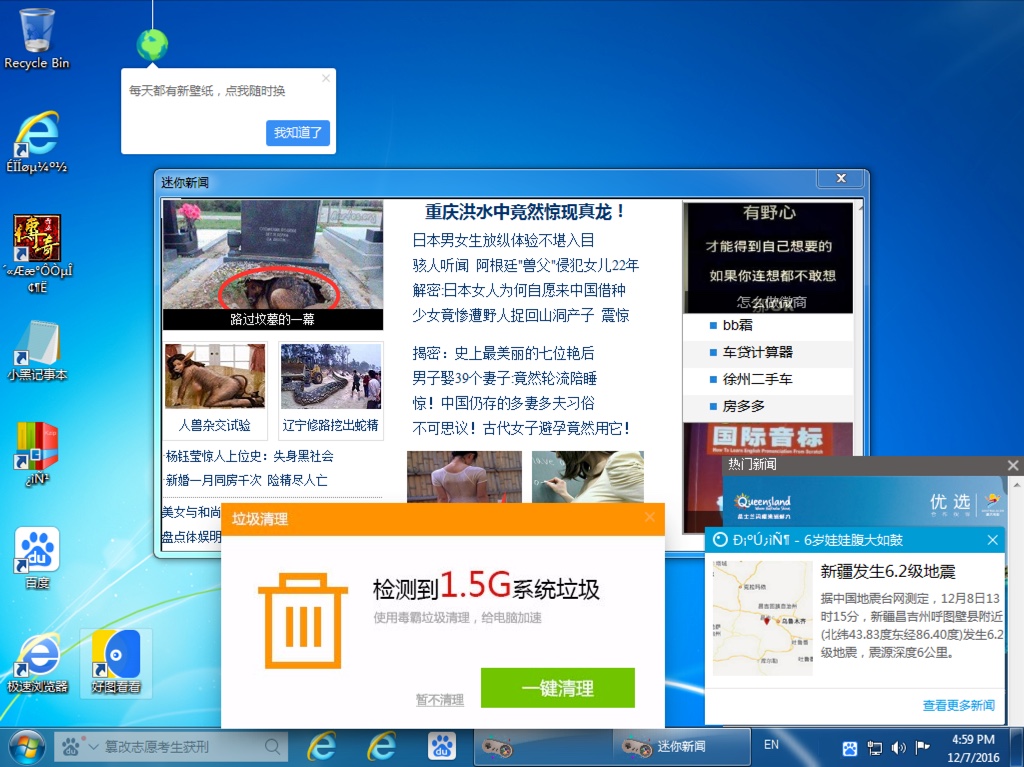
2016-12-07 - KAIXIN EK FROM 220.169.242[.]216
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-12-07-KaiXin-EK-traffic.pcap.zip 6.1 MB (6,079,296 bytes)
- 2016-12-07-KaiXin-EK-traffic.pcap (8,060,637 bytes)
- 2016-12-07-KaiXin-EK-malware-and-artifacts.zip 4.2 MB (4,164,514 bytes)
- 2016-12-07-KaiXin-EK-index.js.txt (3,002 bytes)
- 2016-12-07-KaiXin-EK-jquery-1.4.2.min.js.txt (19,936 bytes)
- 2016-12-07-KaiXin-EK-landing-page.txt (6,907 bytes)
- 2016-12-07-KaiXin-EK-main.htm.txt (16,083 bytes)
- 2016-12-07-KaiXin-EK-payload-server.exe (114,688 bytes)
- 2016-12-07-KaiXin-EK-swfobject.js.txt (12,677 bytes)
- 2016-12-07-KaiXin-EK-win.html.txt (15,519 bytes)
- 2016-12-07-post-infection-down.cables-echu_com-8191-Sanxun_1053.exe (1,447,424 bytes)
- 2016-12-07-post-infection-downdll.baijiai_com-caches-sevice_905_45078.exe (576,680 bytes)
- 2016-12-07-post-infection-senv.selcn_com-senvzhibo-Sesp203_nv_u.exe (1,261,568 bytes)
- 2016-12-07-post-infection-test.baogonghui_com-test-setup_50006.exe (1,928,192 bytes)
NOTES:
- The payload in this case was Murlo, a file downloader that installed a bunch of unwanted Chinese programs.
Shown above: A Windows host after being infected with this particular Murlo file downloader.
TRAFFIC
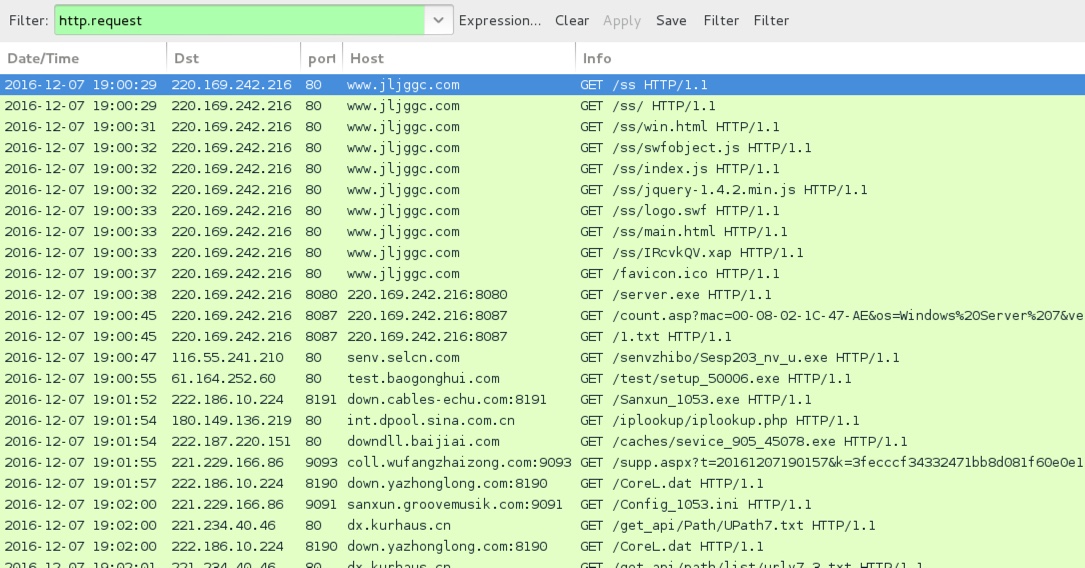
Shown above: Traffic from the infection filtered in Wireshark.
KAIXIN EK:
- 220.169.242[.]216 port 80 - www.jljggc[.]com - KaiXin EK
- 220.169.242[.]216 port 8080 - 220.169.242[.]216:8080 - KaiXin EK payload
- 220.169.242[.]216 port 8087 - 220.169.242[.]216:8087 - post-infection callback for malware list
POST-INFECTION FOLLOW-UP DOWNLOADS:
- 116.55.241[.]210 port 80 - senv.selcn[.]com - GET /senvzhibo/Sesp203_nv_u.exe
- 61.164.252[.]60 port 80 - test.baogonghui[.]com - GET /test/setup_50006.exe
- 222.186.10[.]224 port 8191 - down.cables-echu[.]com:8191 - GET /Sanxun_1053.exe
- 222.187.220[.]151 port 80 - downdll.baijiai[.]com - GET /caches/sevice_905_45078.exe
FILE HASHES
KAXIN EK PAYLOAD (MURLO FILE DOWNLOADER):
- SHA256 hash: 63b622a3bd98d7f0a9648af81f81accf5fa7a7c55950cd86dde3a817af81985e
File description: KaiXin EK payload (114,688 bytes)
FOLLOW-UP DOWNOADS:
- SHA256 hash: 5fd92a8e69998a7eb4fb78c9a799c0e94e4160a11f1f4b3e3dc3539b9f071279
File name: Sanxun_1053.exe (1,447,424 bytes)
- SHA256 hash: a439578a1add97c41aae571533c820d8d8286dc75d1bbbe58093b3b5b3dbb047
File name: Sesp203_nv_u.exe (1,261,568 bytes)
- SHA256 hash: 1e3a2cc84812d8b1ae746855278e67e8d47006cbfc8c0055da41b9311be48f09
File name: setup_50006.exe (1,928,192 bytes)
- SHA256 hash: 43b7231c370dba9bdd8643dcf182ada664e801c7fbde8f46e7343c04826e4272
File name: sevice_905_45078.exe (576,680 bytes)
IMAGES
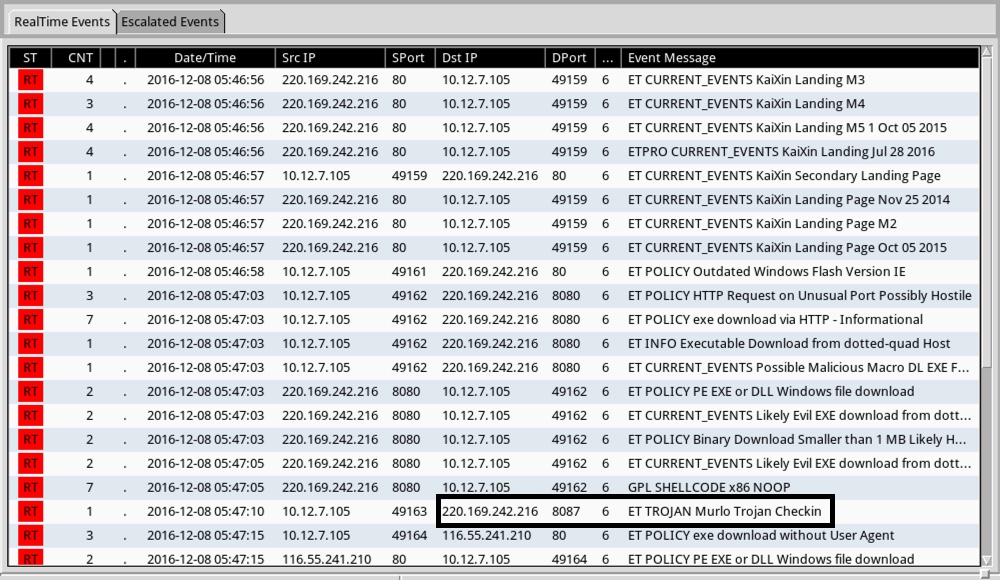
Shown above: Some of alerts from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion.
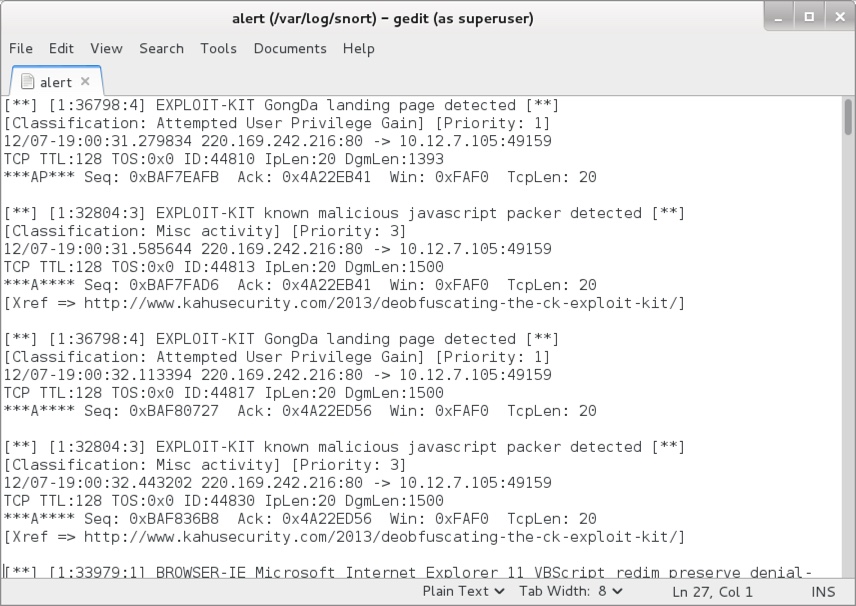
Shown above: Some alerts the Snort subscriber ruleset using Snort 2.9.8.3 on Debian 7.11.
Click here to return to the main page.