2016-12-09 - "OSIRIS" VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-12-09-Locky-ransomware-email-tracker.csv.zip 2.9 kB (2,916 bytes)
- 2016-12-09-Locky-ransomware-traffic.pcap.zip 152.1 kB (152,103 bytes)
- 2016-12-09-emails-distributing-Locky-ransomware-20-examples.zip 654.4 kB (645,438 bytes)
- 2016-12-09-email-attachments-for-Locky-ransomware-20-examples.zip 409.9 kB (409,924 bytes)
- 2016-12-09-files-from-a-Locky-ransomware-infection.zip 185 kB (185,982 bytes)
NOTES:
- On Monday December 5th, Locky ransomware switched from the .zzzzz extension to the .osiris extension for the files it encrypts.
- All attachments from the 2 waves of emails I saw today delivered the same Locky ransomware DLL file.
- The entry point for today's Locky ransomware DLL is sample sym in case anyone wants to run it with rundll32.exe in a controlled environment.
EMAILS
SUBJECT LINES:
- See attached - I will call you in 3 mins
- See attached - I will call you in 5 mins
- See attached - I will call you in 10 mins
- See attached - I will call you in 15 mins
- See attached - I will call you in 20 mins
- See attached - I will call you in 30 mins
- Documents Requested
- Re:Documents Requested
- FW:Documents Requested
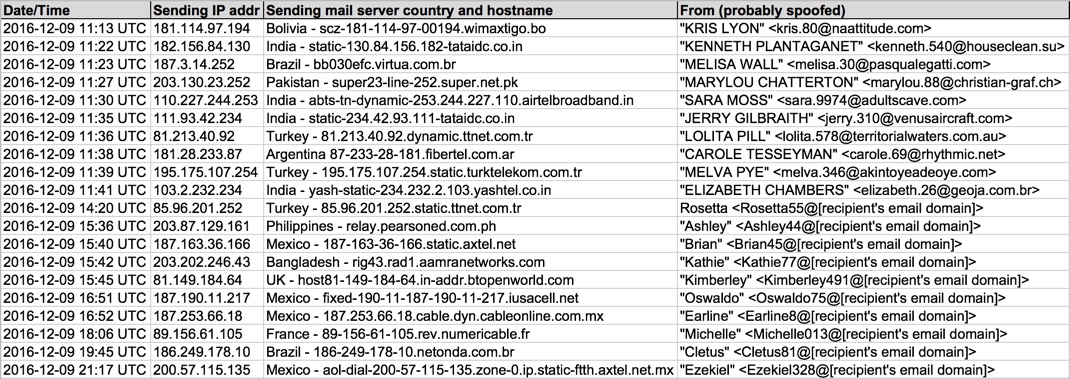
Shown above: Data from 20 emails pushing Locky ransomware (part 1 of 2).
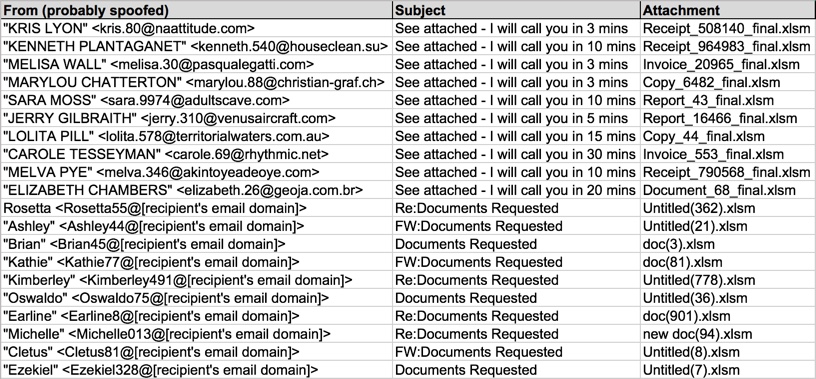
Shown above: Data from 20 emails pushing Locky ransomware (part 2 of 2).
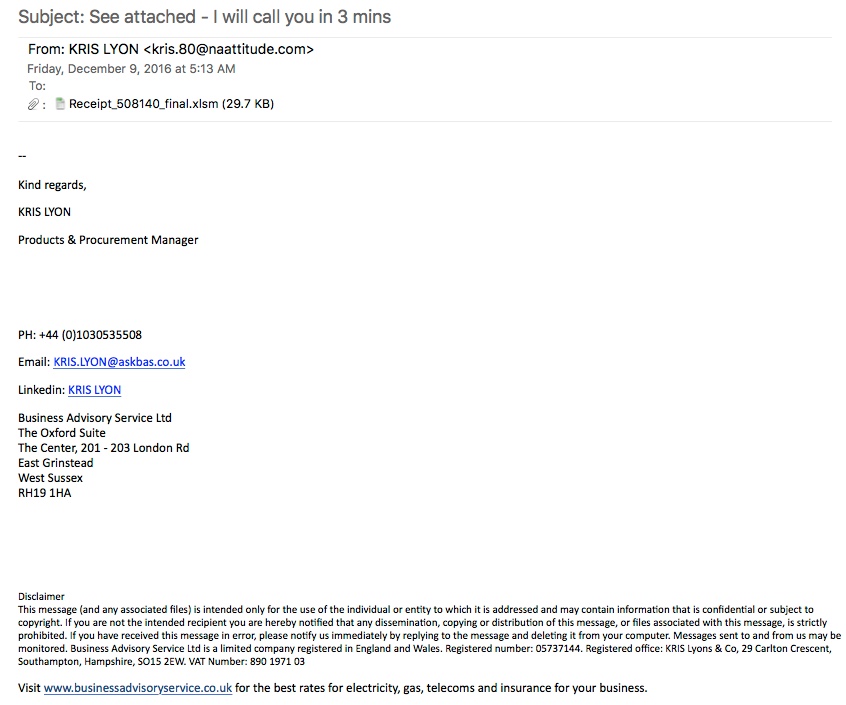
Shown above: An example from the first wave of these emails.
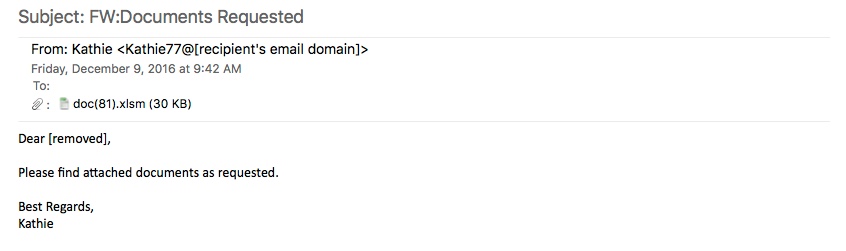
Shown above: An example from second wave of these emails.
TRAFFIC
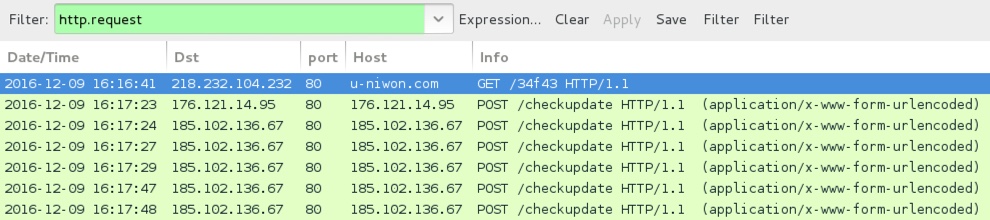
Shown above: An example of infection traffic by the Excel sheets from one of the emails.
EXAMPLES OF TRAFFIC GENERATED BY THE EXCEL MARCO RETRIEVING THE LOCKY RANSOMWARE BINARY:
- 97.74.215[.]147 port 80 - laferwear[.]com - GET /34f43
- 108.174.153[.]189 port 80 - djelixir[.]com - GET /34f43
- 193.68.112[.]65 port 80 - cafe-bg[.]com - GET /34f43
- 195.222.33[.]173 port 80 - facerecognition[.]com[.]ba - GET /34f43
- 195.228.152[.]23 port 80 - polgarorvasad[.]hu - GET /34f43
- 202.125.36[.]106 port 80 - walkonwheels[.]net[.]au - GET /34f43
- 202.174.32[.]106 port 80 - denva-art[.]com - GET /34f43
- 216.250.121[.]1 port 80 - kathollowell[.]com - GET /34f43
- 217.160.223[.]75 port 80 - waat[.]co[.]uk - GET /34f43
- 218.232.104[.]232 port 80 - u-niwon[.]com - GET /34f43
POST-INFECTION CALLBACK FROM THE LOCKY RANSOMWARE SAMPLE:
- 176.121.14[.]95 port 80 - 176.121.14[.]95 - POST /checkupdate
- 185.102.136[.]67 port 80 - 185.102.136[.]67 - POST /checkupdate
TOR DOMAIN FROM THE DECRYPTION INSTRUCTIONS:
- g46mbrrzpfszonuk[.]onion
FILE HASHES
LOCKY RANSOMWARE DLL FILE:
- SHA256 hash: 3f2e77d2ef17c7374f5ca26427cd34348f54c29b1d765c0f0c6a891ed97dd76a (225,280 bytes)
- File name: C:\Users\[username]\AppData\Local\Temp\clsooach1.feds
- DLL entry point: sym
EXCEL SPREADSHEETS FROM THE EMAILS (SHA256 HASH - FILE NAMES):
- 02aed7aa31b4522018e2df2ffdc7c3d2e7853844fffdb8315c251cc5a17150f2 - Copy_6482_final.xlsm
- 08d4dbc7de30671446ee03b209b796a6f91945c66cef7a4d54fc5e91660af4ff - Receipt_508140_final.xlsm
- 0fb0bae04d07fb41f07fb4c0618a441fe6f0e7f1172460966eb616d58be2f023 - Receipt_964983_final.xlsm
- 128e3463d36adf61ef8afd3e560ffb307200886b30c96726ee6d95551f17c14a - doc(901).xlsm
- 1fae5a4c51718733ae0e4be662bd9789a9ed29aa97fe0c0139981464bb914873 - Untitled(362).xlsm
- 23f06446fa649286c2602aacd15821d18aedd4e63e4ffe7b9098f802eb0d4109 - Untitled(21).xlsm
- 5209db0993ea7081d8daed6eab7aa47e604ea014f4280db26bff7a4be6010892 - new doc(94).xlsm
- 7e75750ebd406499d5e36c1d585e00c11edfe3f58e5acf235a394de0b24fdd7b - doc(3).xlsm , doc(81).xlsm
- 916247902cc76455ec88316d86e15fd43365942921acc566350b426a19b417cd - Untitled(7).xlsm
- 99c37808ba2e36224a594c668763fd4f3148ec0769da19cad7930146b1bbbeb8 - Untitled(8).xlsm
- aea3c9a4de3eeb1dc1500c12558426081440ff5ec6d623c45f4ea88c739e9fd1 - Copy_44_final.xlsm , Report_16466_final.xlsm
- b739bc19c49b34171fa08af014291de79d6876aa91316a3103476d6013f263f9 - Report_43_final.xlsm
- ba098fabf6758d5777917bda0589d430b642d217f49d40319eecf4211a3633db - Invoice_20965_final.xlsm
- bb9137f79557696674dbd5bf2306a1b1d046cef7cad8854f6648cd9d3f819760 - Invoice_553_final.xlsm , Receipt_790568_final.xlsm
- bd88640115c4350671fba0dd7063690f0daa4b4755658669680f1b2d88d4e3c0 - Document_68_final.xlsm
- f508fb948d76129da5b348f319858f39670525e5beca9b157bc659e614637a66 - Untitled(36).xlsm
- f8795e7b0ce3cfc97278ec31e35b7833505e6d54f379c5a3d4c3d5bfc326c341 - Untitled(778).xlsm
IMAGES
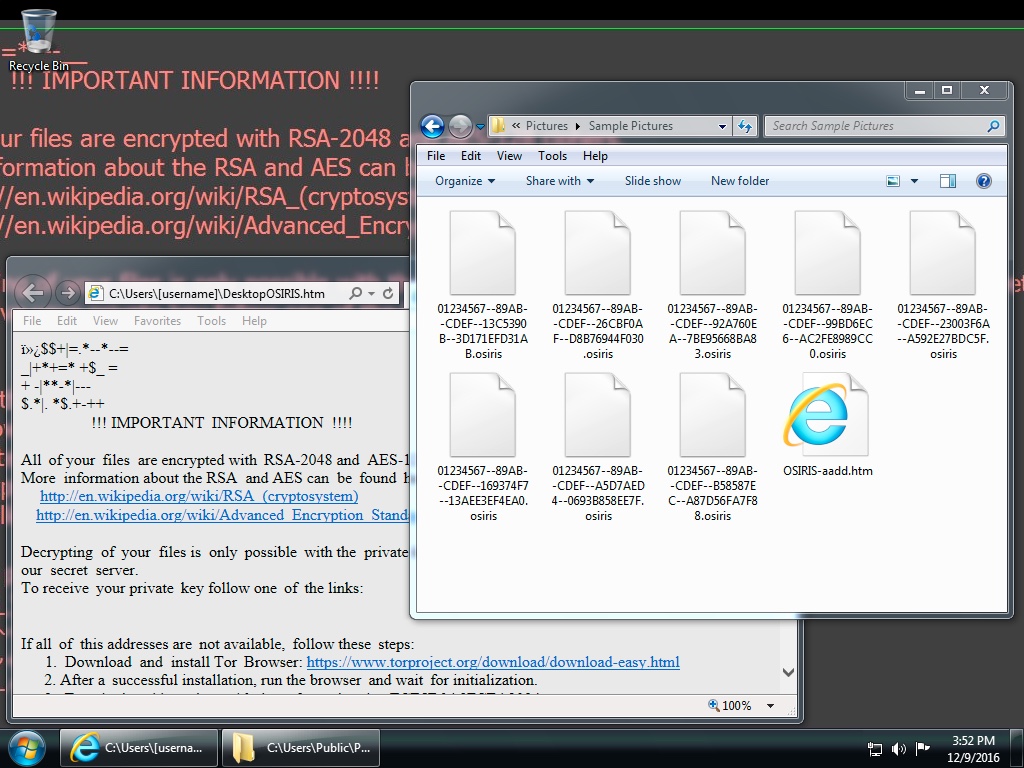
Shown above: Screen shot from an infected Windows desktop. Note the .osiris file extension.
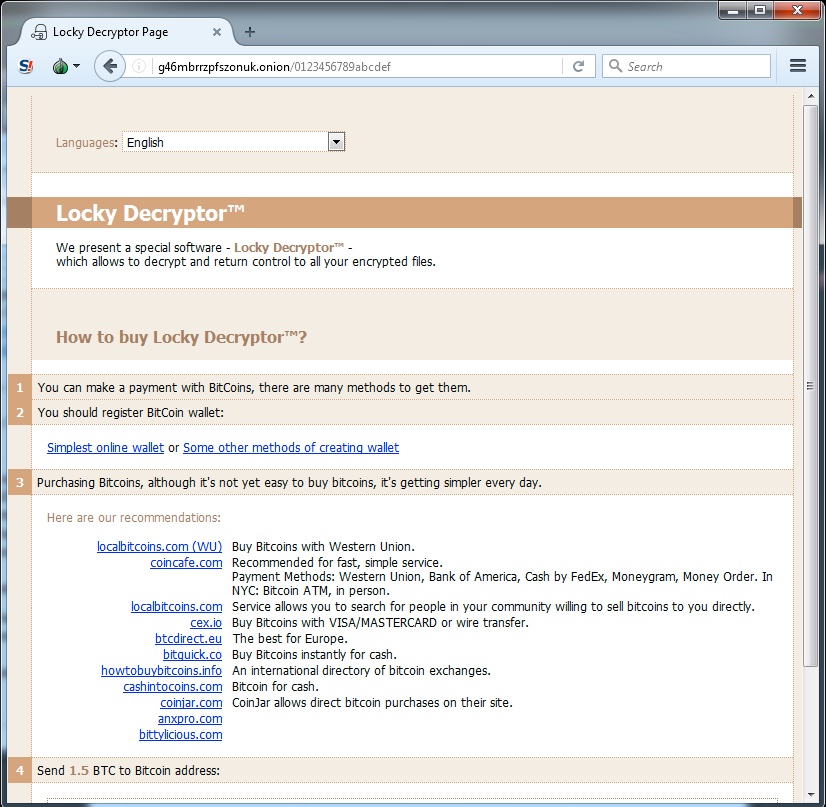
Shown above: Ransom payment was 1.5 bitcoin for the infections I generated.
Click here to return to the main page.
