2016-12-22 - FAKE WALGREENS MALSPAM DISTRIBUTES CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-12-22-Cerber-ransomware-traffic.pcap.zip 363.5 kB (363,456 bytes)
- 2016-12-22-Cerber-ransomware-traffic.pcap (534,456 bytes)
- 2016-12-22-Cerber-ransomware-files.zip 621.9 kB (621,897 bytes)
- 2016-12-22-Cerber-ransomware-downloaded-from-Word-macro.exe (297,642 bytes)
- 2016-12-22-Cerber-ransomware-README_FGS6_.hta (66,409 bytes)
- 2016-12-22-Cerber-ransomware-README_FGS6_.jpg (236,916 bytes)
- 2016-12-22-malspam-pushing-Cerber-ransomware-0823-UTC.eml (4,217 bytes)
- 2016-12-22-fake-invoice-with-malicious-Word-macro.doc (179,200 bytes)
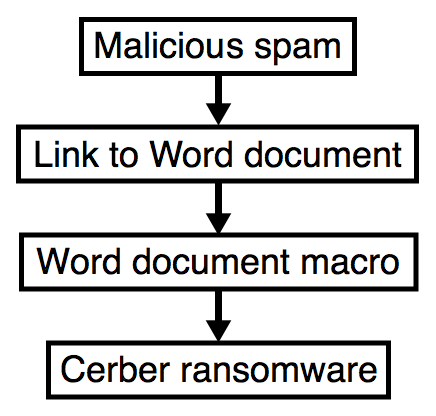
Shown above: Flowchart for this infection.
THE EMAIL
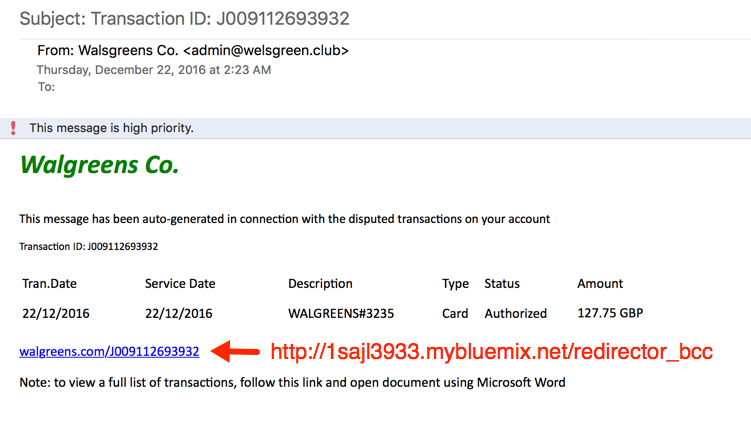
Shown above: Screenshot of the email.
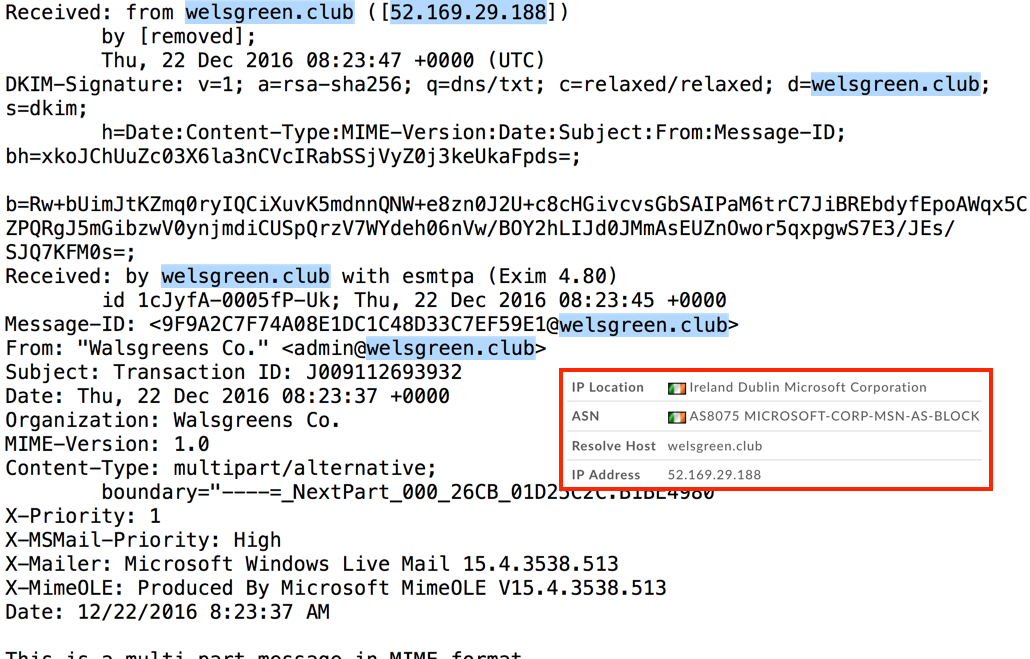
Shown above: Screenshot of the header information.
EMAIL HEADER LINES:
- Date: Thursday, 2016-12-22 at 08:23 UTC
- Subject: Transaction ID: J009112693932
- From: "Walsgreens Co." <admin@welsgreen[.]club>
- Received from mail server at: welsgreen[.]club - 52.169.29[.]188
- Message-ID: <9F9A2C7F74A08E1DC1C48D33C7EF59E1@welsgreen[.]club>
- X-Mailer: Microsoft Windows Live Mail 15.4.3538.513
MESSAGE TEXT:
Walgreens Co.
This message has been auto-generated in connection with the disputed transactions on your account
Transaction ID: J009112693932
Tran.Date Service Date Description Type Status Amount
22/12/2016 22/12/2016 WALGREENS#3235 Card Authorized 127.75 GBP
walgreens.com/J009112693932
Note: to view a full list of transactions, follow this link and open document using Microsoft Word
TRAFFIC
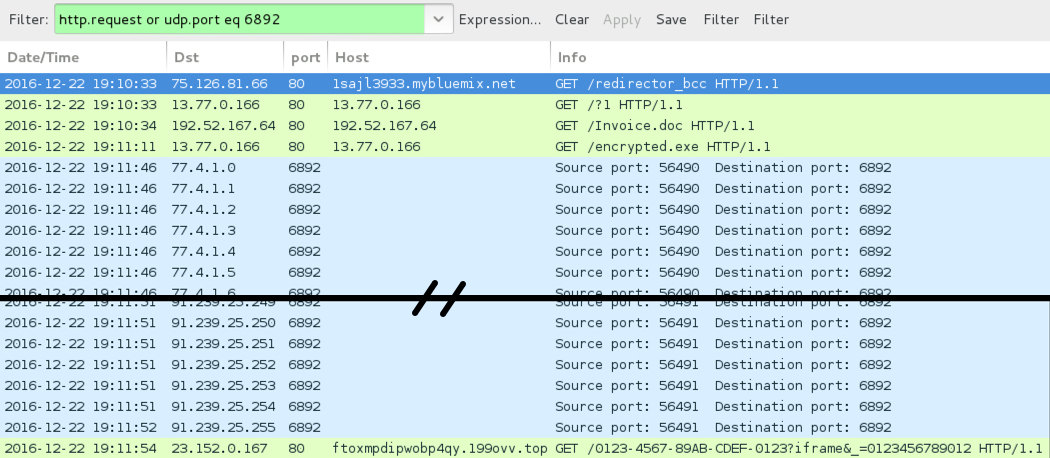
Shown above: Pcap of the infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- 75.126.81[.]66 port 80 - 1sajl3933.mybluemix[.]net - GET /redirector_bcc [Link from the malicious email]
- 13.77.0[.]166 port 80 - 13.77.0[.]166 - GET /?1 [redirects to Word document]
- 192.52.167[.]64 port 80 - 192.52.167[.]64 - GET /Invoice.doc [Word document download]
- 13.77.0[.]166 port 80 - 13.77.0[.]166 - GET /encrypted.exe [Word macro retrieving Cerber ransomware]
- 77.4.1[.]0 to 77.4.1[.]31 UDP port 6892 [Cerber ransomware post-infection UDP traffic]
- 77.15.1[.]0 to 77.15.1[.]26 UDP port 6892 [Cerber ransomware post-infection UDP traffic]
- 91.239.24[.]6 to 91.239.25[.]255 UDP port 6892 [Cerber ransomware post-infection UDP traffic]
- 23.152.0[.]167 port 80 - ftoxmpdipwobp4qy.199ovv[.]top [Cerber ransomware post-infection HTTP traffic]
FILE HASHES
WORD DOCUMENT FROM THE EMAIL LINK:
- SHA256 hash: 957ac9651ff18e086ab354499fcb6ceb5443213f549b041f1735d6e883b8be11 (179,200 bytes)
File name: Invoice.doc
CERBER RANSOMWARE AFTER ENABLING MACROS:
- SHA256 hash: 2e30967573a013437579ba420147878ea20a941e451ad0fe4d9444a3955e80a4 (297,642 bytes)
File path: C:\Users\[Username]\AppData\Local\Temp\14876.exe
IMAGES
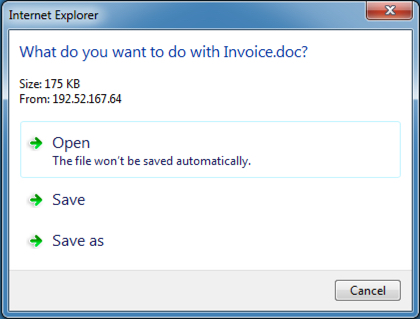
Shown above: Clicking on the email link gave me a Word document.
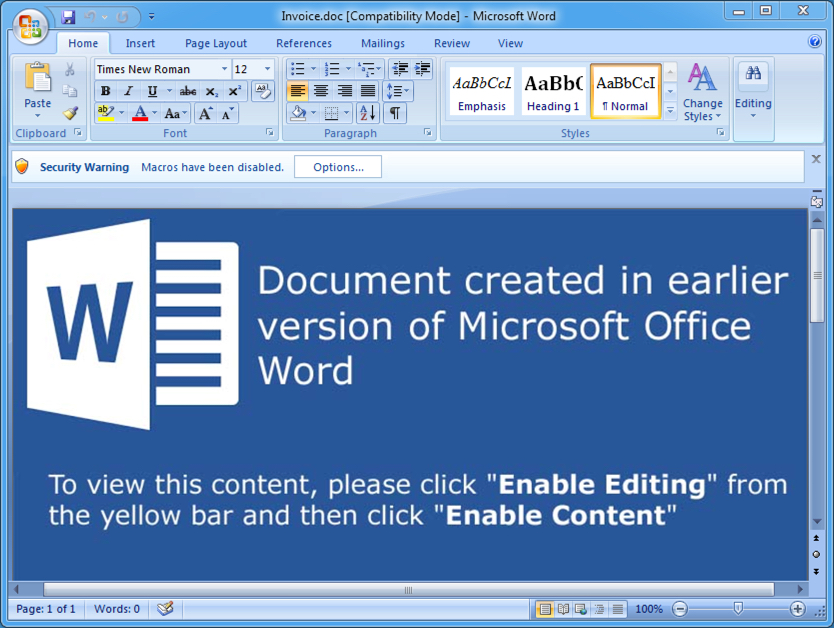
Shown above: Opening the Word document shows a message to enable macros, if they're not already enabled.
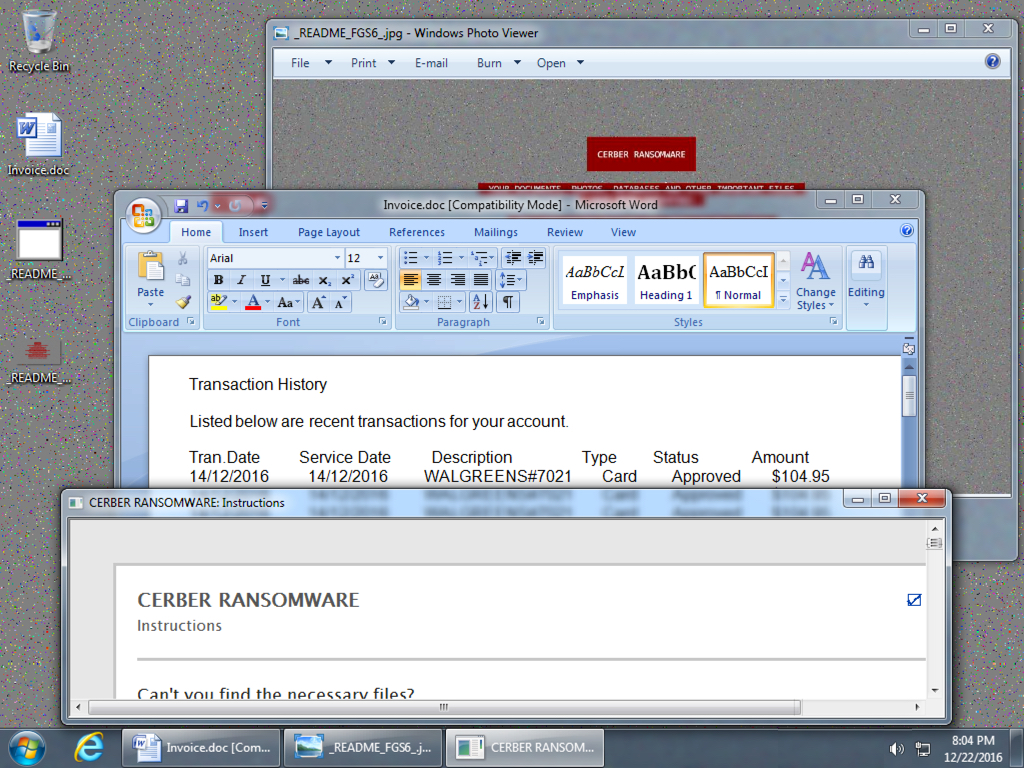
Shown above: Desktop of the infected Windows host.
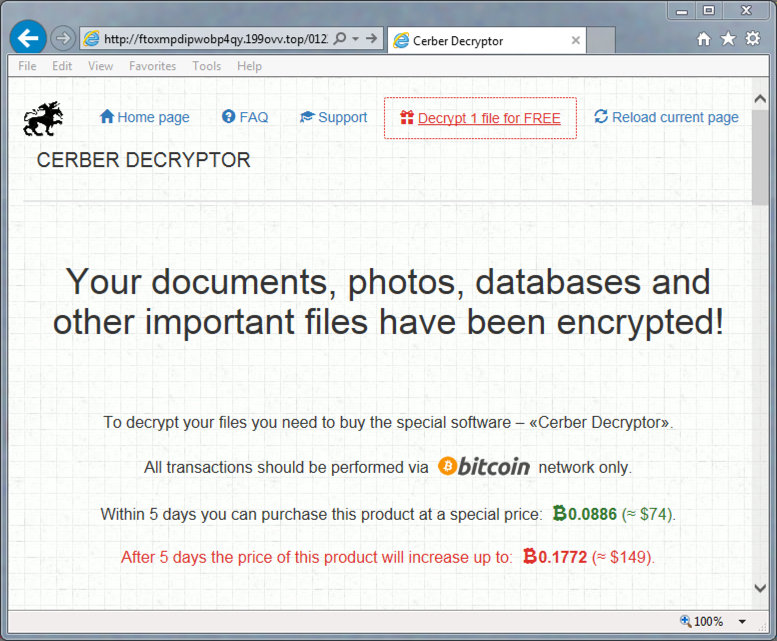
Shown above: 74 US dollars as a ransom payment? Seem cheap compared to what I'm used to seeing.
Click here to return to the main page.
