2016-12-30 - EK DATA DUMP (RIG-E, RIG-V, AND SUNDOWN EK)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-12-30-EK-data-dump-4-pcaps.zip 2.5 MB (2,490,432 bytes)
- 2016-12-30-EITest-Rig-E-sends-Chthoni-banking-Trojan.pcap (1,022,653 bytes)
- 2016-12-30-Sundown-EK-1st-run-sends-Terdot.A-Zloader.pcap (488,504 bytes)
- 2016-12-30-Sundown-EK-2nd-run-failed-payload.pcap (178,428 bytes)
- 2016-12-30-psuedoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (1,253,973 bytes)
- 2016-12-30-EK-data-dump-artifacts-and-malware.zip 1.1 MB (1,067,380 bytes)
- 2016-12-30-Cerber-ransomware-decryption-instructions_82CQLO_README_.hta (67,423 bytes)
- 2016-12-30-Cerber-ransomware-decryption-instructions_82CQLO_README_.jpg (238,214 bytes)
- 2016-12-30-EITest-Rig-E-artifact-OTTYUADAF.txt (1,137 bytes)
- 2016-12-30-EITest-Rig-E-flash-exploit.swf (13,700 bytes)
- 2016-12-30-EITest-Rig-E-landing-page.txt (85,336 bytes)
- 2016-12-30-EITest-Rig-E-payload-Chthonic.exe (159,744 bytes)
- 2016-12-30-Sundown-EK-1st-run-payload-Terdot.A-Zloader.exe (273,920 bytes)
- 2016-12-30-Sundown-EK-2nd-run-Flash-exploit-225.swf (29,707 bytes)
- 2016-12-30-Sundown-EK-2nd-run-Flash-exploit-542.swf (45,026 bytes)
- 2016-12-30-Sundown-EK-2nd-run-exploit-fvdvsdfv.png (52,674 bytes)
- 2016-12-30-Sundown-EK-landing-page-both-runs.txt (72,224 bytes)
- 2016-12-30-page-from-activaclinics_com-with-injected-EITest-script.txt (59,273 bytes)
- 2016-12-30-page-from-joellipman_com-with-injected-pseudoDarkleech-script.txt (67,423 bytes)
- 2016-12-30-pseudoDarkleech-Rig-V-artifact-OTTYUADAF.txt (1,137 bytes)
- 2016-12-30-pseudoDarkleech-Rig-V-flash-exploit.swf (12,681 bytes)
- 2016-12-30-pseudoDarkleech-Rig-V-landing-page.txt (5,191 bytes)
- 2016-12-30-pseudoDarkleech-Rig-V-payload-Cerber-ransomware.exe (298,648 bytes)
TRAFFIC

Shown above: Pcap from the 1st infection filtered in Wireshark

Shown above: Pcap from the 2nd infection filtered in Wireshark
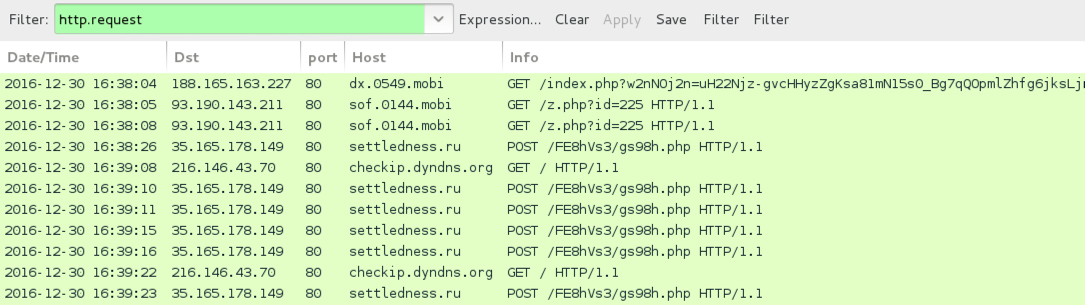
Shown above: Pcap from the 3rd infection filtered in Wireshark
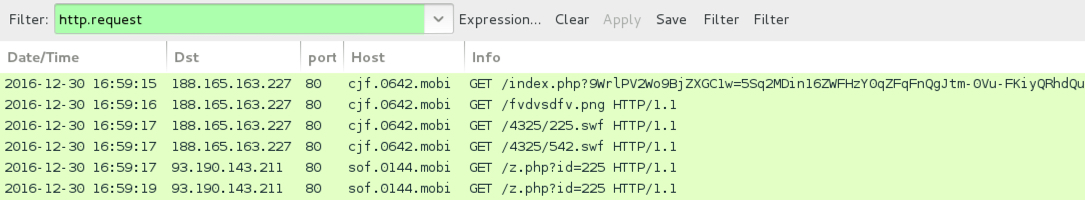
Shown above: Pcap from the 4th infection filtered in Wireshark
ASSOCIATED DOMAINS:
- activaclinics[.]com - Site compromised by the EITest campaign
- joellipman[.]com - Site compromised by the pseudoDarkleech campaign
- 191.101.31[.]118 port 80 - eqzv4.resonguterthet[.]top - Rig-E from the EITest campaign
- 46.30.43[.]195 port 80 - help.239homesforsale[.]com - Rig-V from the psuedoDarkleech campaign
- 188.165.163[.]227 port 80 - dx.0549[.]mobi - Sundown EK landing page & exploits (1st run)
- 188.165.163[.]227 port 80 - cjf.0642[.]mobi - Sundown EK landing page & exploits (2nd run)
- 93.190.143[.]211 port 80 - sof.0144[.]mobi - Sundown EK payload (both runs)
- 45.56.117[.]118 port 53 - TCP-based DNS query for pationare[.]bit caused by Chthonic banking Trojan
- 144.76.133[.]38 port 53 - TCP-based DNS query for pationare[.]bit caused by Chthonic banking Trojan
- 23.88.105[.]63 port 80 - pationare[.]bit - HTTP traffic caused by Chthonic banking Trojan
- 1.22.15[.]0 to 1.22.15[.]31 (1.22.15[.]0/27) UDP port 6892 - post-infection UDP traffic caused by Cerber ransomware
- 2.23.16[.]0 to 2.23.16[.]31 (2.23.16[.]0/27) UDP port 6892 - post-infection UDP traffic caused by Cerber ransomware
- 91.239.24[.]0 to 91.239.25[.]255 (91.239.24[.]0/23) UDP port 6892 - post-infection UDP traffic caused by Cerber ransomware
- 31.214.157[.]47 port 80 - p27dokhpz2n7nvgr.14zwws[.]top - post-infection HTTP traffic caused by Cerber ransomware
- port 80 - checkip.dyndns[.]org - IP address check by Terdot.A/Zloader
- 35.165.178[.]149 port 80 - settledness[.]ru - HTTP traffic caused by Terdot.A/Zloader
FILE HASHES
EXPLOITS:
- SHA256 hash: ce4eacb09dc69865c718f7bda3296d535ad71661867129bdd5539014c42f2d65
File description: Rig-E Flash exploit seen on 2016-12-30
File size: 14,088 bytes
- SHA256 hash: 337fe7adaae5b5ab1029ab73f09dd5383b36afe203ff8b933ffab00d7610ae36
File description: Rig-V Flash exploit seen on 2016-12-30
File size: 29,406 bytes
- SHA256 hash: cf730db69db781c515919b26ac46698c5249a62a5413edd11e1dd92fd3a44acb
File description: Sundown EK Flash exploit sent as 225.swf on 2016-12-30
File size: 29,707 bytes
- SHA256 hash: 67d598c6acbd6545ab24bbd44cedcb825657746923f47473dc40d0d1f122abb6
File description: Sundown EK Flash exploit sent as 542.swf on 2016-12-30
File size: 45,026 bytes
- SHA256 hash: fc4bb31eb4e3d533e369b3687d72abb263937c698019b4f50229a5ca2d083bbb
File description: Exploit sent by Sundown EK as fvdvsdfv.png on 2016-12-30 (see this for details)
File size: 52,674 bytes
PAYLOADS:
- SHA256 hash: c7ad7bf63ae78dfaefa9784f2375d2e88752c48273373581988db9c46ea1a0f6
File description: Chthonic banking Trojan sent by Rig-E from the EITest campaign on 2016-12-30 File size: 159,744 bytes
- SHA256 hash: efcbb009243e2f590351c1bdd6456e140d2711439906674d8d57a17f5c287c98
File description: Cerber ransomware sent by Rig-V from the pseudoDarkleech campaign on 2016-12-30
File size: 298,648 bytes
- SHA256 hash: c4b894094c08ea234a2a2652f77383f4a22c5402918c330a7ad6f39520dcc53c
File description: Terdot.A/Zloader sent by Sundown EK on 2016-12-30
File size: 273,920 bytes
Click here to return to the main page.
