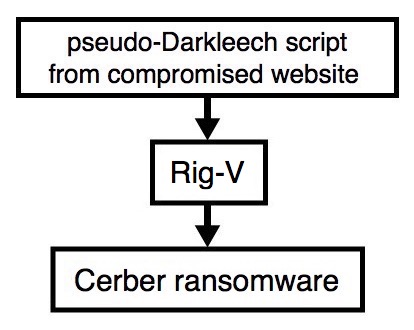
2017-01-01 - PSEUDO-DARKLEECH RIG-V FROM 109.234.36[.]133 SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-01-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap.zip 2.9 MB (2,876,879 bytes)
- 2017-01-01-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (3,147,060 bytes)
- 2017-01-01-pseudoDarkleech-Rig-V-and-Cerber-ransomware-files.zip 898.8 kB (898,790 bytes)
- 2017-01-01-pseudoDarkleech-Rig-V-flash-exploit.swf (37,722 bytes)
- 2017-01-01-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-rad53AB9.tmp.exe (231,624 bytes)
- 2017-01-01-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-rad83D45.tmp.exe (231,624 bytes)
- 2017-01-01-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-radA2306.tmp.exe (231,624 bytes)
- 2017-01-01-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-radC28C1.tmp.exe (231,624 bytes)
BACKGROUND ON RIG EXPLOIT KIT:
- I'm routinely intercepting 2 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns and RC4 encryption for the payload. Used by the Afraidgate, EITest, and pseudoDarkleech campaigns.
- Rig-E: a variant with old URL patterns, but uses with RC4 encryption for the payload. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
BACKGROUND ON THE PSEUDO-DARKLEECH CAMPAIGN:
- My most recent in-depth write-up on the pseudoDarkleech campaign can be found here.
OTHER NOTES:
- Just a quick check on the first day of the new year to see what's going on with Rig-V from the pseudoDarkleech campaign.
Shown above: Flowchart for this infection traffic.
TRAFFIC
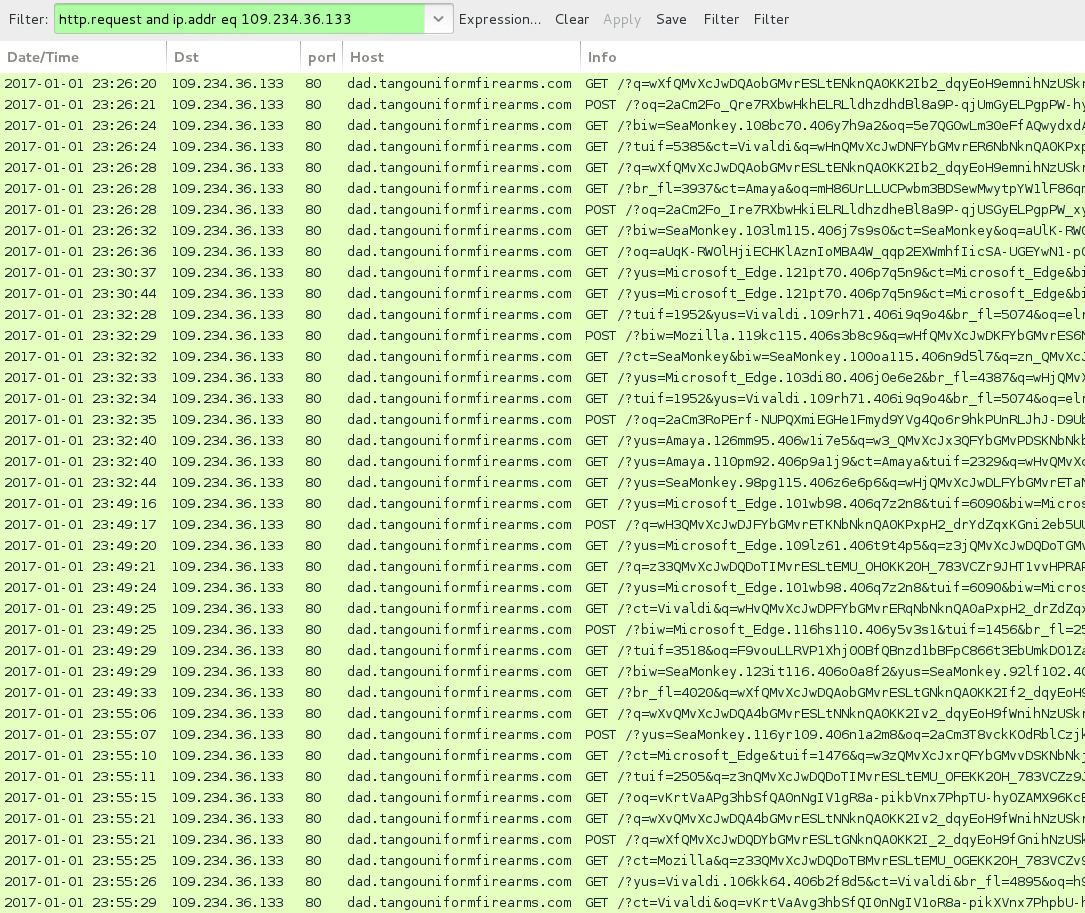
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 109.234.36[.]133 port 80 - dad.tangouniformfirearms[.]com - Rig-V
FILE HASHES
RIG-V FLASH EXPLOIT:
- SHA256 hash: 8f3c7c6189367ad85d3bed9a159203948603870f01f095a787cd85bdd4e3bf41 (37,722 bytes)
File description: Rig-V Flash exploit seen on 2017-01-01
RIG-V PAYLOAD (CERBER RANSOMWARE):
- SHA256 hash: 993a83e4930edf11d5d8bde9ce803ce9948776457f77530079692ca7541aebd2 (231,624 bytes)
File location: C:\Users\[username]\AppData\Local\Temp\rad53AB9.tmp.exe
- SHA256 hash: c6cb420c856ae673bd7d7585bf078b14e53be798e5013579309fe6c3e9edab66 (231,624 bytes)
File location: C:\Users\[username]\AppData\Local\Temp\rad83D45.tmp.exe
- SHA256 hash: aceac1915f214f9d075751092dd8c4ea3ebde5da355ebeffce5ddee6c3e4fe48 (231,624 bytes)
File location: C:\Users\[username]\AppData\Local\Temp\radA2306.tmp.exe
- SHA256 hash: d2f22af28c20a89aea20de312002a30df8433c86e915bb550972cdf150c0d9c9 (231,624 bytes)
File location: C:\Users\[username]\AppData\Local\Temp\radC28C1.tmp.exe
Click here to return to the main page.