2017-01-05 - "BLANK SLATE" CAMPAIGN SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-05-Cerber-ransomware-infection-traffic.pcap.zip 235.4 kB (235,446 bytes)
- 2017-01-05-Cerber-ransomware-infection-traffic.pcap (332,731 bytes)
- 2017-01-05-Blank-Slate-emails-and-Cerber-ransomware.zip 651.9 kB (651,891 bytes)
- 2017-01-04-Blank-Slate-malspam-2312-UTC.eml (36,691 bytes)
- 2017-01-04-Blank-Slate-malspam-2327-UTC.eml (45,945 bytes)
- 2017-01-05-Blank-Slate-malspam-0859-UTC.eml (38,580 bytes)
- 402402188984588.zip (28,241 bytes)
- 7318620611899.zip (26,845 bytes)
- 954461.zip (33,708 bytes)
- Roaming.exE (231,530 bytes)
- 2017-01-05-Cerber-ransomware_NQIB7_README_.hta (67,448 bytes)
- 2017-01-05-Cerber-ransomware_NQIB7_README_.jpg (229,420 bytes)
NOTES:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
EMAILS
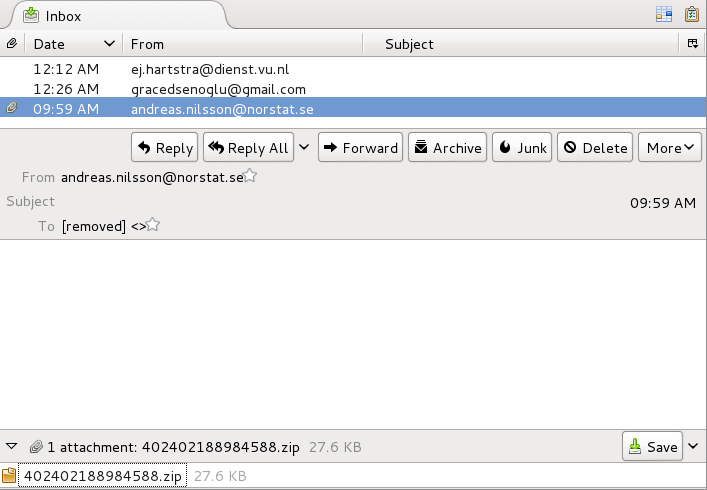
Read: date/time -- received from mailserver at -- message-ID -- sender (spoofed) -- subject -- attachment name -- extracted file
2017-01-04 23:12 UTC -- skyonline[.]net[.]ar -- <148357156002.25068.7364238338216249641@skyonline[.]net[.]ar>
<ej.hartstra@dienst.vu.nl> -- (no subject) -- 7318620611899.zip -- 12027.doc
2017-01-04 23:26 UTC -- 175.202.17[.]89 -- <148357240588.3135.1777837317377017010@175.202.17[.]89>
<gracedsenoglu@gmail.com> -- (no subject) -- 954461.zip -- 24591.doc
2017-01-05 08:59 UTC -- skyonline[.]net[.]ar -- <148360676836.3137.13620895256758905128@skyonline[.]net[.]ar>
<andreas.nilsson@norstat.se> -- (no subject) -- 402402188984588.zip -- 31879.doc
TRAFFIC
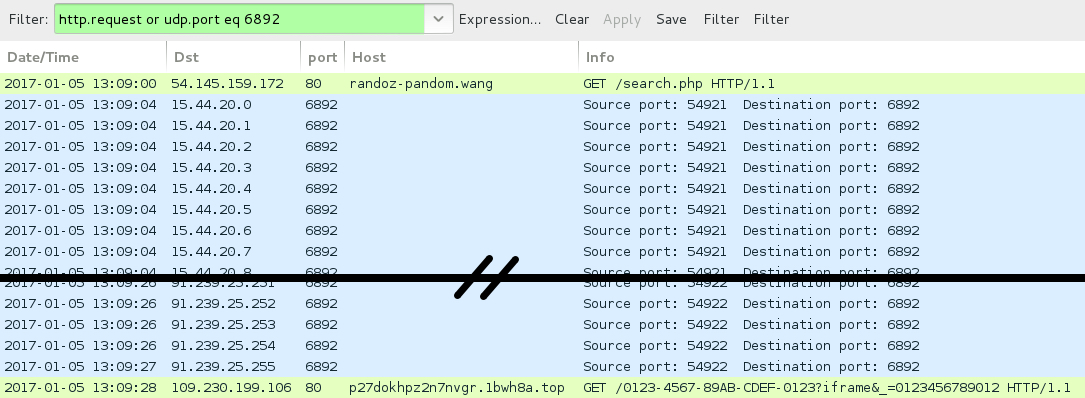
Shown above: Pcap of the infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- 54.145.159[.]172 port 80 - randoz-pandom[.]wang - GET /search.php - Word macro downloading the Cerber ransomware
- 15.44.20[.]0 to 15.44.20[.]31 (15.44.20[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 16.43.12[.]0 to 16.43.12[.]31 (16.43.12[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.239.24[.]0 to 91.239.25[.]255 (91.239.24[.]0/23) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.134.123[.]56 port 80 - p27dokhpz2n7nvgr.1bwh8a[.]top - Cerber ransomware post-infection HTTP traffic
FILE HASHES
EXTRACTED WORD DOCUMENTS:
- SHA256 hash: 748a3c119026f2579867763c33f6fd16375e8f62a38be580654c726709484b94 (65,024 bytes)
File name: 12027.doc
- SHA256 hash: 8745da2b43f07167e6f2c2eb84a646c0feb236671f206047fc2cdc1081b3f982 (79,360 bytes)
File name: 24591.doc
- SHA256 hash: b36bb18faa7adea81436651e6062df0200dca5a578842dc5d6ea03377c4775e9 (68,096 bytes)
File name: 31879.doc
DOWNLOADED MALWARE (CERBER RANSOMWARE):
- SHA256 hash: aeab730e99827a820e318f43a57463f3dcdcb5182b4e41e71a4d5f436623e792 (231,530 bytes)
File path: C:\Users\[username]\Roaming\Roaming.exE
Click here to return to the main page.
