2017-01-30 - HANCITOR INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-30-Hancitor-infection-traffic-2-pcaps.zip 7.8 MB (7,847,495 bytes)
- 2017-01-30-Hancitor-infection-traffic-1-of-2-retreiving-Word-doc.pcap (206,094 bytes)
- 2017-01-30-Hancitor-infection-traffic-2-of-2-post-infection-activity.pcap (8,403,581 bytes)
- 2017-01-30-Hancitor-email-and-malware.zip 255.9 kB (255,933 bytes)
- 2017-01-30-UPS-malspam-1713-UTC.eml (1,192 bytes)
- 2017-01-30-possible-Terdot.A-Zloader-from-UPS-malspam.exe (190,976 bytes)
- UPS_leonard.doc (190,464 bytes)
NOTES:
- More activity similar an ISC diary I wrote covering Hancitor/Pony/Vawtrak from 2017-01-10 (link).
- Today it's a fake parcel information message.
- I'm seeing artifacts on the infected host, but instead of Vawtrak, but I'm getting alerts for Zloader.
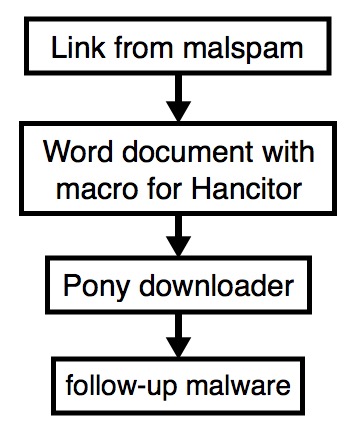
Shown above: Flowchart for this infection traffic.
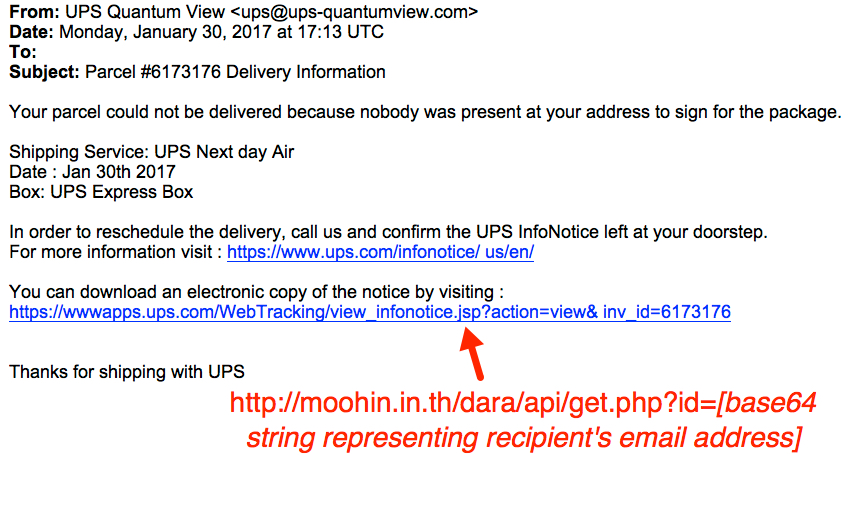
Shown above: Screenshot of the email.
EMAIL HEADERS:
- Date: Monday 2017-01-30 at 17:13 UTC
- From: UPS Quantum View <ups@ups-quantumview[.]com>
- Subject: Parcel #6173176 Delivery Information
- Message-ID: <964F02DE.2937FEE2@ups-quantumview[.]com>

Shown above: Word document downloaded from link in the email.
TRAFFIC
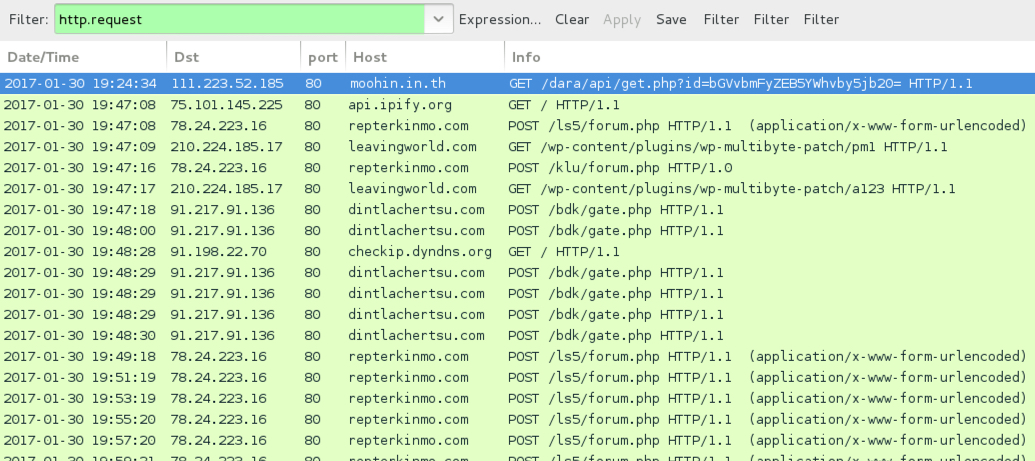
Shown above: Traffic from the infection filtere in Wireshark.
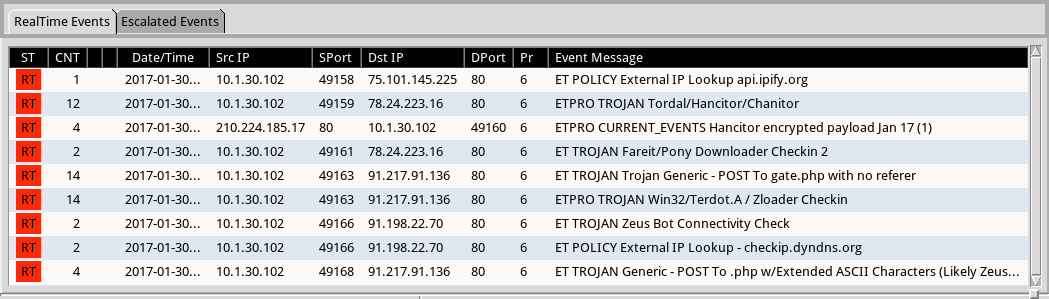
Shown above: Some alerts on the post-infection traffic from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion.
ASSOCIATED NETWORK TRAFFIC:
- 111.223.52[.]185 port 80 - moohin[.]in[.]th - GET /dara/api/get.php?id=[base64 characters representing recipient's email address]
- api.ipify[.]org - GET / [IP address check by the infected host]
- 78.24.223[.]16 port 80 - repterkinmo[.]com - POST /ls5/forum.php [Hancitor check-in]
- 210.224.185[.]17 port 80 - leavingworld[.]com - GET /wp-content/plugins/wp-multibyte-patch/pm1 [Download Pony DLL]
- 78.24.223[.]16 port 80 - repterkinmo[.]com - POST /klu/forum.php [Hancitor check-in]
- 210.224.185[.]17 port 80 - leavingworld[.]com - GET /wp-content/plugins/wp-multibyte-patch/a123 [follow-up download]
- 91.217.91[.]136 port 80 - dintlachertsu[.]com - POST /bdk/gate.php [Terdot.a/Zloader checkin]
FILE HASHES
WORD DOCUMENT:
- SHA256 hash: 5a3c843bfcf31c2f2f2a2e4d5f5967800a2474e07323e8baa46ff3ac64d60d4a (190,464 bytes)
File description: Hancitor maldoc (Word document) on 2017-01-30
FOLLOW-UP MALWARE DOWNLOADED BY PONY:
- SHA256 hash: ed0876f34632254c783ae99b34dde1103e345d1168133f4e3a756454f6845bb0 (190,976 bytes)
File description: Follow-up malware (EXE file) on 2017-01-30, probable Terdot.A/Zloader
Click here to return to the main page.