2017-02-01 - HANCITOR INFECTION WITH SEND SAFE ENTERPRISE (SSE) SPAMBOT TRAFFIC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-02-01-Hancitor-infection-with-SendSafe-spambot-traffic.pcap.zip 10.4 MB (10,377,013 bytes)
- 2017-02-01-Hancitor-infection-with-SendSafe-spambot-traffic.pcap (12,650,233 bytes)
- 2017-02-01-Hancitor-malspam-4-examples.zip 4.1 kB (4,067 bytes)
- 2017-02-01-Hancitor-malspam-1641-UTC.eml (1,638 bytes)
- 2017-02-01-Hancitor-malspam-1642-UTC.eml (1,640 bytes)
- 2017-02-01-Hancitor-malspam-1812-UTC.eml (836 bytes)
- 2017-02-01-Hancitor-malspam-1832-UTC.eml (811 bytes)
- 2017-02-01-malware-from-Hancitor-infection.zip 1.7 MB (1,709,489 bytes)
- 2017-02-01-Invoice_jeremycombs.doc (201,216 bytes)
- 2017-02-01-follow-up-malware-Terdot.A-Zloader.exe (258,048 bytes)
- 2017-02-01-follow-up-malware-24c.exe (1,938,432 bytes)
NOTES:
- More malspam similar to something I posted in an ISC diary I wrote covering Hancitor/Pony/Vawtrak malspam from 2017-01-10 (link).
- Today it's a fake invoice message.
- 2025 note: After reviewing the traffic, the additional SMTP activity was cased by Send Safe Enterprise (SSE) spambot malware.
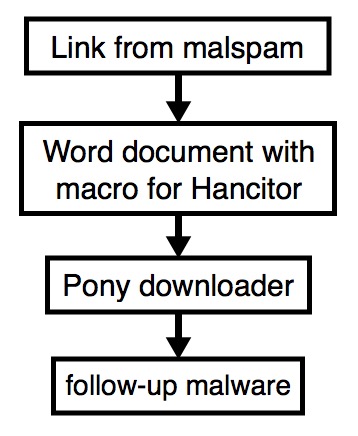
Shown above: Flowchart for this infection traffic.

Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date: Wednesday 2017-02-01 at 16:41 UTC
- Date: Wednesday 2017-02-01 at 16:42 UTC
- Date: Wednesday 2017-02-01 at 18:12 UTC
- Date: Wednesday 2017-02-01 at 18:32 UTC
- From (spoofed): "George Cromwell" <gcromwell@gcromwell@le-bernardin[.]com>
- From (spoofed): "George Cromwell" <gcromwell@gcromwell@le-bernardin[.]com>
- From (spoofed): "gcromwell@le-bernardin[.]com" <gcromwell@gcromwell@le-bernardin[.]com>
- From (spoofed): "gcromwell@thomaskeller[.]com" <gcromwell@thomaskeller[.]com>
- Subject: FW: Re: invoice #6987530
- Subject: FW: Re: invoice # 6658504
- Subject: FW: Re: invoice #50266207
- Subject: FW: Re: invoice #64028380
- Message-ID: <26FMRQTQ.0598363@recknor[.]com>
- Message-ID: <GA5Z0Q0E.6605786@rote-seiten[.]com>
- Message-ID: <80B41CD4.1A4EE0F7@le-bernardin[.]com>
- Message-ID: <6042DE27.A20367EC@thomaskeller[.]com>

Shown above: Word document downloaded from link in the email.
TRAFFIC
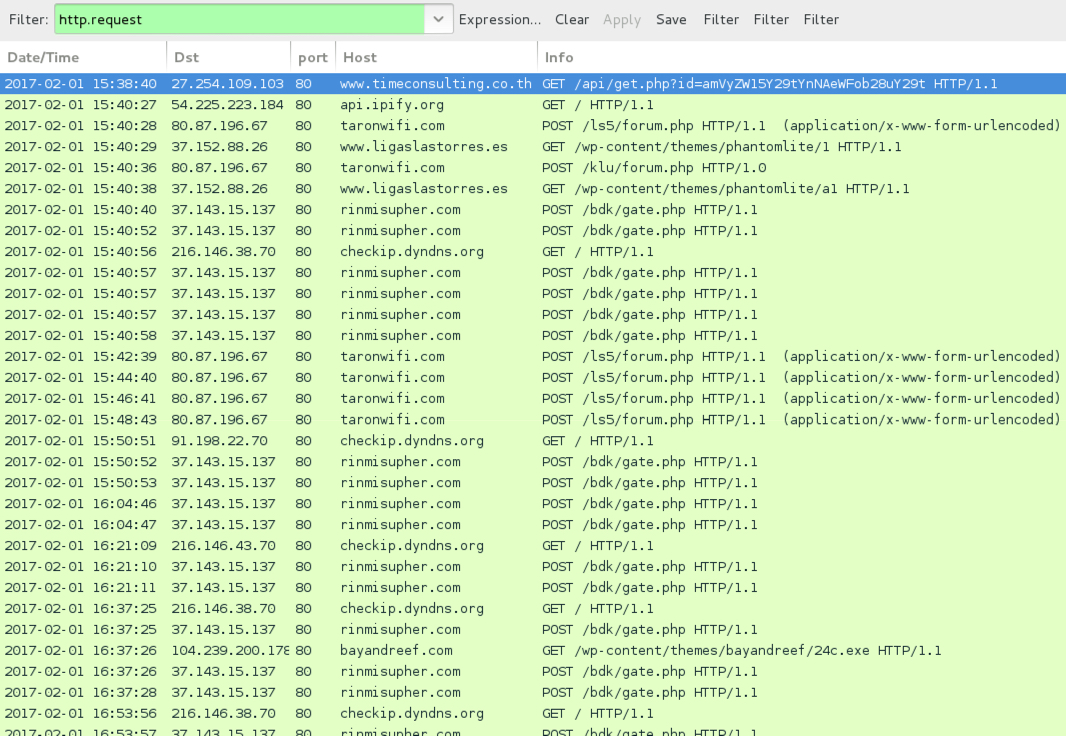
Shown above: Traffic from the infection filtered in Wireshark.
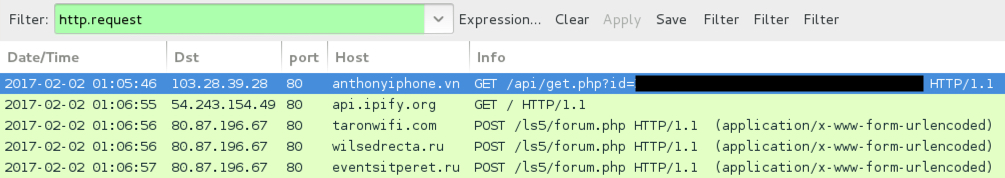
Shown above: Another try using a different URL from one of the emails.
ASSOCIATED DOMAINS:
- 27.254.109[.]103 port 80 - www.timeconsulting[.]co[.]th - GET /api/get.php?id=[base64 characters representing recipient's email address]
- api.ipify[.]org - GET / [IP address check by the infected host]
- 80.87.196[.]67 port 80 - taronwifi[.]com - POST /ls5/forum.php [Hancitor check-in]
- 37.152.88[.]26 port 80 - www.ligaslastorres[.]es - GET /wp-content/themes/phantomlite/1 [Download Pony DLL]
- 80.87.196[.]67 port 80 - taronwifi[.]com - POST /klu/forum.php
- 37.152.88[.]26 port 80 - www.ligaslastorres[.]es - GET /wp-content/themes/phantomlite/a1 [follow-up download]
- 37.143.15[.]137 port 80 - rinmisupher[.]com - POST /bdk/gate.php
- checkip.dyndns[.]org - GET / [IP address check by the infected host]
- 104.239.200[.]178 port 80 - bayandreef[.]com - GET /wp-content/themes/bayandreef/24c.exe
- 91.220.131[.]24 port 50012 - 91.220.131[.]24 - UDP traffic
- 91.220.131[.]24 port 50011 - 91.220.131[.]24 - HTTPS/SSL/TLS traffic over TCP port 50011
- Various IP addresses port 25 - various domains - Attempted SMTP traffic
NOTE: No spam was sent from the infected Windows host, but it did try sending emails using the spoofed sender address gcromwell@thomaskeller[.]com (the same sender address from the email used to infect this particular Windows host).
ASSOCIATED DOMAINS NOTED FROM SECOND ATTEMPT:
- 103.28.39[.]28 port 80 - anthonyiphone[.]vn - GET /api/get.php?id=[base64 characters representing recipient's email address]
- 80.87.196[.]67 port 80 - wilsedrecta[.]ru - POST /ls5/forum.php
- 80.87.196[.]67 port 80 - eventsitperet[.]ru - POST /ls5/forum.php
FILE HASHES
WORD DOCUMENT:
- SHA256 hash: 5e41582be6df17aa6691ab526a93fcfacd612c05618b576988a67acc7be9a145 (201,216 bytes)
File description: Hancitor maldoc (Word document) on 2017-02-01
TERDOT.A/ZLOADER:
- SHA256 hash: c01582eb77ccbc1977db81c3ecf9b5297e28897f91be0f7e4af24b14fbf3cf59 (258,048 bytes)
File description: Terdot.A/Zloader on 2017-02-01
FOLLOW-UP DOWNLOAD:
- SHA256 hash: ffffd99fdc813e58bc9282101036d055a1ea937281b3202132961e5377f34962 (1,938,432 bytes)
File description: Follow-up malware downloaded on 2017-02-01 (SendSafe Spambot malware)
IMAGES
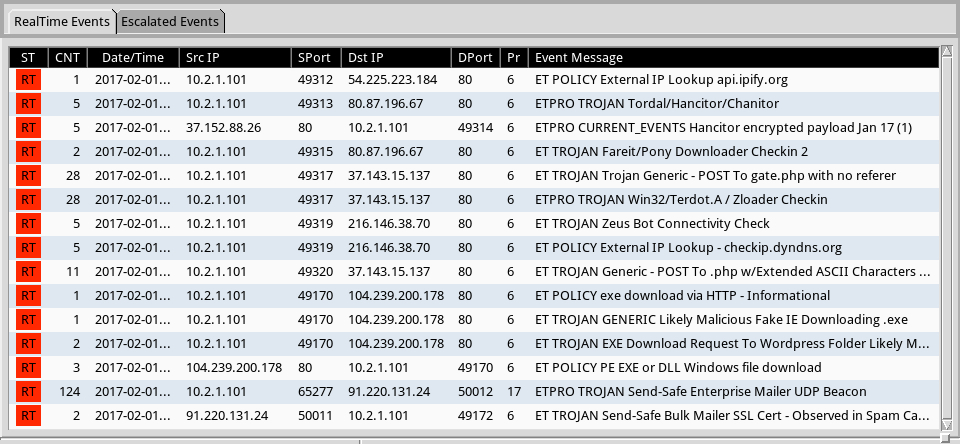
Shown above: Some alerts on the post-infection traffic from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion.
Click here to return to the main page.