2017-02-06 - HANCITOR INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-02-06-Hancitor-infection-traffic.pcap.zip 8.4 MB (8,377,226 bytes)
- 2017-02-06-Hancitor-infection-traffic.pcap (9,171,958 bytes)
- 2017-02-06-Hancitor-malspam-1550-UTC.eml.zip 1.2 kB (1,215 bytes)
- 2017-02-06-Hancitor-malspam-1550-UTC.eml (1,880 bytes)
- 2017-02-06-malware-from-Hancitor-infection.zip 327.1 kB (327,104 bytes)
- 2017-02-06-Terdot.A-Zloader-from-Hancitor-malspam.exe (296,448 bytes)
- USPS_invoice_reggie.cage.doc (204,288 bytes)
NOTES:
- More malspam similar to an ISC diary I wrote covering Hancitor/Pony/Vawtrak malspam on 2017-01-10 (link), but today it's Zloader instead of Vawtrak.
- Today's email was disguised as a USPS parcel notification.
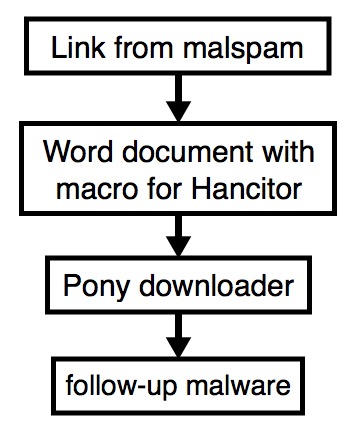
Shown above: Flowchart for this infection traffic.
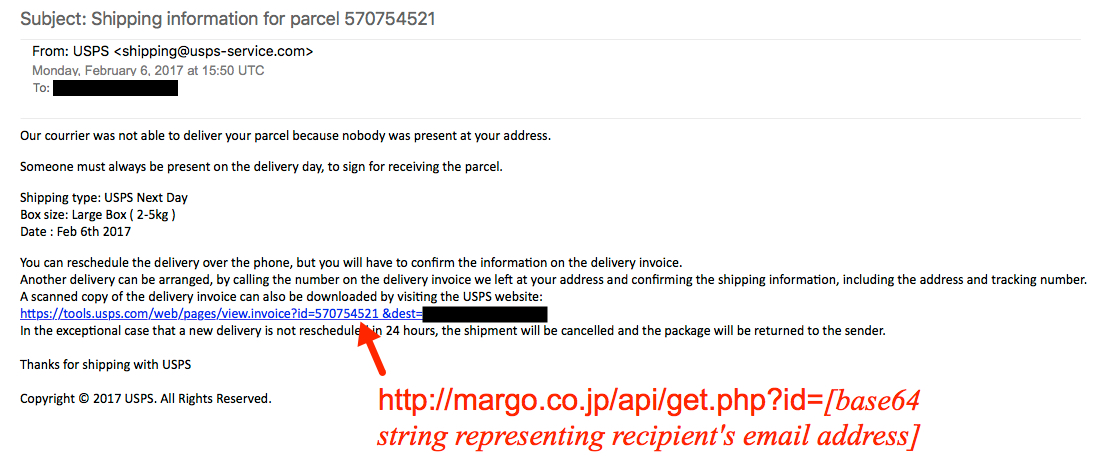
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date: Monday 2017-02-06 at 15:50 UTC
- From (spoofed): "USPS" <shipping@usps-service[.]com>
- Subject: Shipping information for parcel 570754521
- Message-ID: <5D2F5530.4C8BB703@usps-service[.]com>
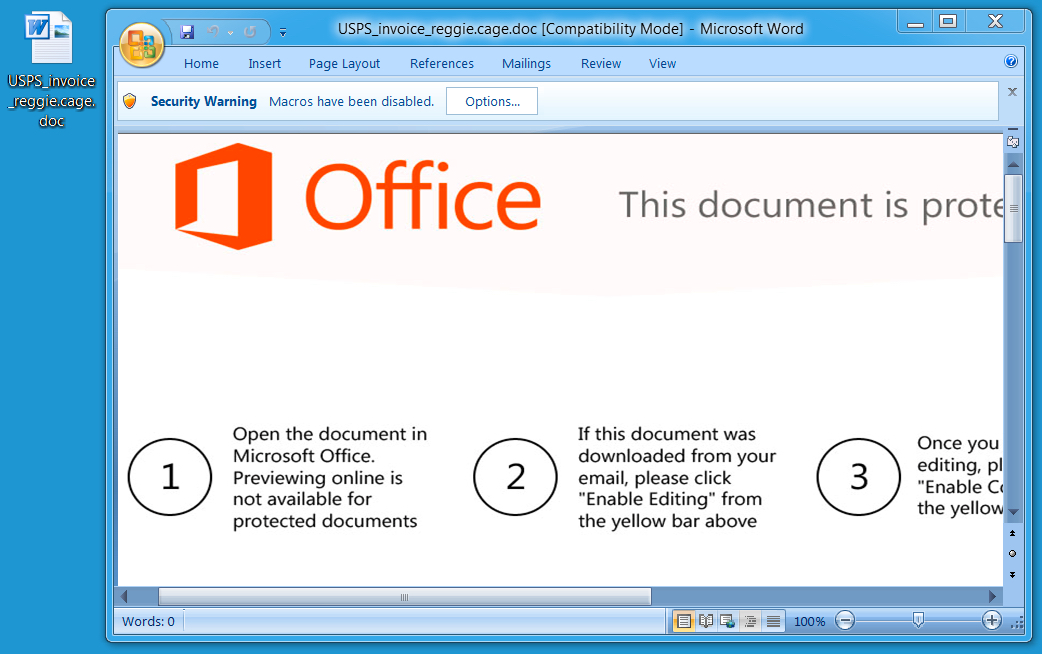
Shown above: Word document downloaded from link in the email.
TRAFFIC
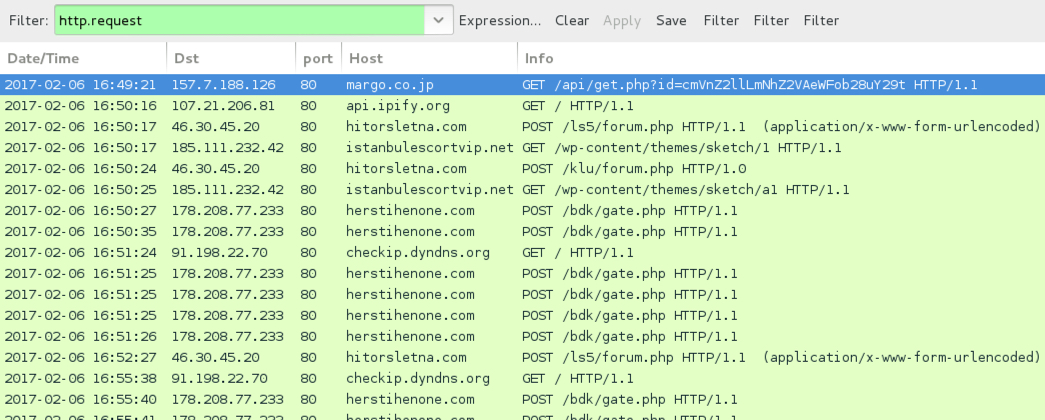
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 157.7.188[.]126 port 80 - margo[.]co[.]jp - GET /api/get.php?id=[base64 characters representing recipient's email address]
- api.ipify[.]org - GET / [IP address check by the infected host]
- 46.30.45[.]20 port 80 - hitorsletna[.]com - POST /ls5/forum.php [Hancitor check-in]
- 185.111.232[.]42 port 80 - istanbulescortvip[.]net - /wp-content/themes/sketch/1 [Download Pony DLL]
- 46.30.45[.]20 port 80 - hitorsletna[.]com - POST /klu/forum.php
- 185.111.232[.]42 port 80 - istanbulescortvip[.]net - GET /wp-content/themes/sketch/a1 [follow-up download]
- 178.208.77[.]233 port 80 - herstihenone[.]com - POST /bdk/gate.php
- checkip.dyndns[.]org - GET / [IP address check by the infected host]
FILE HASHES
WORD DOCUMENT:
- SHA256 hash: e3f26b8c434e47984ca81cc80e8b9c734b70708d7a5bcaf9e839292e4ccd4298 (204,288 bytes)
File description: Hancitor maldoc (Word document) on 2017-02-06
TERDOT.A/ZLOADER:
- SHA256 hash: 3af7cdf36d1542a2723487f40b58f735e03058a4e28010861070cf9a8151b261 (296,448 bytes)
File description: Terdot.A/Zloader on 2017-02-06
Click here to return to the main page.