2017-02-07 - HANCITOR INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-02-07-Hancitor-infection-traffic.pcap.zip 8.7 MB (8,659,436 bytes)
- 2017-02-07-Hancitor-infection-traffic.pcap (9,494,012 bytes)
- 2017-02-07-Hancitor-malspam-1607-UTC.eml.zip 1.8 kB (1,820 bytes)
- 2017-02-07-Hancitor-malspam-1607-UTC.eml (3,936 bytes)
- 2017-02-07-malware-from-Hancitor-infection.zip 293.3 kB (293,267 bytes)
- 2017-02-07-hancitor-maldoc.doc (194,560 bytes)
- 2017-02-07-follow-up-malware-Terdot.A-Zloader.exe (255,488 bytes)
NOTES:
- More malspam with a link to a malicious Word document.
- Today's email was disguised as an eFax notification.
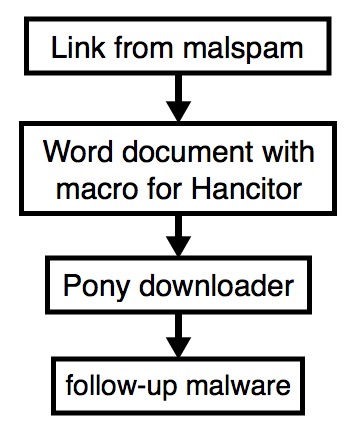
Shown above: Flowchart for this infection traffic.

Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date: Tuesday, 2017-02-06 at 16:07 UTC
- From (spoofed): "eFax" <messaging@efax[.]com>
- Subject: You received a new eFax from 202-935-2034
- Message-ID: <B7629267.F8732A87@efax[.]com>
Shown above: Word document downloaded from link in the email.
TRAFFIC
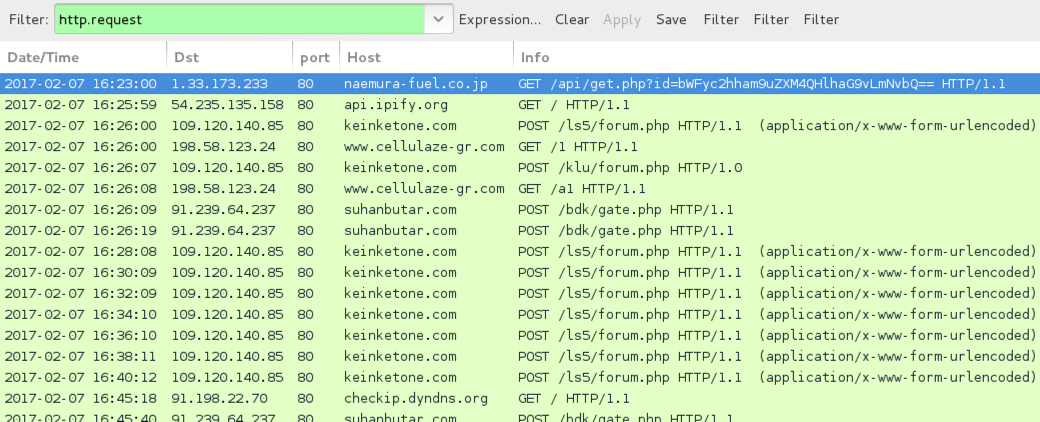
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 1.33.173[.]233 port 80 - naemura-fuel[.]co[.]jp - GET /api/get.php?id=[base64 characters representing recipient's email address]
- api.ipify[.]org - GET / [IP address check by the infected host]
- 109.120.140[.]85 port 80 - keinketone[.]com - POST /ls5/forum.php [Hancitor check-in]
- 198.58.123[.]24 port 80 - www.cellulaze-gr[.]com - /1 [Download Pony DLL]
- 109.120.140[.]85 port 80 - keinketone[.]com - POST /klu/forum.php
- 198.58.123[.]24 port 80 - www.cellulaze-gr[.]com - GET /a1 [follow-up download]
- 91.239.64[.]237 port 80 - suhanbutar[.]com - POST /bdk/gate.php
- checkip.dyndns[.]org - GET / [IP address check by the infected host]
FILE HASHES
WORD DOCUMENT:
- SHA256 hash: 2006bc2eb231815ba3f6aaae10d29a04e52aaec3f3c2d40a7f7274828b85eb9b (194,560 bytes)
File description: Hancitor maldoc (Word document) on 2017-02-07
TERDOT.A/ZLOADER:
- SHA256 hash: e91f109f221072475ef853b949b55b0da4e10bb84ede29d4c7b5b6b219dd0c9b (255,488 bytes)
File description: Terdot.A/Zloader on 2017-02-07
Click here to return to the main page.