2017-02-14 - EITEST HOEFLERTEXT CHROME POPUP LEADS TO SPORA RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-02-14-EITest-HoeflerText-Chrome-popup-leads-to-Spora-ransomware-5-pcaps.zip 297.2 kB (297,227 bytes)
- 2017-02-14-EITest-HoeflerText-artifacts-and-Spora-ransomware.zip 235.4 kB (235,361 bytes)
BACKGROUND ON EITEST HOEFLERTEXT CHROME POPUPS:
- 2017-01-17 - Kafeine at Proofpoint published a writeup about this campaign: EITest Nabbing Chrome Users with a "Chrome Font" Social Engineering Scheme.
BACKGROUND ON SPORA RANSOMWARE:
- BleepingComputer published a good write-up on Spora shortly after it first appeared (link).
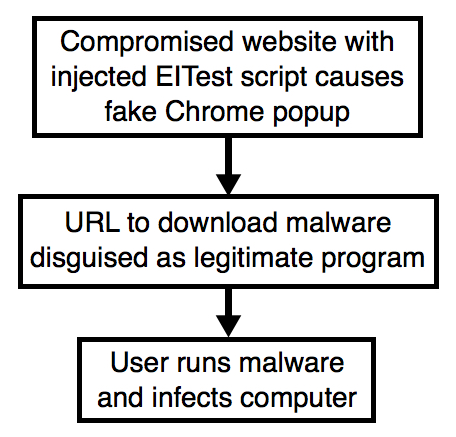
Shown above: Flowchart for this infection traffic.
TRAFFIC
ASSOCIATED DOMAINS:
- holinergroup[.]com - Compromised site
- 193.255.242[.]61 port 80 - kuzem2.kku.edu[.]tr - POST /info.php [returned Spora ransomware]
- 131.123.99[.]24 port 80 - nutr.ehhs.kent[.]edu - POST /info.php [returned Spora ransomware]
- 190.104.250[.]116 port 80 - www.emprendedores.itba[.]edu[.]ar - POST /info.php [returned Spora ransomware]
- 217.26.213[.]73 port 80 - vpsle[.]edu[.]rs - POST /info.php [returned Spora ransomware]
- 103.224.23[.]101 port 80 - www.distanceeducationschool[.]com - POST /info.php [returned Spora ransomware]
- 186.2.163[.]47 port 443 - spora[.]biz - Spora decryption site
FILE HASHES
SPORA RANSOMWARE:
- 444cf5c58a75936d8522db7a46369d732ecf90321fb8fc64bcb126ded213eca0 - Chrome Font v1.25.exe
- e2c68ced5b9078c88dded6ee92dcda61f9ccff467f47eb4cdff9c0423acede66 - Chrome Font v2.41.exe
- 55cd11127474fb89f0edeab556690a492f520812d2de40d0c765d8c14286af6c - Chrome Font v2.96.exe
- 664e65f58fb8b110ef5564af4f059c1526715f2e902feec90313310c455ffd5d - Chrome Font v3.28.exe
- 3e0e79f7994192308160afe7d3783088a47fc9fd84ff0ef03f1a197e595894aa - Chrome Font v3.66.exe
IMAGES
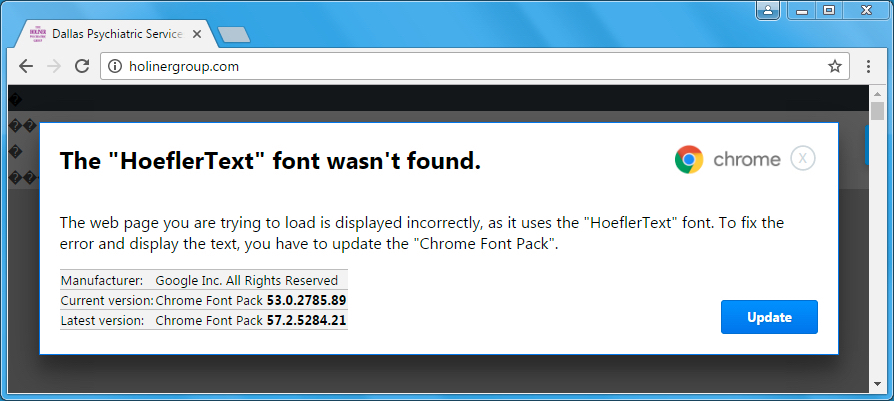
Shown above: Popup within Chrome when viewing the compromised website (image 1 of 2).
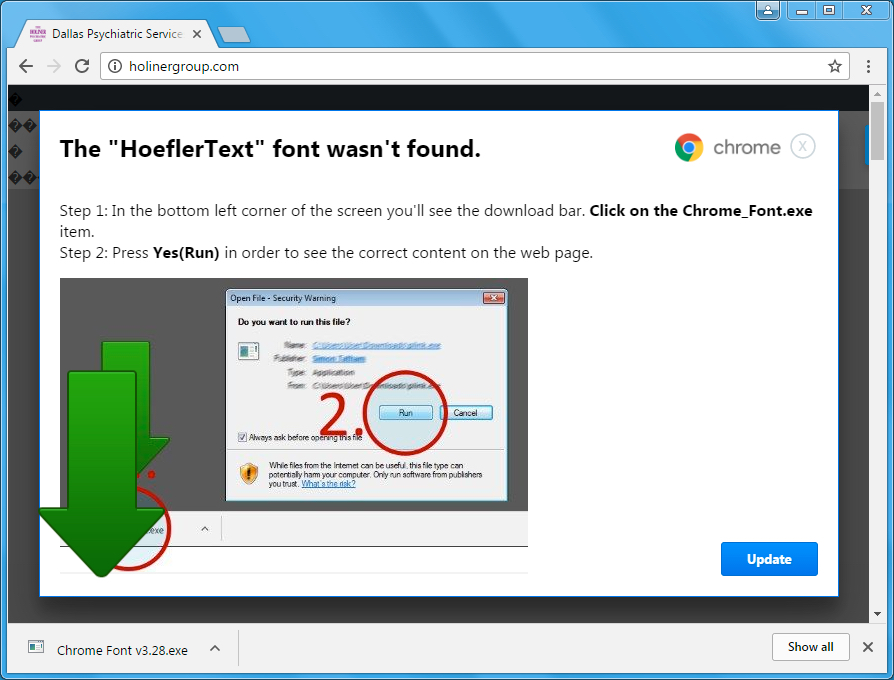
Shown above: Popup within Chrome when viewing the compromised website (image 2 of 2).
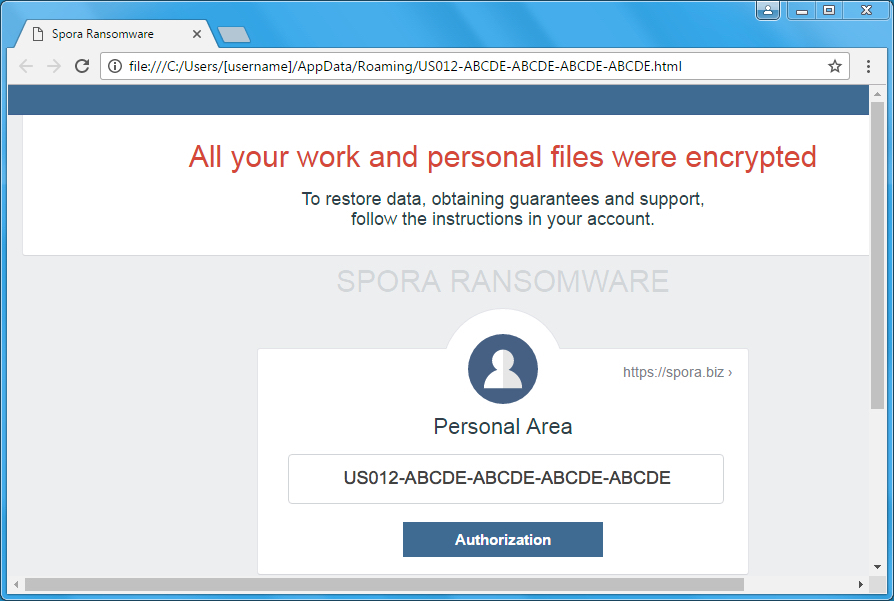
Shown above: Spora decryption instructions from the HTML file dropped to the Desktop.
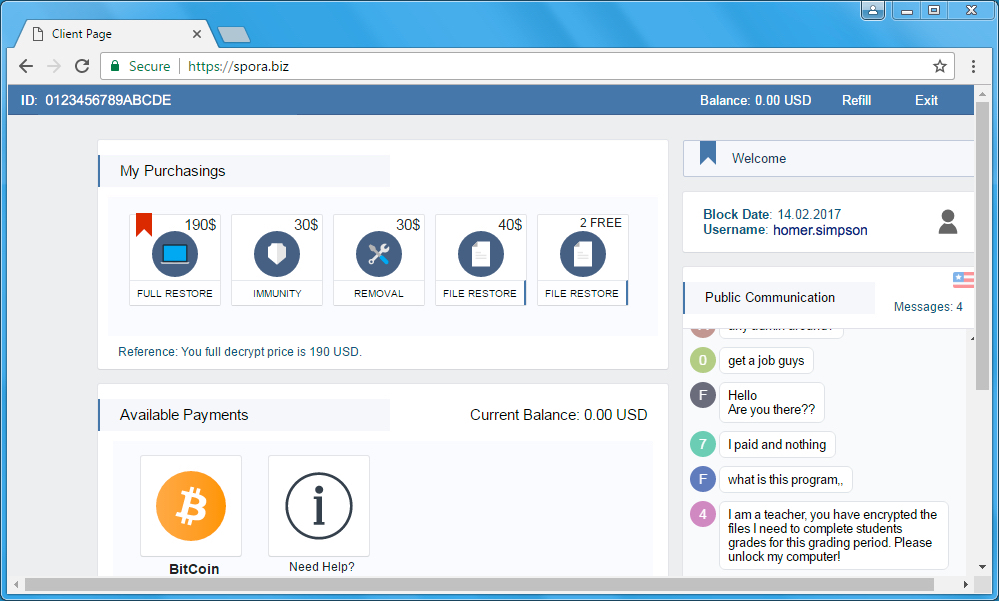
Shown above: Spora decryption site at spora.biz.
Click here to return to the main page.