2017-02-27 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-02-27-Hancitor-infection-with-ZLoader.pcap.zip 14 MB (14,015,771 bytes)
- 2017-02-27-Hancitor-infection-with-ZLoader.pcap (15,101,064 bytes)
- 2017-02-27-Hancitor-malspam-6-examples.zip 6.8 kB (6,795 bytes)
- 2017-02-27-Hancitor-malspam-1551-UTC.eml (1,634 bytes)
- 2017-02-27-Hancitor-malspam-1557-UTC.eml (1,656 bytes)
- 2017-02-27-Hancitor-malspam-1617-UTC.eml (1,686 bytes)
- 2017-02-27-Hancitor-malspam-1636-UTC.eml (1,635 bytes)
- 2017-02-27-Hancitor-malspam-1952-UTC.eml (1,596 bytes)
- 2017-02-27-Hancitor-malspam-2019-UTC.eml (1,620 bytes)
- 2017-02-27-malware-from-Hancitor-infection.zip 290.7 kB (290,748 bytes)
- ADP_Invoice_fred.jaison.doc (176,640 bytes)
- BN4B90.tmp.exe (263,680 bytes)
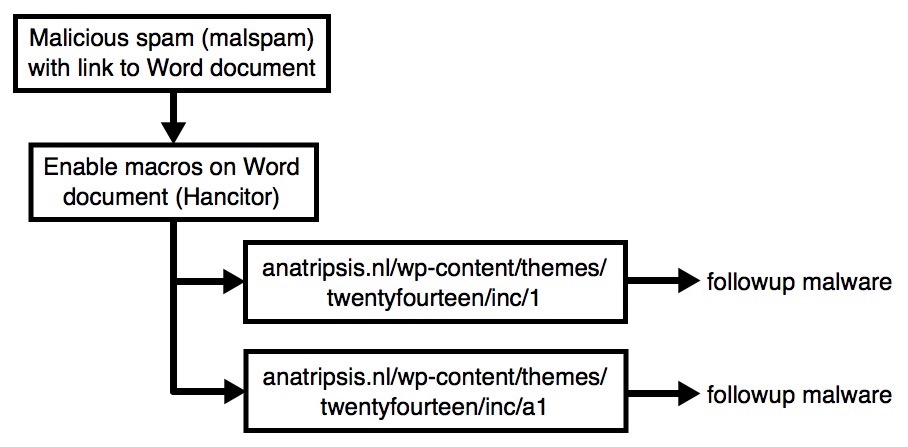
Shown above: Flow chart for today's traffic.
DESCRIPTION:
- Malicious spam (malspam) with link that downloaded a malcious Microsoft Word document (Hancitor). The Hancitor malware document is designed to download and infect Windows hosts with Pony and DELoader (ZLoader).
EMAIL HEADERS:
- Date: Mon, 27 Feb 2017 15:58:02 UTC
- Subject: Your invoice 781712 is ready for your review!
- Message-ID: <AA667E22.C943A5FF@adp-service[.]com>
- From: "ADP Billing" <billing@adp-service[.]com>
- X-Mailer: iPad Mail (13F69)
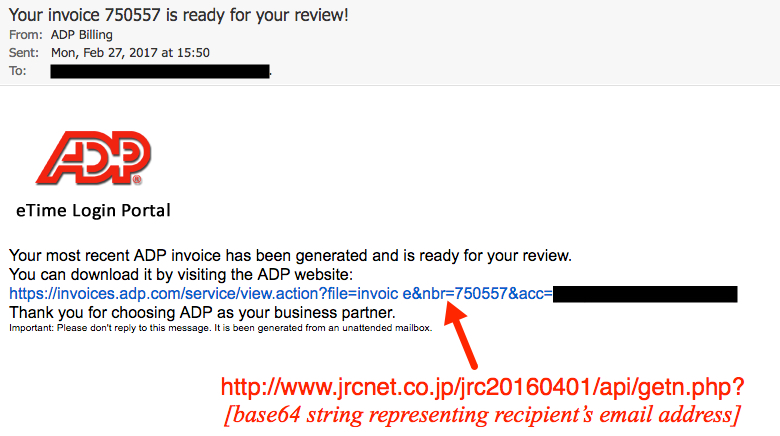
Shown above: Screenshot from one of the emails.
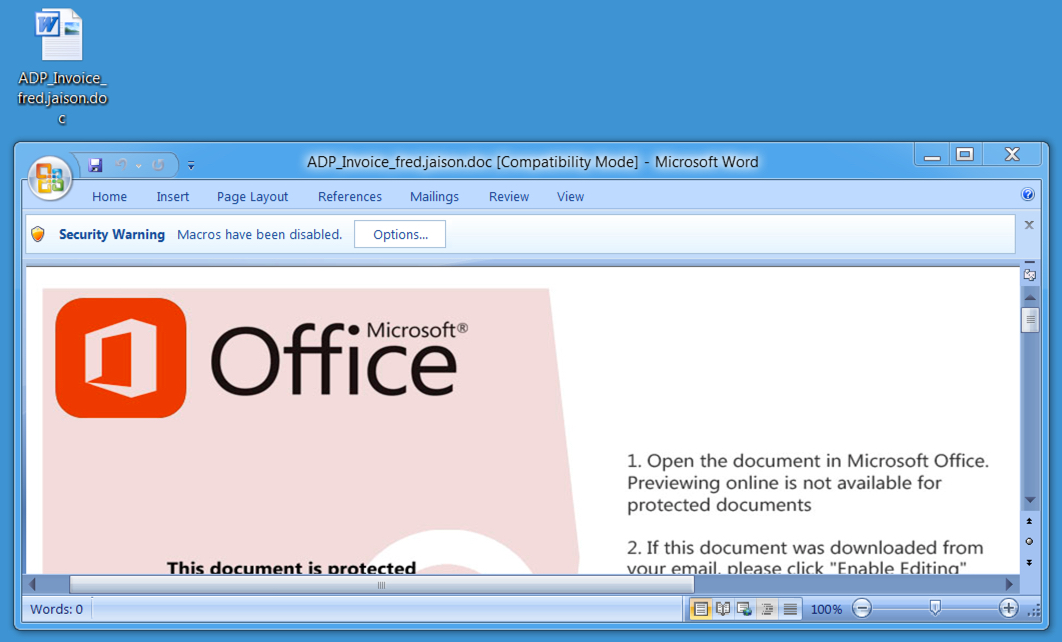
Shown above: Malicious Word document (Hancitor).
TRAFFIC
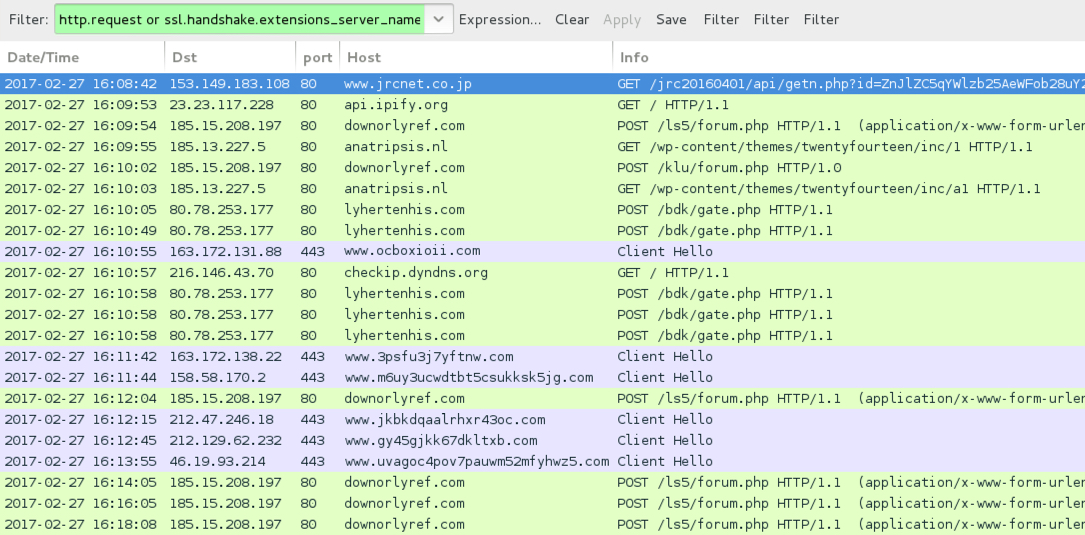
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS AND URLS:
- 153.149.183.108 port 80 - www.jrcnet[.]co[.]jp - GET /jrc20160401/api/getn.php?id=[base64 string]
- 185.15.208[.]197 port 80 - downorlyref[.]com - POST /ls5/forum.php
- 185.15.208[.]197 port 80 - downorlyref[.]com - POST /klu/forum.php
- 185.13.227[.]5 port 80 - anatripsis[.]nl - GET /wp-content/themes/twentyfourteen/inc/1
- 185.13.227[.]5 port 80 - anatripsis[.]nl - GET /wp-content/themes/twentyfourteen/inc/a1
- 80.78.253[.]177 port 80 - lyhertenhis[.]com - POST /bdk/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses, various ports - Tor traffic
- 186.202.153[.]165 port 80 - www.bxlog[.]com[.]br - GET /api/getn.php?id=[base64 string] Note: This one was seen in one of the later emails. It's not in the pcap.
FILE HASHES
HANCITOR MALDOC:
- SHA256 hash: d2d786e373e968858e8a45118b20b744c621e10c84d5bbfddd0ff12841c5442b
- File name: ADP_Invoice_fred.jaison.doc
- File size: 176,640 bytes
- File description: Hancitor maldoc
DELOADER (ZLOADER):
- SHA256 hash: 8a79ea947bc742cddb33a7ad4852e69582d28898cd8d325743d6e08b2ce84117
- File location: C:\Users\[username]\AppData\Local\Temp\BN4B90.tmp
- File size: 263,680 bytes
- File description: ZLoader/DELoader (I think)
FINAL NOTES
Click here to return to the main page.