2017-02-28 - "BLANK SLATE" CAMPAIGN SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-02-28-Cerber-ransomware-infections-3-pcaps.zip 803.4 kB (803,394 bytes)
- 2017-02-28-Blank-Slate-malspam-tracker.csv.zip 1.1 kB (1,082 bytes)
- 2017-02-28-Blank-Slate-emails-and-Cerber-ransomware.zip 3.4 MB (3,441,489 bytes)
NOTES:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
EMAILS
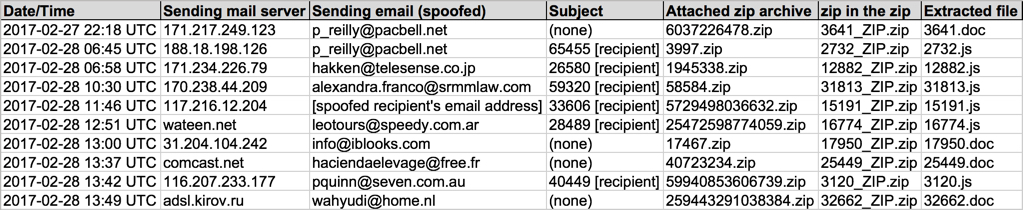
Shown above: Information from the spreadsheet tracker (part 1 of 2).
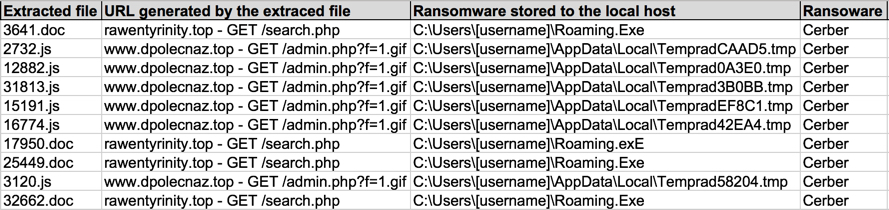
Shown above: Information from the spreadsheet tracker (part 2 of 2).
EMAILS GATHERED:
(Read: Date/Time -- Sending mail server -- Sending email (spoofed) -- Subject -- Attached zip -- Extracted file)
- 2017-02-27 22:18 UTC -- 171.217.249[.]123 -- p_reilly@pacbell[.]net -- (none) -- 6037226478.zip -- 3641.doc
- 2017-02-28 06:45 UTC -- 188.18.198[.]126 -- p_reilly@pacbell[.]net -- 65455 [recipient] -- 3997.zip -- 2732.js
- 2017-02-28 06:58 UTC -- 171.234.226[.]79 -- hakken@telesense[.]co[.]jp -- 26580 [recipient] -- 1945338.zip -- 12882.js
- 2017-02-28 10:30 UTC -- 170.238.44[.]209 -- alexandra.franco@srmmlaw[.]com -- 59320 [recipient] -- 58584.zip -- 31813.js
- 2017-02-28 11:46 UTC -- 117.216.12[.]204 -- [spoofed recipient's email address] -- 33606 [recipient] -- 5729498036632.zip -- 15191.js
- 2017-02-28 12:51 UTC -- wateen[.]net -- leotours@speedy[.]com[.]ar -- 28489 [recipient] -- 25472598774059.zip -- 16774.js
- 2017-02-28 13:00 UTC -- 31.204.104[.]242 -- info@iblooks[.]com -- (none) -- 17467.zip -- 17950.doc
- 2017-02-28 13:37 UTC -- comcast[.]net -- haciendaelevage@free[.]fr -- (none) -- 40723234.zip -- 25449.doc
- 2017-02-28 13:42 UTC -- 116.207.233[.]177 -- pquinn@seven[.]com[.]au -- 40449 [recipient] -- 59940853606739.zip -- 3120.js
- 2017-02-28 13:49 UTC -- adsl.kirov[.]ru -- wahyudi@home[.]nl -- (none) -- 259443291038384.zip -- 32662.doc
TRAFFIC
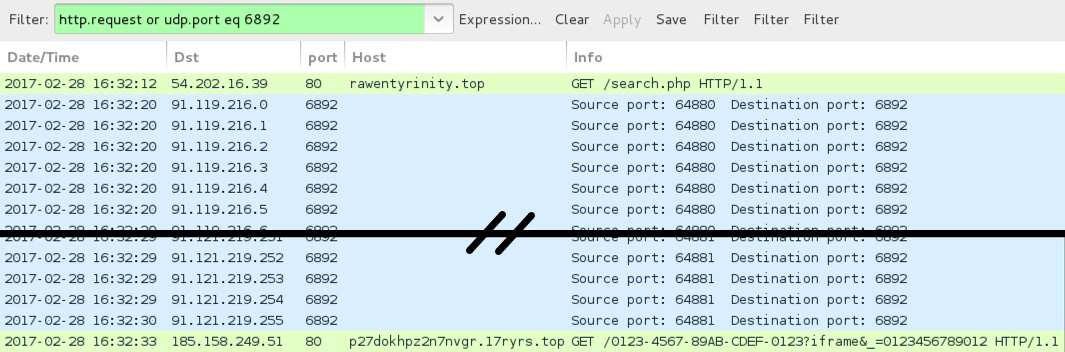
Shown above: Example from a full infection chain of traffic filtered in Wireshark.
HTTP REQUESTS FOR THE CERBER RANSOMWARE:
- 35.166.18[.]233 port 80 - www.dpolecnaz[.]top - GET /admin.php?f=1.gif
- 89.223.28[.]60 port 80 - www.dpolecnaz[.]top - GET /admin.php?f=1.gif
- 54.202.16[.]39 port 80 - rawentyrinity[.]top - GET /search.php
CERBER RANSOMWARE POST-INFECTION TRAFFIC:
- 91.119.216[.]0 to 91.119.216[.]31 (91.119.216[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.120.216[.]0 to 91.120.216[.]31 (91.120.216[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.121.216[.]0 to 91.121.219[.]255 (91.121.216[.]0/22) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 185.158.249[.]51 port 80 - p27dokhpz2n7nvgr.17ryrs[.]top - Cerber ransomware post-infection HTTP traffic
MALWARE
ATTACHMENETS:
- 273f54b93938ab8c93c0be1187d3c9a6734652c2f65bcf62e65049393fdb7263 - 17467.zip (104,294 bytes)
- d85b96945e13dfa7c251c5fd9285883950415f909ceabf5599c19da267663d1a - 1945338.zip (12,504 bytes)
- dc86485c0d4a769375323416f14c320ad2213610ba490ac1b1df66568fced185 - 25472598774059.zip (12,517 bytes)
- 0c57bc7e361cc549b6a941e6c3c198755a06b555941f5dd36475e1691dd873b4 - 259443291038384.zip (103,612 bytes)
- 364e7631c8f231dc3e630284e0cb9045d178bd78ebd3facc21c8f61cfe00482f - 3997.zip (12,377 bytes)
- a652071586a83e16403ddd27f8b477a5e66a887ded6fd16476c98b4af4634784 - 40723234.zip (103,612 bytes)
- cb3428a40ec6c34bbe27f11e37156b0c5cc3d8e6f468f4802968818b00e1ade3 - 5729498036632.zip (12,476 bytes)
- b338cbc77759733066699c66ecac9d5723a39d9bfe52f8f9c62affea8dfb7ad3 - 58584.zip (12,482 bytes)
- 25cc75648ab6a3f6d79f56737f5c5c721267a039ef2c102bcf03bcc683028fcf - 59940853606739.zip (12,272 bytes)
- 308675500a6bcc64e2ecbdc2b11a189b0ea18f1cd51b40935a9973de646b4401 - 6037226478.zip (103,349 bytes)
EXTRACTED FILES:
- 79c5592aa5a425ae69727df96bb66b54fa0be9b645b56bd404befe4e2233f6c5 - 12882.js (52,348 bytes)
- 4700b3ec1dacbfabe43b146168dd97f4b0bd24bc2be21430df04a77ddda80c1c - 15191.js (56,702 bytes)
- a9bb197c178ac3f10d824a23d02931e3a0ec27589d9b4595c00bb79eb28347a8 - 16774.js (58,099 bytes)
- 5c108a46139c3ce494a5570874d065695870b66b94a73b4827f0ca57a9374fd5 - 17950.doc (158,720 bytes)
- 2047611a981ca1d6e865edea00bee46488df4815ee4cf29d09778491d0076de5 - 25449.doc (157,184 bytes)
- ec0691a2079f34c4ae2320403dfde7089ed475bf5d2f953d3d5b99390f540042 - 2732.js (51,876 bytes)
- c6293b87f8482acbb9fccfc7b2a9da4b6a7385a640b5c9aeee511932ad5e5e17 - 3120.js (53,758 bytes)
- b17cad0a9f3ae064dc3fb49ddf6b53dc949c2b576022934de247228c7462f896 - 31813.js (54,414 bytes)
- 2047611a981ca1d6e865edea00bee46488df4815ee4cf29d09778491d0076de5 - 32662.doc (157,184 bytes)
- f462fcbabfd2cbe8fdcc7c0fca4850586a076c5e013116038d28be579cfaf6ac - 3641.doc (156,672 bytes)
CERBER SAMPLES:
- 65906d590b8b6fa26e5d4ef510c1f6852a1d540fe9f444e4f1146fab41a76434 - Cerber ransomware from dpolecnaz[.]top (1 of 3) (248,718 bytes)
- d285563d49b932854f0ced61ccb332d6b8c601badd09474bc2fa68d4278b6e9b - Cerber ransomware from dpolecnaz[.]top (2 of 3) (248,718 bytes)
- 7ee9975d7e8f58f5ad20589d9b6214e0c0fc476473e47dfa2dc891636c641747 - Cerber ransomware from dpolecnaz[.]top (3 of 3) (248,718 bytes)
- 6f42249f07e7cea6d0d1b60cff42b30cd4526e8b1388bc22c46b50928961dcf3 - Cerber ransomware from rawentyrinity[.]top (1 of 3) (248,717 bytes)
- 2521feb8887c5e9544e4d7686cb11962a95349722f661e175a75143d9cbc0ad7 - Cerber ransomware from rawentyrinity[.]top (2 of 3) (250,041 bytes)
- 9d547ef0e4fae0c8a70fc78545d221fdba8e794caf2e9da04d1e7f5a1d7b0f1f - Cerber ransomware from rawentyrinity[.]top (3 of 3) (250,041 bytes)
IMAGES
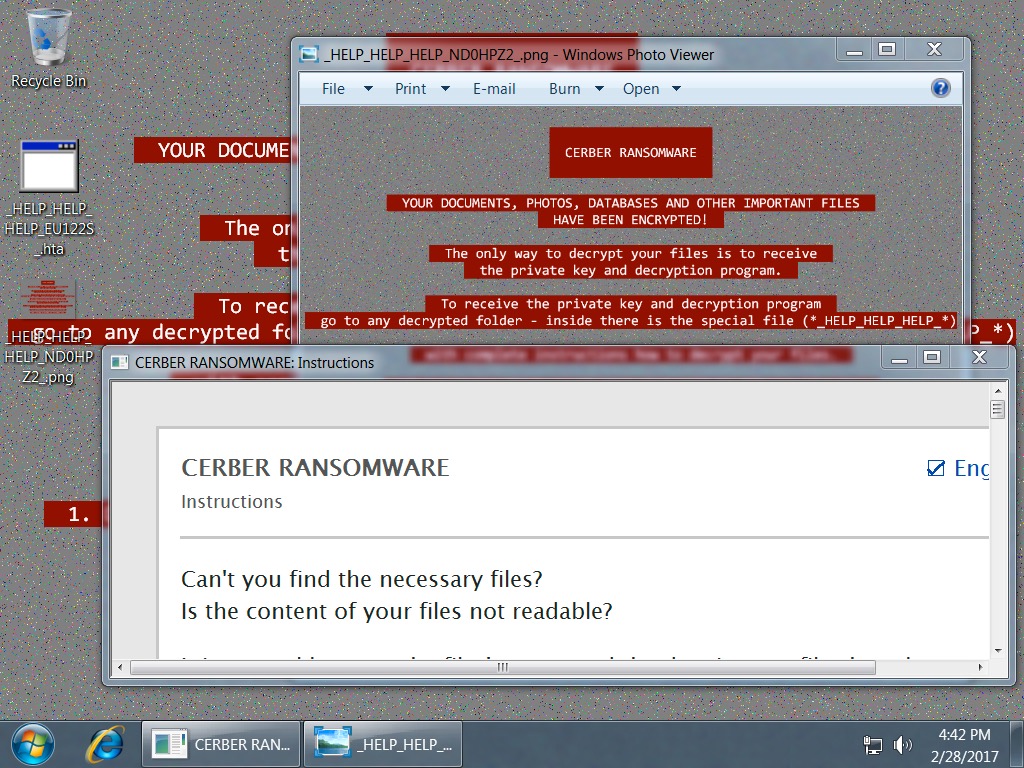
Shown above: One of the infected hosts after rebooting.
Click here to return to the main page.
