2017-02-28 - HANCITOR INFECTION WITH ZLOADER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-02-28-Hancitor-infection-with-ZLoader.pcap.zip 14.0 MB (14,036,486 bytes)
- 2017-02-28-Hancitor-infection-with-ZLoader.pcap (15,049,538 bytes)
- 2017-02-28-Hancitor-malspam-4-examples.zip 5.1 kB (5,131 bytes)
- 2017-02-28-Hancitor-malspam-1534-UTC.eml (1,712 bytes)
- 2017-02-28-Hancitor-malspam-1618-UTC.eml (1,643 bytes)
- 2017-02-28-Hancitor-malspam-1624-UTC.eml (1,669 bytes)
- 2017-02-28-Hancitor-malspam-1641-UTC.eml (1,643 bytes)
- 2017-02-28-malware-from-Hancitor-infection.zip 224.8 kB (224,823 bytes)
- BN2FDA.tmp.exe (150,528 bytes)
- USPS_Notice.doc (184,832 bytes)
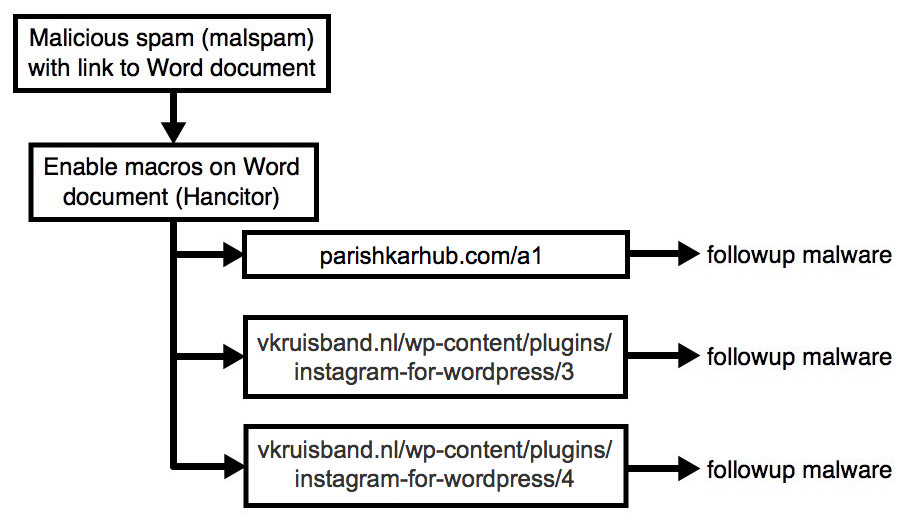
Shown above: Flow chart for today's traffic.
DESCRIPTION:
- Malicious spam (malspam) with link that downloaded a malcious Microsoft Word document (Hancitor). The Hancitor malware document is designed to download and infect Windows hosts with Pony and ZLoader (DELoader).
EMAIL HEADERS:
- Date: Tuesday, 2017-02-28 15:34 UTC thru at least 16:41 UTC
- From (spoofed): "USPS" <usps@usps-shipment[.]com>
- Subject: Shipment status change notification for parcel #55742318
- Subject: Shipment status change notification for parcel #70587240
- Subject: Shipment status change notification for parcel #11002057
- Subject: Shipment status change notification for parcel #34330022
- Message-ID: <D9DDE5C4.C1AFEAB2@usps-shipment[.]com>
- Message-ID: <0AAF7291.31C70C00@usps-shipment[.]com>
- Message-ID: <C76124B7.CBF5C4AE@usps-shipment[.]com>
- Message-ID: <C6B893B6.DA7B3377@usps-shipment[.]com>
- X-Mailer: Apple Mail (2.1082)
- X-Mailer: iPhone Mail (9B176)
- X-Mailer: iPhone Mail (13A344)
- X-Mailer: iPhone Mail (13A404)
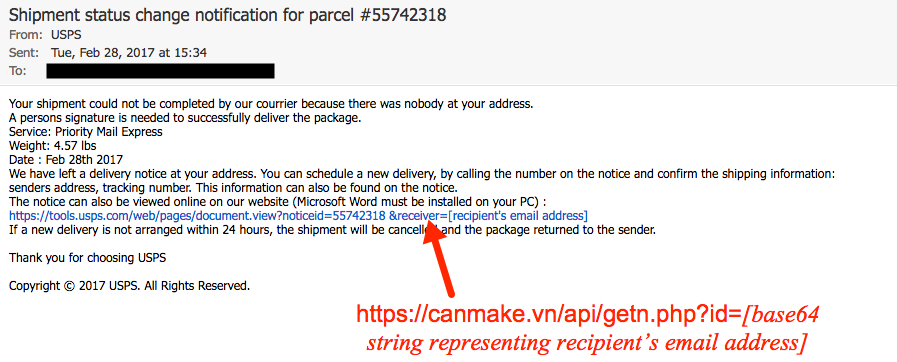
Shown above: Screenshot from one of the emails.
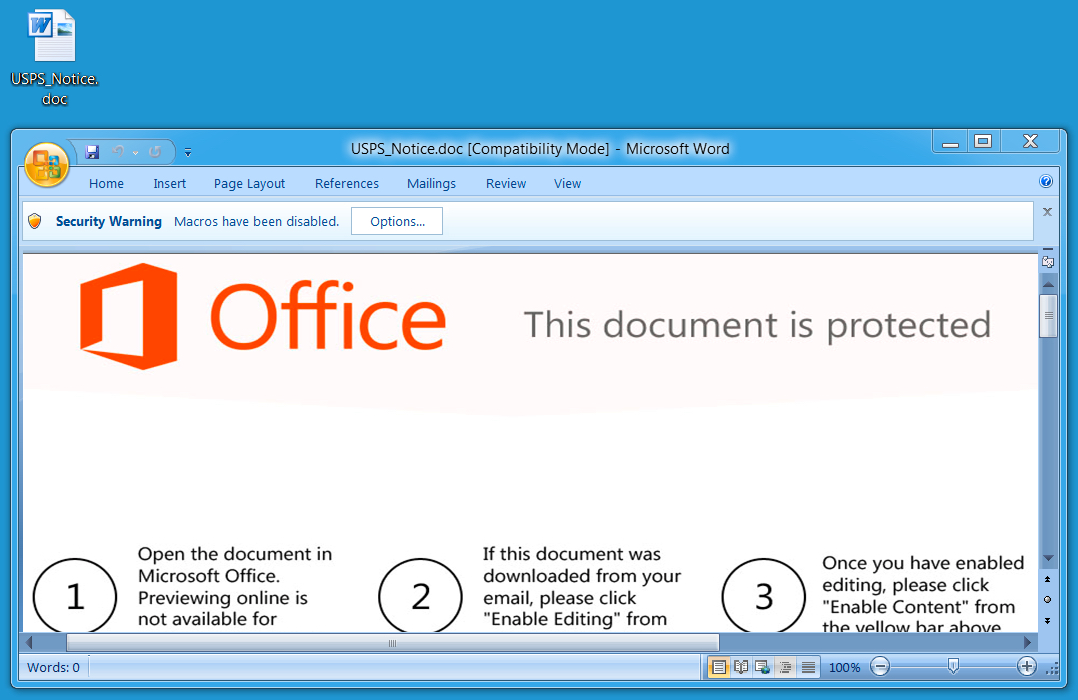
Shown above: Malicious Word document (Hancitor).
TRAFFIC
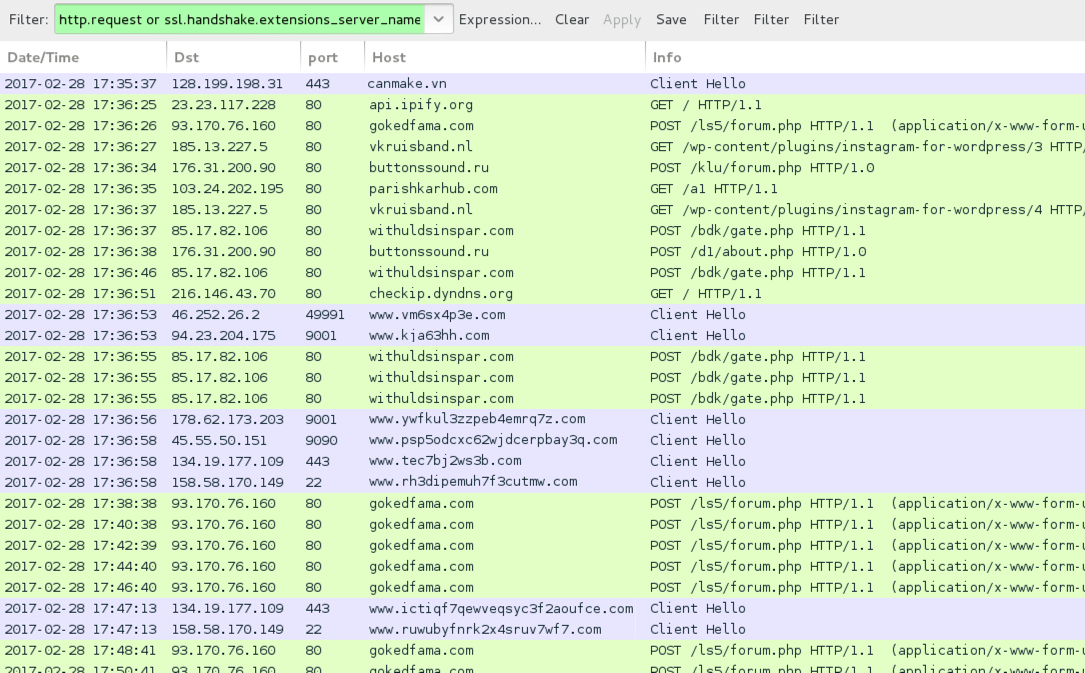
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS AND URLS:
- 128.199.198.31 port 443 - canmake.vn - GET /api/getn.php?id=[base64 string] <-- HTTPS
- 93.170.76[.]160 port 80 - gokedfama[.]com - POST /ls5/forum.php
- 103.24.202[.]195 port 80 - parishkarhub[.]com - GET /a1
- 185.13.227[.]5 port 80 - vkruisband[.]nl - GET /wp-content/plugins/instagram-for-wordpress/3
- 185.13.227[.]5 port 80 - vkruisband[.]nl - GET /wp-content/plugins/instagram-for-wordpress/4
- 176.31.200[.]90 port 80 - buttonssound[.]ru - POST /klu/forum.php
- 176.31.200[.]90 port 80 - buttonssound[.]ru - POST /d1/about.php
- 85.17.82[.]106 port 80 - withuldsinspar[.]com - POST /bdk/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses, various ports - Tor traffic
FILE HASHES
HANCITOR MALDOC:
- SHA256 hash: 780a5096b52f18316eeb93aa8a8e17cd7f8372f3dae08094bff39acae457fdc9
- File name: USPS_Notice.doc
- File size: 184,832 bytes
- File description: Hancitor maldoc
DELOADER (ZLOADER):
- SHA256 hash: 220c3ea724b1ec9ca2095b67f359035512fcebb7b8c32ea8298be030a82e97b1
- File location: C:\Users\[username]\AppData\Local\Temp\BN2FDA.tmp
- File size: 150,528 bytes
- File description: ZLoader (DELoader)
Click here to return to the main page.