2017-03-03 - SHADE (TROLDESH) RANSOMWARE INFECTION
ASSOCIATED FILES:
- 2017-03-03-Shade-ransomware-infection.pcap.zip 16.5 MB (16,539,225 bytes)
- 2017-03-03-Shade-ransomware-infection.pcap (17,849,841 bytes)
- 2017-03-03-Shade-ransomware-eamils-and-malware.zip 5.5 MB (5,533,862 bytes)
- 2017-03-03-Shade-ransomware-decryption-instructions.txt (4,170 bytes)
- 2017-03-03-Shade-ransomware-desktop-background.bmp (2,087,494 bytes)
- 2017-03-03-fake-IRS-email-1342-UTC.eml (2,176 bytes)
- 2017-03-03-malware-downloaded-by-js-file.exe (952,470 bytes)
- 75FA005B.exe (173,084 bytes)
- 82E39F81.exe (887,808 bytes)
- A86B5C6747183B1C9BBB4181C53F302D.dll (1,012,224 bytes)
- C9AA35DA.exe (1,032,704 bytes)
- D88AD939.exe (1,497,600 bytes)
- Realty.tax.division.xls.js (22,539 bytes)
- Realty.tax.division.xls.zip (9,445 bytes)
NOTES:
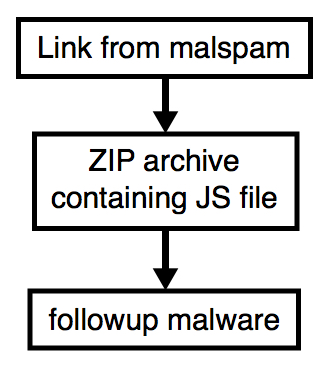
- The malicious spam (malspam) has a link to a zip archive containing a .js file.
- The .js file was disguised as an XLS spreadsheet from the IRS.
- The .js file dropped Shade (Troldesh) ransomware and other items of malware.
- The file extension for any encrypted files on the infected Windows host was .no_more_ransom.
- The infected host also attempted logins on several hundred Wordpress sites before I stopped it.
Shown above: Flowchart for this infection traffic.
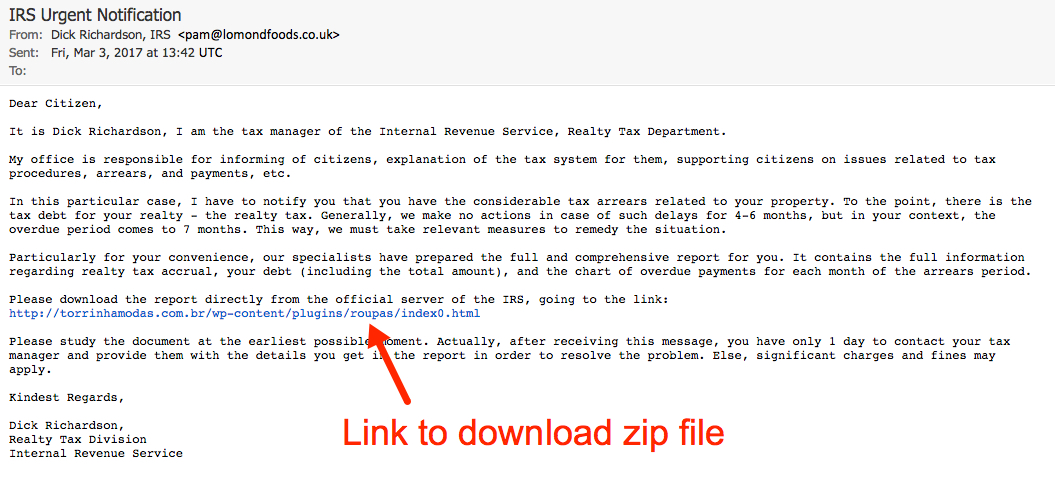
Shown above: Screenshot from the email.
EMAIL HEADERS:
- Date: Friday 2017-03-03 at 13:42 UTC
- From (spoofed): "Dick Richardson, IRS" <pam@lomondfoods[.]co[.]uk>
- Subject: IRS Urgent Notification
- Message-ID: <002601d29424$68bb6210$602d4eec@UTC2pk>
EMAIL MESSAGE:
Dear Citizen,
It is Dick Richardson, I am the tax manager of the Internal Revenue Service, Realty Tax Department.
My office is responsible for informing of citizens, explanation of the tax system for them, supporting citizens on issues related to tax procedures, arrears, and payments, etc.
In this particular case, I have to notify you that you have the considerable tax arrears related to your property. To the point, there is the tax debt for your realty - the realty tax. Generally, we make no actions in case of such delays for 4-6 months, but in your context, the overdue period comes to 7 months. This way, we must take relevant measures to remedy the situation.
Particularly for your convenience, our specialists have prepared the full and comprehensive report for you. It contains the full information regarding realty tax accrual, your debt (including the total amount), and the chart of overdue payments for each month of the arrears period.
Please download the report directly from the official server of the IRS, going to the link:
[link to malicious zip file]
Please study the document at the earliest possible moment. Actually, after receiving this message, you have only 1 day to contact your tax manager and provide them with the details you get in the report in order to resolve the problem. Else, significant charges and fines may apply.
Kindest Regards,
Dick Richardson,
Realty Tax Division
Internal Revenue Service
DOWNLOADED FILE:
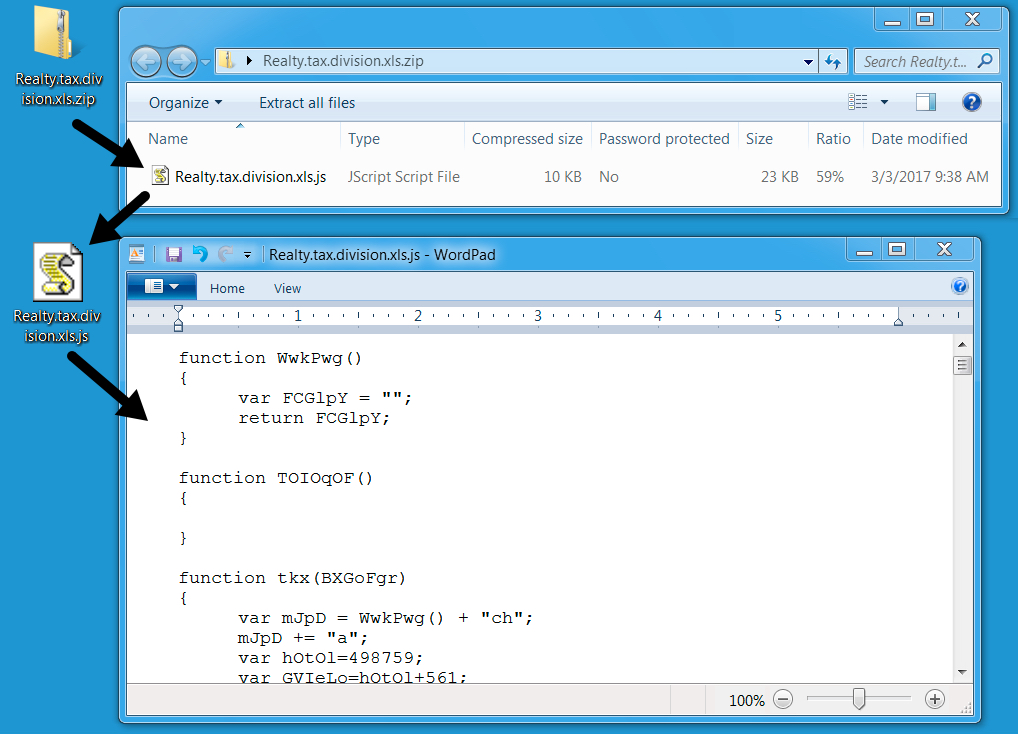
Shown above: Zip archive downloaded from link in the email.
TRAFFIC
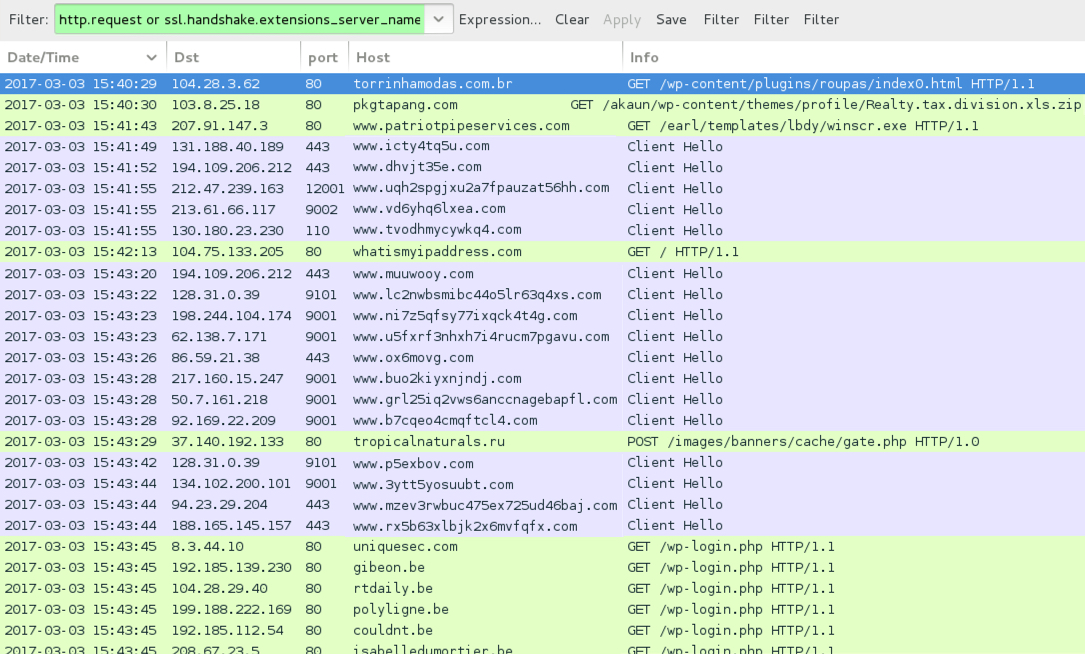
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 104.28.3[.]62 port 80 - torrinhamodas[.]com[.]br - GET /wp-content/plugins/roupas/index0.html
- 103.8.25[.]18 port 80 - pkgtapang[.]com - GET /akaun/wp-content/themes/profile/Realty.tax.division.xls.zip
- 207.91.147[.]3 port 80 - www.patriotpipeservices[.]com - GET /earl/templates/lbdy/winscr.exe
- whatismyipaddress[.]com - GET /
- 37.140.192[.]133 port 80 - tropicalnaturals[.]ru - POST /images/banners/cache/gate.php
- various IP addresses, various domains - Tor traffic
- various IP addresses, various domains - Bruteforce wordpress logins from the infected host
FILE HASHES
FROM LINK IN THE EMAIL:
- SHA256 hash: 16b2ef370e854859a4e9b85a047b6564d2ada124cef841f52d30bc2970d8a9ea
File name: Realty.tax.division.xls.zip
File description: Downloaded .zip file from link in the email
- SHA256 hash: 8ddf908f8f1ba26942d5697964a6dbf3cb86e1703cf5a4903d92b54928439ff7
File name: Realty.tax.division.xls.js
File description: Extracted .js file
ARTIFACTS FROM THE INFECTED HOST:
- SHA256 hash: 50d4b6751f288b5ad1e6d4ab10c64c609bebf5d939593e1eed4e8f1652e4efab
File path: C:\Users\[username]\AppData\Local\Temp\rad77F2A.tmp
File path: C:\ProgramData\Windows\csrss.exe
File description: malware downloaded by js file - Shade (Troldesh) ransomware
- SHA256 hash: 2a82ab2f870f6e1bd1f5ef002fa5679f1e3ab7821df4c15e4009ae8ef3e6d89c
File path: C:\Users\[username]\AppData\Local\Temp\75FA005B.exe
File description: Follow-up malware
- SHA256 hash: 9d3bac28e24a997c2d2b3a955b7f0d57494950a0269f1bf31dc45fb1dadcdb84
File path: C:\Users\[username]\AppData\Local\Temp\82E39F81.exe
File path: C:\ProgramData\Drivers\csrss.exe
File description: Follow-up malware
- SHA256 hash: 047fd3fcc12afbe18816e7f8d18f5573e1da36bdd9883df1b28f3aee908a8abc
File path: C:\Users\[username]\AppData\Local\Temp\A86B5C6747183B1C9BBB4181C53F302D.dll
File description: Follow-up malware
- SHA256 hash: 0df932043d6da40d958284ea8ee065f6269a3babdbb45ff319f2030d0d6fe115
File path: C:\Users\[username]\AppData\Local\Temp\C9AA35DA.exe
File path: C:\ProgramData\Csrss\csrss.exe
File description: Follow-up malware
- SHA256 hash: 29a8babbce680179675485b775f2c9ee1c2924afda7236feb31aabf5ddf05c3c
File path: C:\Users\[username]\AppData\Local\Temp\D88AD939.exe
File path: C:\ProgramData\services\csrss.exe
File description: Follow-up malware
IMAGES
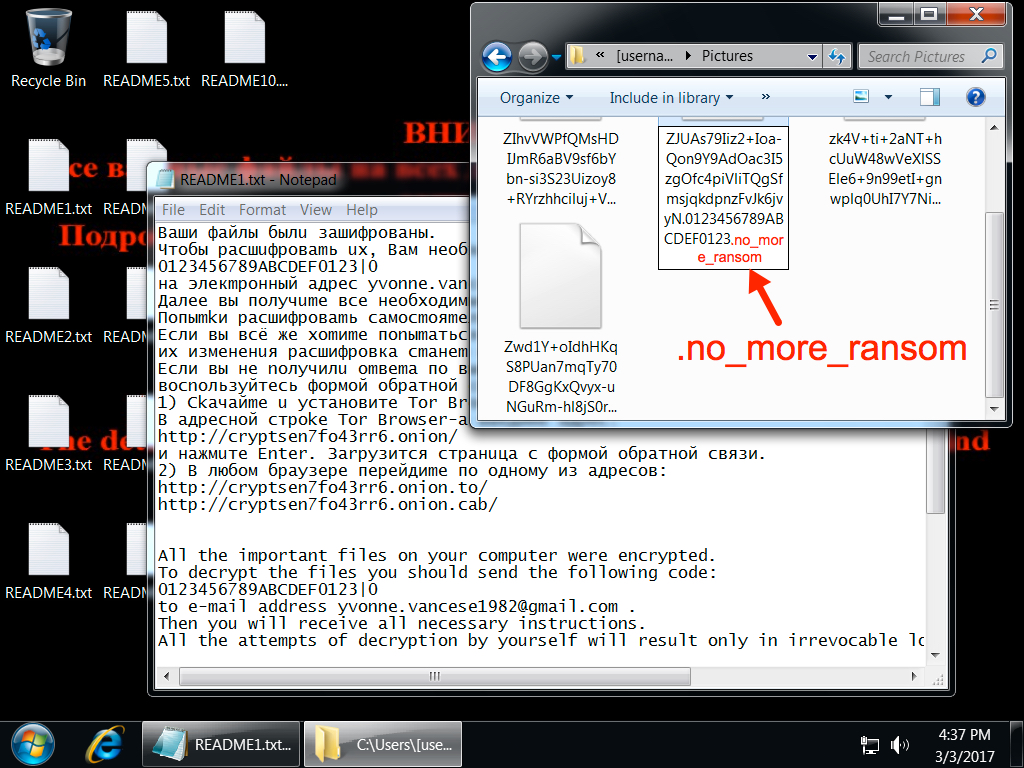
Shown above: Desktop of the infected Windows host.
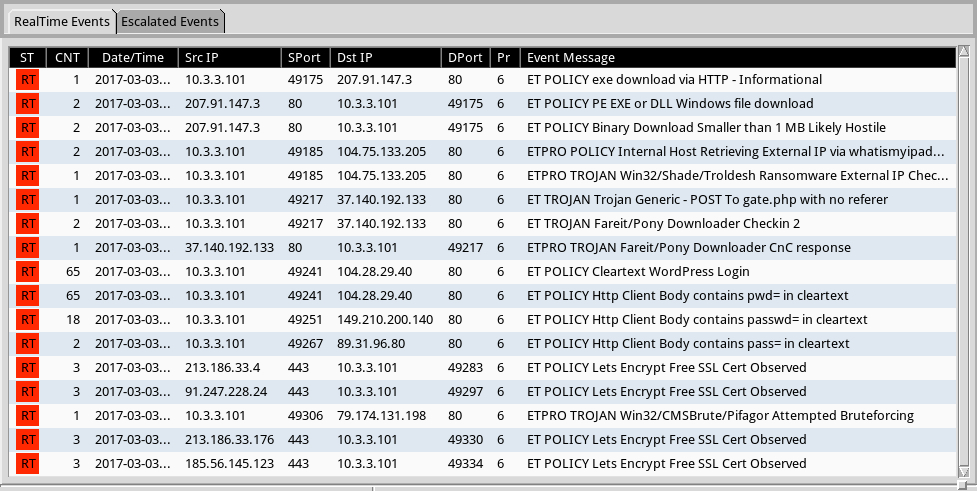
Shown above: Some (not all) alerts on the post-infection traffic from the ETPRO ruleset using Sguil on Security Onion.
Click here to return to the main page.