2017-03-06 - HANCITOR INFECTION
ASSOCIATED FILES:
- 2017-03-06-Hancitor-infection-traffic.pcap.zip 2.3 MB (2,287,188 bytes)
- 2017-03-06-Hancitor-infection-traffic.pcap (2,771,544 bytes)
- 2017-03-06-Hancitor-malspam-5-examples.zip 6.4 kB (6,364 bytes)
- 2017-03-06-Hancitor-malspam-1537-UTC.eml (2,189 bytes)
- 2017-03-06-Hancitor-malspam-1646-UTC.eml (2,237 bytes)
- 2017-03-06-Hancitor-malspam-1647-UTC.eml (2,241 bytes)
- 2017-03-06-Hancitor-malspam-1703-UTC.eml (2,184 bytes)
- 2017-03-06-Hancitor-malspam-1718-UTC.eml (2,217 bytes)
- 2017-03-06-malware-from-Hancitor-infection.zip 220.8 kB (220,785 bytes)
- BN7EF2.tmp.exe (153,088 bytes)
- Delta_Ticket_gene.mandell.doc (184,320 bytes)
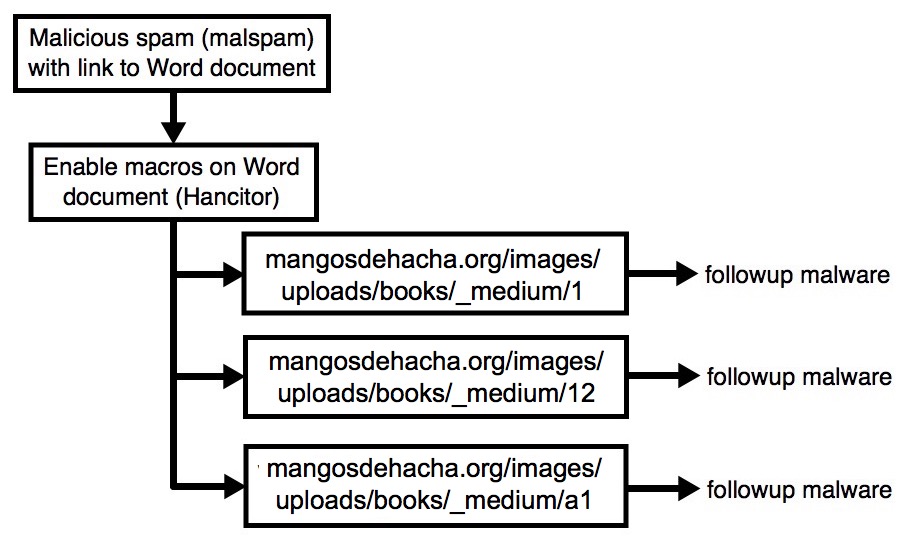
Shown above: Flow chart for today's traffic.
DESCRIPTION:
- Malicious spam (malspam) with link that downloaded a malcious Microsoft Word document (Hancitor). The Hancitor malware document is designed to download and infect Windows hosts with malware.
EMAIL HEADERS:
- Date: Monday, 2017-03-06 as early as 15:37 UTC thru at least 17:18 UTC
- From (spoofed): "Delta Air Lines" <DeltaAirLines@t.delta[.]com>
- Subject: Your Flight Ticket Invoice 08518 - [recipient's name from the email address]
- Subject: Your Flight Ticket Invoice 08680 - [recipient's name from the email address]
- Subject: Your Flight Ticket Invoice 30825 - [recipient's name from the email address]
- Subject: Your Flight Ticket Invoice 42874 - [recipient's name from the email address]
- Subject: Your Flight Ticket Invoice 47174 - [recipient's name from the email address]
- Message-ID: <32D3FF24.109A2BE4@t.delta[.]com>
- Message-ID: <38799D32.4BAB4791@t.delta[.]com>
- Message-ID: <B9F55FB2.9A801B1C@t.delta[.]com>
- Message-ID: <C351785A.65BC35B7@t.delta[.]com>
- Message-ID: <D0A43245.98019F4B@t.delta[.]com>
- X-Mailer: Apple Mail (2.1084)
- X-Mailer: Apple Mail (2.1510)
- X-Mailer: iPad Mail (11D257)
- X-Mailer: iPad Mail (12A405)
- X-Mailer: iPhone Mail (11D257)
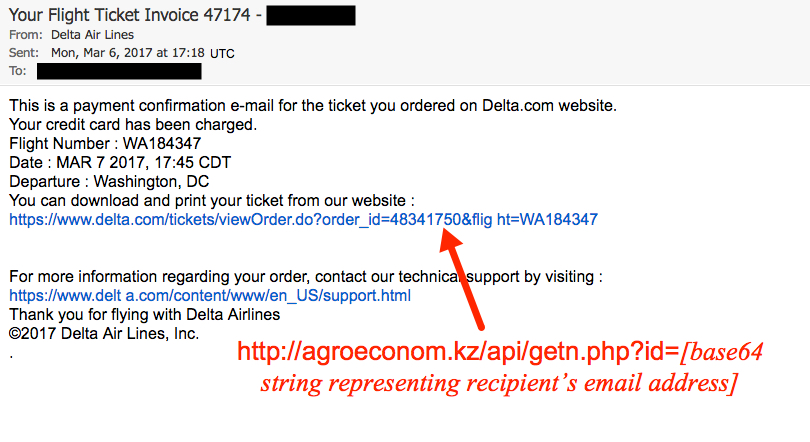
Shown above: Screenshot from one of the emails.
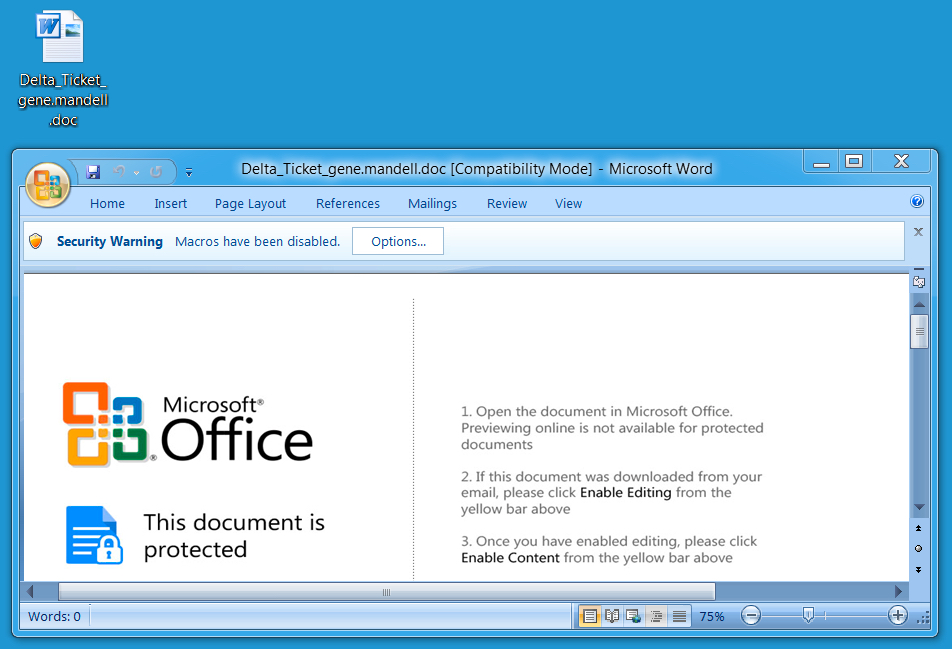
Shown above: Malicious Word document (Hancitor).
TRAFFIC
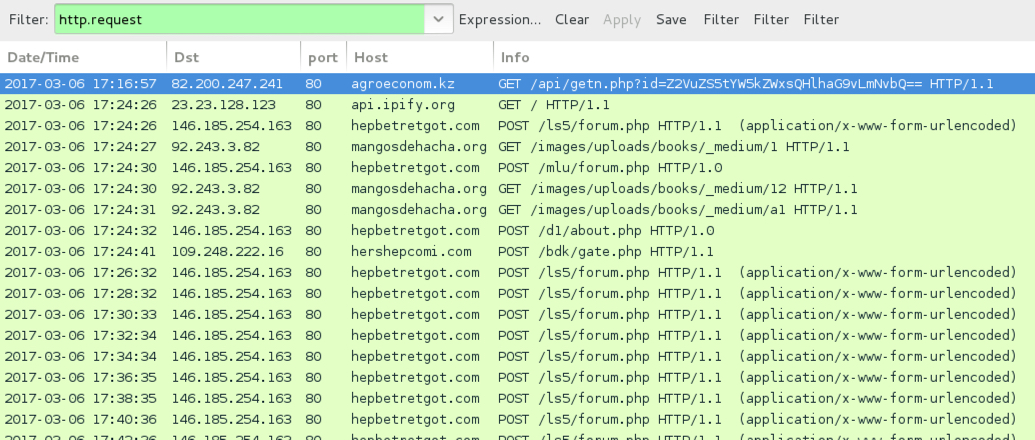
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS AND URLS:
- 103.21.182[.]106 port 80 - www.malton[.]com[.]my - GET /api/getn.php?id=[base64 string]
- 82.200.247[.]241 port 80 - agroeconom[.]kz - GET /api/getn.php?id=[base64 string]
- 146.185.254[.]163 port 80 - hepbetretgot[.]com - POST /ls5/forum.php
- 146.185.254[.]163 port 80 - hepbetretgot[.]com - POST /mlu/forum.php
- 146.185.254[.]163 port 80 - hepbetretgot[.]com - POST /d1/about.php
- 92.243.3[.]82 port 80 - mangosdehacha[.]org - GET /images/uploads/books/_medium/1
- 92.243.3[.]82 port 80 - mangosdehacha[.]org - GET /images/uploads/books/_medium/12
- 92.243.3[.]82 port 80 - mangosdehacha[.]org - GET /images/uploads/books/_medium/a1
- 109.248.222[.]16 port 80 - hershepcomi[.]com - POST /bdk/gate.php
- api.ipify[.]org - GET /
FILE HASHES
HANCITOR MALDOC:
- SHA256 hash: e2b8af79b1d874352e8f833b6ffa860bced91c059d60c821860a9cc69852c5e6
- File name: Delta_Ticket_gene.mandell.doc
- File size: 184,320 bytes
- File description: Hancitor maldoc
FROM THE INFECTED HOST:
- SHA256 hash: e8dfbdbbb201d808915004e840395f7c77b339894880de3e7e2ef9df9356bbd4
- File location: C:\Users\[username]\AppData\Local\Temp\BN7EF2.tmp
- File size: 153,088 bytes
- File description: ZLoader/DELoader (I think)
Click here to return to the main page.