2017-03-08 - HANCITOR INFECTION WITH ZLOADER
ASSOCIATED FILES:
- 2017-03-08-Hancitor-infection-with-ZLoaderpcap.zip 12.4 MB (12,430,228 bytes)
- 2017-03-08-Hancitor-infection-with-ZLoader.pcap (13,078,617 bytes)
- 2017-03-08-Hancitor-malspam-10-examples.zip 17.6 kB (17,578 bytes)
- 2017-03-08-Hancitor-malspam-1547-UTC.eml (3,338 bytes)
- 2017-03-08-Hancitor-malspam-1715-UTC.eml (3,357 bytes)
- 2017-03-08-Hancitor-malspam-1744-UTC.eml (3,384 bytes)
- 2017-03-08-Hancitor-malspam-1949-UTC.eml (3,310 bytes)
- 2017-03-08-Hancitor-malspam-1954-UTC.eml (3,308 bytes)
- 2017-03-08-Hancitor-malspam-2016-UTC.eml (3,333 bytes)
- 2017-03-08-Hancitor-malspam-2031-UTC.eml (3,336 bytes)
- 2017-03-08-Hancitor-malspam-2057-UTC.eml (3,332 bytes)
- 2017-03-08-Hancitor-malspam-2101-UTC.eml (3,354 bytes)
- 2017-03-08-Hancitor-malspam-2125-UTC.eml (3,311 bytes)
- 2017-03-08-Hancitor-malspam-tracker.csv (2,160 bytes)
- 2017-03-08-malware-from-Hancitor-infection.zip 227.0 kB (226,988 bytes)
- BNE80.tmp.exe (175,104 bytes)
- eFax_gabe.smith.doc (166,400 bytes)
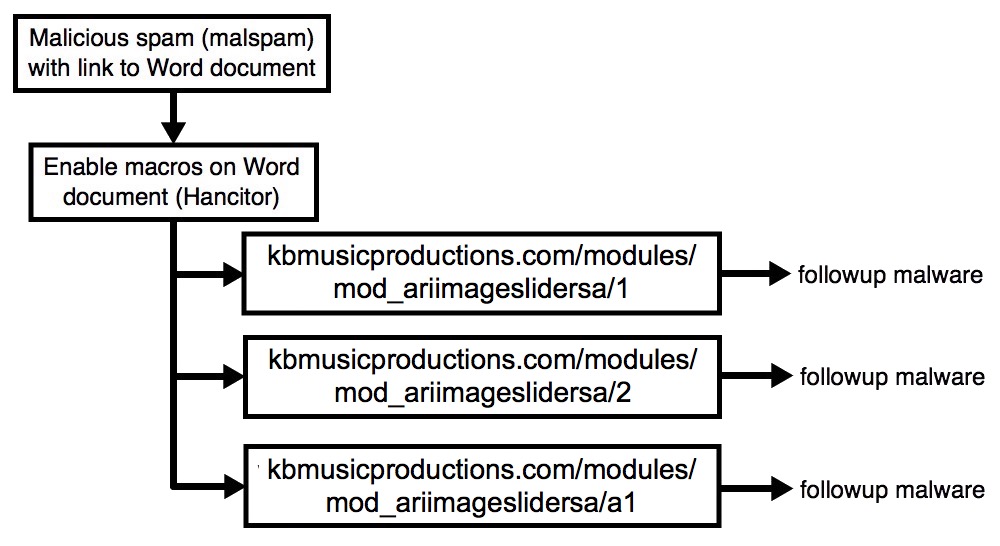
Shown above: Flow chart for today's traffic.
DESCRIPTION:
- Malicious spam (malspam) with link that downloaded a malcious Microsoft Word document (Hancitor). The Hancitor malware document is designed to download and infect Windows hosts with malware.
EMAIL HEADERS:
- Date: Monday, 2017-03-08 as early as 15:47 UTC thru at least 21:25 UTC
- From (spoofed): "eFax" <message@efaxcorporate[.]com>
- Subject: You received a new eFax from [10-digit US phone number starting with area code 212]
- See the spreadsheet tracker for details.
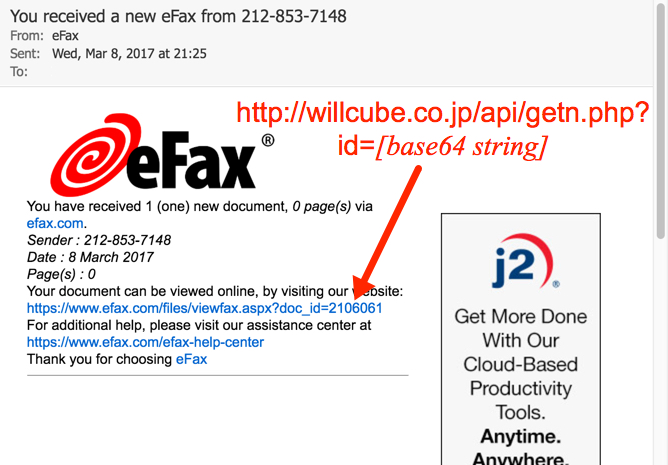
Shown above: Screenshot from one of the emails.
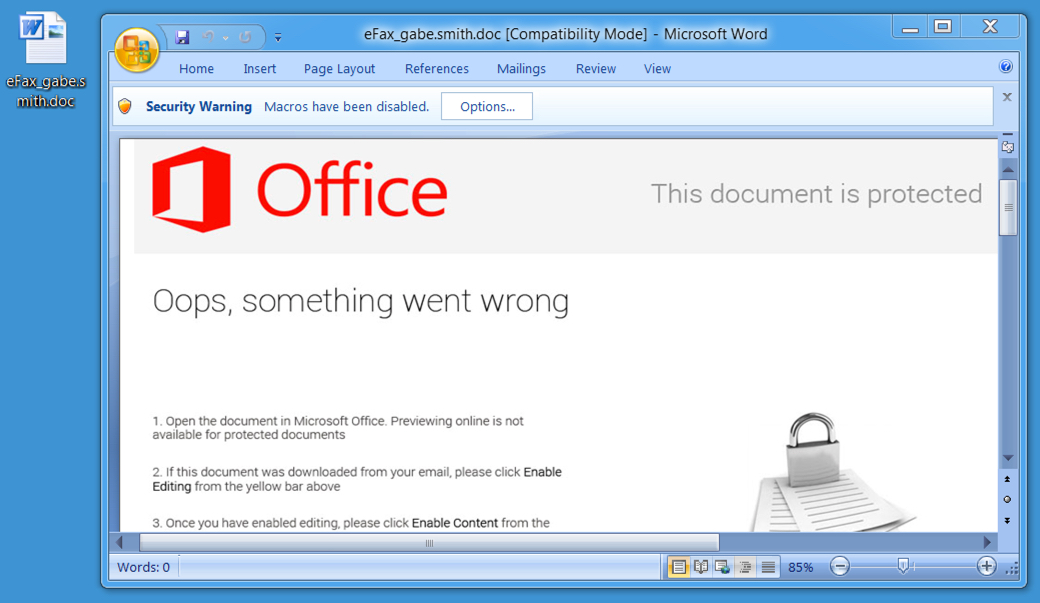
Shown above: Malicious Word document (Hancitor).
TRAFFIC
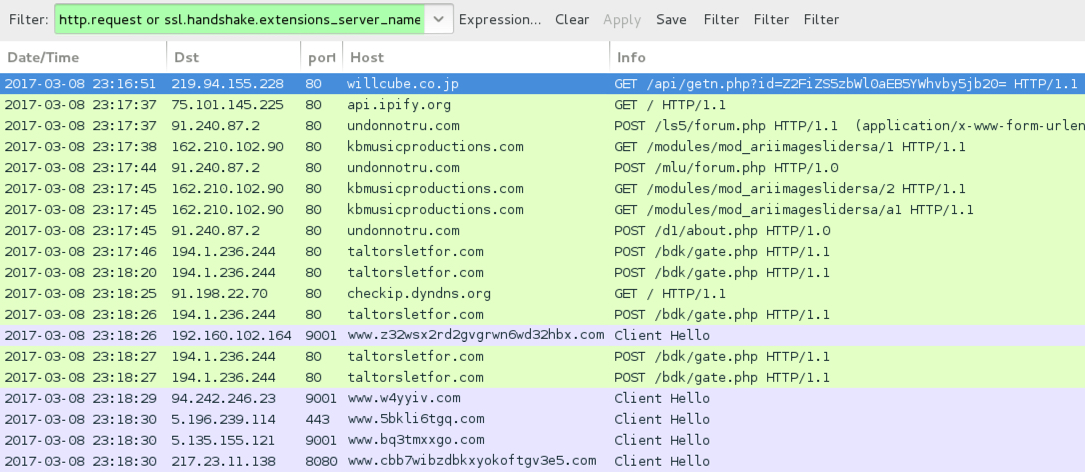
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS AND URLS:
- 210.245.80[.]30 port 80 - cocdoc.fpt[.]edu[.]vn - GET /api/getn.php?id=[base64 string] [not working when I checked]
- 103.6.198[.]124 port 80 - peakfitness[.]com[.]my - GET /api/getn.php?id=[base64 string] [not working when I checked]
- 219.94.155[.]228 port 80 - willcube[.]co[.]jp - GET /api/getn.php?id=[base64 string]
- 91.240.87[.]2 port 80 - undonnotru[.]com - POST /ls5/forum.php
- 91.240.87[.]2 port 80 - undonnotru[.]com - POST /mlu/forum.php
- 91.240.87[.]2 port 80 - undonnotru[.]com - POST /d1/about.php
- 162.210.102[.]90 port 80 - kbmusicproductions[.]com - GET /modules/mod_ariimageslidersa/1
- 162.210.102[.]90 port 80 - kbmusicproductions[.]com - GET /modules/mod_ariimageslidersa/2
- 162.210.102[.]90 port 80 - kbmusicproductions[.]com - GET /modules/mod_ariimageslidersa/a1
- 194.1.236[.2]44 port 80 - taltorsletfor.com - POST /bdk/gate.php
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses, various ports - various domains - Tor traffic
FILE HASHES
HANCITOR MALDOC:
- SHA256 hash: f1ca46b16fa0101d2e147e2a5b6452f29ef189495903162ffa887e11a0412df5
- File name: eFax_gabe.smith.doc
- File size: 166,400 bytes
- File description: Hancitor maldoc
FROM THE INFECTED HOST:
- SHA256 hash: 2798928b07527108872bde33079be1f6a712fdfcd73316798b6725f922a91169
- File location: C:\Users\[username]\AppData\Local\Temp\BNE80.tmp
- File size: 175,104 bytes
- File description: ZLoader/DELoader (I think)
Click here to return to the main page.