2017-03-09 - RIG EK SENDS ZBOT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-03-09-Rig-EK-sends-Zbot.pcap.zip 980 kB (980,108 bytes)
- 2017-03-09-Rig-EK-sends-Zbot.pcap (1,251,677 bytes)
- 22017-03-09-Rig-EK-artifacts-and-Zbot-malware.zip 466.5 kB (466,534 bytes)
- 2017-03-09-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-03-09-Rig-EK-flash-exploit.swf (16,090 bytes)
- 2017-03-09-Rig-EK-landing-page.txt (57,094 bytes)
- 2017-03-09-Rig-EK-payload-Zbot-qfb4a0n0.exe (369,664 bytes)
- 2017-03-09-page-from-hurtmehard_net-with-injected-script.txt (253,295 bytes)
NOTES:
- This instance of Rig EK is not from one of the campaigns I normally track (Afraidgate, EITest, pseudoDarkleech).
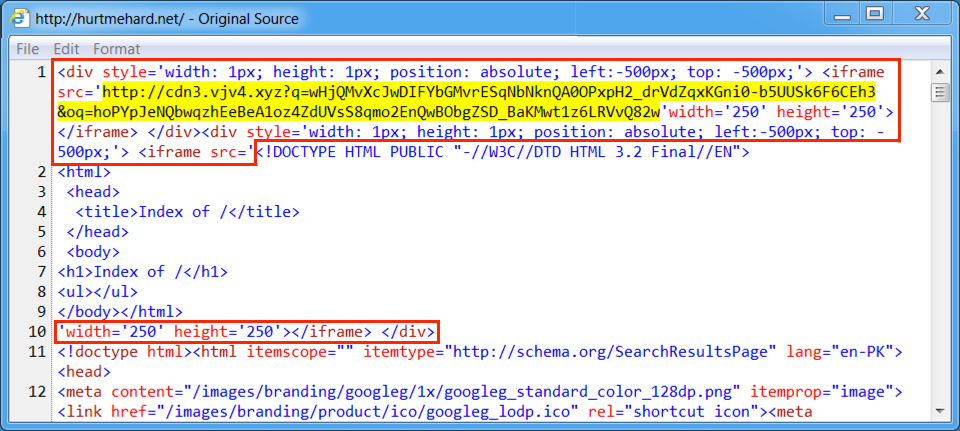
- Also, the injected script looks like it got jumbled up in the web page from the compromised site.
Shown above: Injected script in page from the compromised site. Looks like the web page text may have been scrambled.
TRAFFIC
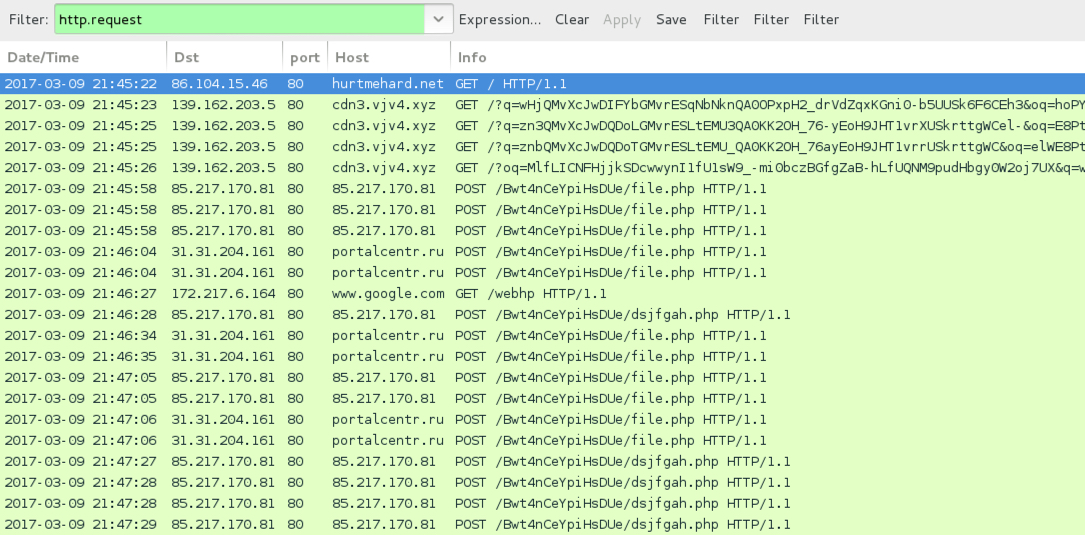
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS AND URLS:
- hurtmehard[.]net - Compromised site
- 139.162.203[.]5 port 80 - cdn3.vjv4[.]xyz - Rig EK
- 85.217.170[.]81 port 80 - 85.217.170[.]81 - POST /Bwt4nCeYpiHsDUe/file.php [Zbot callback]
- 31.31.204[.]161 port 80 - portalcentr[.]ru - POST /Bwt4nCeYpiHsDUe/file.php [Zbot callback]
- www.google[.]com - GET /webhp [Zbot post-infection connectivity check]
FILE HASHES
RIG EK FLASH EXPLOIT:
- SHA256 hash: d5ee007a06cc4b8c0100ed4950a4350c0e8e4ad17fe5417de2c2231f48a6021f
- File size: 16,090 bytes
RIG EK PAYLOAD:
- SHA256 hash: 904ba982fd067daed01ebcd896a8b8cf3e21e1a4069aadb236825f2f5180e326
- File location: C:\Users\[username]\AppData\Local\Temp\qfb4a0n0.exe
- File location: C:\Users\[username]\AppData\Roaming\Arybusquyq\egxudeuz.exe
- File size: 369,664 bytes
SOME ARTIFACTS ON THE INFECTED HOST:
- C:\Users\[username]\AppData\Local\Temp\System32\shell32.dll (4 kB)
- C:\Users\[username]\AppData\Roaming\Arybusquyq\egxudeuz.exe (361 kB)
- C:\Users\[username]\AppData\Roaming\Efhevuyni\iwpycyrow.owe (0 kB)
- C:\Users\[username]\AppData\Roaming\Qyifexihvy\saozezycmin.tmp (1 kB)
IMAGES
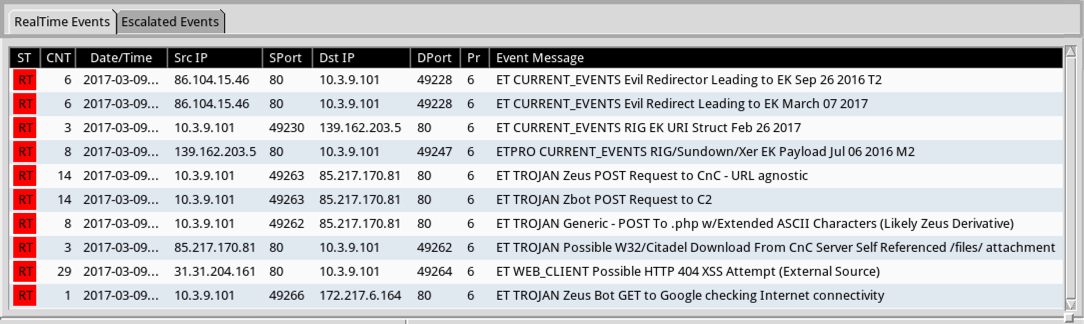
Shown above: Some alerts on the traffic from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion.
Click here to return to the main page.