2017-03-13 HANCITOR INFECTION WITH ZLOADER AND SEND SAFE ENTERPRISE (SSE) SPAMBOT TRAFFIC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-03-13-Hancitor-infection-with-ZLoader-and-SendSafe-spambot-traffic.pcap.zip 16.1 MB (16,053,632 bytes)
- 2017-03-13-Hancitor-malspam-9-examples.zip 8.6 kB (8,644 bytes)
- 2017-03-13-malware-from-Hancitor-infection.zip 1.8 MB (1,798,892 bytes)
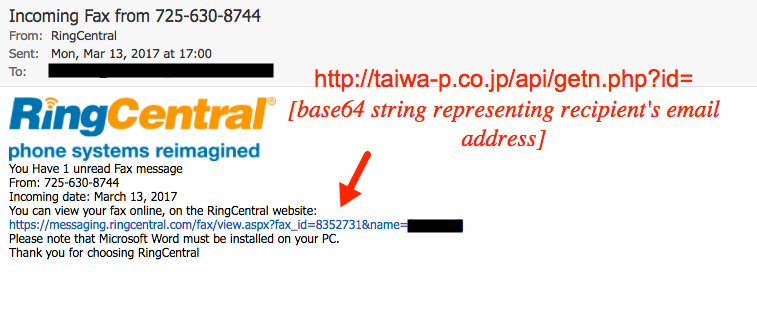
Shown above: Screen shot of the email.
EMAIL HEADERS:
- Date/Time: Monday 2017-03-13 from 17:00 thru at least 20:01 UTC
- Subject: Incoming Fax from (various phone numbers starting with area code 725)
- From: "RingCentral" <ringcentral@messaging[.]com>
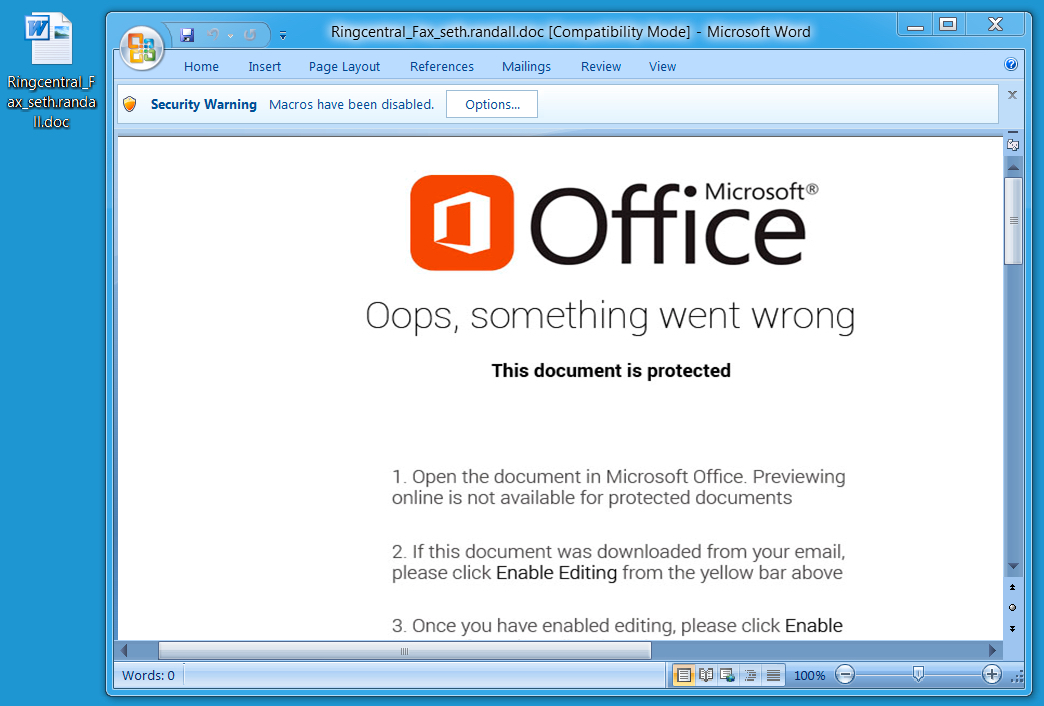
Shown above: Malicious Word document (Hancitor) from link in the malspam.
TRAFFIC
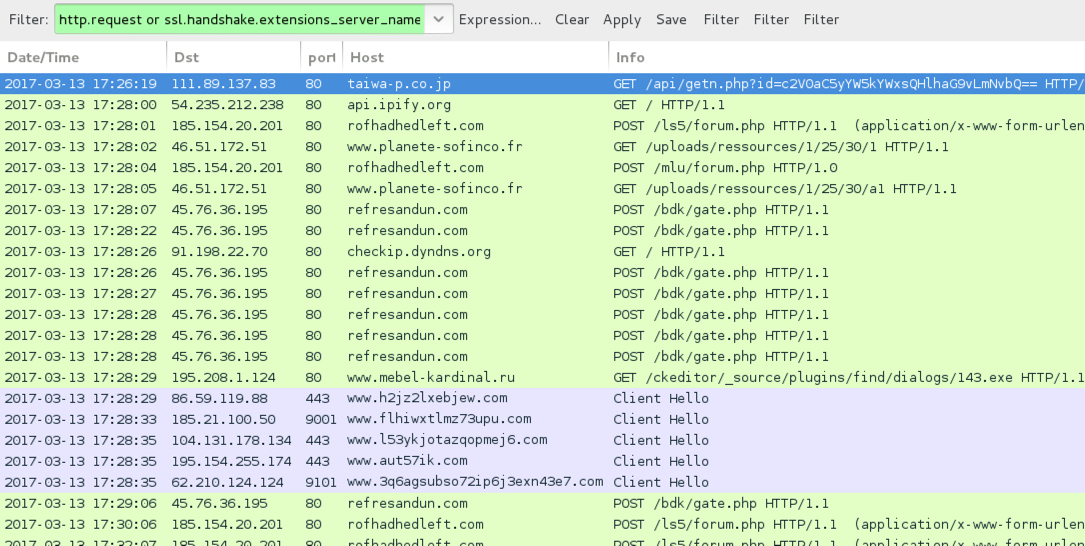
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 111.89.137[.]83 port 80 - taiwa-p[.]co[.]jp - GET /api/getn.php?[base64 string]
- 185.154.20[.]201 port 80 - rofhadhedleft[.]com - POST /ls5/forum.php
- 185.154.20[.201 port 80 - rofhadhedleft[.]com - POST /mlu/forum.php
- 46.51.172[.]51 port 80 - www.planete-sofinco[.]fr - GET /uploads/ressources/1/25/30/1
- 46.51.172[.]51 port 80 - www.planete-sofinco[.]fr - GET /uploads/ressources/1/25/30/a1
- 45.76.36[.]195 port 80 - refresandun[.]com - POST /bdk/gate.php
- 195.208.1[.]124 port 80 - www.mebel-kardinal[.]ru - GET /ckeditor/_source/plugins/find/dialogs/143.exe
- api.ipify[.]org - GET /
- checkip.dyndns[.]org - GET /
- Various IP addresses, various ports - Tor traffic
- Various IP addresses, port 25 - Attempted SMTP traffic
- 91.220.131[.]143 port 50008 - UDP beacon traffic
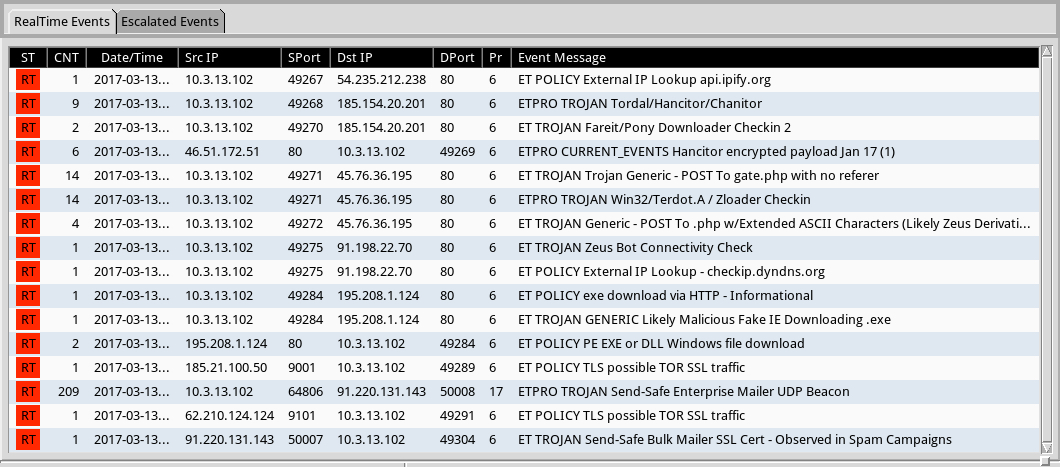
Shown above: Some alerts on the traffic from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion.
FILE HASHES
FROM LINK IN THE EMAIL:
- SHA256 hash: 800bf028a23440134fc834efc5c1e02cc70f05b2e800bbc285d7c92a4b126b1c
File name: Ringcentral_Fax_seth.randall.doc
File description: Hancitor maldoc
DOWNLOADED MALWARE:
- SHA256 hash: 124dfffd5286bb6d831a18a598e4100904a522e1c8fa0d2e5014f0fb7ed7d088
File location: C:\Users\[username]\AppData\Local\Temp\BNA6E8.tmp
File description: DELoader/ZLoader
- SHA256 hash: 8161c820dc9137e68b2542b20940d89ca653852d13291c72f6ef2eca9f34a2d9
File name: 143.exe
File description: SendSafe spambot malware
Click here to return to the main page.
