2017-03-15 - UNIDENTIFIED CAMPAIGN RIG EK SENDS ZLOADER (DELOADER)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-03-15-unidentified-campaign-Rig-EK-sends-ZLoader.pcap.zip 3.5 MB (3,465,332 bytes)
- 2017-03-15-unidentified-campaign-Rig-EK-sends-ZLoader.pcap (3,703,929 bytes)
- 2017-03-15-unidentified-campaign-Rig-EK-artifacts-and-ZLoader-malware.zip 243.8 kB (243,809 bytes)
- 2017-03-15-page-from-xbox360torrent_com-with-injected-script.txt (31,651 bytes)
- 2017-03-15-unidentified-campaign-Rig-EK-1st-run-artifact-o32.tmp.txt (1,141 bytes)
- 2017-03-15-unidentified-campaign-Rig-EK-flash-exploit.swf (14,956 bytes)
- 2017-03-15-unidentified-campaign-Rig-EK-landing-page.txt (117,890 bytes)
- 2017-03-15-unidentified-campaign-Rig-EK-payload-ZLoader-otr4miha.exe (169,791 bytes)
DETAILS
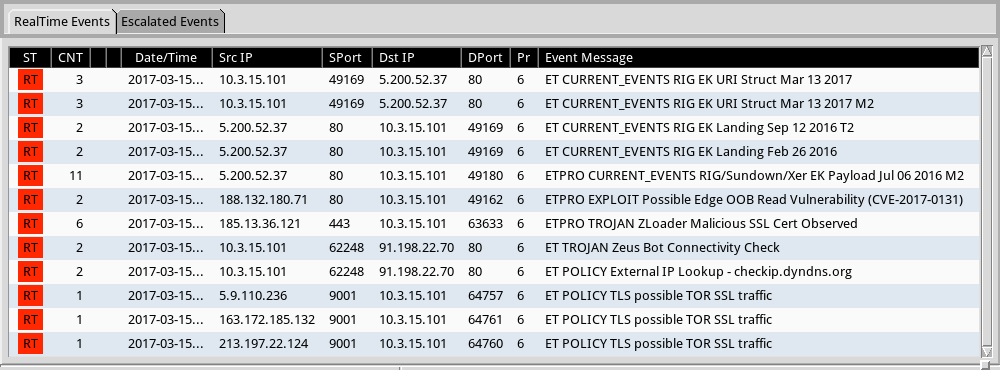
DESCRIPTION:
- An unidentified campaign using Rig EK to distribute malware. On Wednesday 2017-03-15, it sent DELoader/Zloader as the payload.
ASSOCIATED DOMAINS:
- xbox360torrent[.]com - compromised side
- 5.200.52[.]37 port 80 - add.tas-goodiebag[.]com - Rig EK
- 185.121.177[.]53 port 53 - TCP-based DNS query for funchat[.]bit
- 185.13.36[.]121 port 80 - funchat[.]bit - attempted TCP connections but RST by server
- 185.13.36[.]121 port 443 - funchat[.]bit - HTTPS/SSL/TLS traffic using "Moscow Ltd" certificate
- checkip.dyndns[.]org - GET / - IP address check
- Various IP addresses on various ports - Tor traffic
ARTIFACTS ON THE INFECTED HOST:
- C:\Users\[username]\AppData\Roaming\Egsef\fbxae.nio (0 kB)
- C:\Users\[username]\AppData\Roaming\tor\cached-certs (19 kB)
- C:\Users\[username]\AppData\Roaming\tor\cached-microdesc-consensus (2,191 kB)
- C:\Users\[username]\AppData\Roaming\tor\cached-microdescs.new (3,680 kB)
- C:\Users\[username]\AppData\Roaming\tor\lock (0 kB)
- C:\Users\[username]\AppData\Roaming\tor\state (2 kB)
- C:\Users\[username]\AppData\Roaming\Ugnu\badeazpoo.php (4 kB)
- C:\Users\[username]\AppData\Roaming\Ugnu\php.exe (29 kB)
- C:\Users\[username]\AppData\Roaming\Ugnu\php5tl.dll (5,589 kB)
- C:\Users\[username]\AppData\Roaming\Wyqyuf\huab.zia (21,687 kB)
- C:\Users\[username]\AppData\Roaming\Ywal\efyku.ovt (95 kB)
- C:\Users\[username]\AppData\Roaming\libeay32.dll (1,944 kB)
- C:\Users\[username]\AppData\Roaming\libevent-2-0-5.dll (703 kB)
- C:\Users\[username]\AppData\Roaming\libgcc_s_sjlj-1.dll (511 kB)
- C:\Users\[username]\AppData\Roaming\libssp-0.dll (91 kB)
- C:\Users\[username]\AppData\Roaming\ssleay32.dll (391 kB)
- C:\Users\[username]\AppData\Roaming\tor.exe (2,898 kB)
- C:\Users\[username]\AppData\Roaming\zlib1.dll (105 kB)
FILE HASHES:
- SHA256 hash: cc41480100b0fd2e39d4d636fac3d4e682314b4c6b14ecef0d03281c06a7789c
File description: Rig EK Flash exploit seen on 2017-03-15
- SHA256 hash: 7a582e7ad76cd0f90b0e51092212603883f9db0d5e810f6fb20f809d4322e057
File location: C:\Users\[username]\AppData\Local\Temp\otr4miha.exe
File description: Rig EK payload sent by unidentified campaign - ZLoader (DELoader)
FINAL NOTES
Click here to return to the main page.
