2017-03-15 - PSEUDO-DARKLEECH RIG EK SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-03-15-pseudoDarkleech-Rig-EK-sends-Cerber-ransomware-2-pcaps.zip 976.9B (976,910 bytes)
- 2017-03-15-pseudoDarkleech-Rig-EK-sends-Cerber-ransomware-1st-run.pcap (797,089 bytes)
- 2017-03-15-pseudoDarkleech-Rig-EK-sends-Cerber-ransomware-2nd-run.pcap (406,889 bytes)
- 2017-03-15-pseudoDarkleech-Rig-EK-artifacts-and-Cerber-ransomware.zip 2.6 MB (2,624,479 bytes)
- 2017-03-12-pseudoDarkleech-Rig-EK-artifact-both-runs-o32.tmp.txt (1,141 bytes)
- 2017-03-15-Cerber-ransomware_READ_THIS_FILE_KVGVA_.hta (77,345 bytes)
- 2017-03-15-Cerber-ransomware_READ_THIS_FILE_L5KW_.jpeg (1,975,631 bytes)
- 2017-03-15-Cerbe-ransomwarer_READ_THIS_FILE_M0761P_.txt (1,337 bytes)
- 2017-03-15-page-from-jesuisanimateur_fr-with-injected-pseudoDarkleech-script-1st-run.txt (157,692 bytes)
- 2017-03-15-page-from-jesuisanimateur_fr-with-injected-pseudoDarkleech-script-2nd-run.txt (156,494 bytes)
- 2017-03-15-pseudoDarkleech-Rig-EK-1st-run-flash-exploit.swf (14,956 bytes)
- 2017-03-15-pseudoDarkleech-Rig-EK-1st-run-landing-page.txt (117,920 bytes)
- 2017-03-15-pseudoDarkleech-Rig-EK-1st-run-payload-Cerber-ransomware-n0ofzkos.exe (257,225 bytes)
- 2017-03-15-pseudoDarkleech-Rig-EK-2nd-run-flash-exploit.swf (14,942 bytes)
- 2017-03-15-pseudoDarkleech-Rig-EK-2nd-run-landing-page.txt (57,857 bytes)
- 2017-03-15-pseudoDarkleech-Rig-EK-2nd-run-payload-Cerber-ransomware-wyprkl4v.exe (257,225 bytes)
DETAILS
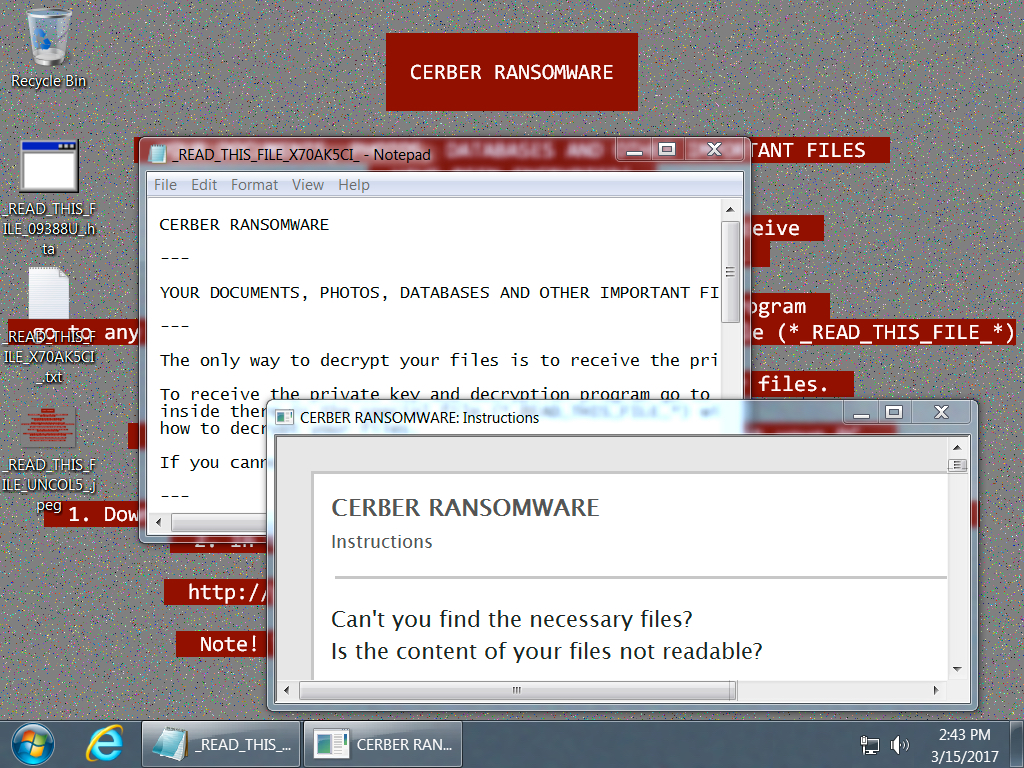
TRAFFIC FROM AN INFECTION:
- www.jesuisanimateur[.]fr - compromised side
- 5.200.52[.]37 port 80 - rew.thebookingsites[.]com - Rig EK
- 149.202.64[.]0 - 149.202.64[.]31 (149.202.64[.]0/27) UDP port 6892 - Cerber ransomware UDP post-infection traffic
- 149.202.122[.]0 - 149.202.122[.]31 (149.202.122[.]0/27) UDP port 6892 - Cerber ransomware UDP post-infection traffic
- 149.202.248[.]0 - 149.202.251[.]255 (149.202.248[.]0/22) UDP port 6892 - Cerber ransomware UDP post-infection traffic
- 104.232.37[.]30 port 80 - p27dokhpz2n7nvgr.16bwhs[.]top - Cerber ransomware HTTP post-infection traffic
FILE HASHES:
- SHA256 hash: cc41480100b0fd2e39d4d636fac3d4e682314b4c6b14ecef0d03281c06a7789c
File description: Rig EK Flash exploit seen on 2017-03-15
- SHA256 hash: 3ff2b1e57b82789084f722fb22388af0d79dc3340325d8db83e63c1a2a42da79
File description: Rig EK Flash exploit seen on 2017-03-15 (2nd run)
- SHA256 hash: af53d162953b030e0b81c84f13e33b0378686d214a4a02b05e55218bab2fd609
File location: C:\Users\[username]\AppData\Local\Temp\n0ofzkos.exe
File description: Rig EK payload sent by pseudo-Darkleech campaign - Cerber ransomware (1st run)
- SHA256 hash: 00386621b62147ab8fa6c6dc095259a9923b71f97a2c7b323995883b6cf5773b
File location: C:\Users\[username]\AppData\Local\Temp\wyprkl4v.exe
File description: Rig EK payload sent by pseudo-Darkleech campaign - Cerber ransomware (2nd run)
Click here to return to the main page.
