2017-03-24 - "BLANK SLATE" CAMPAIGN TRIES FAKE CHROME INSTALL PAGE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-03-24-Blank-Slate-activity-3-pcaps.zip 543.8 kB (543,784 bytes)
- 2017-03-24-Blank-Slate-malspam-tracker.csv.zip 1.4 kB (1,441 bytes)
- 2017-03-24-Blank-Slate-emails-and-Cerber-ransomware.zip 1.1 MB (1,051,346 bytes)
NOTES:
- Blank Slate tried mixing it up today, with fake emails about your Microsoft account and links to a fake Chrome install page.
- After 4 to 5 hours of the fake Microsoft/Chrome emails, Blank Slate went back to normal operations (blank emails with the double-zipped attachments).
- The same domains were used for the regular blank emails and the fake Microsoft/Chrome emails.
- I got Locky ransomware when I first tried it at 1529 UTC; however, I accidentally deleted the pcap.
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- I wrote a follow-up for the Internet Storm Center (ISC) titled: "Blank Slate" malspam still pushing Cerber ransomware.
EMAILS
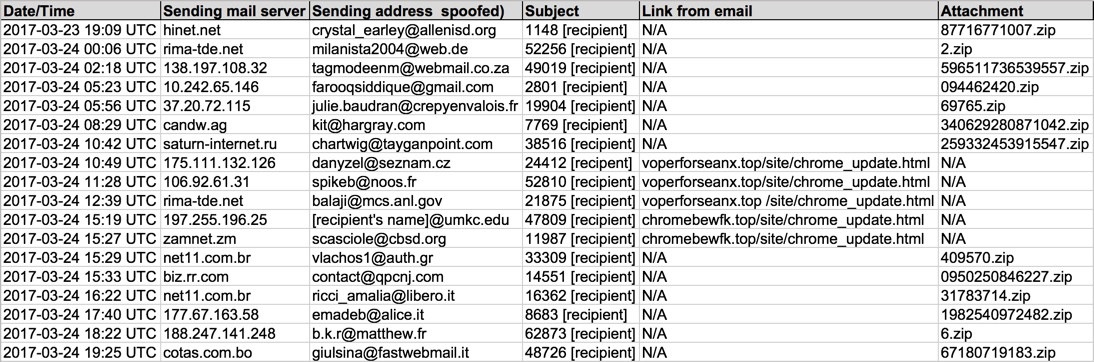
Shown above: Information from the spreadsheet tracker (part 1 of 2).
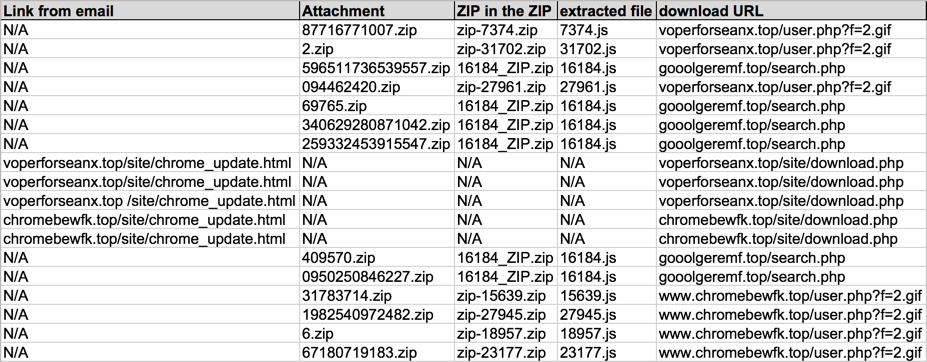
Shown above: Information from the spreadsheet tracker (part 2 of 2).
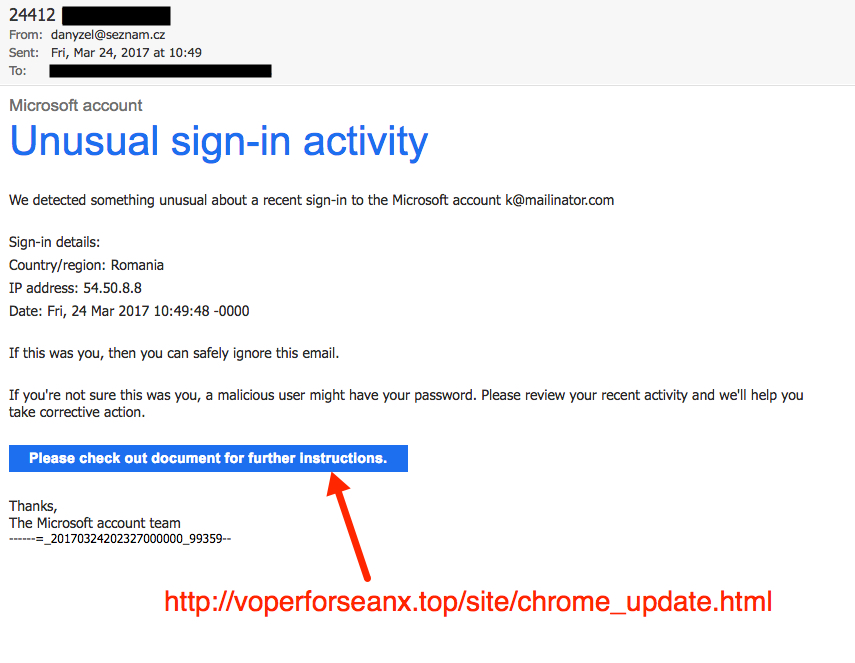
Shown above: Example of a Blank Slate email that wasn't blank.
EMAILS GATHERED:
(Read: Date/Time -- Sending mail server -- Sending email (spoofed) -- Subject -- Attached zip or URL from email link)
- 2017-03-23 19:09 UTC -- hinet[.]net -- crystal_earley@allenisd[.]org -- 1148 [recipient] -- 87716771007.zip
- 2017-03-24 00:06 UTC -- rima-tde[.]net -- milanista2004@web[.]de -- 52256 [recipient] -- 2.zip
- 2017-03-24 02:18 UTC -- 138.197.108[.]32 -- tagmodeenm@webmail[.]co[.]za -- 49019 [recipient] -- 596511736539557.zip
- 2017-03-24 05:23 UTC -- 10.242.65[.]146 -- farooqsiddique@gmail[.]com -- 2801 [recipient] -- 094462420.zip
- 2017-03-24 05:56 UTC -- 37.20.72[.]115 -- julie.baudran@crepyenvalois[.]fr -- 19904 [recipient] -- 69765.zip
- 2017-03-24 08:29 UTC -- candw[.]ag -- kit@hargray[.]com -- 7769 [recipient] -- 340629280871042.zip
- 2017-03-24 10:42 UTC -- saturn-internet[.]ru -- chartwig@tayganpoint[.]com -- 38516 [recipient] -- 259332453915547.zip
- 2017-03-24 10:49 UTC -- 175.111.132[.]126 -- danyzel@seznam[.]cz -- 24412 [recipent] -- voperforseanx[.]top - GET /site/chrome_update.html
- 2017-03-24 11:28 UTC -- 106.92.61[.]31 -- spikeb@noos[.]fr -- 52810 [recipient] -- voperforseanx[.]top - GET /site/chrome_update.html
- 2017-03-24 12:39 UTC -- rima-tde[.]net -- balaji@mcs.anl[.]gov -- 21875 [recipient] -- voperforseanx[.]top - GET /site/chrome_update.html
- 2017-03-24 15:19 UTC -- 197.255.196[.]25 -- [recipient's name]@umkc.edu -- 47809 [recipient] -- chromebewfk[.]top - GET /site/chrome_update.html
- 2017-03-24 15:27 UTC -- zamnet[.]zm -- scasciole@cbsd[.]org -- 11987 [recipient] -- chromebewfk[.]top - GET /site/chrome_update.html
- 2017-03-24 15:29 UTC -- net11[.]com[.]br -- vlachos1@auth[.]gr -- 33309 [recipient] -- 409570.zip
- 2017-03-24 15:33 UTC -- biz.rr[.]com -- contact@qpcnj[.]com -- 14551 [recipient] -- 0950250846227.zip
- 2017-03-24 16:22 UTC -- net11[.]com[.]br -- ricci_amalia@libero[.]it -- 16362 [recipient] -- 31783714.zip
- 2017-03-24 17:40 UTC -- 177.67.163[.]58 -- emadeb@alice[.]it -- 8683 [recipient] -- 1982540972482.zip
- 2017-03-24 18:22 UTC -- 188.247.141[.]248 -- b.k.r@matthew[.]fr -- 62873 [recipient] -- 6.zip
- 2017-03-24 19:25 UTC -- cotas[.]com[.]bo -- giulsina@fastwebmail[.]it -- 48726 [recipient] -- 67180719183.zip
TRAFFIC
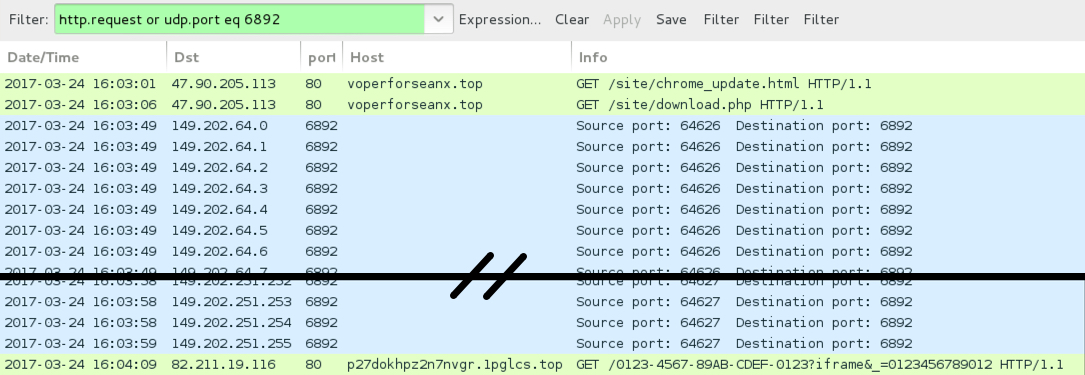
Shown above: Pcap of the infection traffic filtered in Wireshark.
HTTP TRAFFIC FOR THE RANSOMWARE:
- 47.91.158[.]176 or 54.145.185[.]110 port 80 - gooolgeremf[.]top - GET /search.php
- 47.90.205[.]113 or 35.187.59[.]173 port 80 - voperforseanx[.]top - GET /site/chrome_update.html
- 47.90.205[.]113 or 35.187.59[.]173 port 80 - voperforseanx[.]top - GET /site/download.php
- 47.90.205[.]113 or 35.187.59[.]173 port 80 - voperforseanx[.]top - GET /user.php?f=2.gif
- 47.90.205[.]113 or 35.187.59[.]173 port 80 - chromebewfk[.]top - GET /site/chrome_update.html
- 47.90.205[.]113 or 35.187.59[.]173 port 80 - chromebewfk[.]top - GET /site/download.php
- 47.90.205[.]113 or 35.187.59[.]173 port 80 - www.chromebewfk[.]top - GET /user.php?f=2.gif
CERBER RANSOMWARE POST-INFECTION TRAFFIC:
- 149.202.64[.]0 to 149.202.64[.]31 (149.202.64[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 149.202.122[.]0 to 149.202.122[.]31 (149.202.122[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 149.202.248[.]0 to 149.202.251[.]255 (149.202.248[.]0/22) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 82.211.19[.]116 port 80 - p27dokhpz2n7nvgr.1pglcs[.]top - Cerber ransomware post-infection HTTP traffic
LOCKY POST-INFECTION TRAFFIC:
- 91.234.34[.]98 port 80 - 91.234.34[.]98 - POST /checkupdate
- g46mbrrzpfszonuk[.]onion - Domain from the Locky ransomware decryption instructions
MALWARE
ATTACHMENETS:
- e5dbc3c109c84ac06b0c487032cfca6cf84179f683bc058376ad0cd2cc78b5c2 - 094462420.zip
- 4e9d3523997d3a6b25bb5c0732f3a47d993710caaf3090d721ea653148befac0 - 0950250846227.zip
- f50996eb0968d0fbdcd5b465a142e735a799081c4354fbce235fbc1f08ae304e - 1982540972482.zip
- d5bdfa631d94f45efaf017c323e562cf2e2c235307069eb855e4f68593a5f81b - 2.zip
- 4e9d3523997d3a6b25bb5c0732f3a47d993710caaf3090d721ea653148befac0 - 259332453915547.zip
- d63403e44c8589682262808c1b309492f832975118d7b5eda99f57dec7e040d1 - 31783714.zip
- 4e9d3523997d3a6b25bb5c0732f3a47d993710caaf3090d721ea653148befac0 - 340629280871042.zip
- 4e9d3523997d3a6b25bb5c0732f3a47d993710caaf3090d721ea653148befac0 - 409570.zip
- 4e9d3523997d3a6b25bb5c0732f3a47d993710caaf3090d721ea653148befac0 - 596511736539557.zip
- abb20f55faf4a7db51d19466ad4a27d4b13c8bdfe376ccce3cf61137501dd6d8 - 6.zip
- cda35229006a6555e4cf439130b1a5b97d41e2bab3726658dee97c6da8d6de97 - 67180719183.zip
- 4e9d3523997d3a6b25bb5c0732f3a47d993710caaf3090d721ea653148befac0 - 69765.zip
- a8a50eac46c95dd806c1e0a8d416636b7c9ada51ce5040d09845c0bd002b8f52 - 87716771007.zip
EXTRACTED FILES:
- 3f5830fb868c0182add3a2233c02c404e65d56380680d0bc5d2f71e5f13e0789 - 15639.js
- 1b1ea158a58da8cffbaa7b7cc26b5fb5bc5451016f0c8aa5fdf44c9db3ba9283 - 16184.js
- 198814e7e979098a2992b10479b2a1551fb6030ce8124411dbfeb602a2e6f1c8 - 18957.js
- c9c3cb47cd132ade95a5fb99b53a0f32da21e2c1e69890fc8201d179026aa146 - 23177.js
- b31975437de87e43f5b1546f8f787ee95ed8353181ad3306a2c932dbe47cf5c6 - 27945.js
- d6fecbe3efbe2a10fa517600a07f0b0a2938c8f12e283b39376069f7da9a08f3 - 27961.js
- dc473f4c12899141567b60bc352d4884e6a7c66bafc9b6000d65dc6662761d22 - 31702.js
- fc9674dfadaff53a759316e0e3959bfd74d44f7158d2b0b996d677ce2feb22c5 - 7374.js
RANSOMWARE SAMPLES:
- SHA256 hash: 1deb727ed389a37a83a04ca1fa6c5350dbba840bfc521b7abcce905c7a1f3d2c
File dscription: 2017-03-24 Ceber ransomware from chromebewfk[.]top using attachment
File size: 288,458 bytes
- SHA256 hash: c20a3dfdf51ca43b2ea6cf6065a473b49c41ce9aea7a5bba4c3a70fd3aabc7dd
File dscription: 2017-03-24 Ceber ransomware from gooolgeremf[.]top
File size: 426,409 bytes
- SHA256 hash: b45eed71cb31ca1c04433874a0ca471364353ed7193d963c2541b4ee66700a1b
File dscription: 2017-03-24 Cerber ransomware from voperforseanx[.]top using fake Chrome page
File size: 288,458 bytes
- SHA256 hash: d896e8d6516b6fe3f2d36bdd2abc3af1db222dfdcffc0a37cd1ea3c46d68f27e
File dscription: 2017-03-24 Locky ransomware from voperforseanx[.]top using fake Chrome page
File size: 145,408 bytes
IMAGES
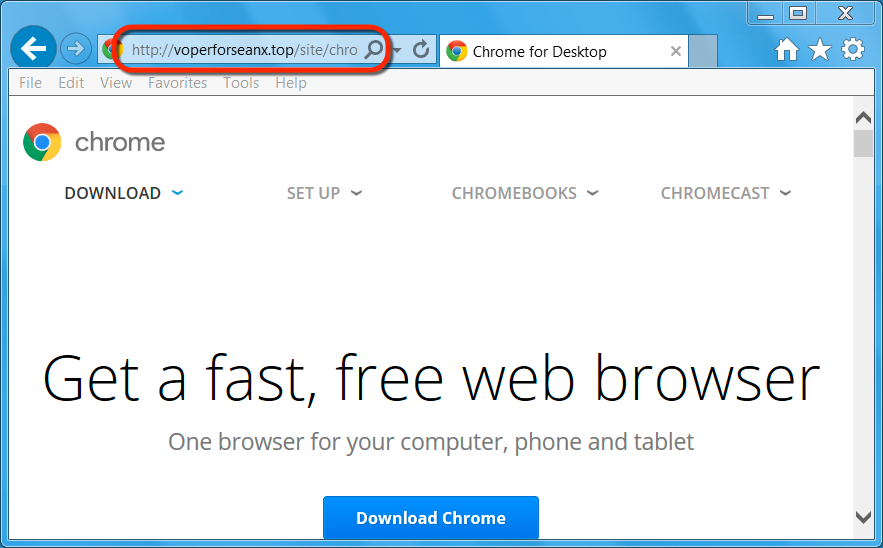
Shown above: The fake Google Chrome installation page.
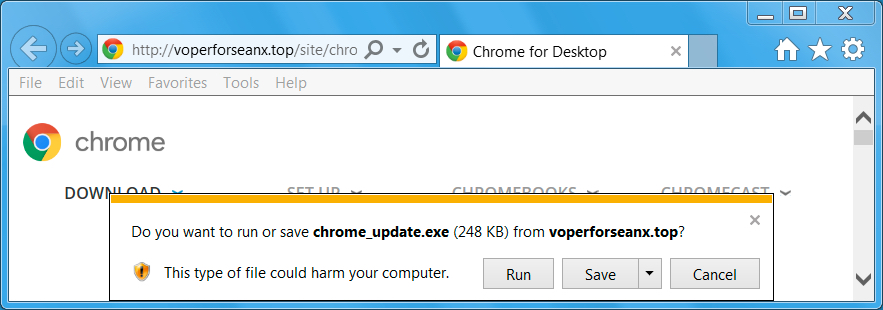
Shown above: If you wait without clicking anything, you're presented with the ransomware named chrome_update.exe.
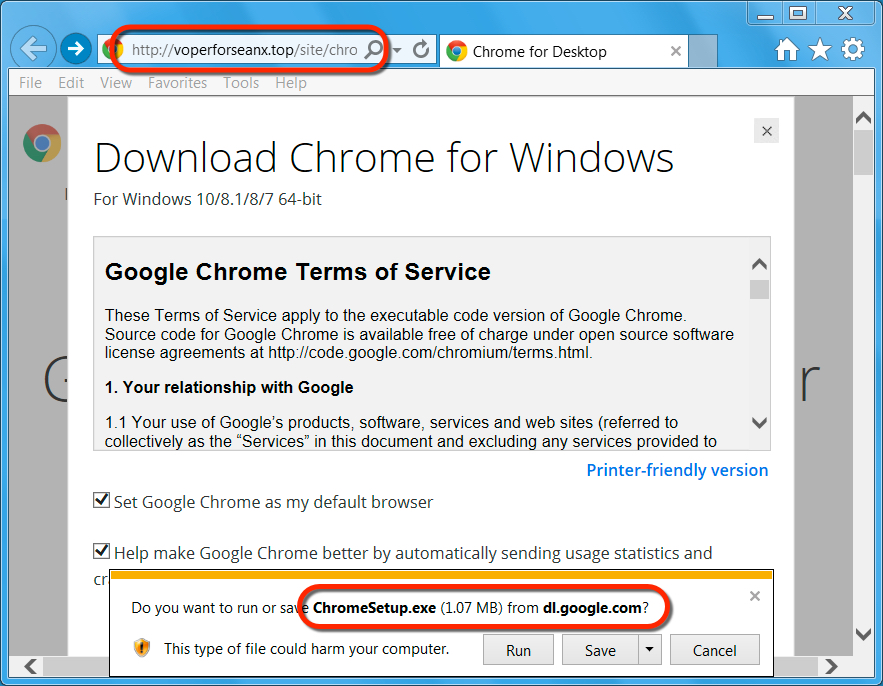
Shown above: If you click to download, you get the actual Google Chrome installer from Google.
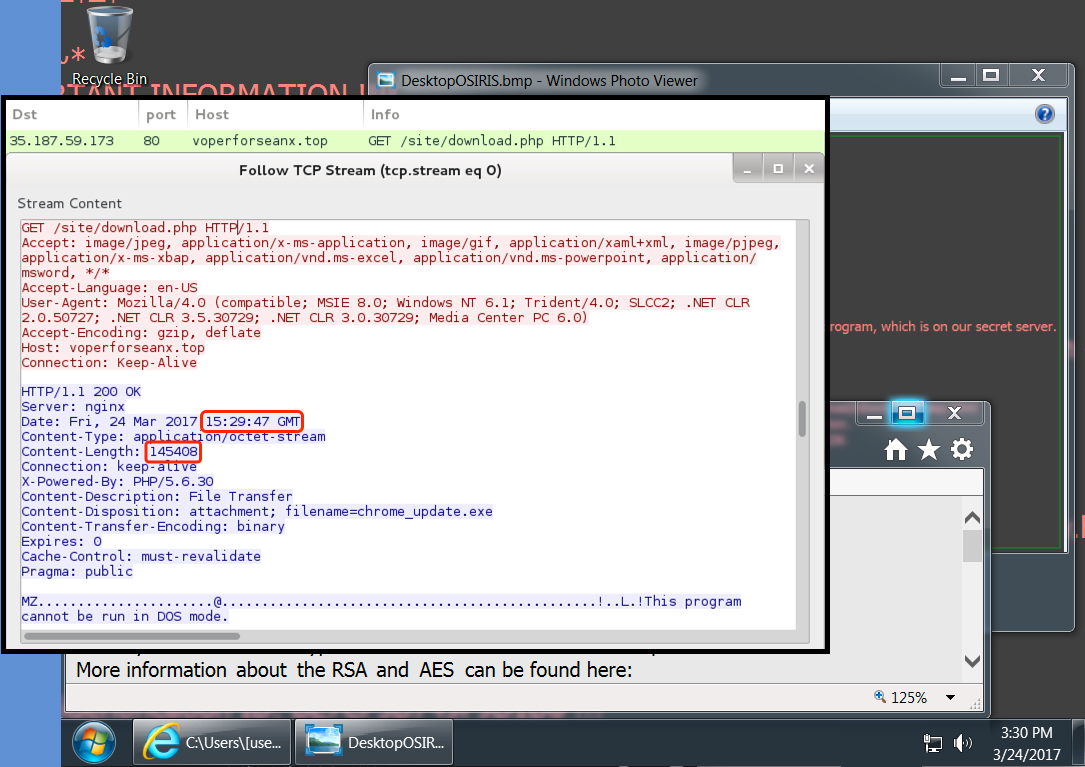
Shown above: My first chrome_update.exe download (the one I lost my pcap for) was Locky ransomware. Fortunately, I'd taken some images and saved the binary.
I would normally show an image of a Cerber ransowmare-infected desktop, but I'm about sick of seeing Cerber every day.
Click here to return to the main page.
